The document summarizes an analysis of an organized Russian ransomware campaign. Key points include:
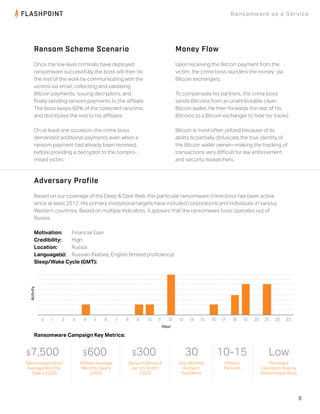
- The campaign recruited low-level Russian cybercriminals to spread ransomware through phishing emails and compromised servers. The mastermind kept 60% of ransom profits.
- Ransomware was distributed through botnet installs, emails, social media, and file sharing sites. It encrypted victim's files until ransom was paid in Bitcoin.
- On average, the mastermind earned $7,500 per month while affiliates earned $600. Ransoms averaged $300 per US victim. The operation had low perceived risk.