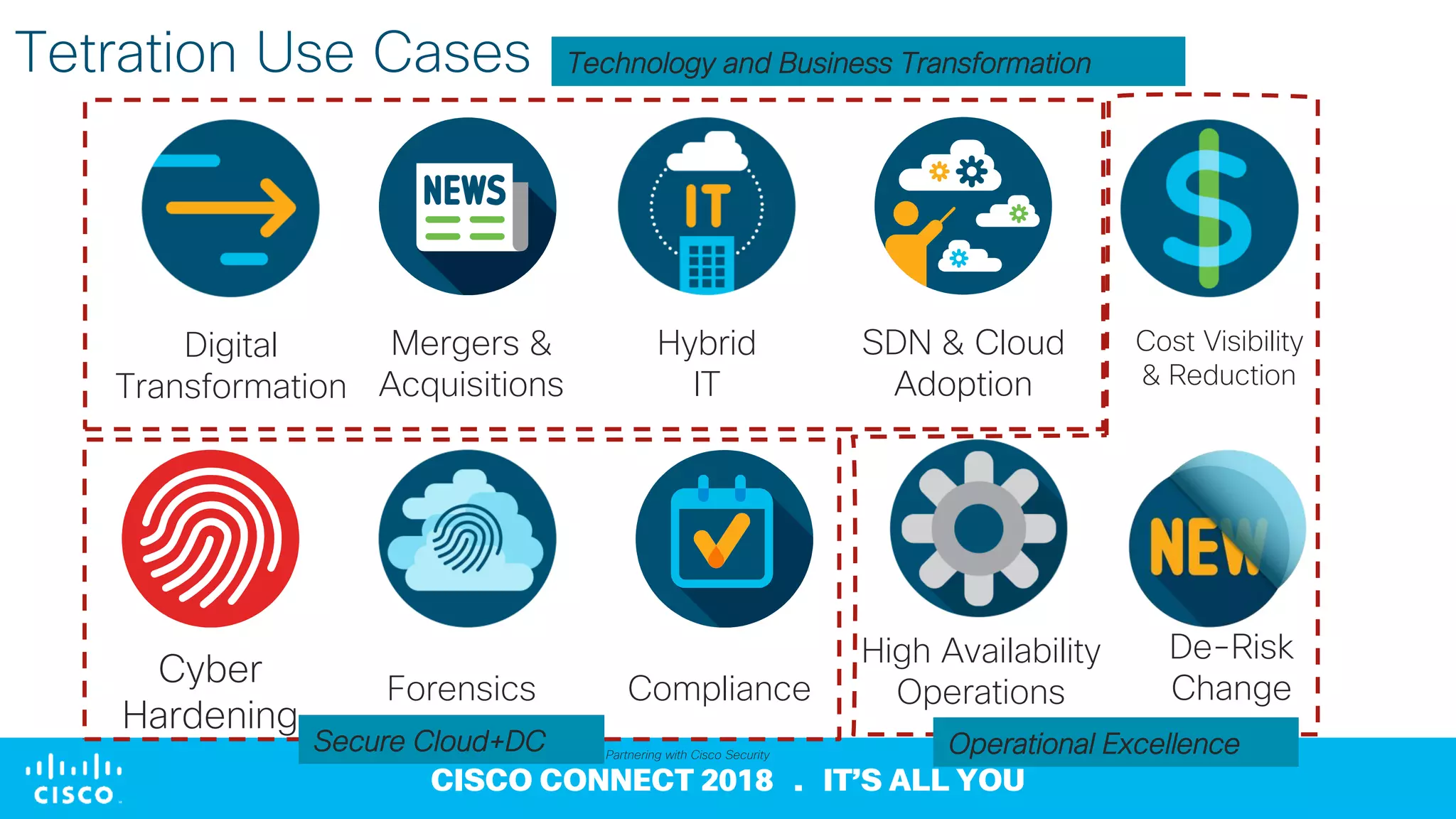
1) The document discusses Cisco Tetration Analytics, a product that provides visibility and security for data centers through machine learning-powered network monitoring and analytics.
