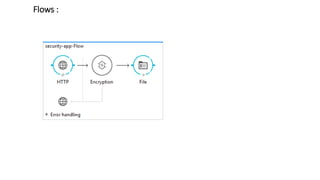
This document provides instructions for encrypting payload data using Anypoint Enterprise Security. It describes using a Mule ESB flow to encrypt an incoming XML payload with the Encryption configuration and write the encrypted output to a file. The flow listens for HTTP requests, encrypts the payload body using the JCE encryption algorithm with a key, and writes the encrypted output to a specified file location. Testing instructions are included to send sample payload data via HTTP POST and verify an encrypted file is generated.