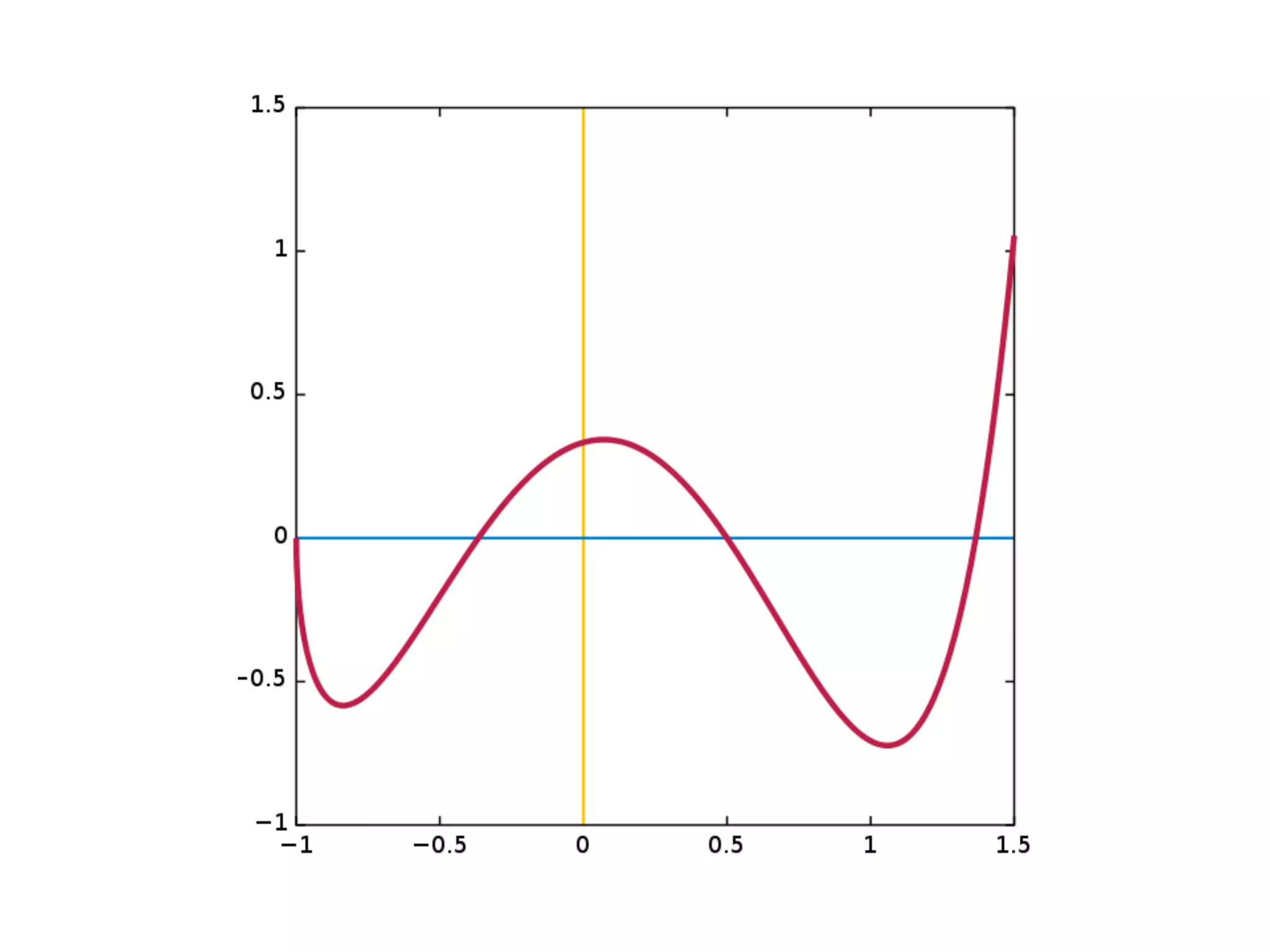
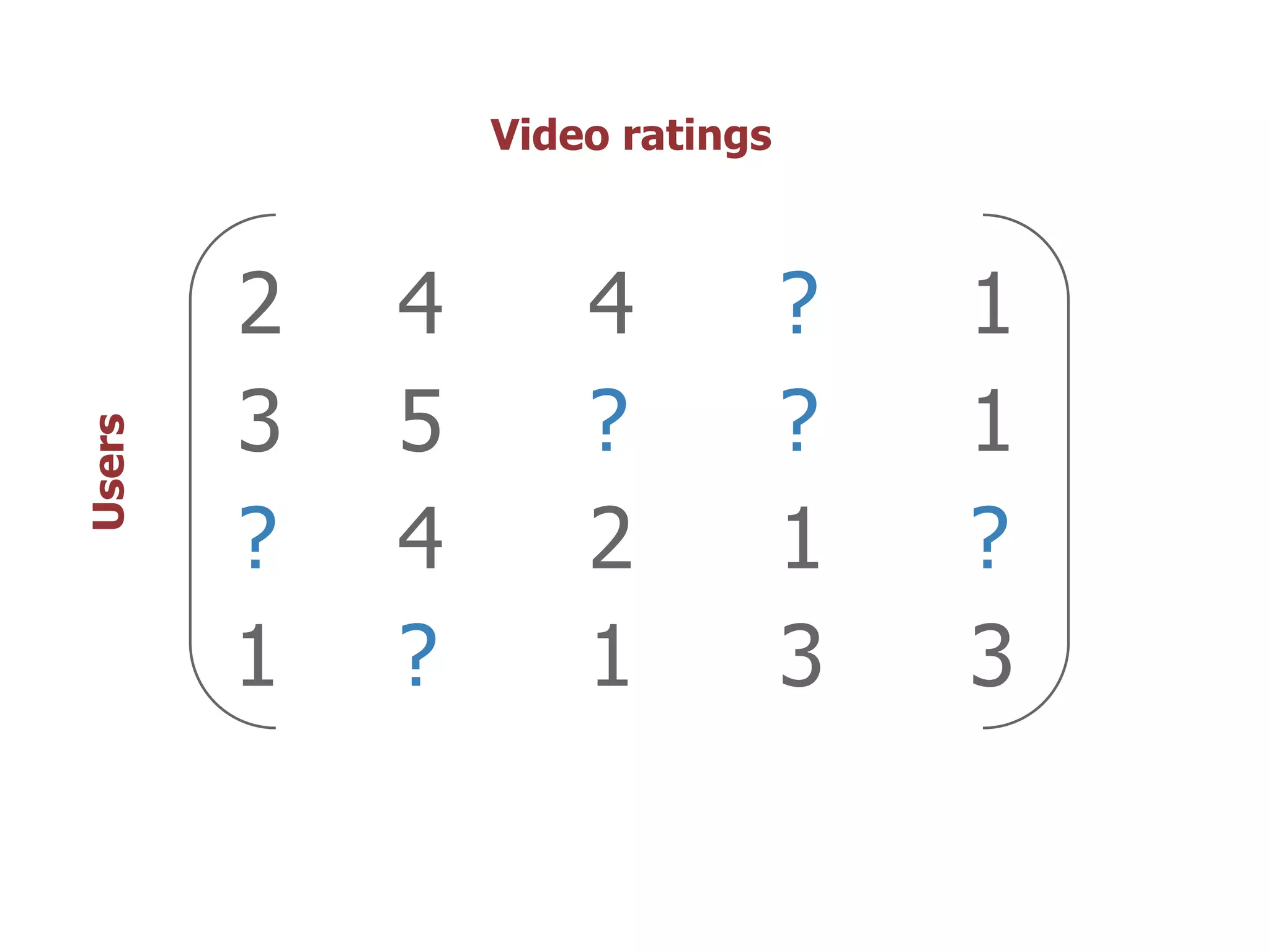
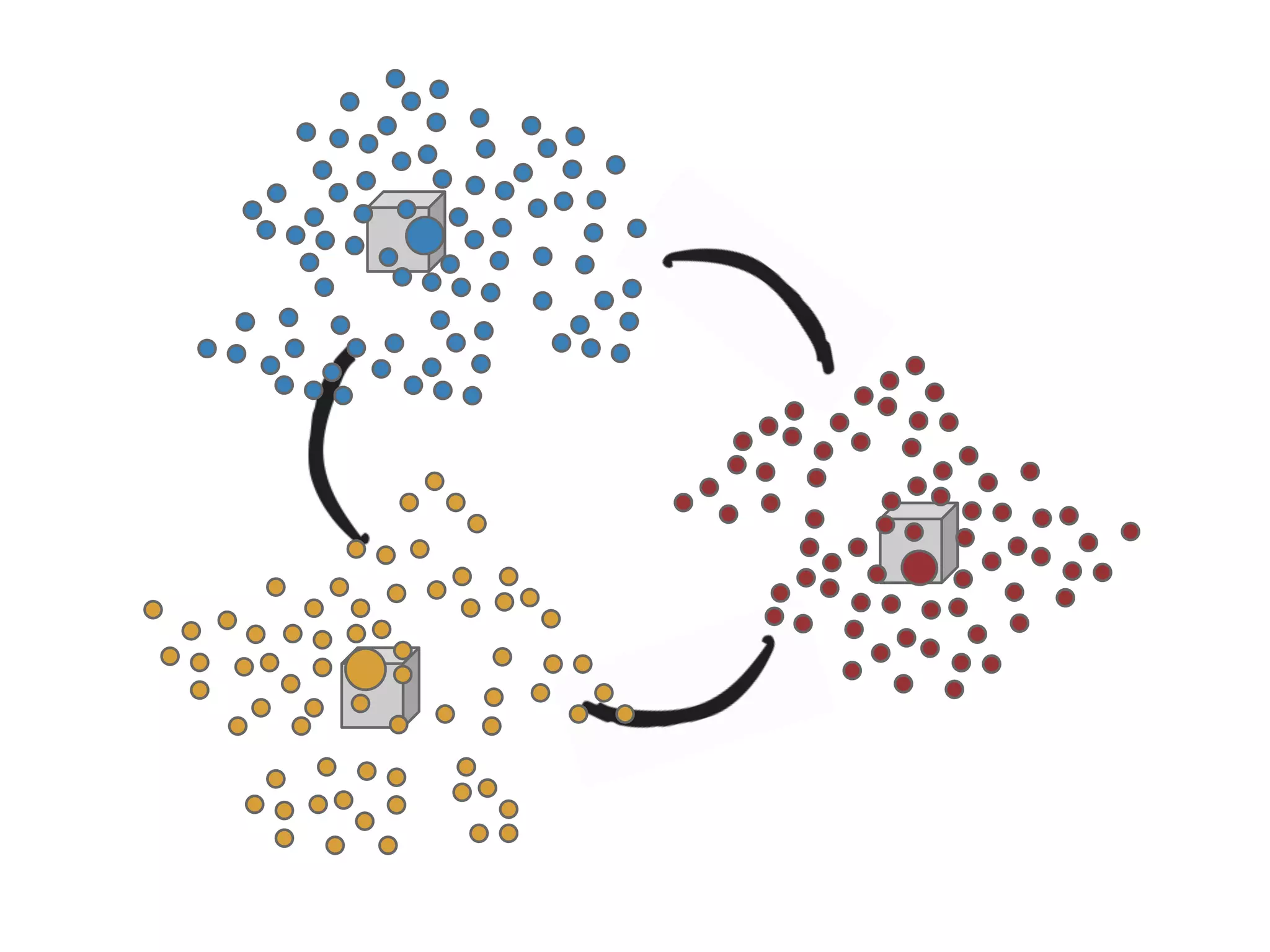
