- The Large Hadron Collider (LHC) Computing Grid is a worldwide federation of computing resources used for particle physics research at CERN. It consists of a tiered system with over 160 sites across 39 countries.
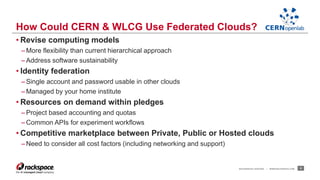
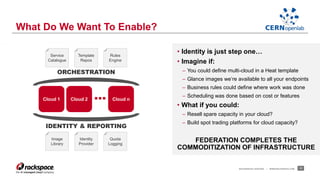
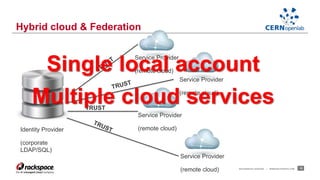
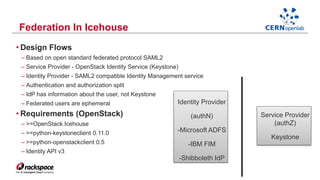
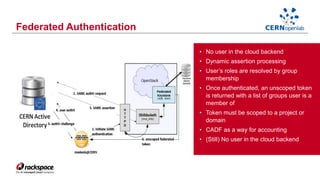
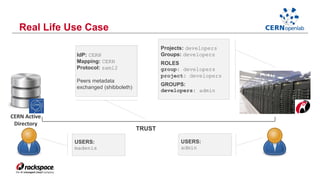
- Federating cloud resources could provide more flexibility than the current hierarchical model and help address issues like software sustainability. Identity federation would allow single sign-on across clouds managed by different institutions.
- A CERN OpenLab project demonstrated federation between Rackspace's private cloud and a third-party OpenStack cloud, laying the groundwork for further work on federation.















![RACKSPACE® HOSTING | WWW.RACKSPACE.COM 23
Mapping Engine
Saml
Assertion
Keystone
credentials
LOGIN: madenis
LANGUAGE: EN
DEPARTMENT: IT/OIS
FULLNAME: Marek Denis
BLDGS:31;513;40
[
{ "local”:
[ { "user": { "name”: "{0}" } } ],
"remote”:
[ { "type": "LOGIN" } ]
},
{ "local”:
[ { "group": { "id": „devs" } } ],
"remote”:
[ { "type":“BLDGS”,"any_one_of":["1", "2", "31"] } ]
}
]
{
“user_id”:
“madenis”
“groups”: [“devs”]
}](https://image.slidesharecdn.com/openstackparis-cernrackspace-141126055435-conversion-gate02/85/OpenStack-Paris-2014-Federation-are-we-there-yet-23-320.jpg)
![RACKSPACE® HOSTING | WWW.RACKSPACE.COM 24
Mapping Rules – A Closer Look
[
{
"local": [
{ "user": {"name": "{0}"} }
],
"remote": [
{ "type": "ADFS_LOGIN” }
]
},
{
"local": [
{
"group": { "id": "developers” }
}
],
"remote":[
{
"type": "ADFS_DEP”,
"any_one_of": ["IT/OIS"]
},
{
"type": "ADFS_LANGUAGE",
"any_one_of": ["PL", "EN"]
}
]
}
]
Rule
Map 0th attribute from ‘remote’
Use ADFS_LOGIN
Rule
Assign group “developers”
If ADFS_DEP is “IT/OIS”…
.... and ADFS_LANGUAGE is either “PL” or “EN”](https://image.slidesharecdn.com/openstackparis-cernrackspace-141126055435-conversion-gate02/85/OpenStack-Paris-2014-Federation-are-we-there-yet-24-320.jpg)
![• JSON
• List of rules
• Rule is a dictionary
• Each rule has two items:
– local
– remote
• Rules can be concatenated
• One rule must map user id
– Required for federated users identification
– Keystone fails with HTTP 401 (Unauthorized) if username is not defined
• Assertion attributes can be ‘;’ separated (e.g. list of users groups)
• Mapping keywords: any_one_of, not_any_of
• Mapping rules must be changed to reflect group/projects changes
RACKSPACE® HOSTING | WWW.RACKSPACE.COM 25
Mapping Rules
{
"local": [
{ "user": {"name": "{0}"}},
{"group": { "id": "developers"}}
],
"remote":[
{ "type": "ADFS_DEP",
"any_one_of": ["IT/OIS"]
},
]
}](https://image.slidesharecdn.com/openstackparis-cernrackspace-141126055435-conversion-gate02/85/OpenStack-Paris-2014-Federation-are-we-there-yet-25-320.jpg)



