Introduction of cryptography and network security
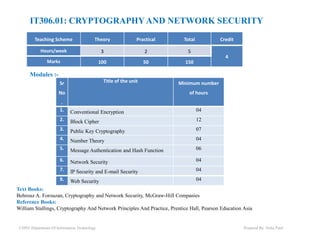
- 1. IT306.01: CRYPTOGRAPHYAND NETWORK SECURITY Teaching Scheme Theory Practical Total Credit Hours/week 3 2 5 4 Marks 100 50 150 Sr No . Title of the unit Minimum number of hours 1. Conventional Encryption 04 2. Block Cipher 12 3. Public Key Cryptography 07 4. Number Theory 04 5. Message Authentication and Hash Function 06 6. Network Security 04 7. IP Security and E-mail Security 04 8. Web Security 04 Text Books: Behrouz A. Forouzan, Cryptography and Network Security, McGraw-Hill Companies Reference Books: William Stallings, Cryptography And Network Principles And Practice, Prentice Hall, Pearson Education Asia Modules :- CSPIT-Department Of Information Technology Prepared By: Neha Patel
- 2. Introduction Neha Patel Assistant Professor, Department of I.T, CSPIT-Changa. CSPIT-Department Of Information Technology Prepared By: Neha Patel
- 3. CSPIT-Department Of Information Technology Prepared By: Neha Patel • The advancement of technology has made man dependent on Internet for all his needs. • Internet has given man easy access to everything while sitting at one place. Social networking, online shopping, storing data, gaming, online studying, online jobs, every possible thing that man can think of can be done through the medium of internet. • Internet is used in almost every sphere. • With the development of the internet and its related benefits also developed the concept of cyber crimes. • Cyber crimes are committed in different forms. A few years back, there was lack of awareness about the crimes that could be committed through internet. Why Need to Study this Subject?
- 4. Cyber Attacks • Phishing fraud :Escorts MD Nikhil Nanda, son-in-law of Amitabh Bachchan, was cheated into submitting his email ID, password and date of birth to a fake Microsoft account on July 21-13. The scamsters hacked two email accounts and his social network profile, and sought money from his contacts by impersonating him. • Sony Cyber Attack One of Worst in Corporate History. Wiper-Malware attack. Nov-14 – Thousands of files, seized by hackers last week, have been leaked online including personal details of around 6,000 Sony employees, upcoming Sony feature films and the salary details of top executives. • Xbox Live is Struggling Due to a Lizard Squad DDoS Attack .Dec-14 – This DDoS has resulted in many users being unable to connect to the service, making online play next to impossible, in addition to impacting update and game downloads. • Huawei hacked India’s Biggest telecommunication Network ‘BSNL’ –Feb -14 • Sony Xperia Smartphones have default installed Spyware, Sending data to China –oct-14 • One in Six Smartphone Users Victim of Cyber Attack: Study The Indian News Express. • Report by Arbor Networks reveals that India has seen a significant increase in attacks against financial and government organizations, with 34 percent and 43 percent reporting cyber threats and attacks respectively, up from last year’s 15 percent and 19 percent respectively Indian News Express news.google.co.in CSPIT-Department Of Information Technology Prepared By: Neha Patel
- 5. The Internet landscape has been transformed into a binary battlefield. Who needs a gun when you have a keyboard? CSPIT-Department Of Information Technology Prepared By: Neha Patel
- 6. Tutorial#1 • For the two entities A and B to communicate with each other semantically correctly, • Identify what are the properties desired in the protocol that facilitates the communication ? • What additional properties are required in presence of an adversary ? A B Adversary CSPIT-Department Of Information Technology Prepared By: Neha Patel
- 7. Security Goals(CIA) • Confidentiality :- – The protection of data from unauthorized disclosure. • Integrity:- – The assurance that data received are exactly as sent by an authorized entity (i.e., contain no modification, insertion, deletion or replay). • Availability – The information created and stored by an organization needs to be available to authorized entities CSPIT-Department Of Information Technology Prepared By: Neha Patel
- 8. Attacks • Security attack: Any action that compromises the security Goals. • The three goals of security confidentiality, integrity, and availability can be threatened by security attacks. • Attacks Threatening Confidentiality:- CSPIT-Department Of Information Technology Prepared By: Neha Patel A B C
- 9. Attacks Threatening Confidentiality:- • Snooping - unauthorized access to or interception of data. o For example, if you login to a website that uses no encryption, your username and password can be sniffed off the network by someone who can capture the network traffic between you and the web site. • Traffic Analysis- monitoring online traffic. CSPIT-Department Of Information Technology Prepared By: Neha Patel
