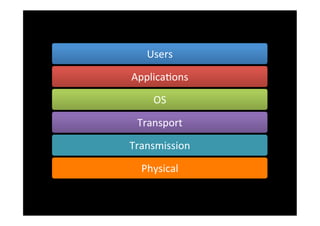
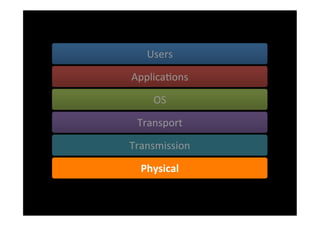
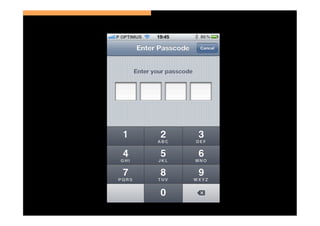
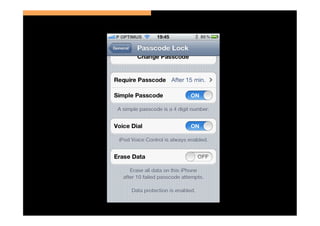
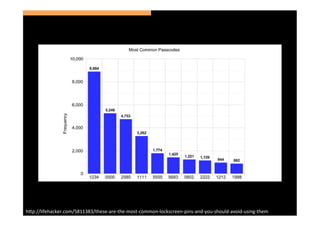
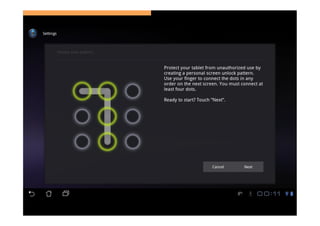
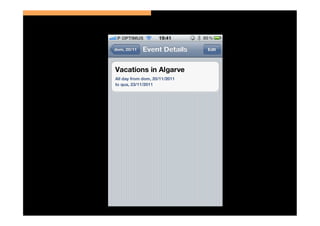
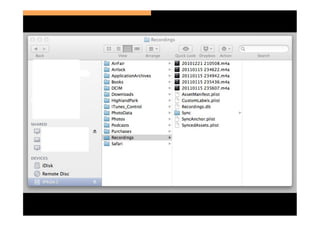
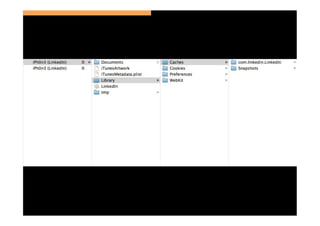
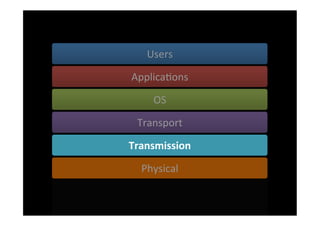
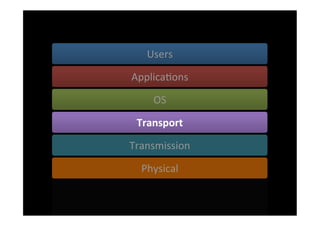
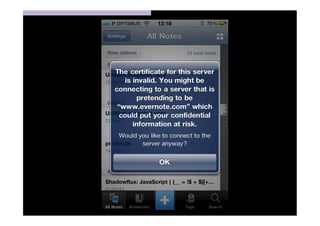
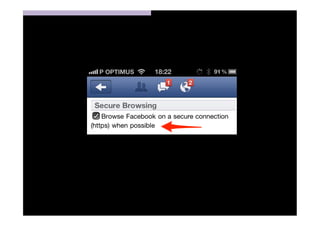
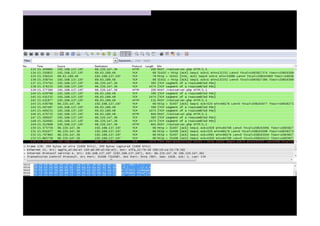
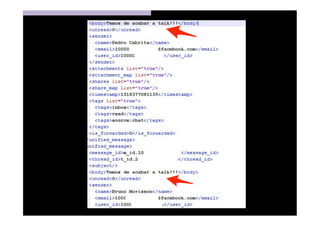
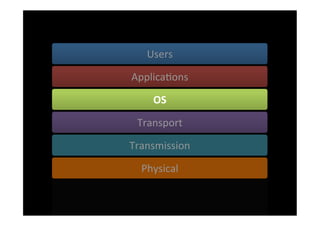
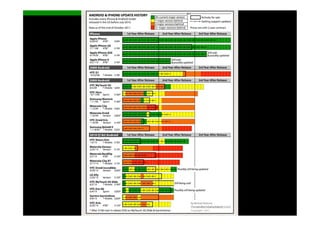
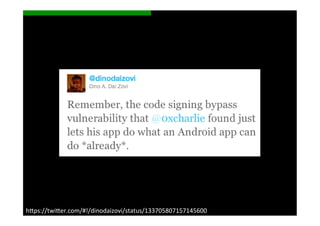
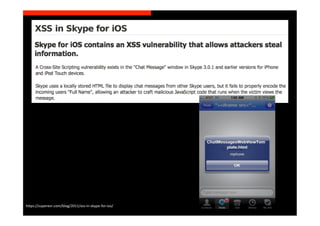
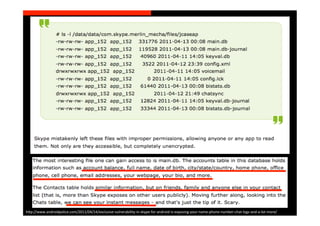
