The document discusses computer networks and the client-server model. It provides the following key points:
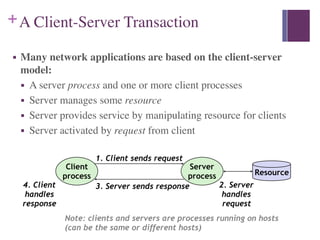
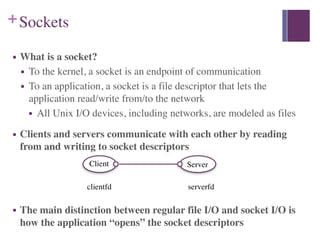
1. In the client-server model, a server manages resources and provides services to client processes by manipulating resources. Clients send requests to the server which handles the request and sends a response.
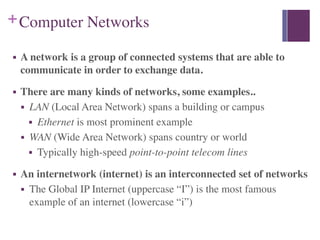
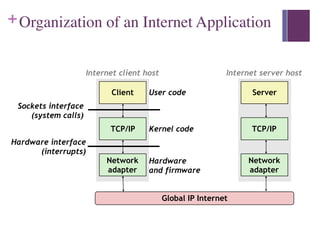
2. A network allows connected systems to communicate and exchange data. Examples include LANs, WANs, and internetworks like the global Internet. Nodes on the network include devices like computers, phones, and networking hardware.
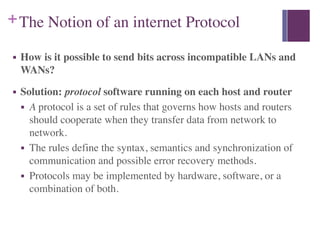
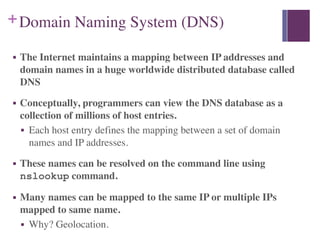
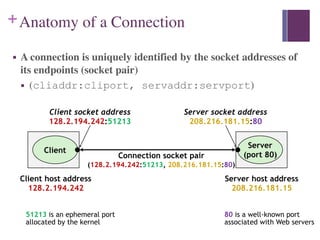
3. The Internet Protocol (IP) provides a naming scheme for host addresses and a delivery mechanism for transferring data packets from source to destination across interconnected networks.








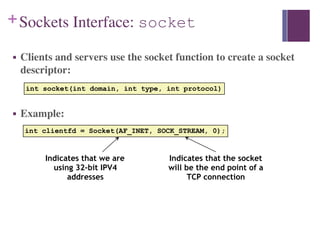
![+Socket Address Structures
■ Generic socket address:
■ For address arguments to connect, bind, and accept
■ Necessary only because C did not have generic (void*) pointers
when the sockets interface was designed
struct sockaddr {
uint16_t sa_family; /* Protocol family */
char sa_data[14]; /* Address data. */
};
sa_family
Family Specific](https://image.slidesharecdn.com/networkprogramming-231112170537-75f17ef3/85/Network-Programming-pdf-16-320.jpg)
![+Socket Address Structures con’t
■ Internet-specific socket address:
■ Must cast struct sockaddr_in* to struct sockaddr*
for functions that take socket address arguments.
0 0 0 0 0 0 0 0
sa_family
Family Specific
struct sockaddr_in {
uint16_t sin_family; /* Protocol family (always AF_INET) */
uint16_t sin_port; /* Port num in network byte order */
struct in_addr sin_addr; /* IP addr in network byte order */
unsigned char sin_zero[8]; /* Pad to sizeof(struct sockaddr) */
};
sin_port
AF_INET
sin_addr
sin_family](https://image.slidesharecdn.com/networkprogramming-231112170537-75f17ef3/85/Network-Programming-pdf-17-320.jpg)