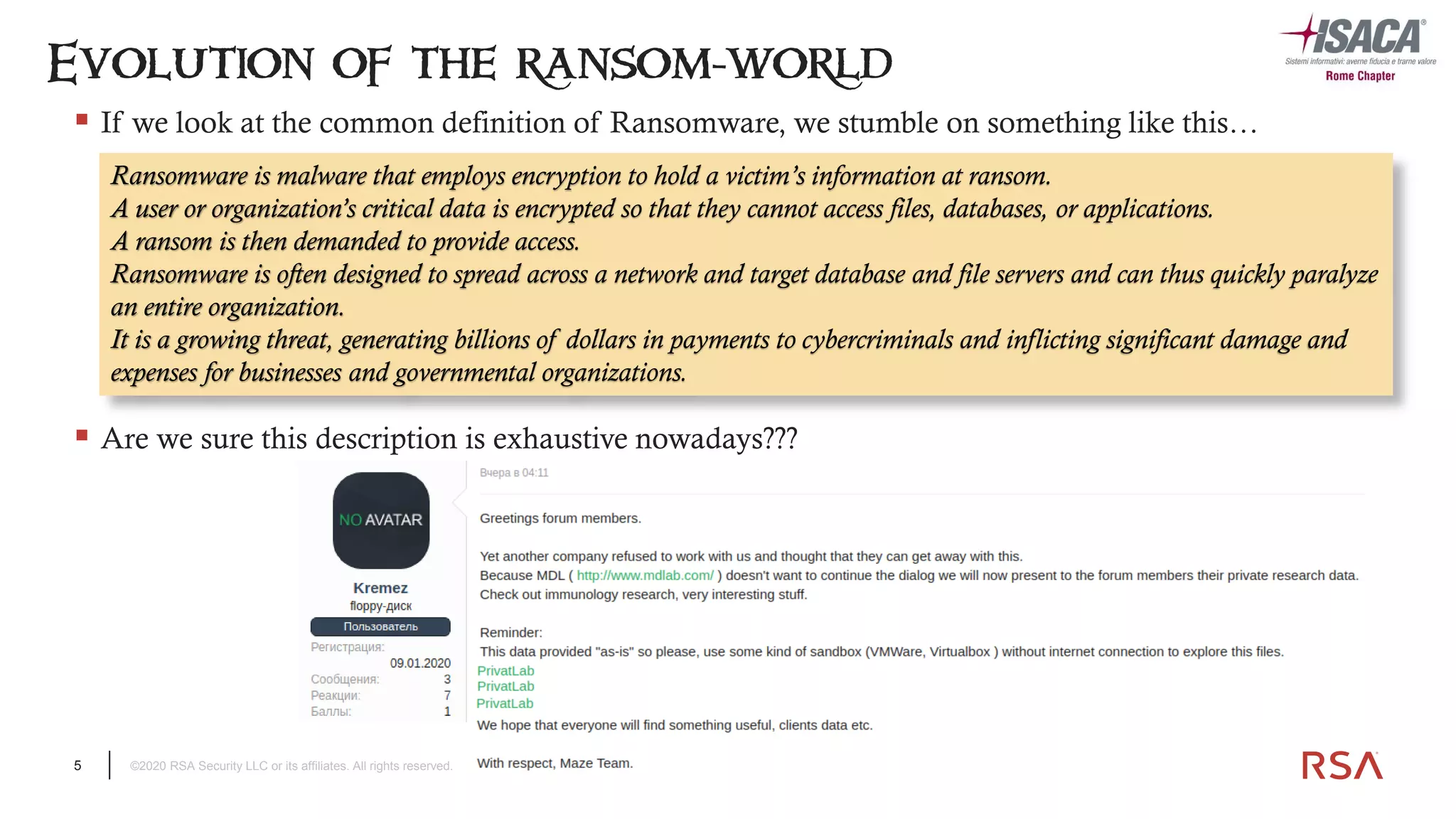
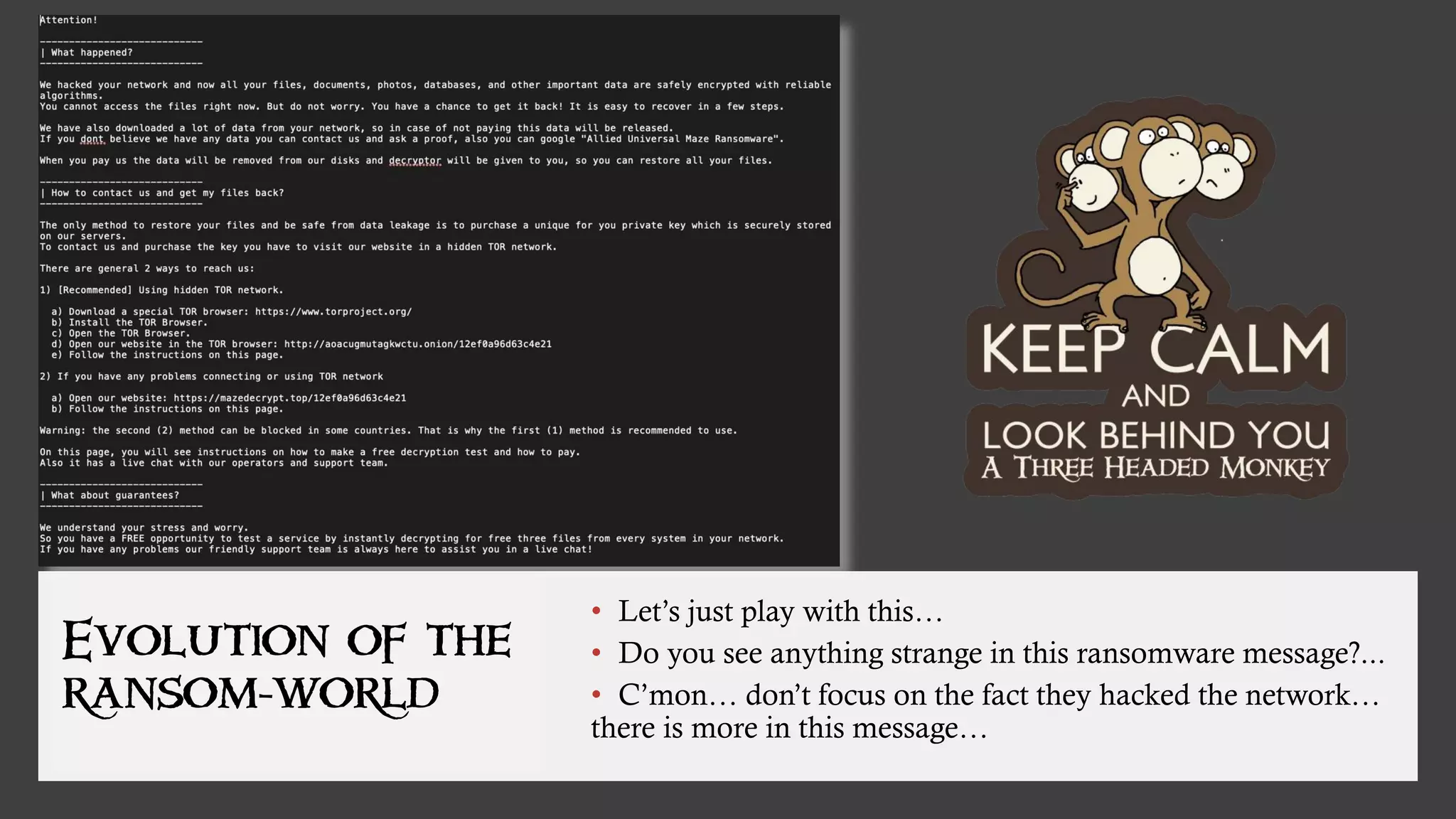
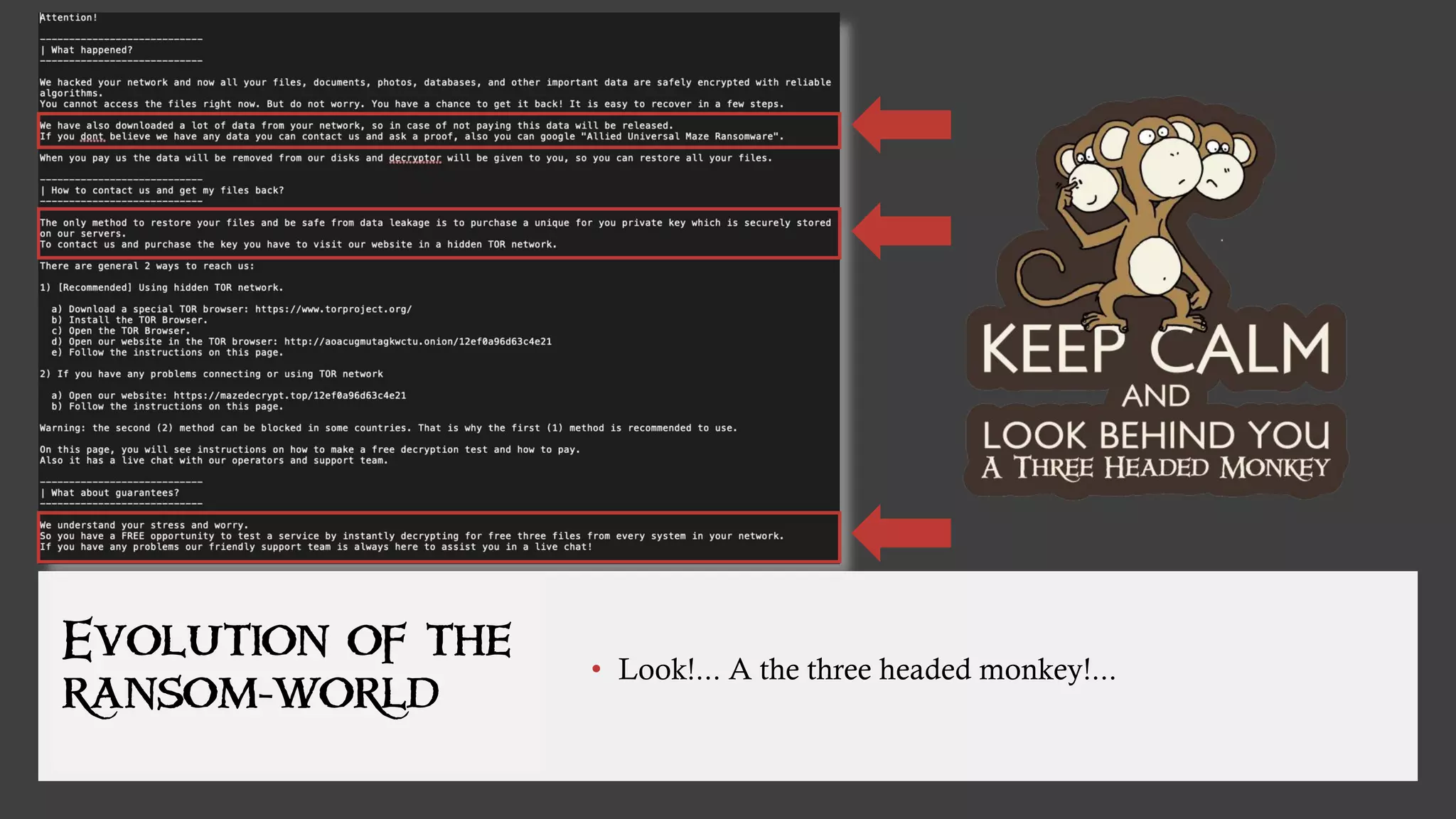
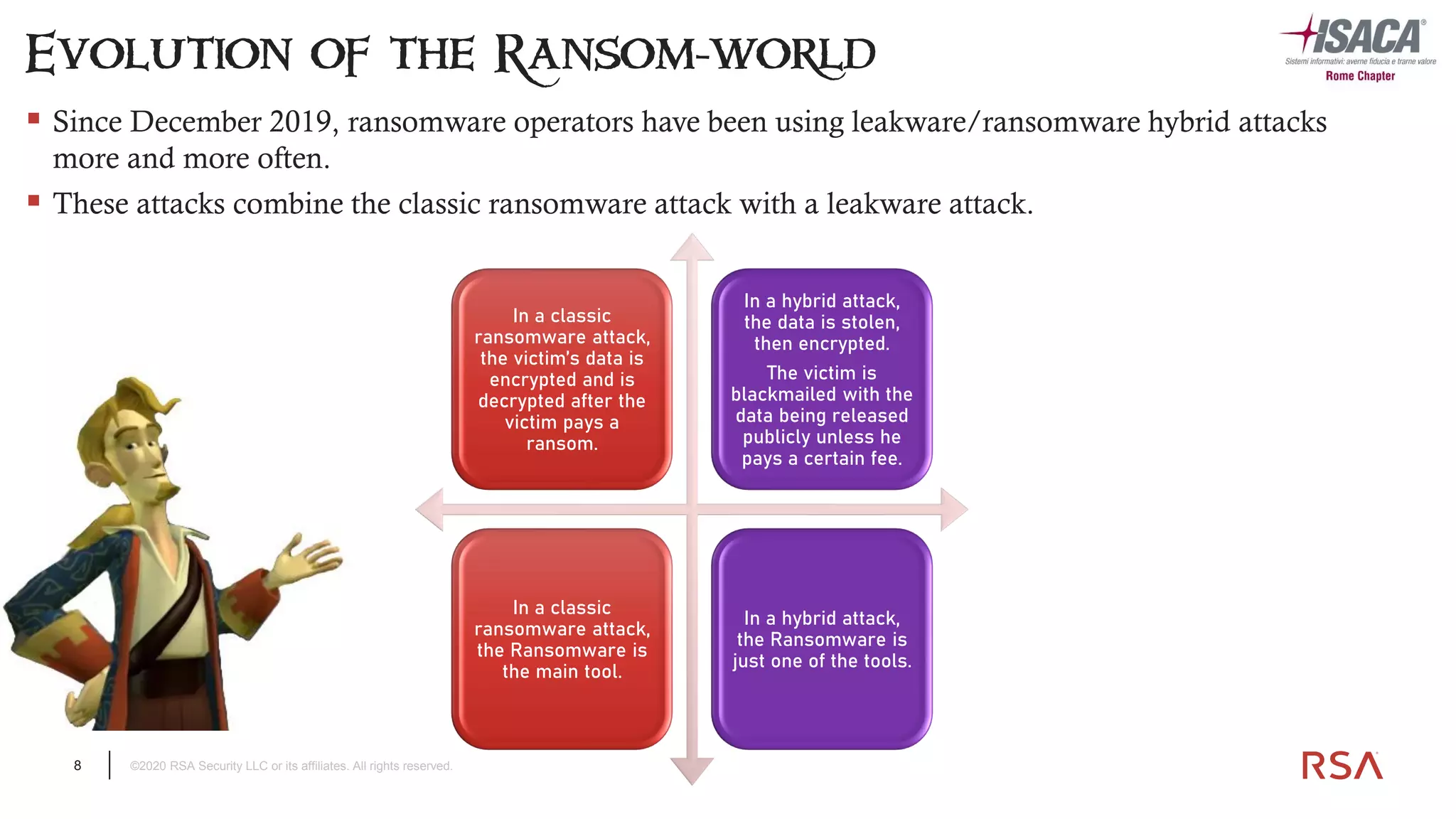
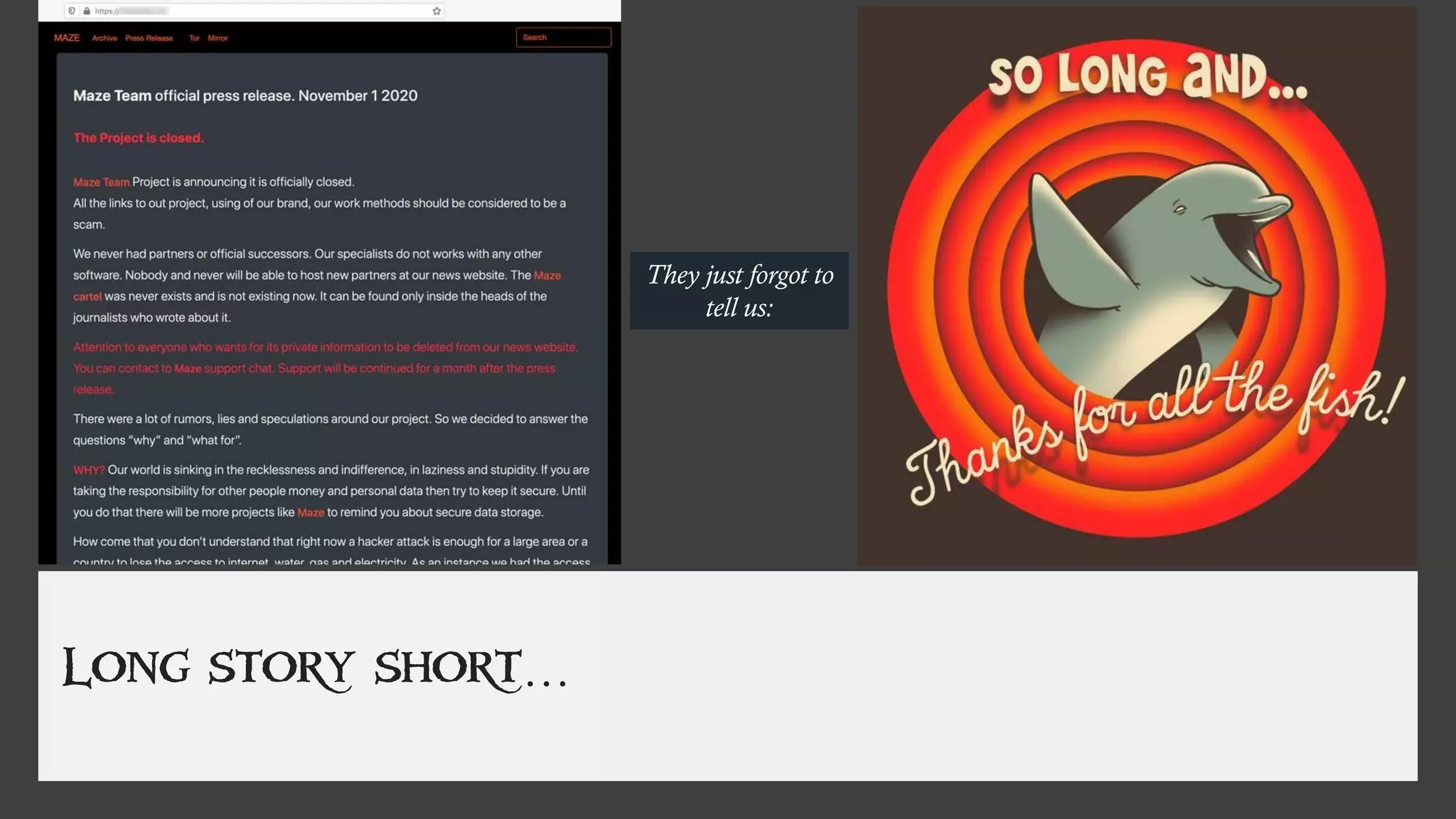
