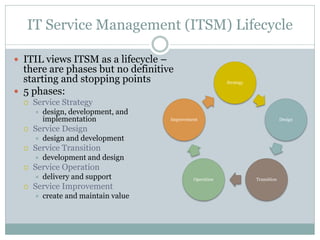
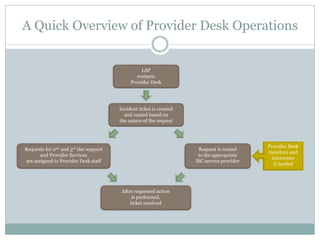
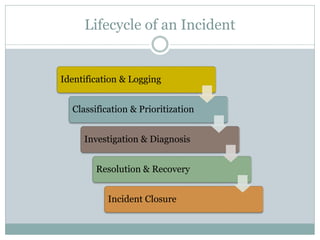
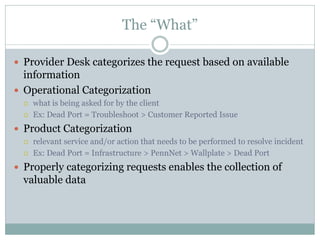
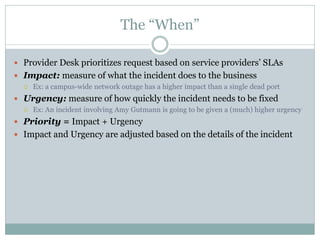
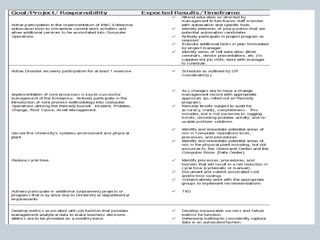
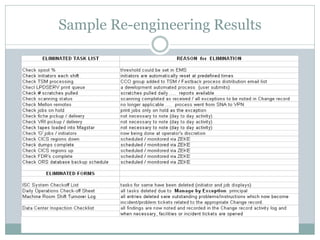
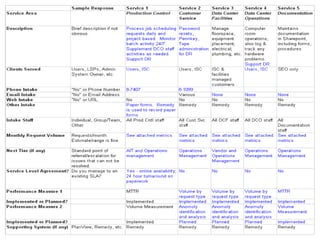
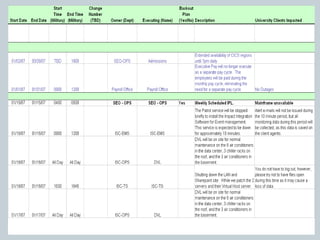
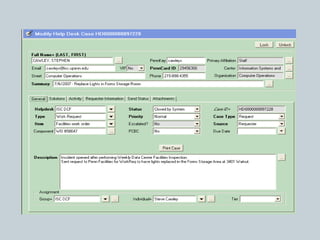
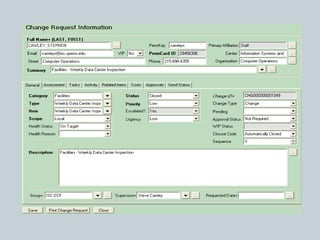
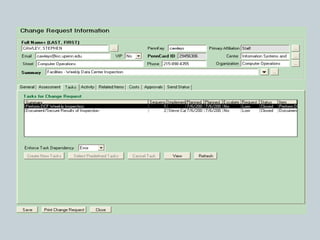
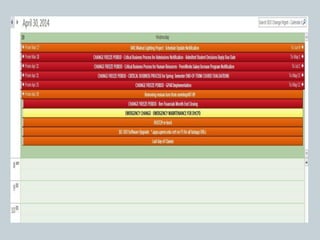
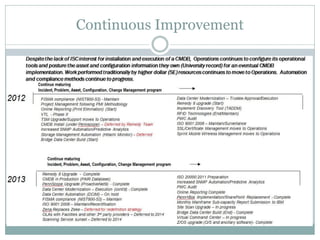
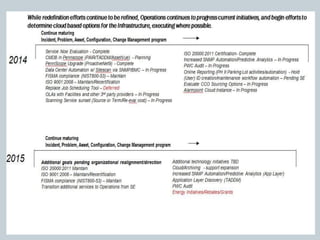
This document provides an overview of ITIL and how two departments at the University of Pennsylvania Information Systems and Computing division have implemented aspects of the ITIL framework. It describes how the Provider Desk utilizes ITIL practices like incident management and how Computer Operations restructured its organization and processes according to the ITIL lifecycle model to improve service and implement metrics and reporting. The case studies demonstrate how ITIL can provide structure and best practices to help IT organizations deliver high quality services aligned with business needs.