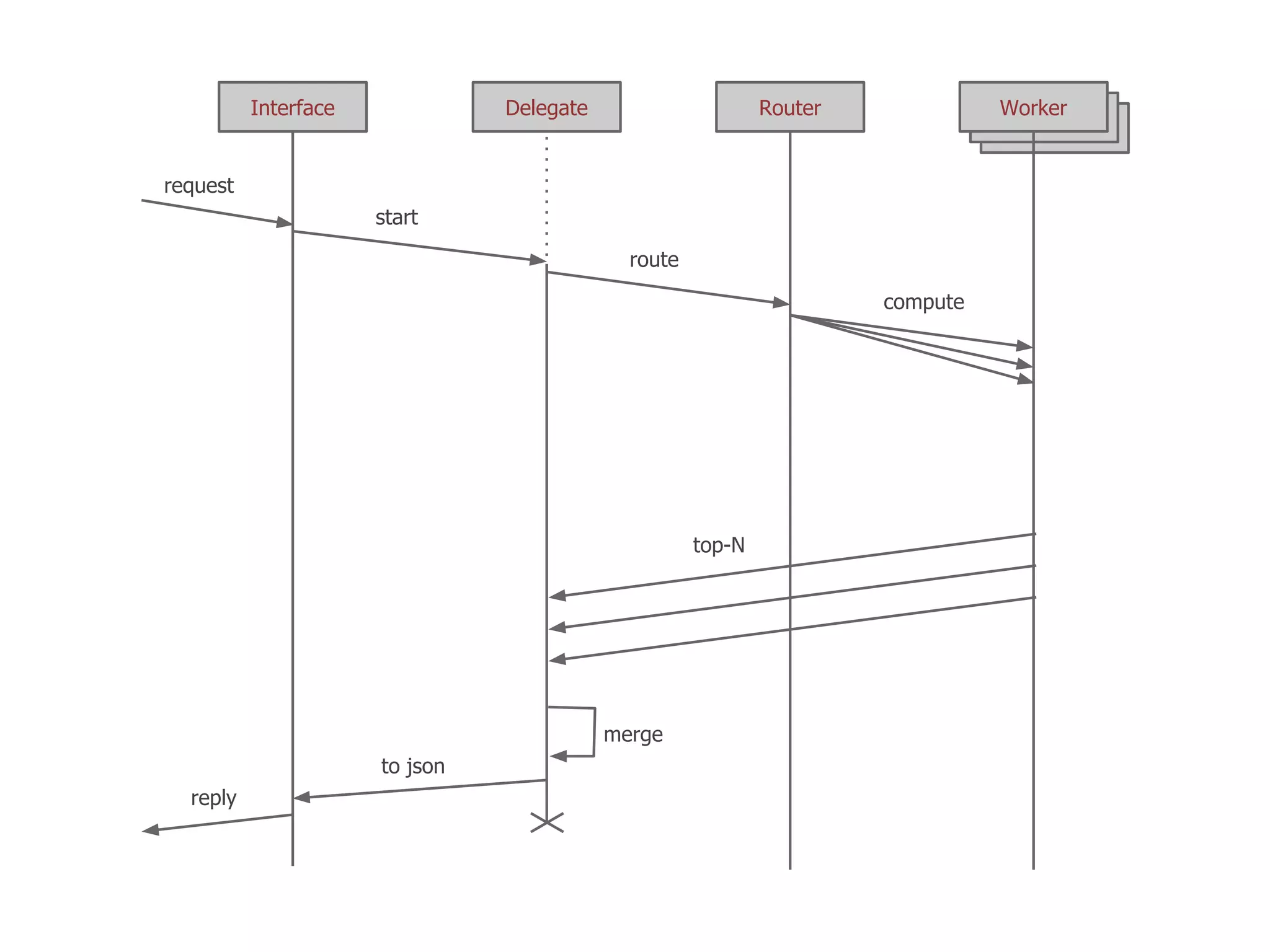
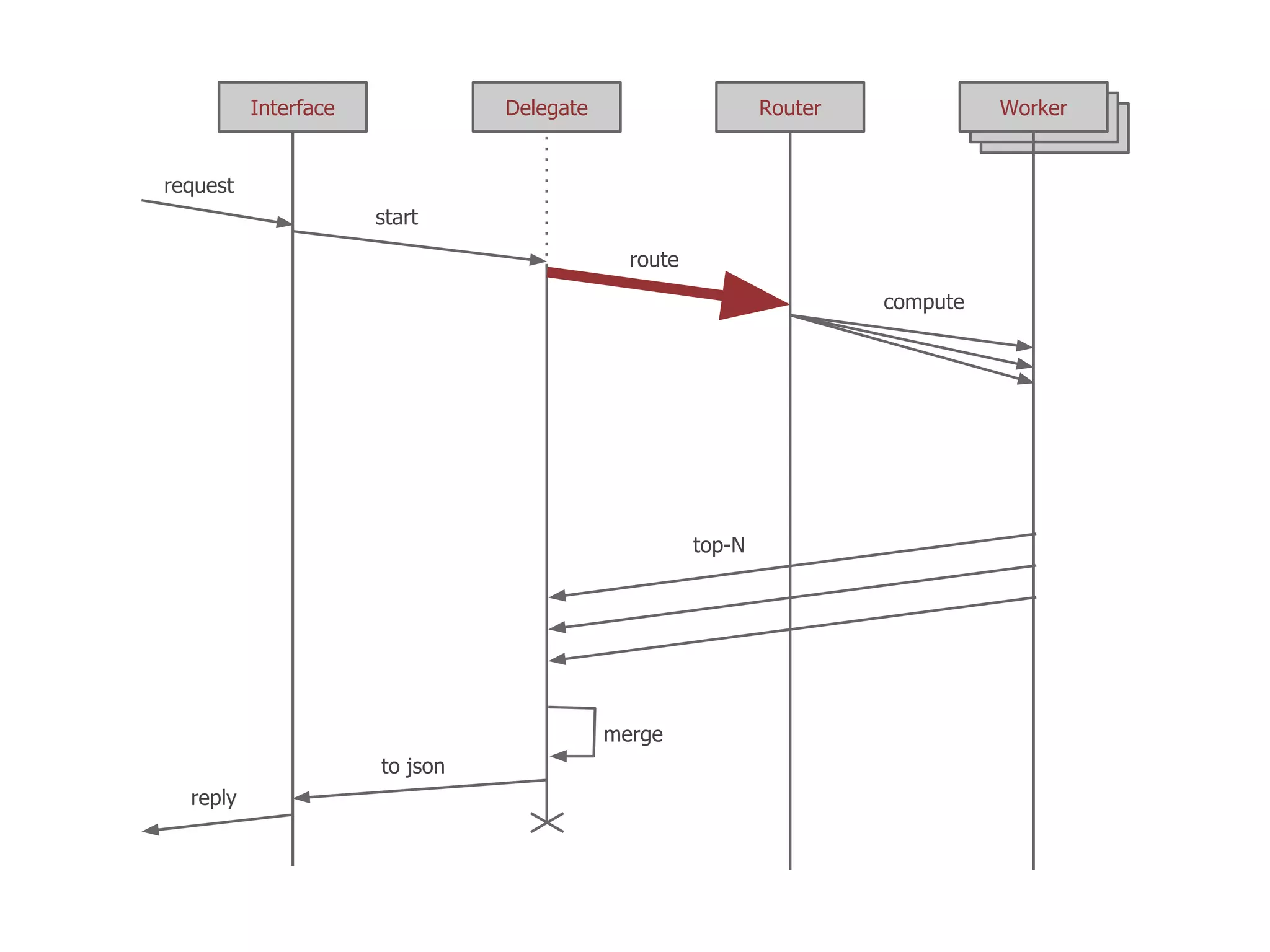