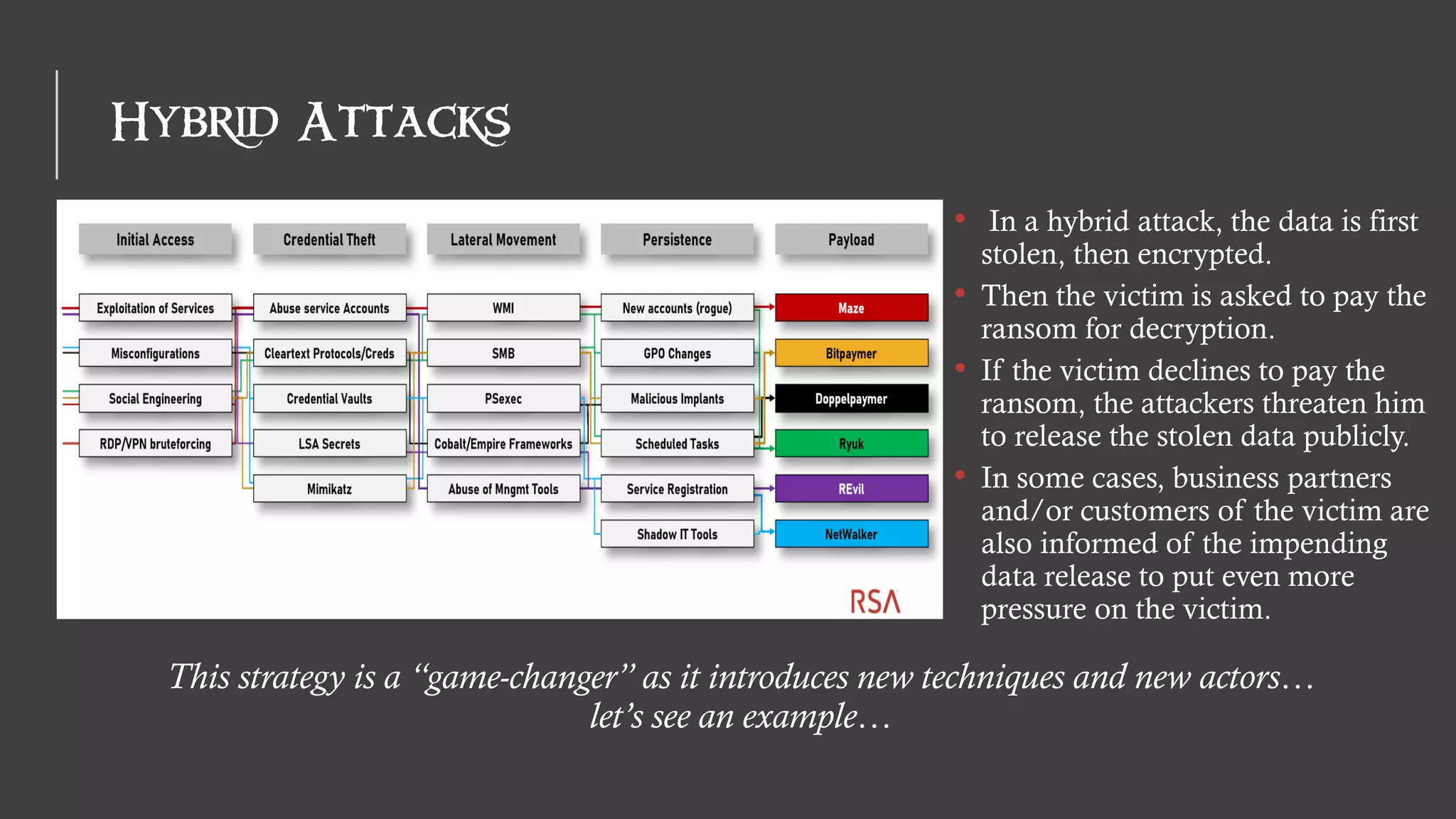
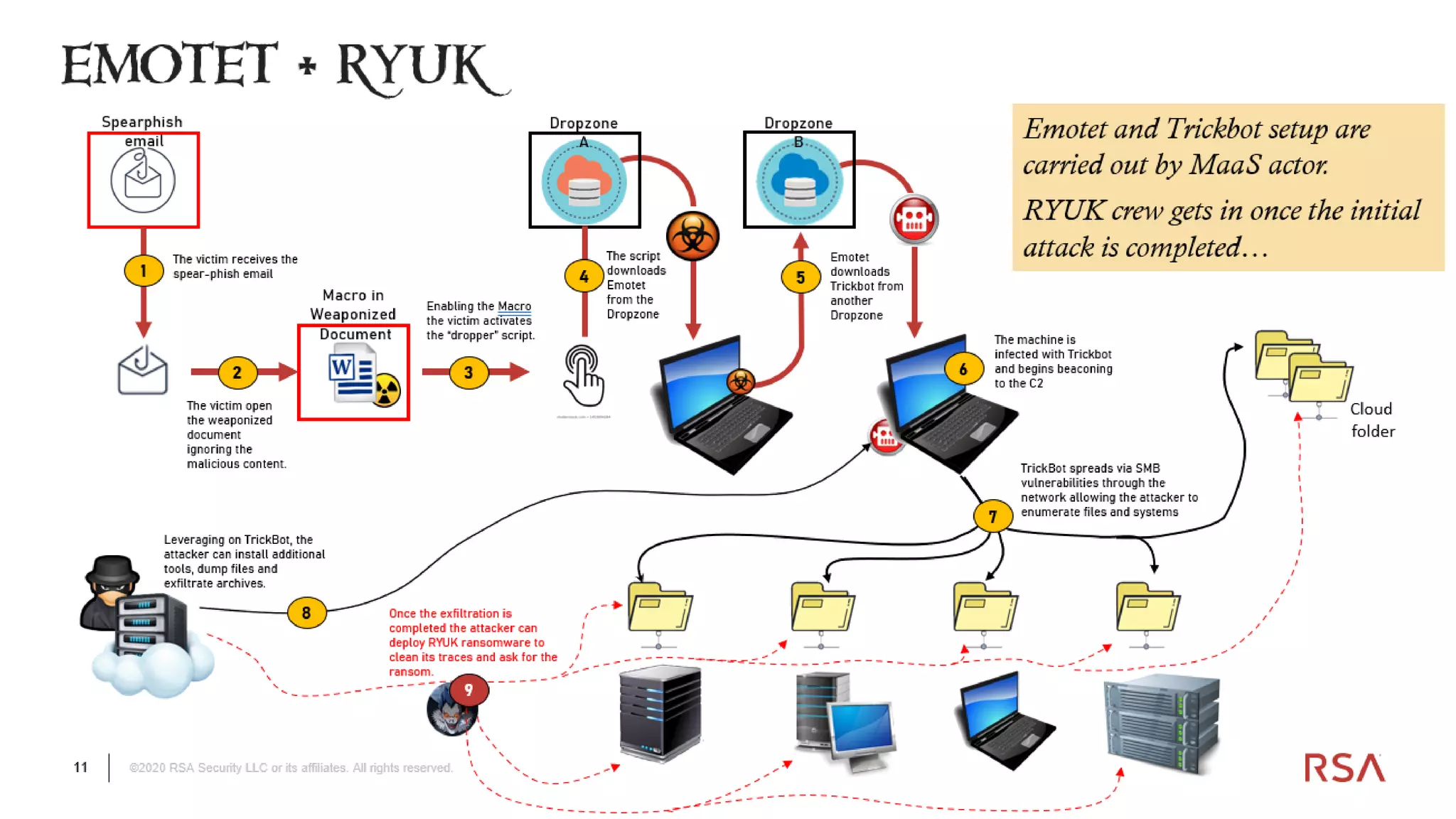
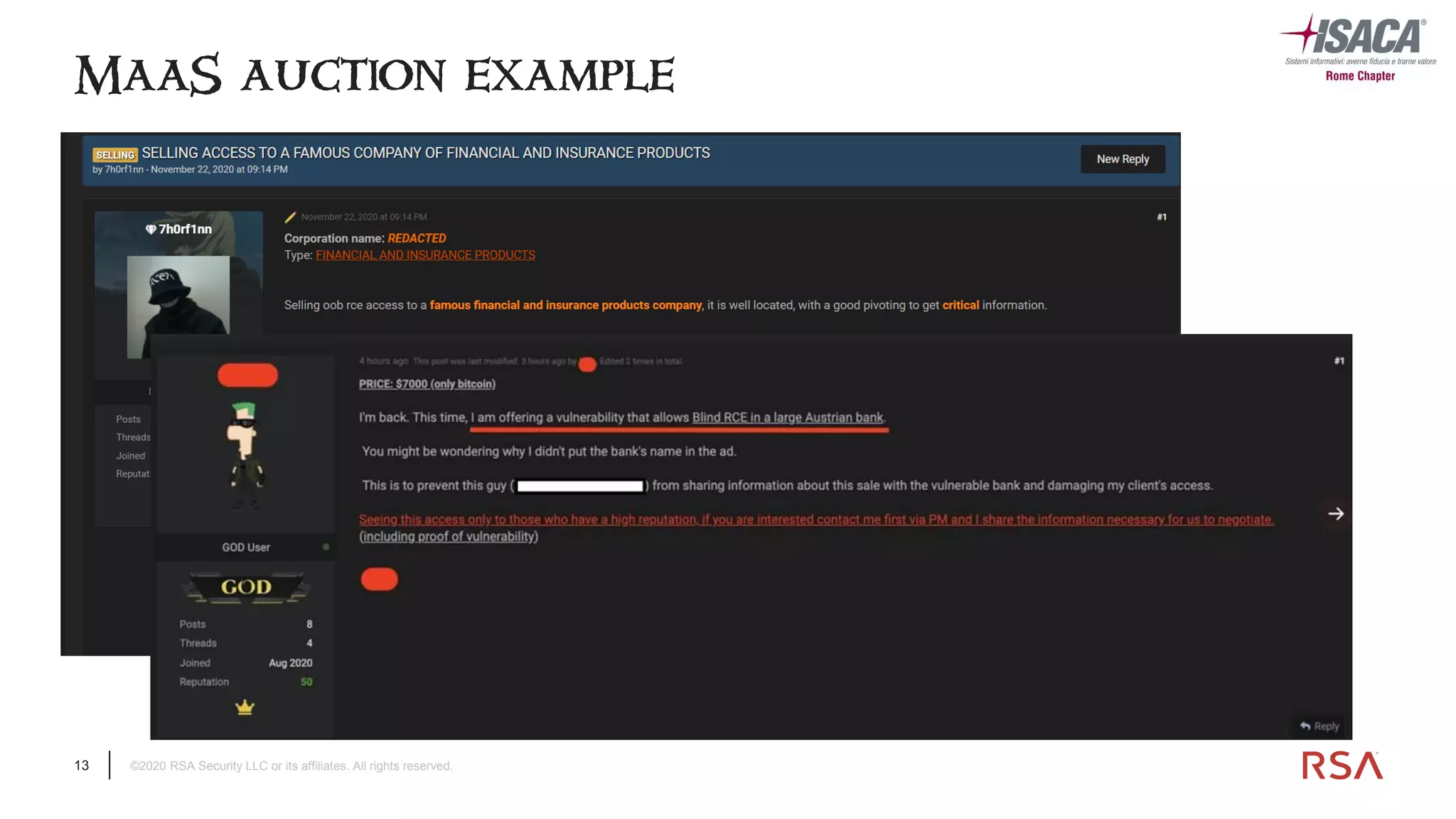
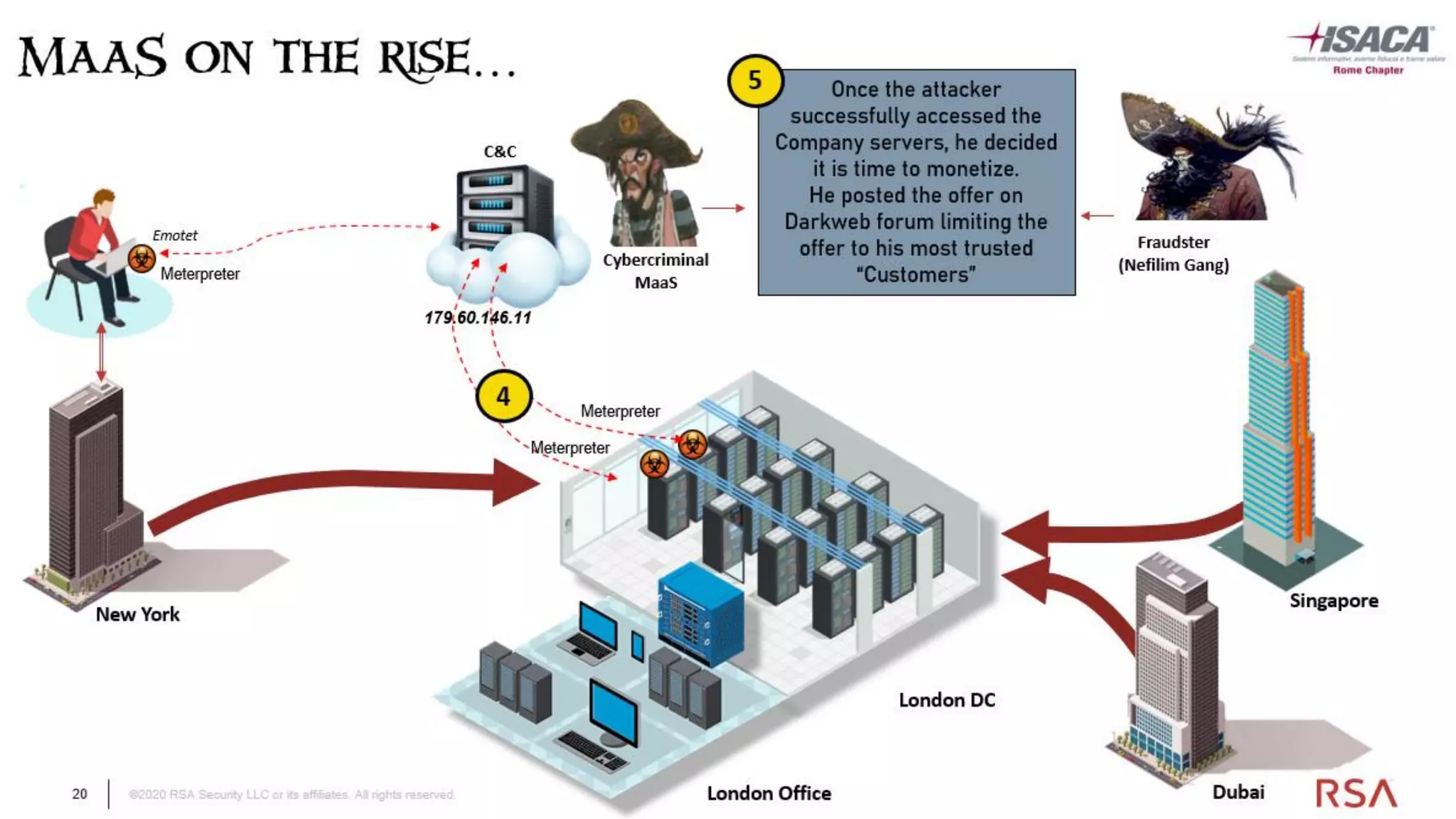