- 10. Attacks Threatening Integrity. • Modification means that the attacker intercepts the message and changes it. • An example is the man-in-the-middle attack, in which an intruder reads messages from the sender and sends (possibly modified) versions to the recipient, • Masquerading or spoofing happens when the attacker impersonates somebody else. • Replaying means the attacker obtains a copy of a message sent by a user and later tries to replay it. • Repudiation means that sender of the message might later deny that she has sent the message; the receiver of the message might later deny that he has received the message A B C CSPIT-Department Of Information Technology Prepared By: Neha Patel
- 11. Attacks Threatening Availability • Attacks Denial of service (DoS) is a very common attack. It may slow down or totally interrupt the service of a system A B C CSPIT-Department Of Information Technology Prepared By: Neha Patel
- 12. • Passive attack: The goal of the opponent is to obtain information that is being transmitted. • Active attack :Involve some modification of the data stream or the creation of a false stream CSPIT-Department Of Information Technology Prepared By: Neha Patel Passive versus Active Attacks [Forouzan]
- 13. Cryptanalysis objective to recover key not just message • general approaches: – cryptanalytic attack – brute-force attack • if either succeed all key use compromised CSPIT-Department Of Information Technology Prepared By: Neha Patel
- 14. Kerckhoff’s Principle [Forouzan] Based on Kerckhoff’s principle, one should always assume that the adversary, Eve, knows the encryption/decryption algorithm. The resistance of the cipher to attack must be based only on the secrecy of the key. CSPIT-Department Of Information Technology Prepared By: Neha Patel
- 15. Cryptanalytic Attacks ciphertext only only know algorithm & ciphertext, is statistical, know or can identify plaintext known plaintext know/suspect plaintext & ciphertext chosen plaintext select plaintext and obtain ciphertext chosen ciphertext select ciphertext and obtain plaintext
- 16. Brute-force attack • The attacker tries every possible key on a piece of ciphper text until an intelligent translation into plaintext is obtained. On average half of all possible keys must be tried CSPIT-Department Of Information Technology Prepared By: Neha Patel
- 17. The OSI Security Architecture [William Stalling] • ITU-T provides some security services and some mechanisms to achieve security goals services. Security services and mechanisms are closely related because a mechanism or combination of mechanisms are used to provide a service.. • Security service: A processing or communication service that enhances the security of the data processing systems and the information transfers of an organization. • Security mechanism: A process (or a device incorporating such a process) that is designed to detect, prevent, or recover from a security attack. – Methods or techniques to achieve security services. Note : For detail study refer Textbook and Reference book CSPIT-Department Of Information Technology Prepared By: Neha Patel
- 18. Security Services [Forouzan] CSPIT-Department Of Information Technology Prepared By: Neha Patel
- 19. Security mechanisms[Forouzan] CSPIT-Department Of Information Technology Prepared By: Neha Patel
- 20. Relation between Services and Mechanisms[William Stalling] CSPIT-Department Of Information Technology Prepared By: Neha Patel
- 21. About Subject • In this subject you will learn different security mechanism/techniques to achieve security goals and services. • There are many cryptanalytic techniques. CSPIT-Department Of Information Technology Prepared By: Neha Patel
- 22. 1.22 Encipher Techniques • The actual implementation of security goals needs some techniques. Two techniques are prevalent today: cryptography and steganography. • Cryptography : o Cryptography, a word with Greek origins, means “secret writing.” However, we use the term to refer to the science and art of transforming messages to make them secure and immune to attacks. • Steganography o The word steganography, with origin in Greek, means “covered/Hide writing,” in contrast with cryptography, which means “secret writing.” CSPIT-Department Of Information Technology Prepared By: Neha Patel
- 23. Cryptography Characteristics • can characterize cryptographic system by: – type of encryption operations used • substitution • transposition • product – number of keys used • single-key or private • two-key or public – way in which plaintext is processed • block • stream CSPIT-Department Of Information Technology Prepared By: Neha Patel
- 24. THE REST OF THE BOOK The rest of this book is divided into four parts. Part One: Symmetric-Key Enciphermen Part Two: Asymmetric-Key Encipherment Part Three: Integrity, Authentication, and Key Management Part Four: Network Security CSPIT-Department Of Information Technology Prepared By: Neha Patel
