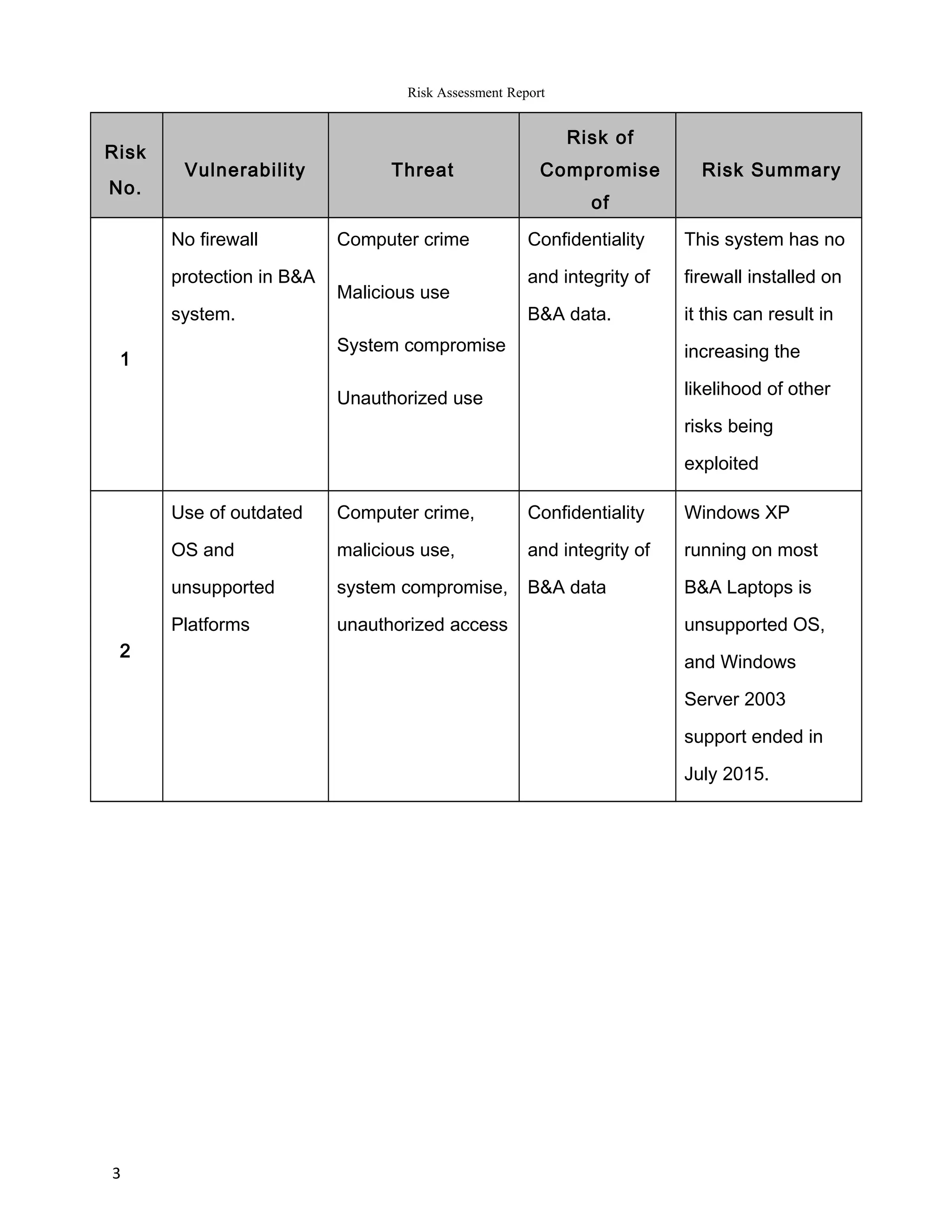
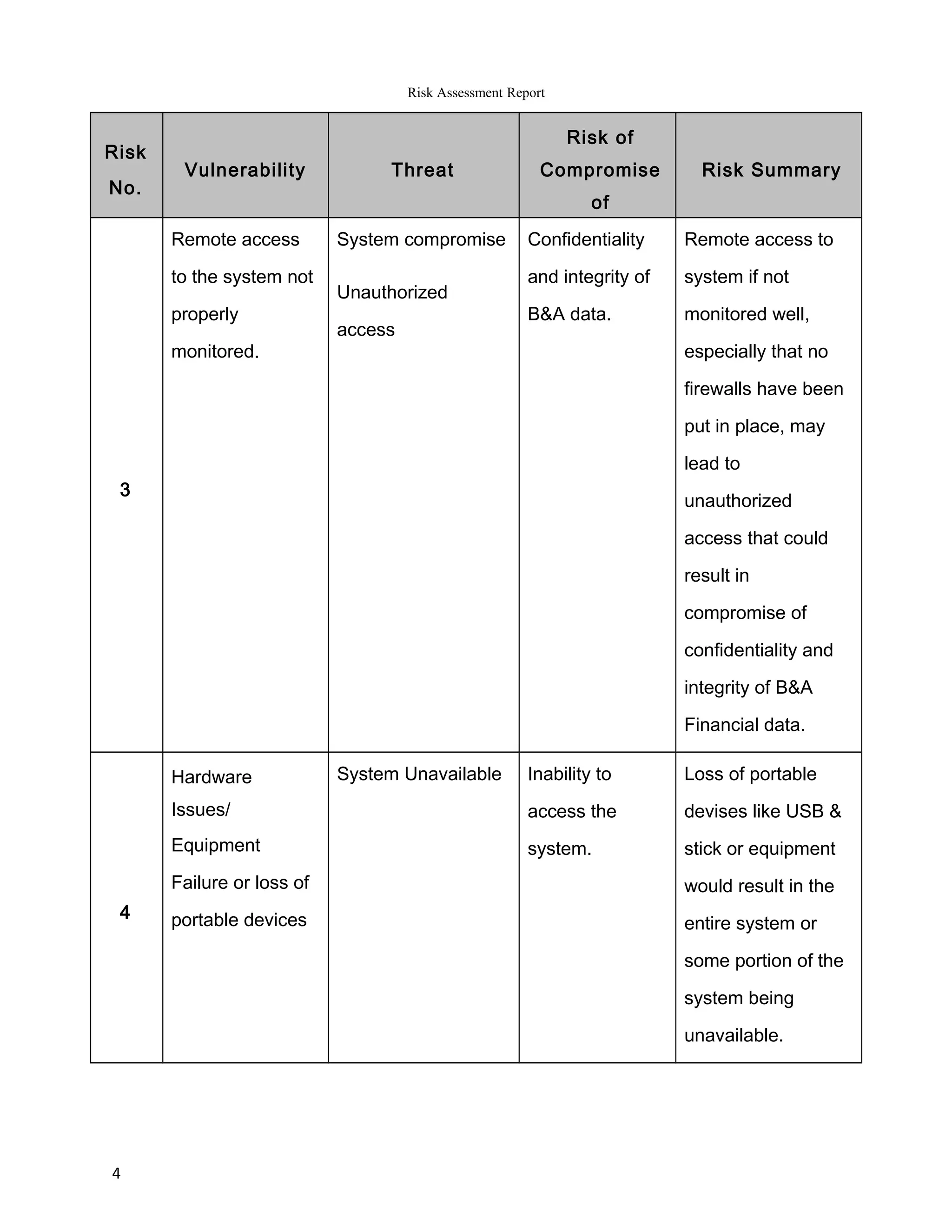
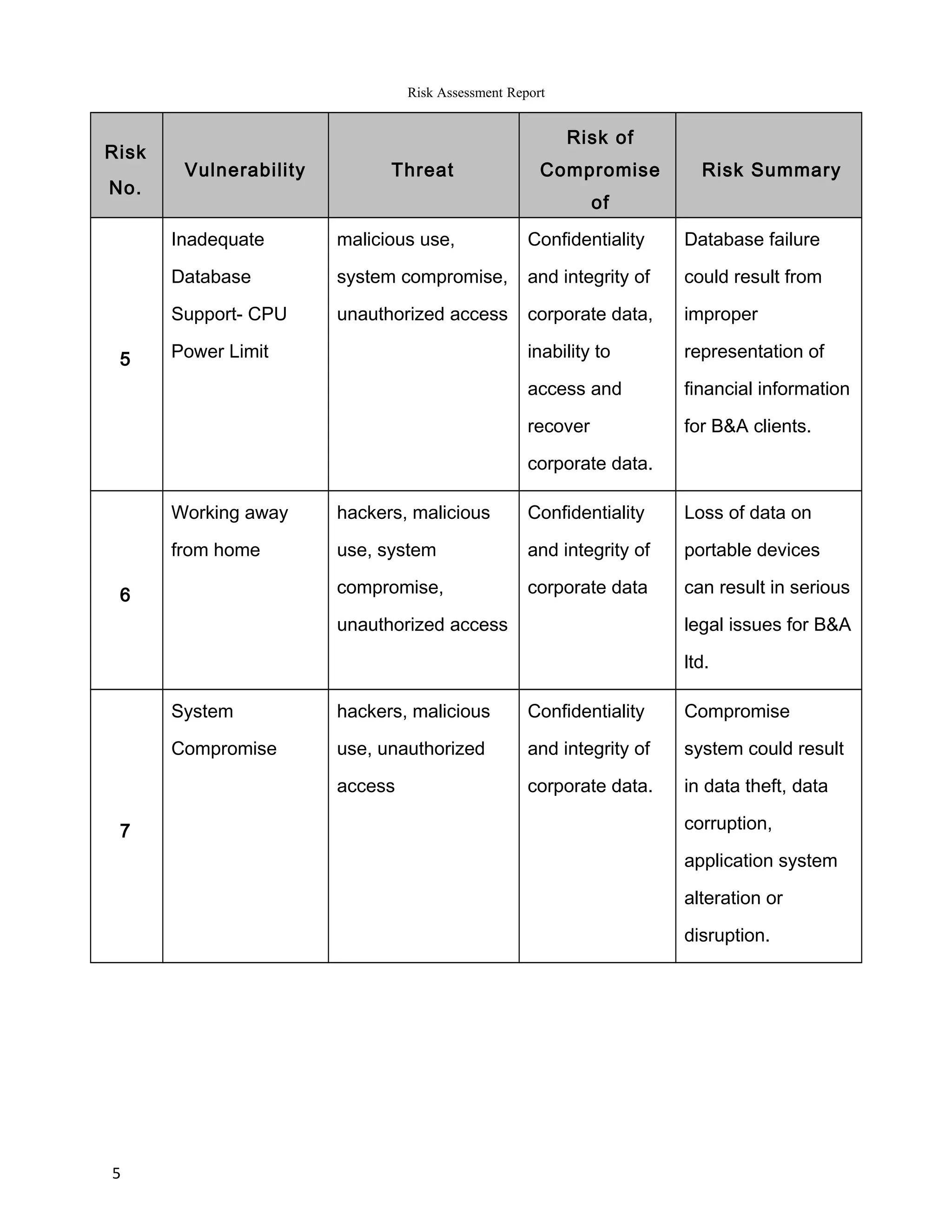
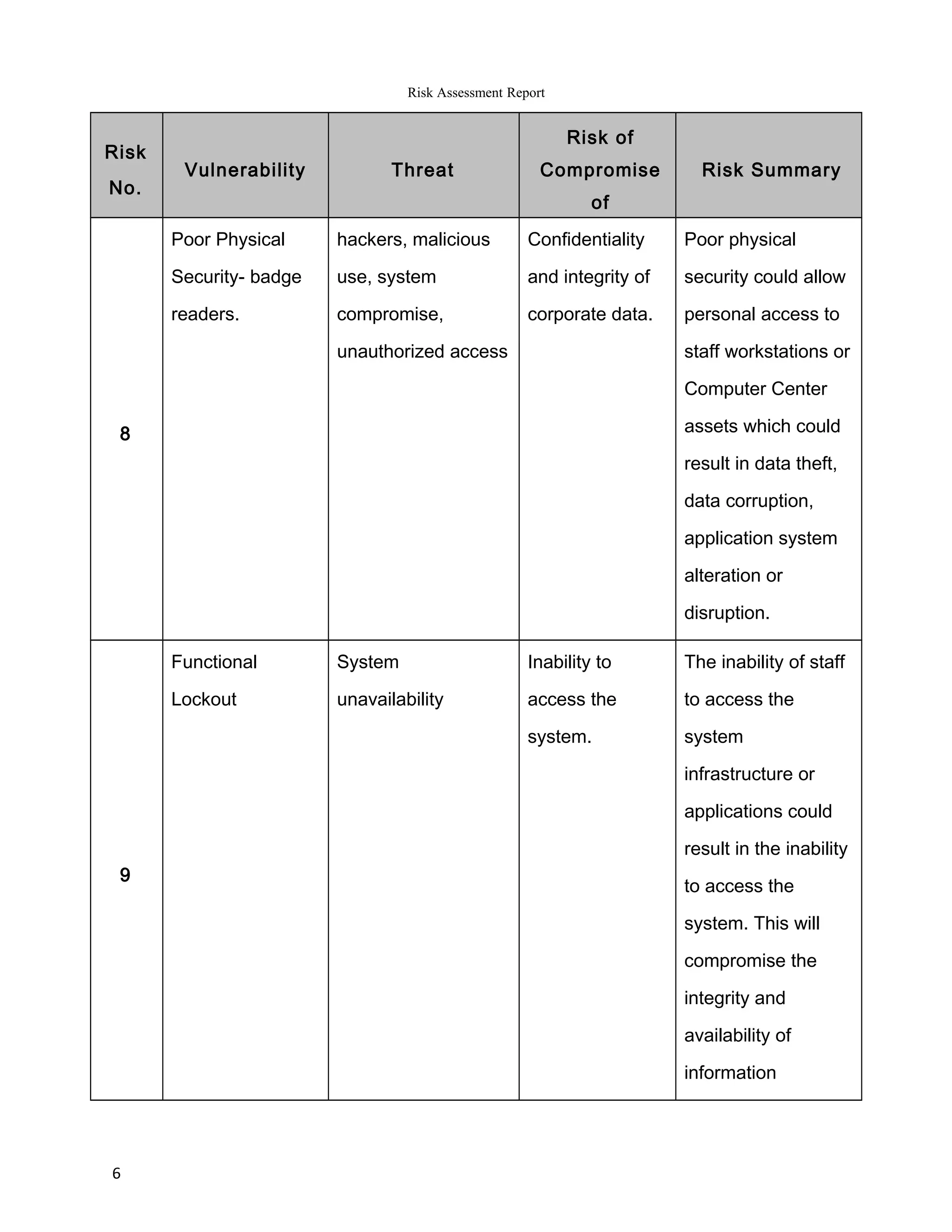
