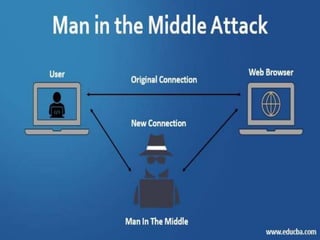
The document discusses cyber attacks, defining them as malicious activities aimed at damaging computer networks or systems using harmful code. It outlines various types of cyber attacks, including malware, denial of service (DoS and DDoS), password attacks, phishing, and man-in-the-middle attacks. Additionally, it highlights the advantages and disadvantages of cyber attacks, such as protecting personal data and potential financial theft.