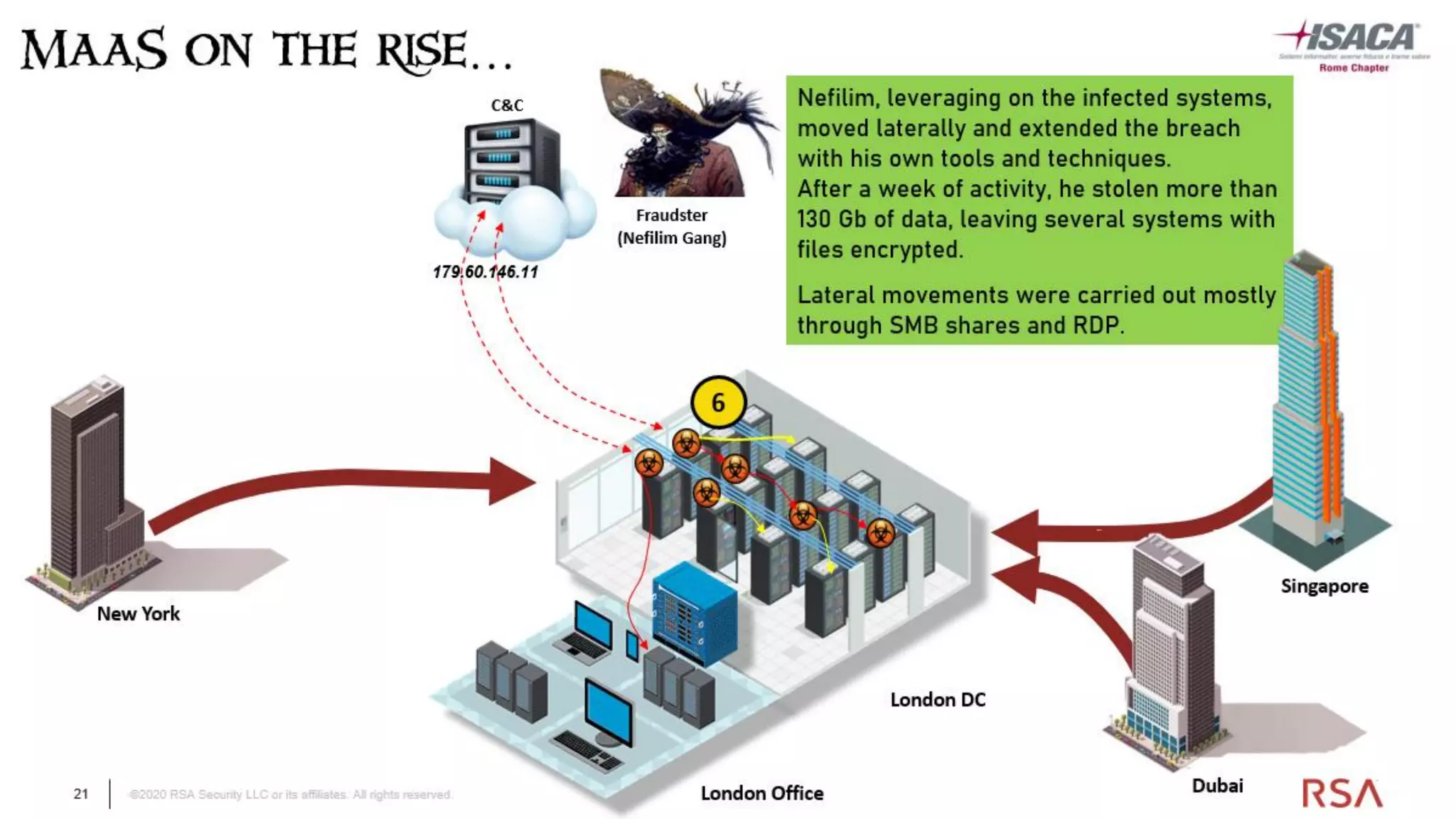
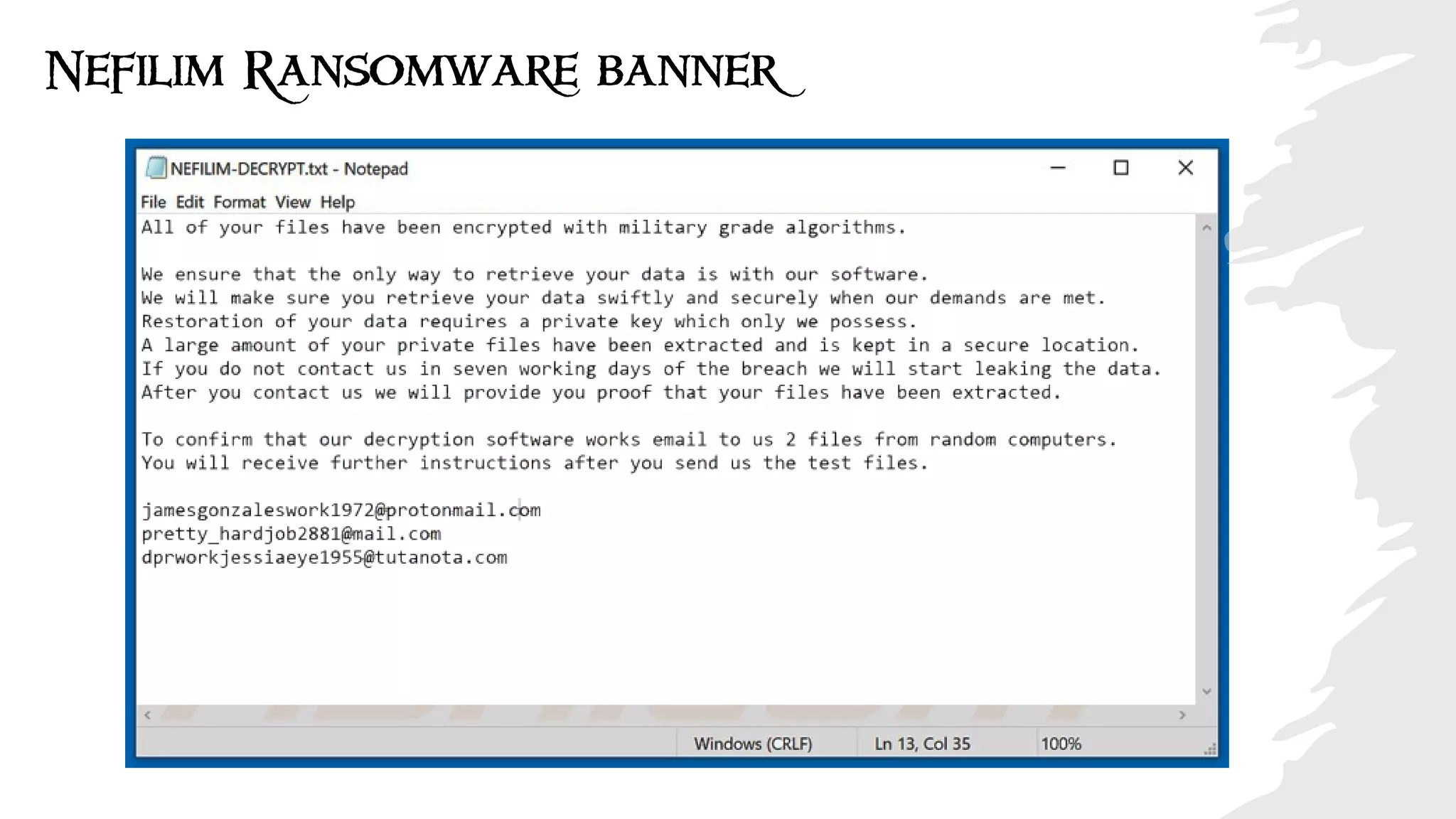
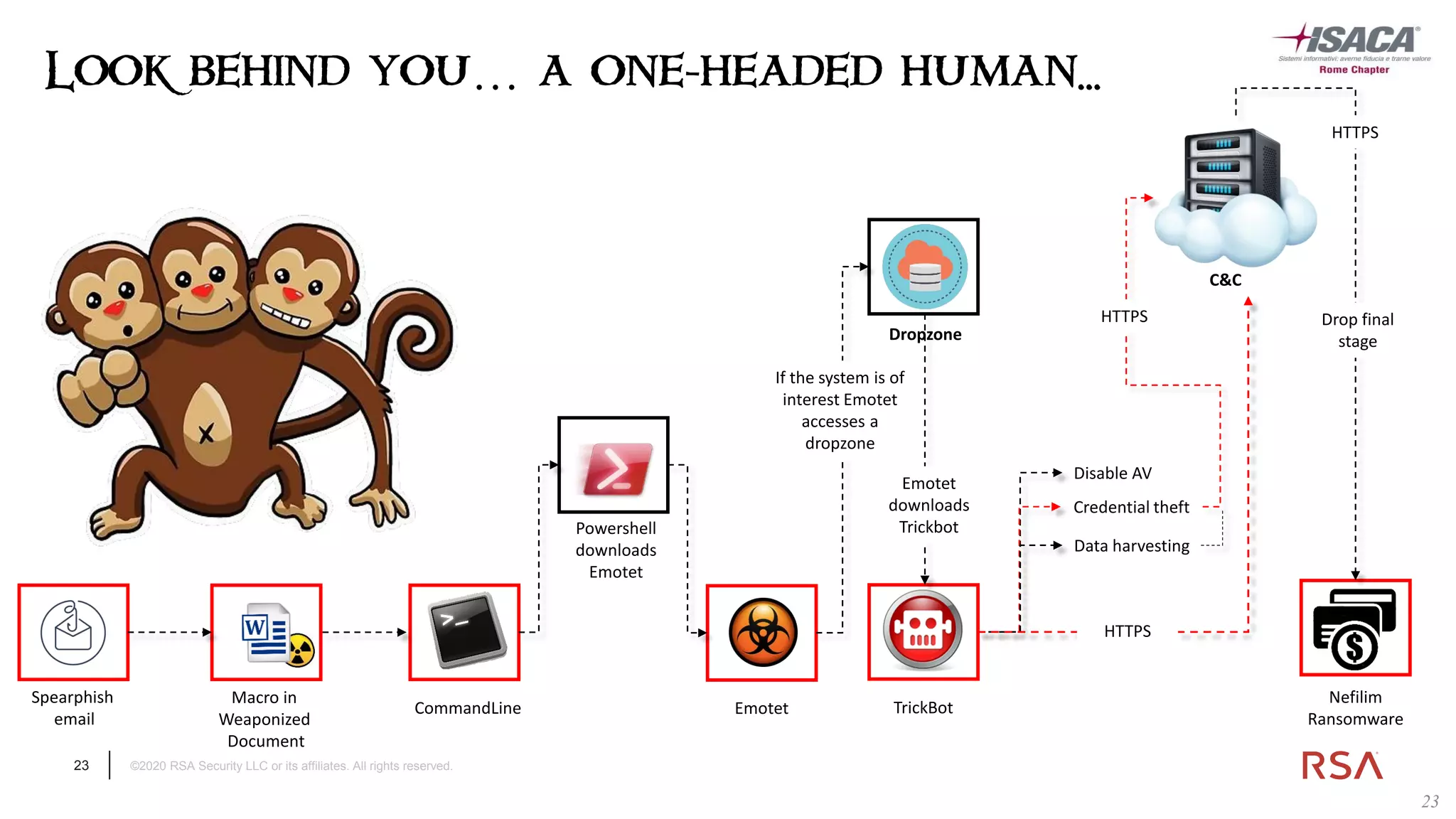
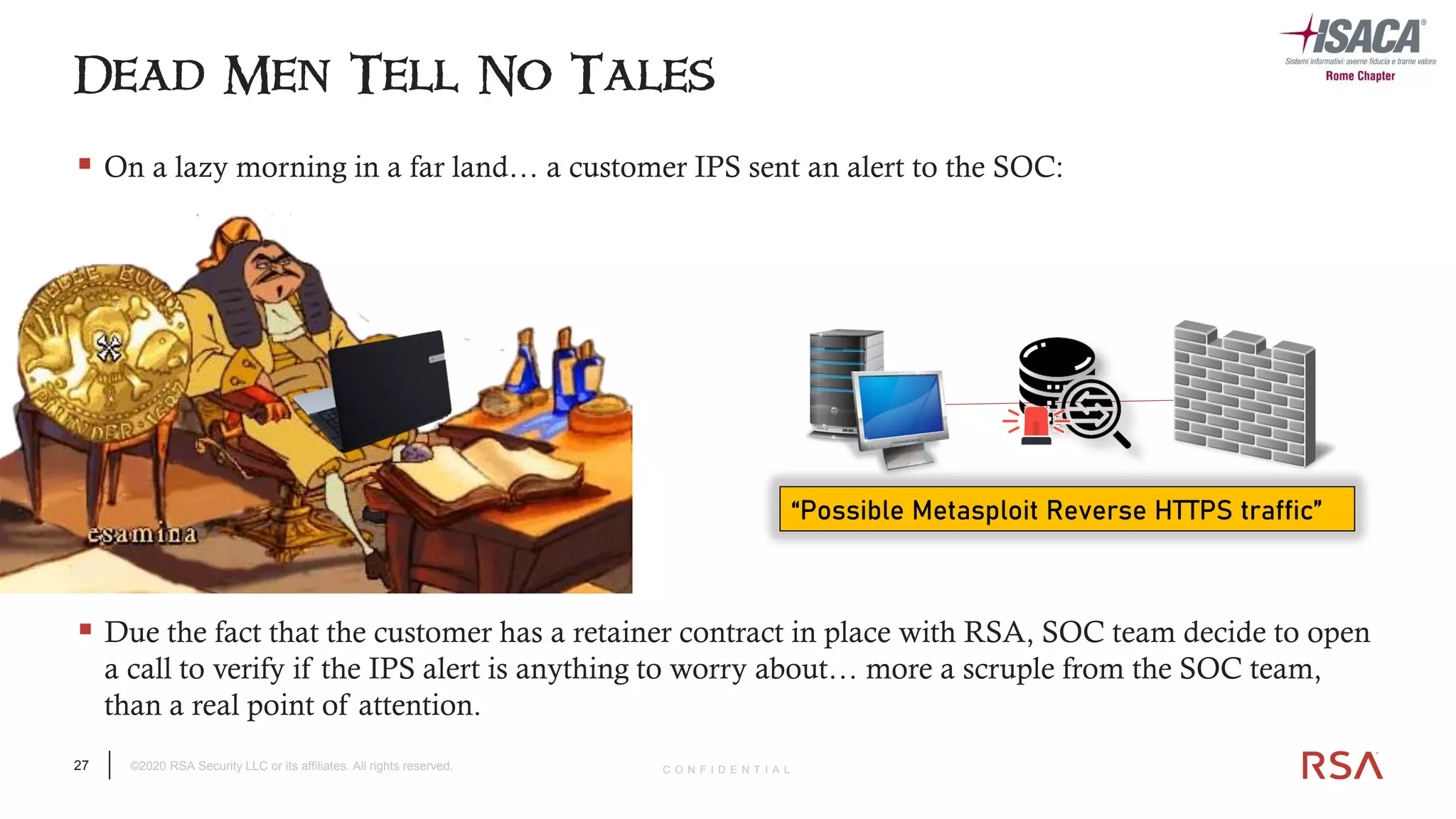
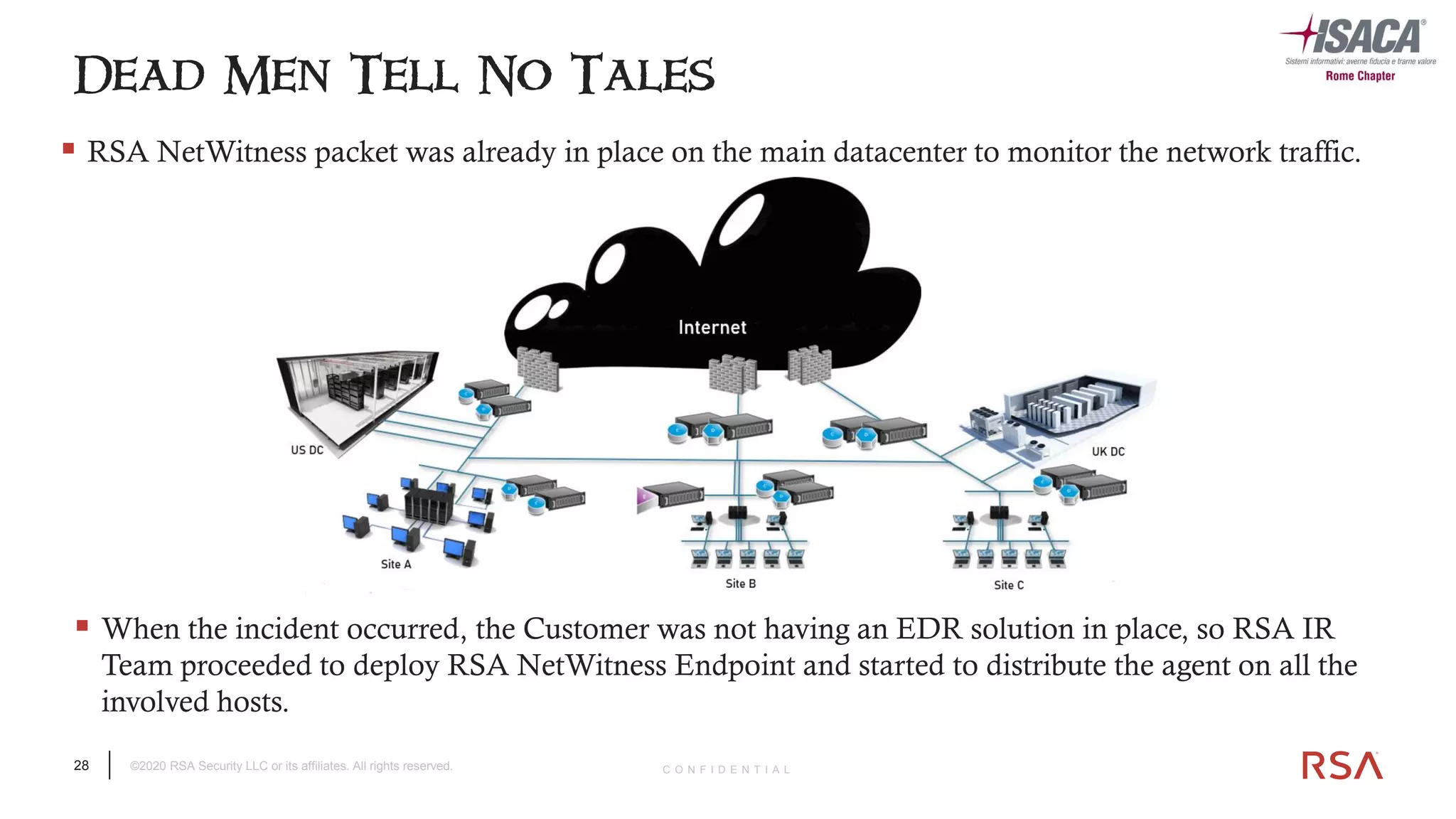
