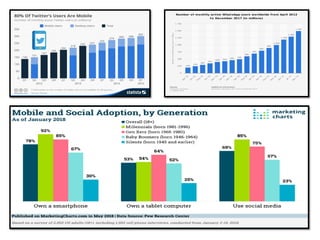
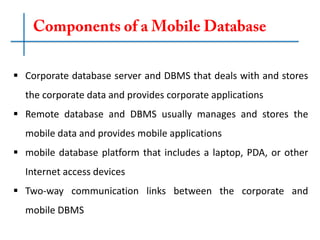
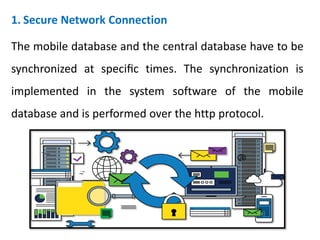
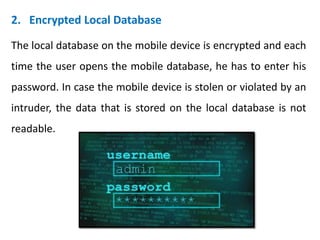
The document discusses the significance of mobile database systems in modern enterprises and their growing reliance on databases for mission-critical applications. It outlines the essential components of mobile databases, including security measures such as encrypted local databases and secure network connections to protect sensitive data. Additionally, it highlights market share leaders in mobile database systems, with Sybase SQL Anywhere dominating the field.