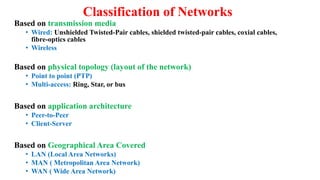
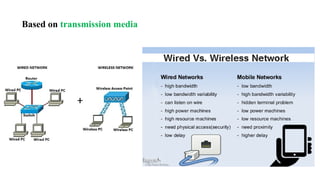
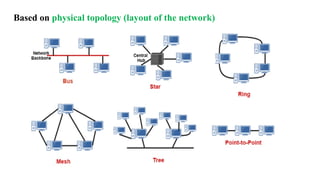
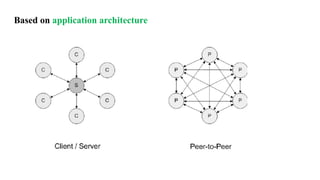
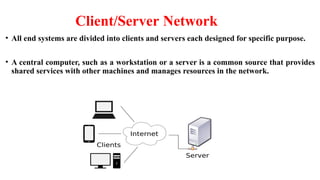
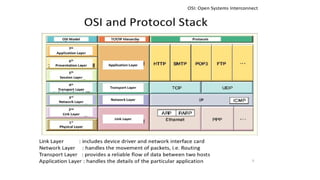
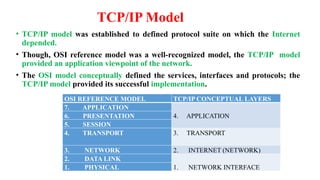
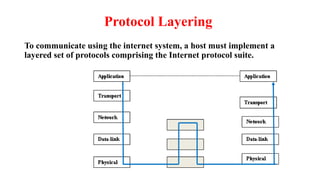
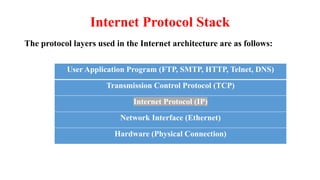
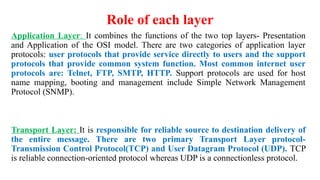
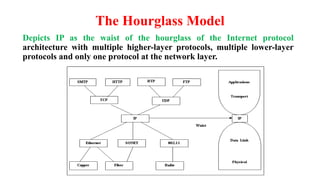
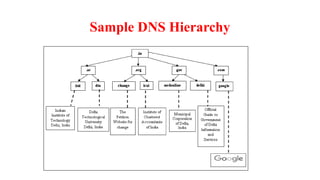
Chapter 1 details the structure and functioning of the internet, distinguishing it from the World Wide Web, and explaining the evolution of networking technologies such as the ARPANET and the development of protocols like TCP/IP. It categorizes networks by transmission media (wired and wireless), topologies, and geographical coverage, including LAN, MAN, and WAN, while discussing client-server and peer-to-peer architectures. The chapter also covers internet addressing through IP addresses and URLs, the role of web browsers, and organizations involved in internet governance.