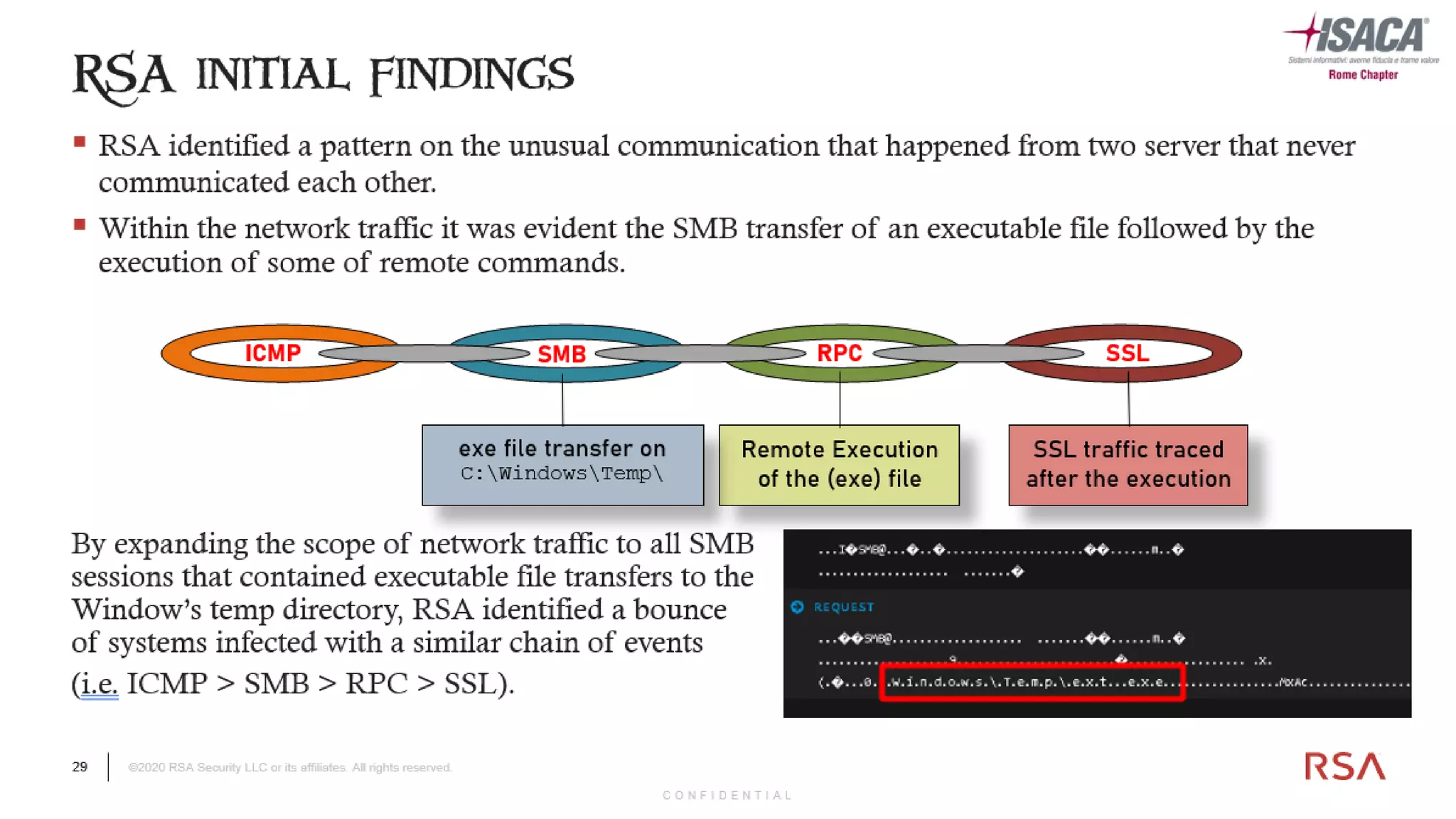
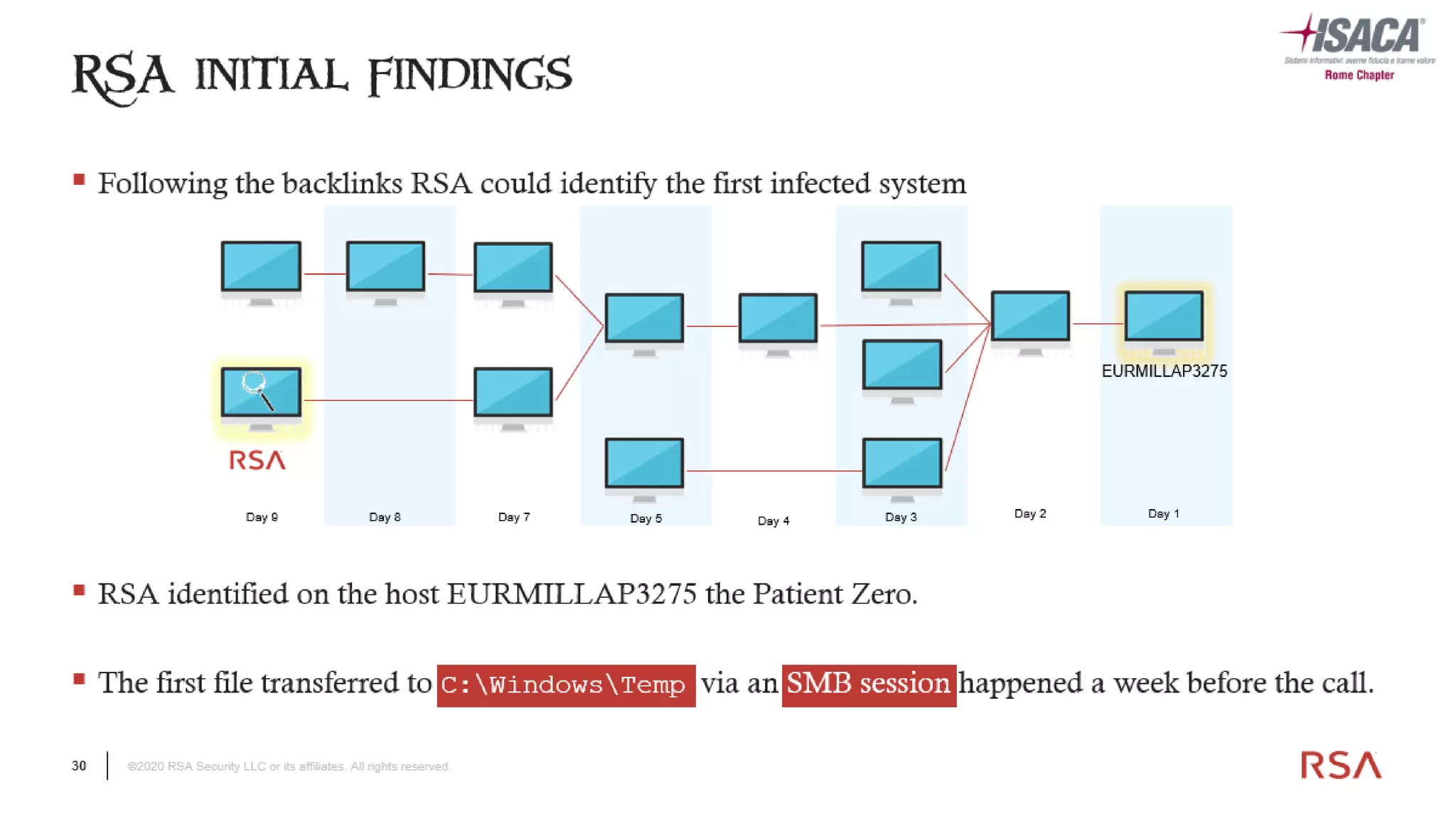
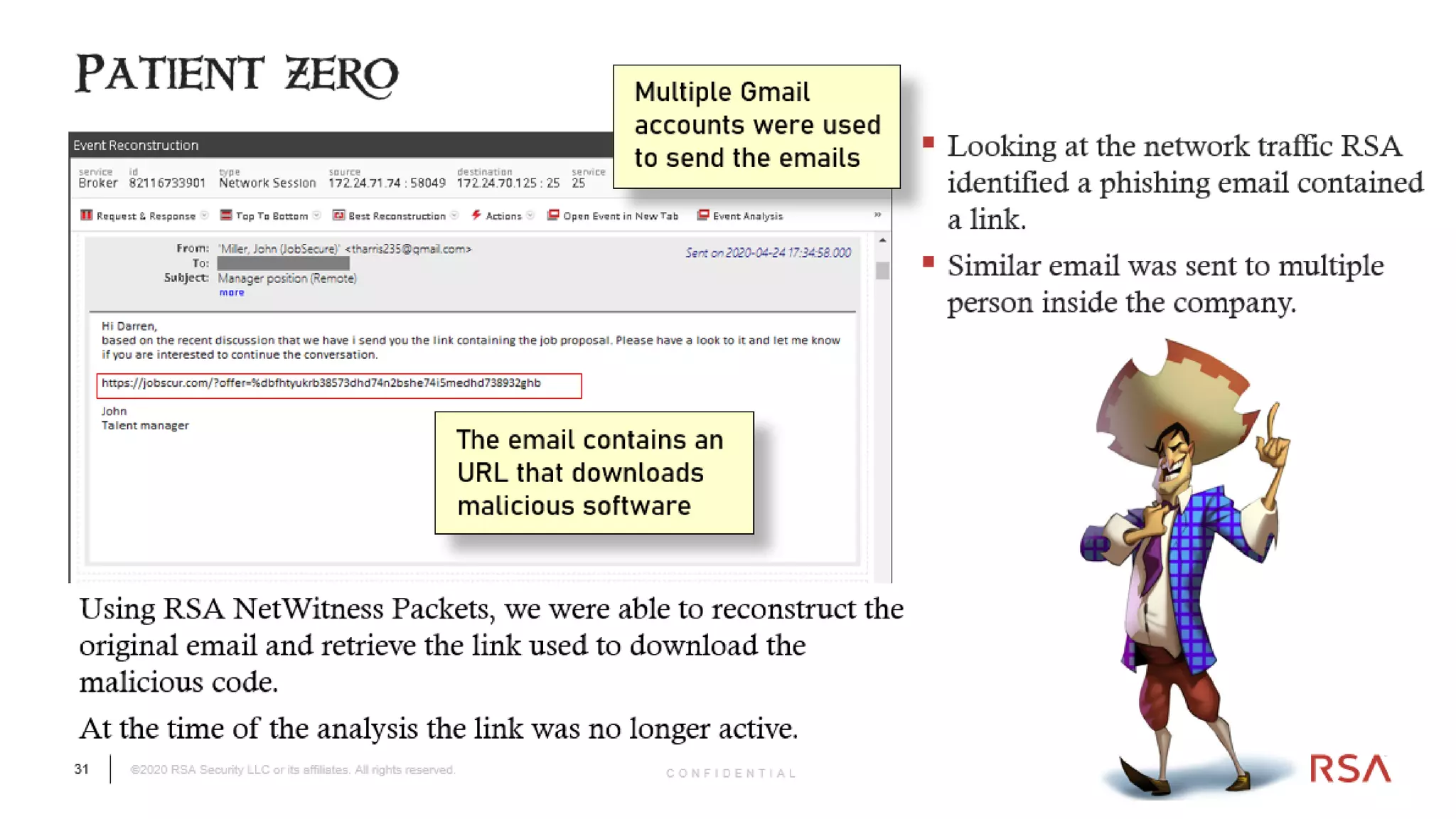
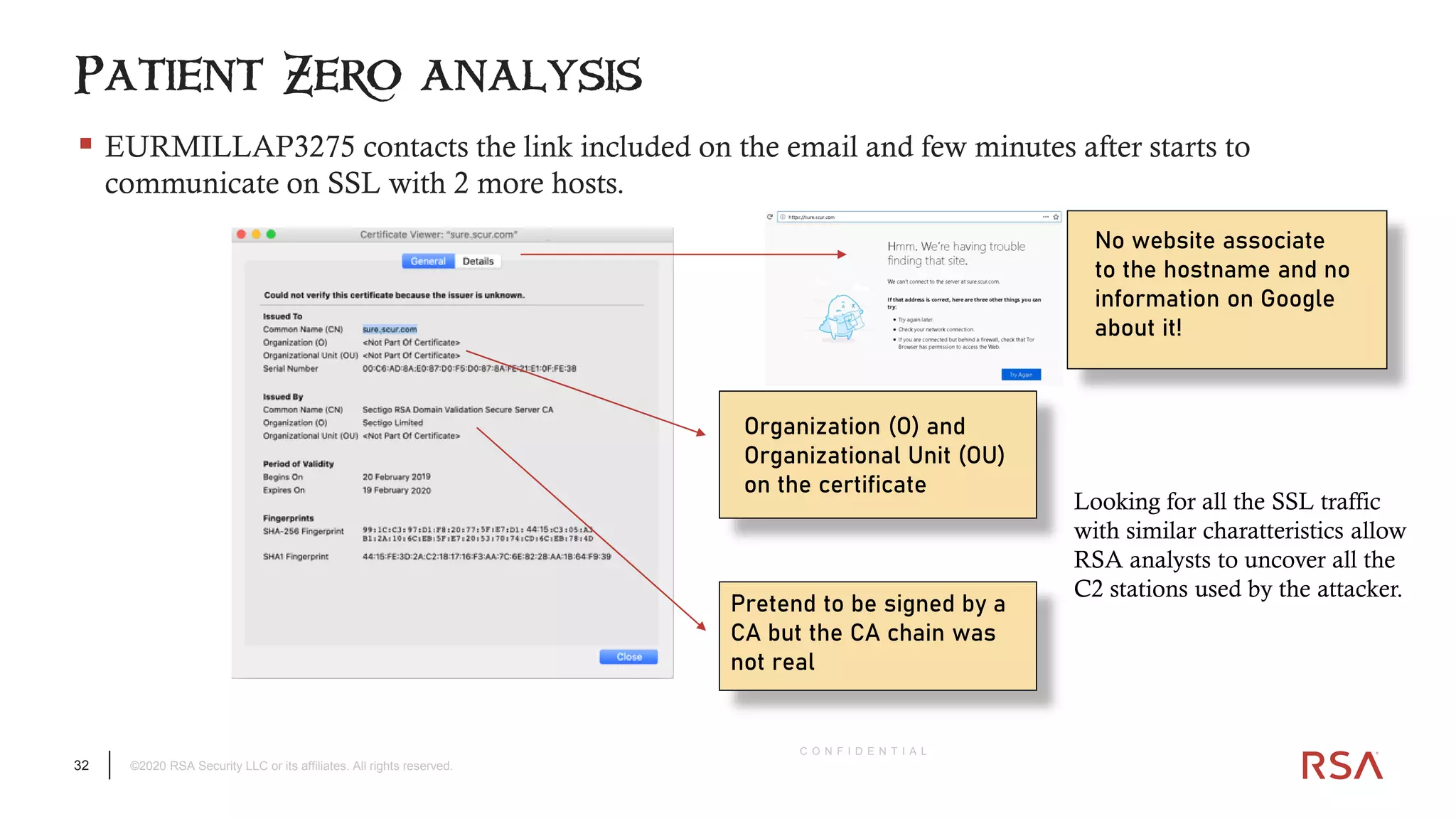
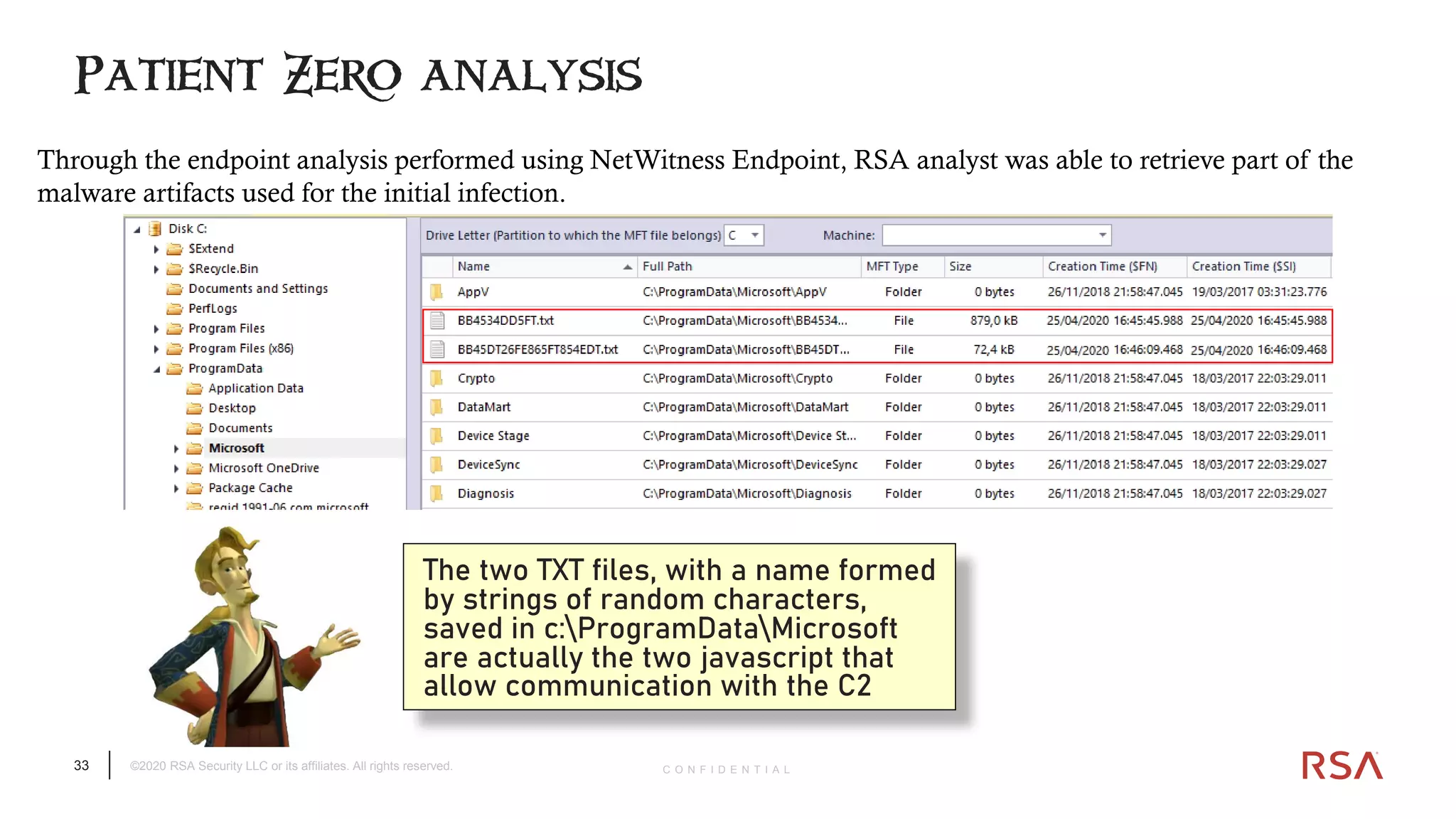