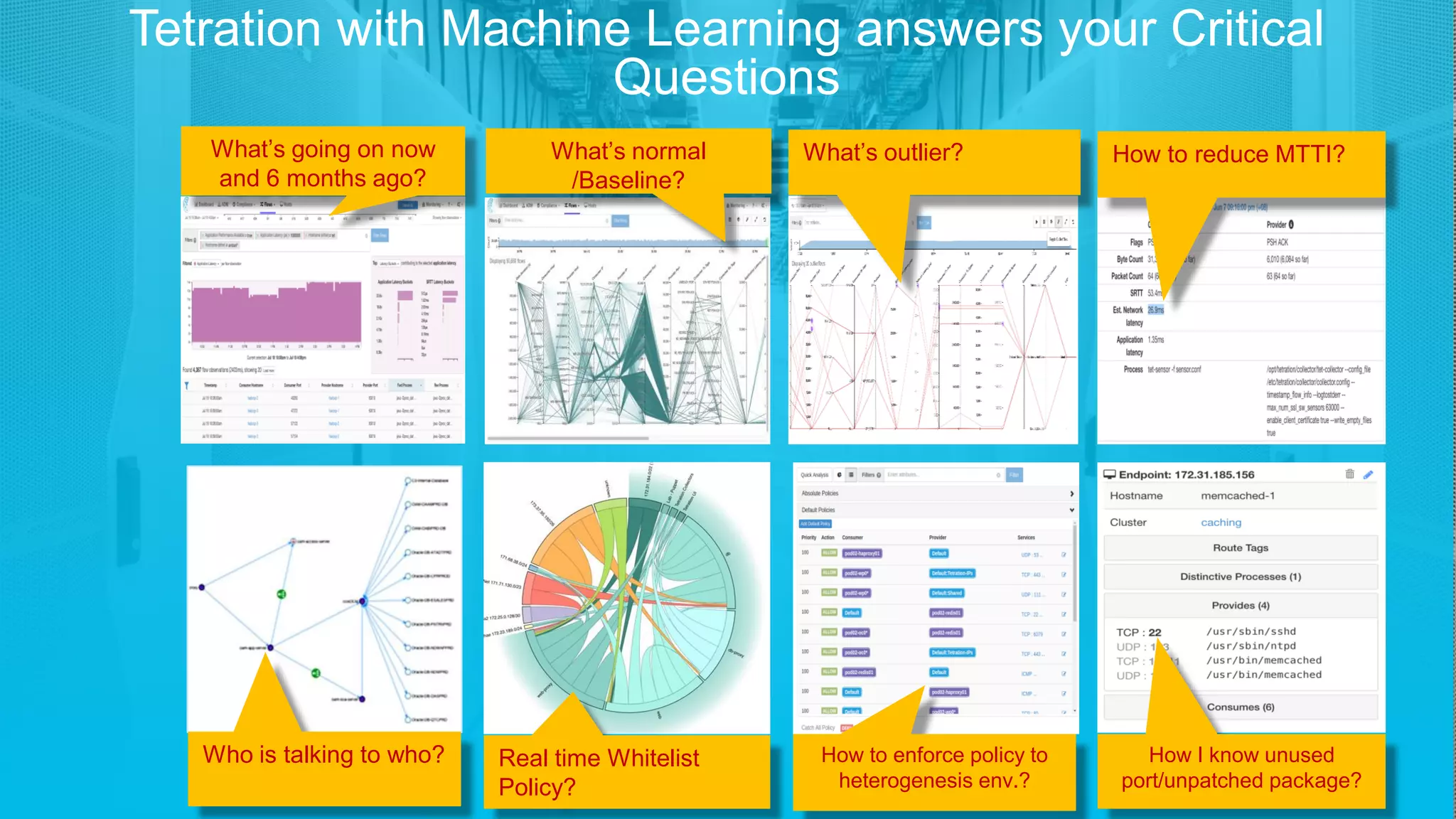
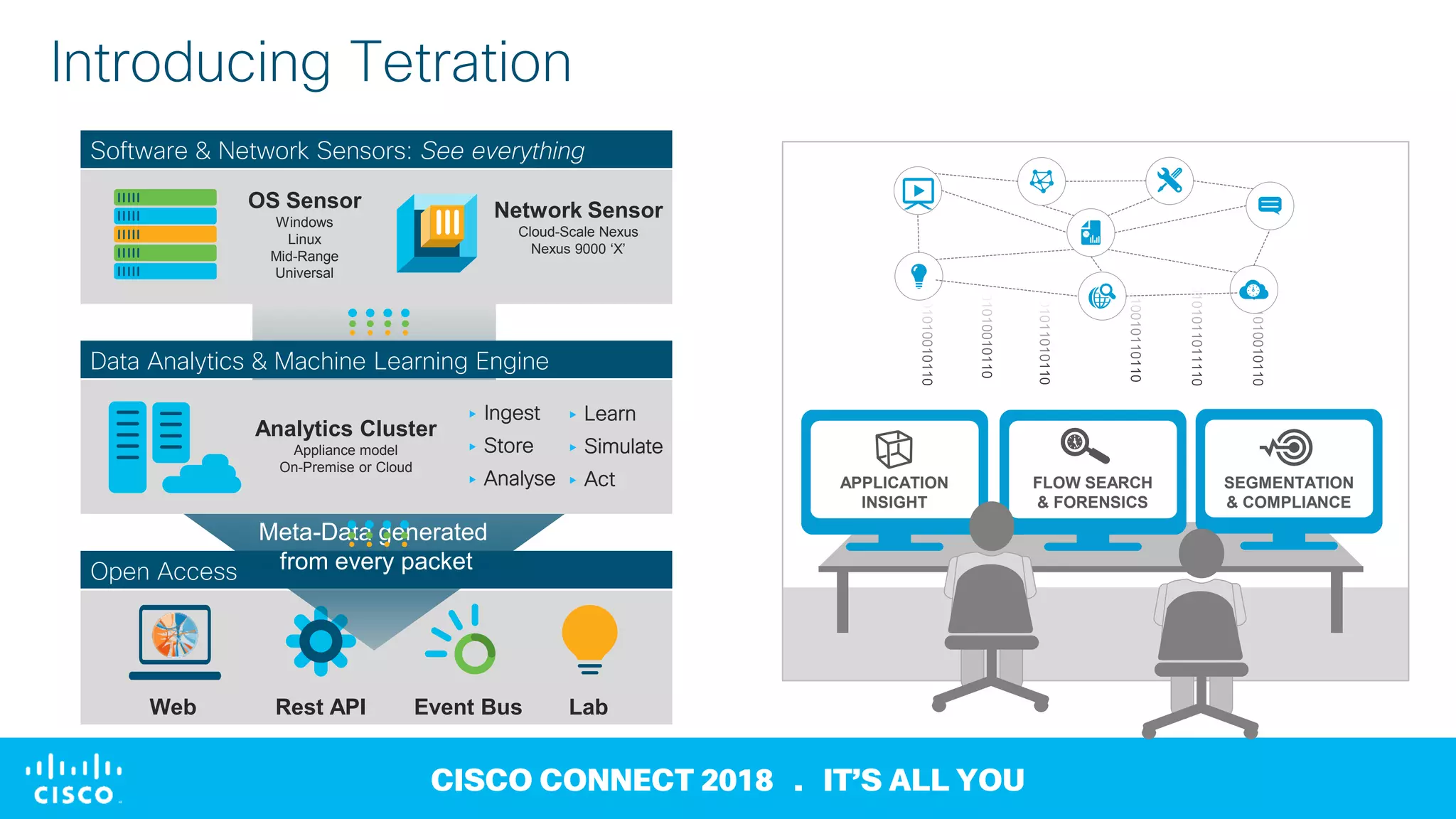
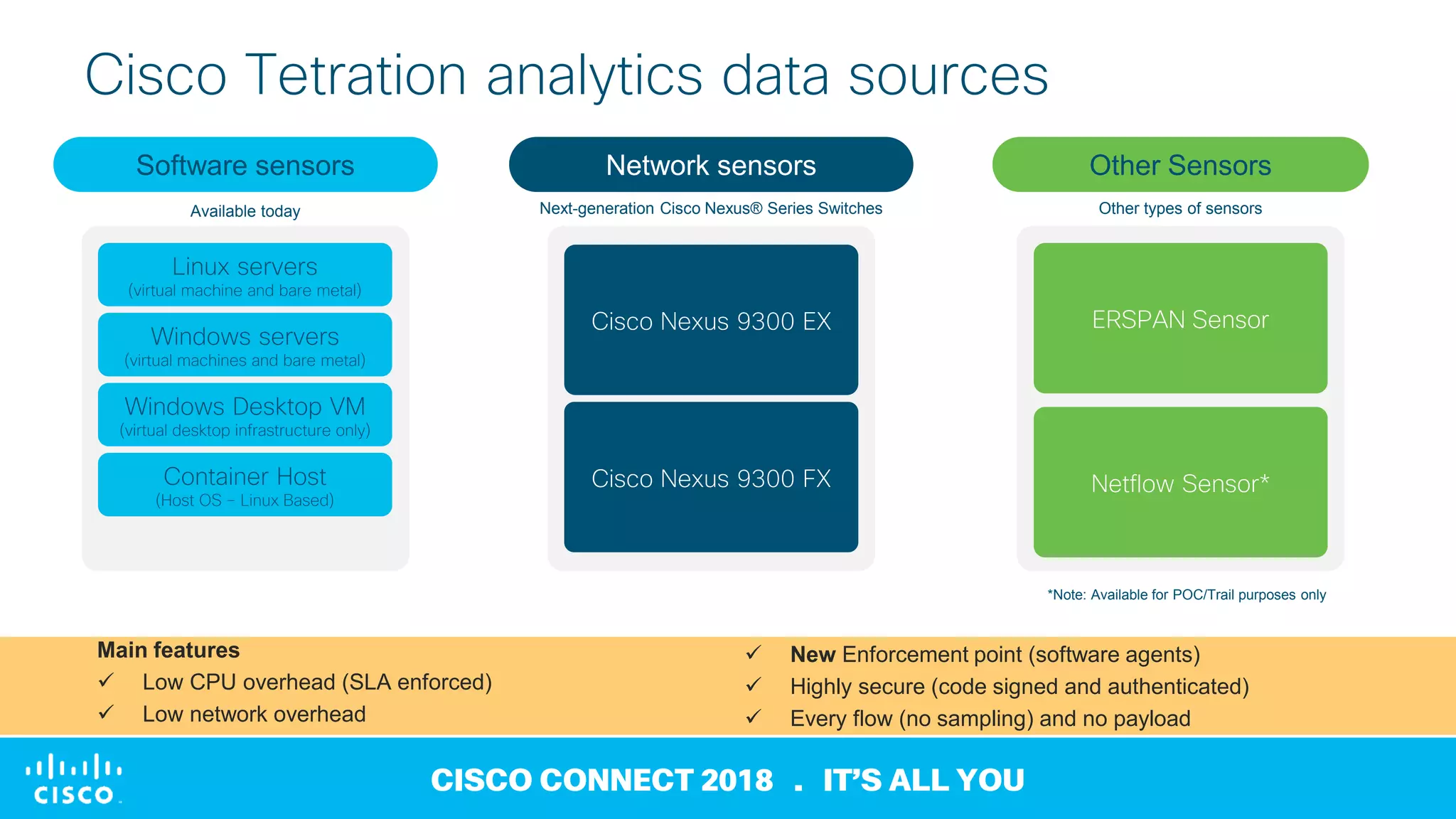
2) Tetration collects data from sensors on network devices, servers, and endpoints to generate metadata about all network traffic and identify anomalies, outliers, and deviations from baselines.
