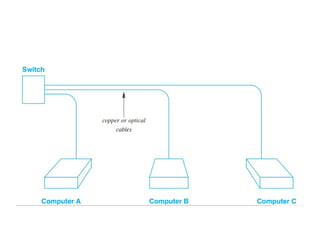
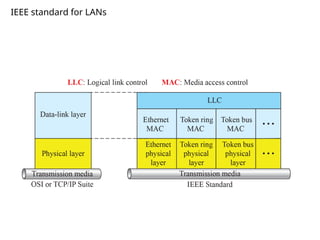
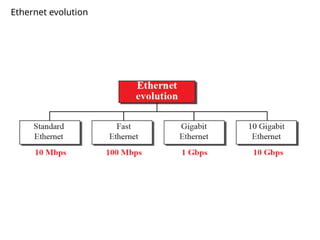
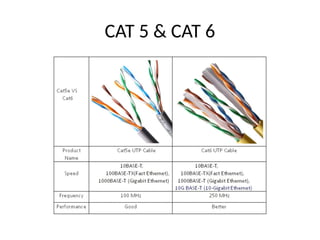
This document analyzes routing challenges in Vehicular Sensor Networks (VSNs), where high mobility, dynamic topology, and heavy data loads limit traditional protocols. It highlights the limitations of OLSR and introduces Cognitive Radio (CR) to dynamically detect unused spectrum and enhance routing reliability. The paper reviews existing VSN routing, clustering, and energy-optimization techniques, including K-means and Ant Colony algorithms. It also discusses security issues such as malicious reporting, privacy risks, and network vulnerabilities. Overall, the study emphasizes improving VSN routing efficiency, reducing energy consumption, and strengthening security for intelligent transportation systems.







![TCP/IP Internet
• TCP/IP protocol suite, was designed in 1970s
by 2 DARPA [
Defense Advanced Research Projects Agency]
scientists
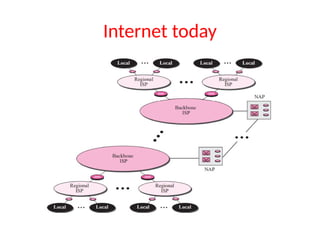
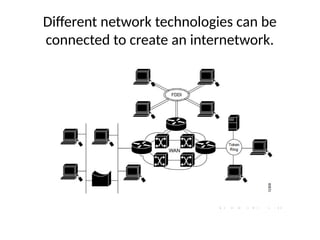
• It is the set of communications protocols used
for the Internet and other similar networks.](https://image.slidesharecdn.com/tcpmodule1-251208185804-46b082e9/85/Modular-representation-of-TCP-IP-Network-protocols-18-320.jpg)




![History And Scope Of The Internet
• 1969. Four-node ARPANET (Advanced Research Project Agency)
established.
• 1970. ARPA hosts implement NCP(Network Control Protocol).
• 1973. Development of TCP/IP suite begins.
• 1977. An internet tested using TCP/IP.
• 1978. UNIX distributed to academic/research sites.
• 1981. CSNET established.
• 1983. TCP/IP becomes the official protocol for ARPANET.
• 1983. MILNET was born.
• 1986. NSFNET [National Science Foundation Network] established.
• 1990. ARPANET decommissioned and replaced by NSFNET.
• 1995. NSFNET goes back to being a research network.
• 1995. Companies known as Internet Service Providers (ISPs) started.](https://image.slidesharecdn.com/tcpmodule1-251208185804-46b082e9/85/Modular-representation-of-TCP-IP-Network-protocols-24-320.jpg)