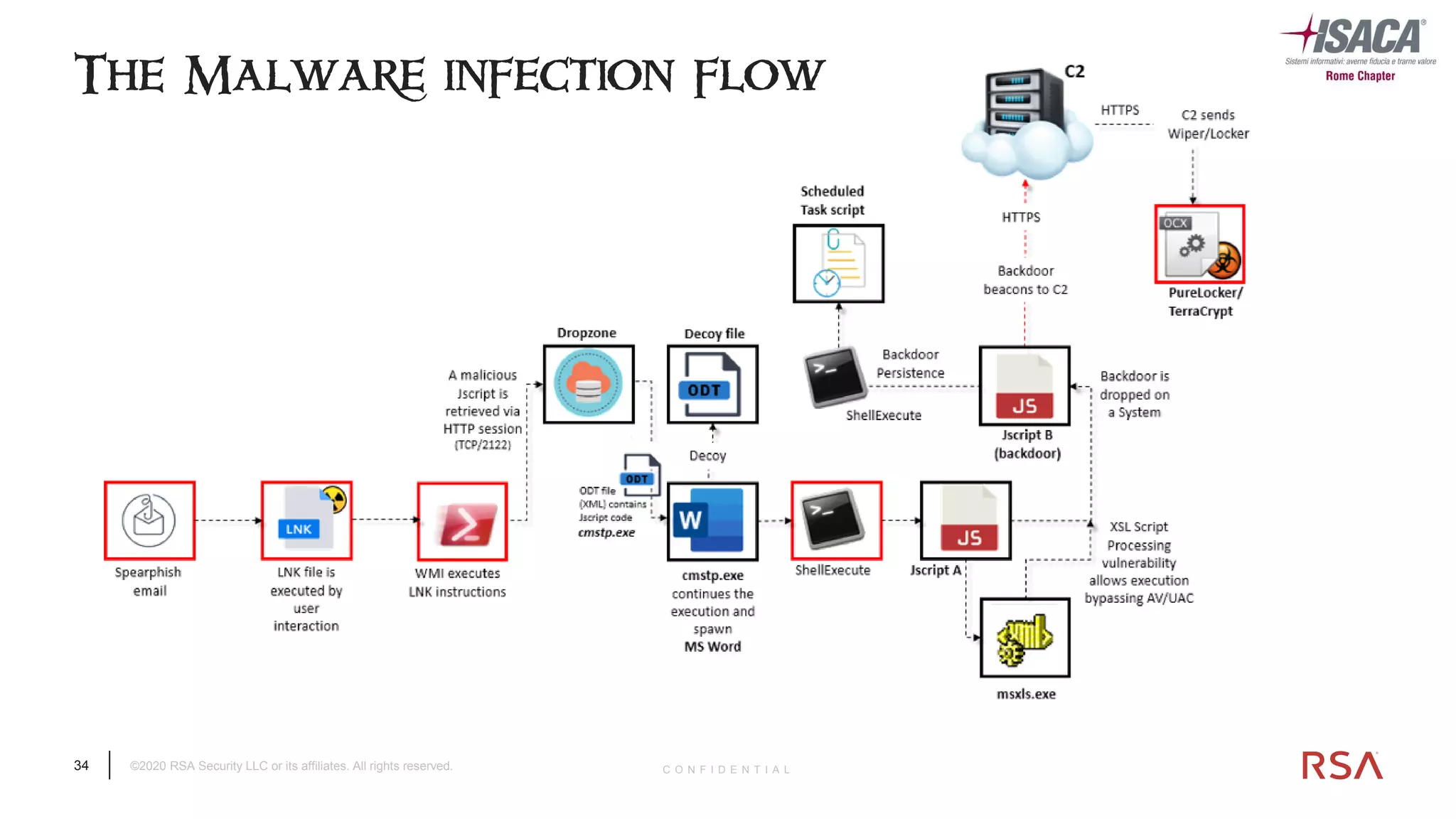
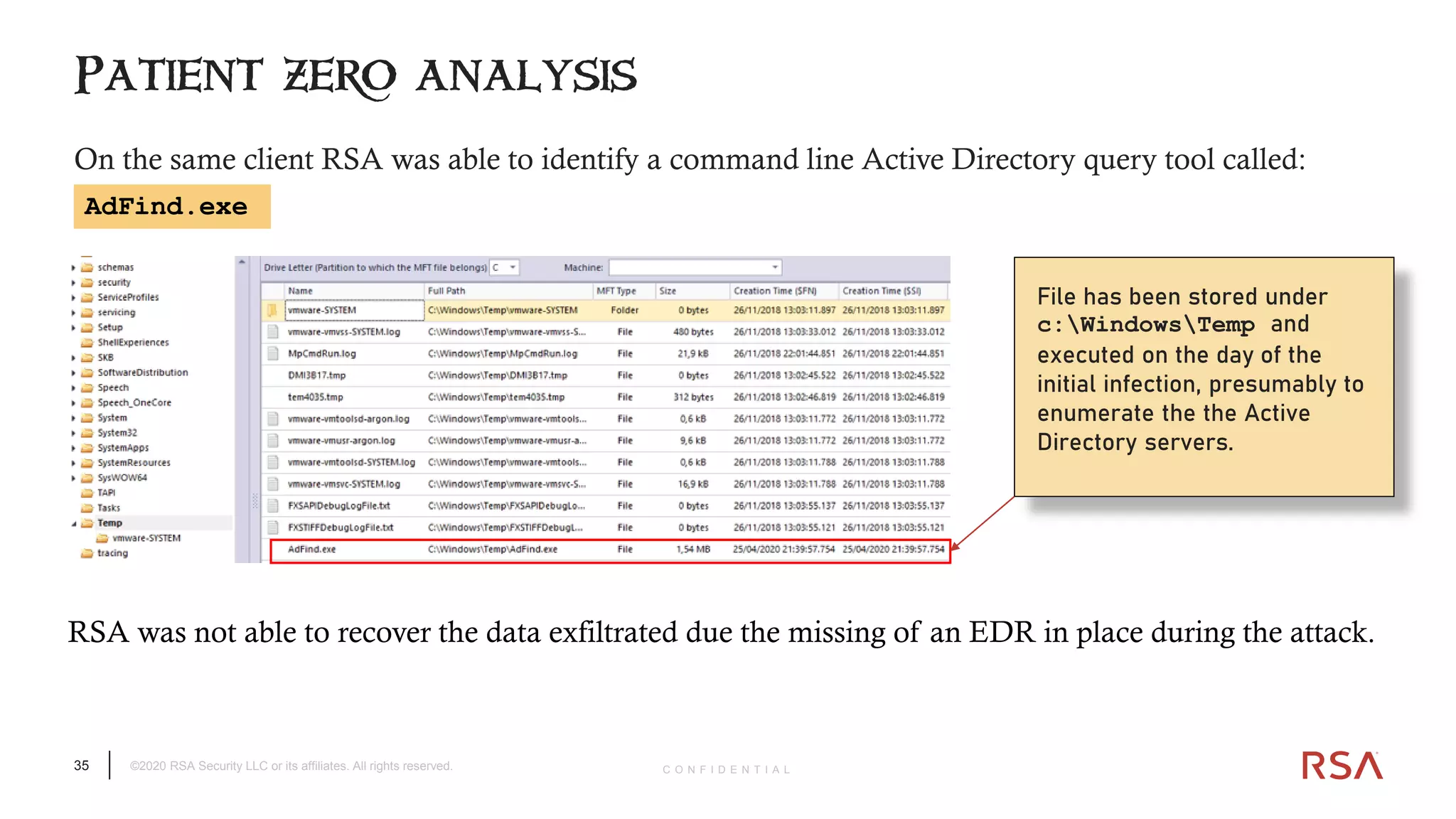
The document discusses the evolution of ransomware attacks and hybrid leakware/ransomware attacks. It describes how hybrid attacks now steal data first before encrypting it, then blackmail victims with threats to release the stolen data if ransom is not paid. The document also discusses the rise of malware-as-a-service (MaaS) and how this has lowered barriers to entry for criminals. Two case studies of recent ransomware attacks are presented, highlighting investigation techniques used like deploying endpoint monitoring tools. The document concludes with recommendations around negotiating with attackers, supporting investigations, and improving defenses to prevent such attacks.