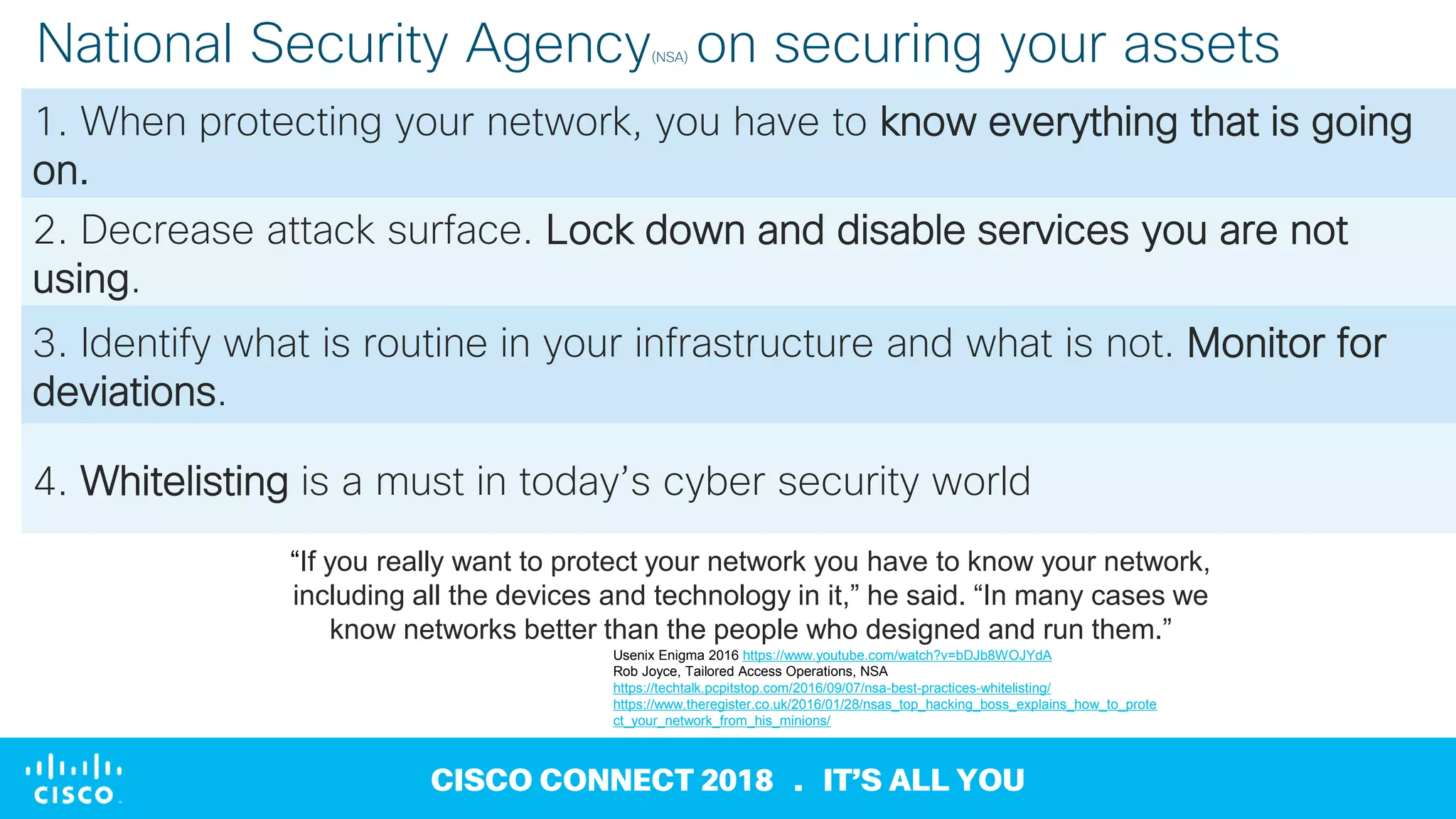
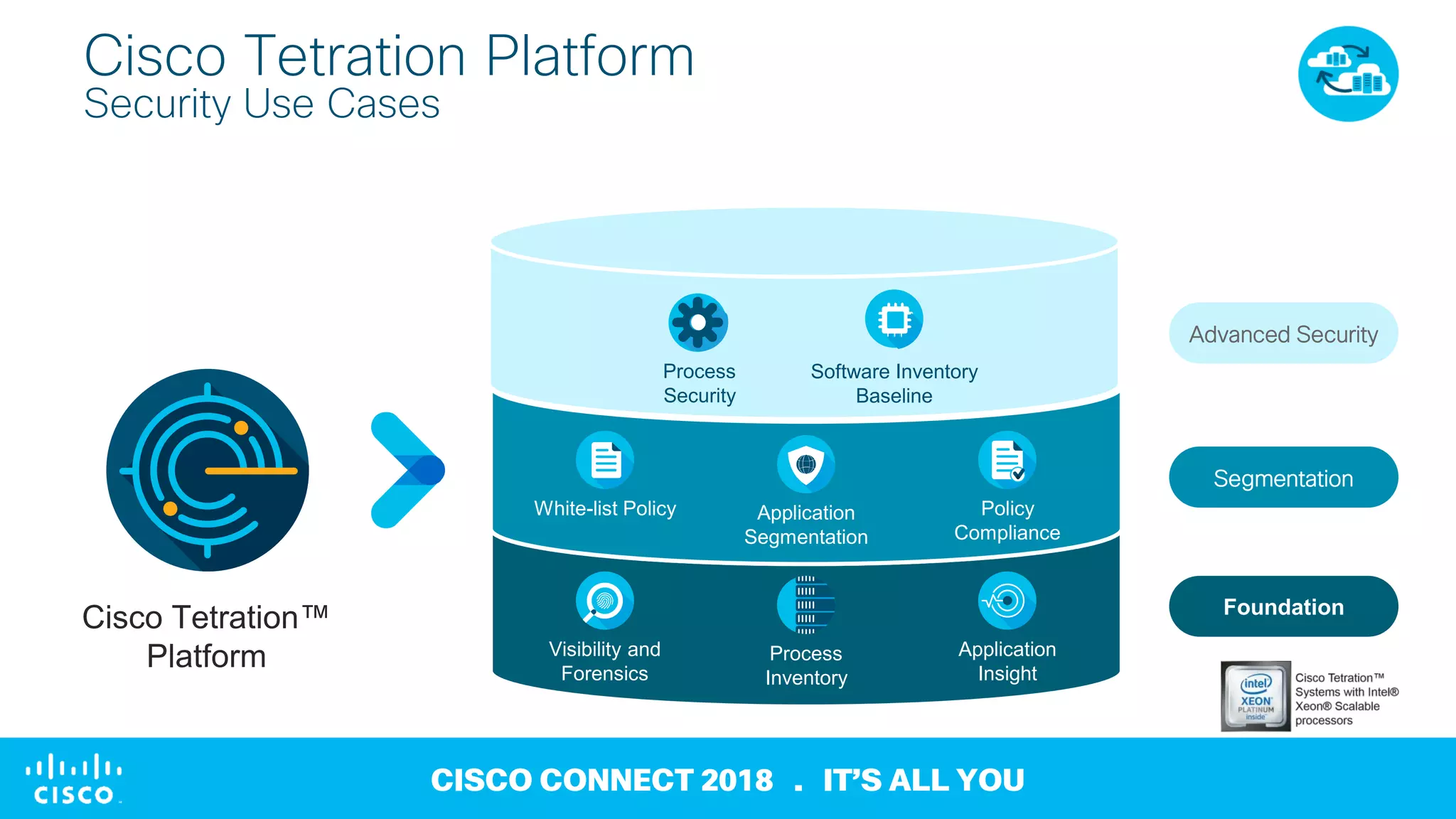
3) It offers capabilities like application dependency mapping, real-time whitelisting, inventory of software and open ports, and network forensics to help strengthen data center security, reduce mean time to identify issues, and enable compliance.





![[Cisco Connect 2018 - Vietnam] Anh duc le building a secure data center](https://image.slidesharecdn.com/anhduclebuildingasecuredatacenter-180504035351/75/Cisco-Connect-2018-Vietnam-Anh-duc-le-building-a-secure-data-center-15-2048.jpg)