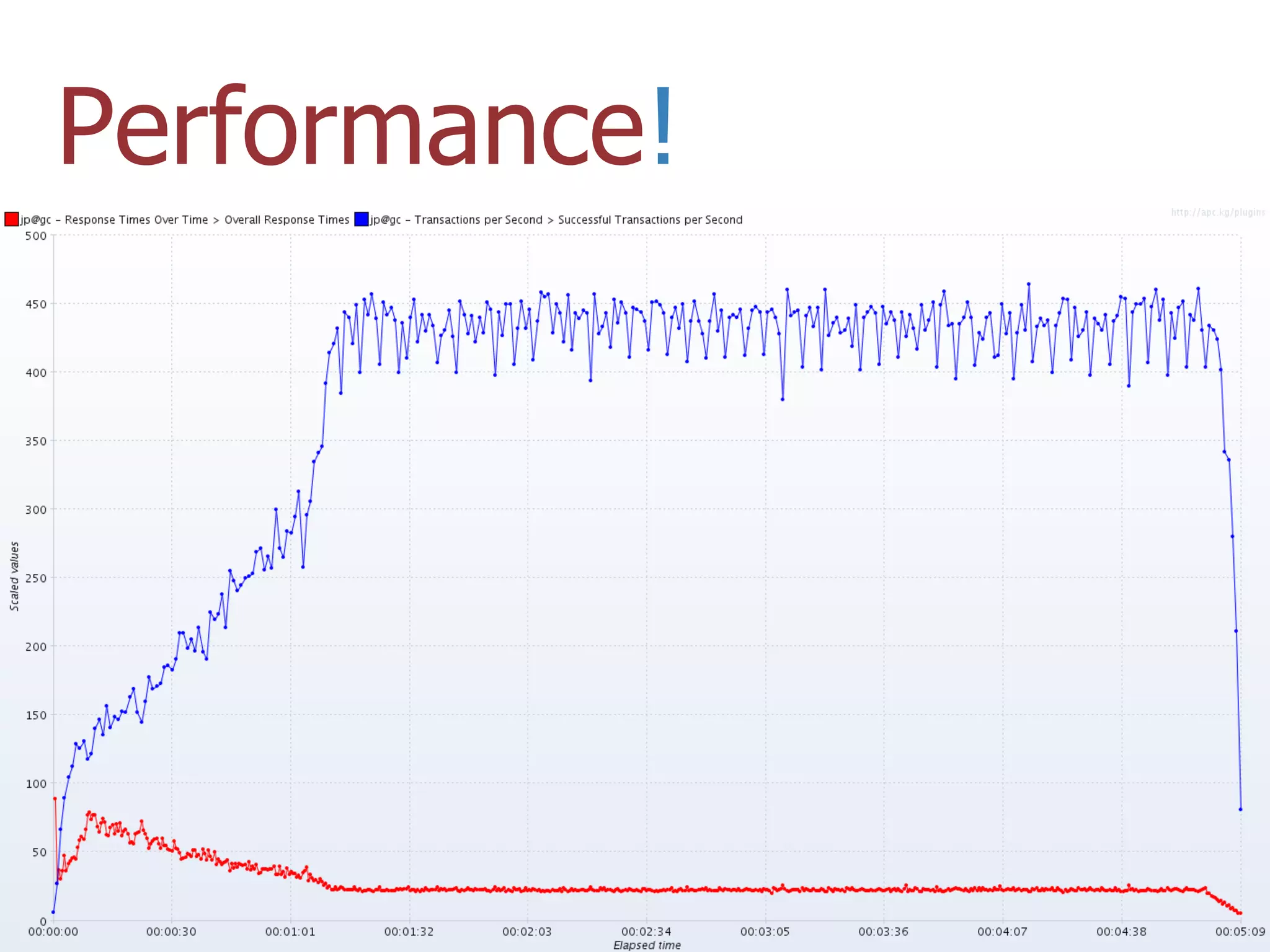
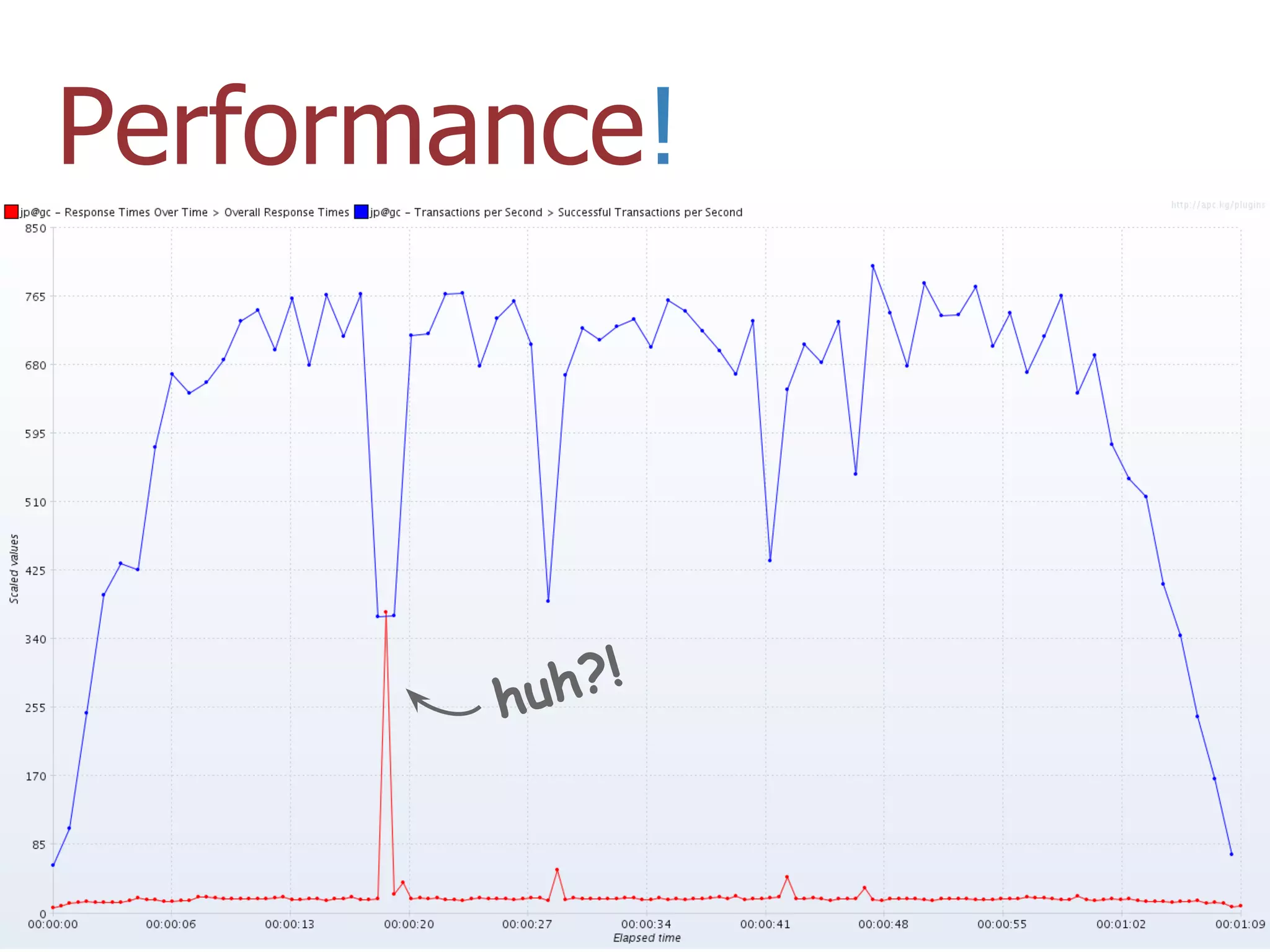
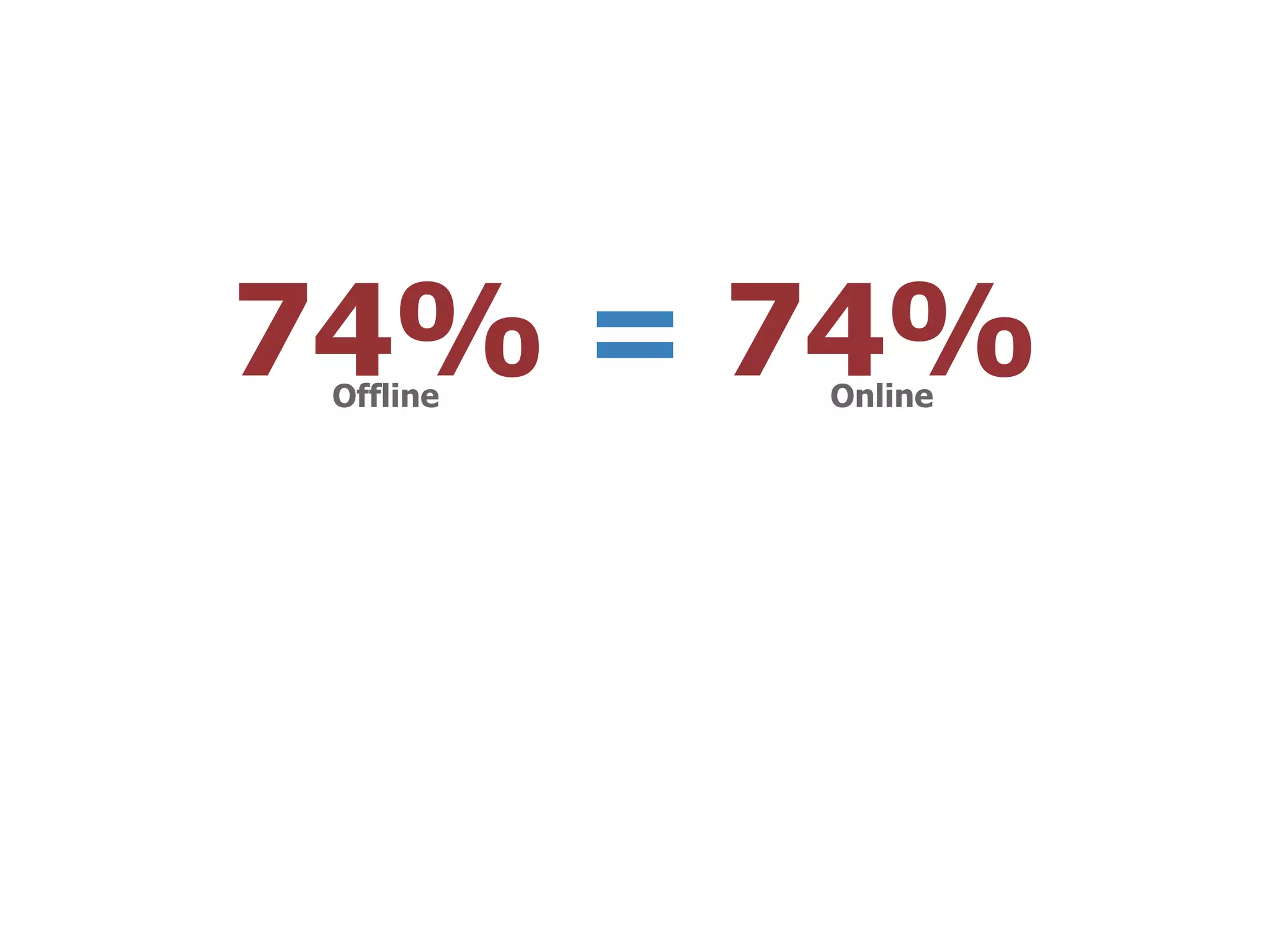
