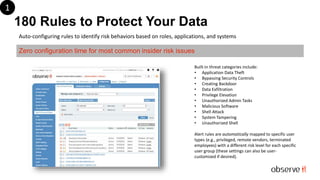
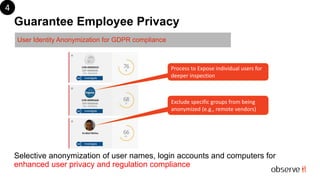
ObserveIT, the global leader in insider threat detection, addresses the significant issue of insider-caused security incidents, which represent 90% of security issues. The document highlights the features of the ObserveIT 6.7 release, including enhanced user activity monitoring, privacy measures through anonymization, and monitoring of user behaviors through a comprehensive alert system. It emphasizes the need for regulatory compliance and provides options for both existing customers and new users to upgrade or trial the software.