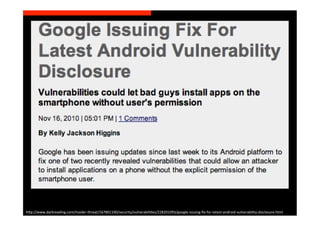
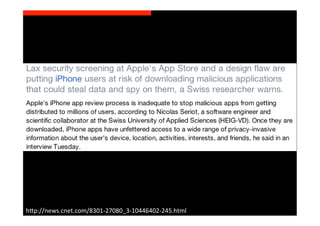
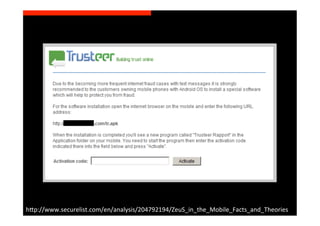
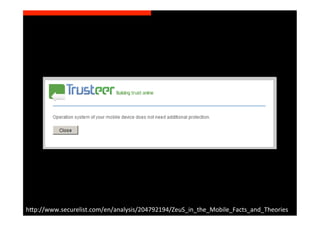
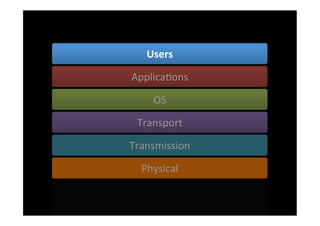
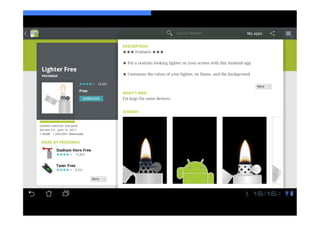
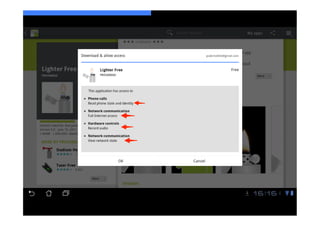
The document discusses the challenges and vulnerabilities associated with mobile security, emphasizing that if someone gains physical access to a device, security measures can be rendered ineffective. It highlights various risks such as insecure data storage, weak application security, and the prevalence of malware, stressing the importance of user awareness and device protection. The authors call for better security practices in application development and encourage users to prioritize security features and encrypted communications.