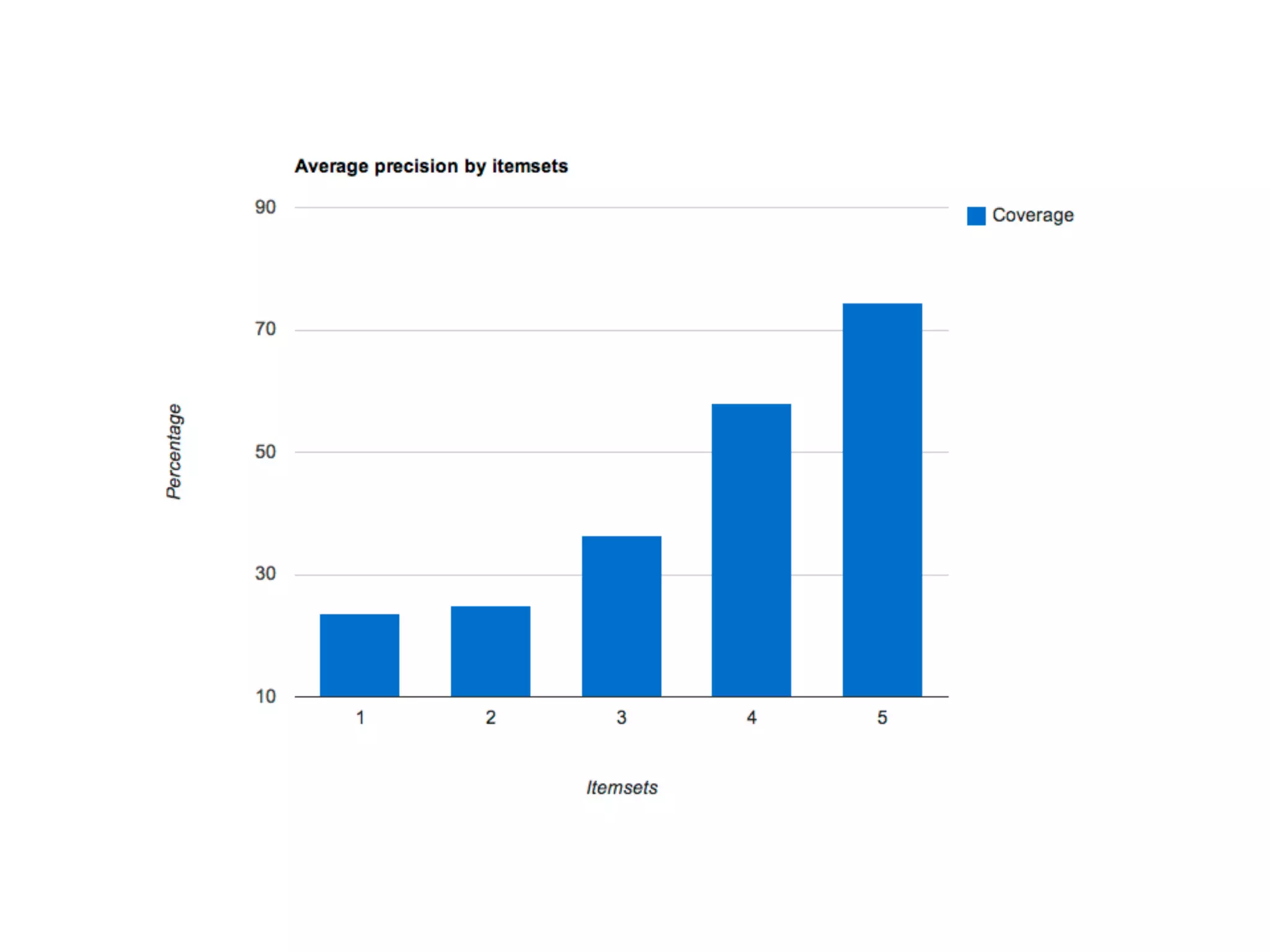
The thesis presentation discusses the challenges of providing online movie recommendations at scale using matrix factorization, highlighting that 75% of daily movie starts come from recommendations. It outlines the performance of a system tested on 1 million items and emphasizes the need for balanced clusters and efficient data handling. The document concludes with a summary of setup and performance metrics, indicating a successful implementation with 74% effectiveness.