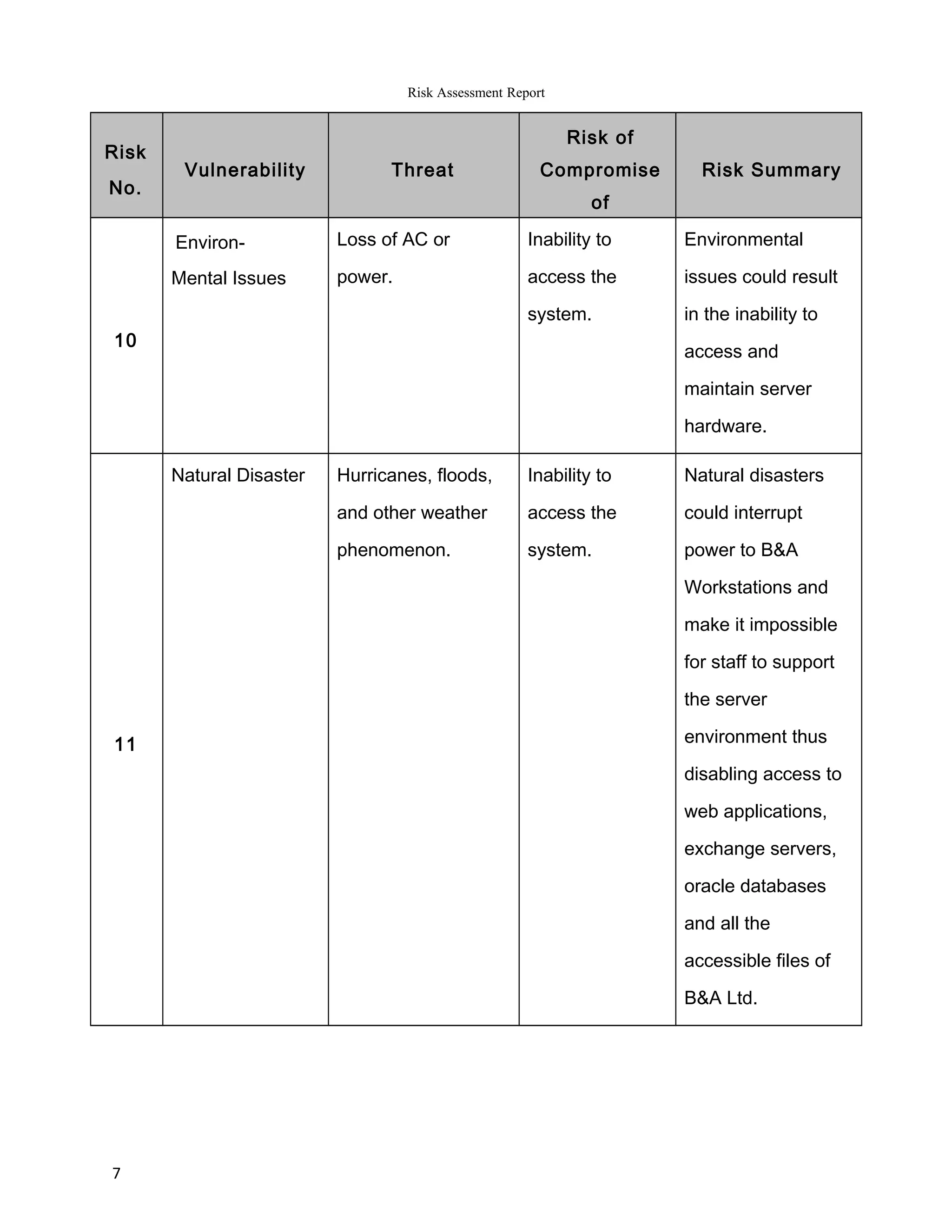
The report summarizes the results of a risk assessment of Barratt & Associates' information systems. It identifies 11 vulnerabilities in areas such as outdated operating systems, lack of firewalls, remote access monitoring, and physical security. For each vulnerability, it outlines the potential threats they pose, including computer crime, system compromise, and data loss or corruption. It then provides a risk summary, assessing the impact various threats could have on the confidentiality, integrity and availability of Barratt's data and systems. The report concludes by recommending measures to address the identified risks, such as using latest IT platforms and implementing comprehensive security controls.