The document provides an overview of a group presentation on cyber crime and security. It includes:
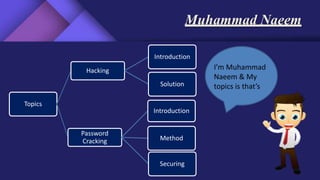
1. The names and topics of each group member: Shams will discuss the impact of technology and introduction; Ehtasham will cover viruses; Rehman will cover malware and trojan horses; Naeem will discuss hacking and password cracking.
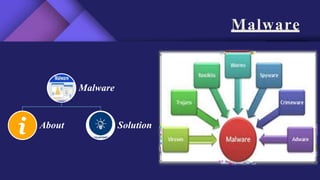
2. Introductions and outlines for the topics of viruses, malware, trojan horses, hacking, and password cracking.
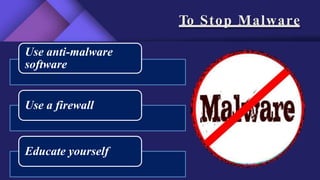
3. Suggested solutions and ways to prevent cyber threats such as using antivirus software, firewalls, strong passwords, and education.