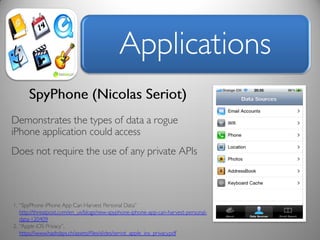
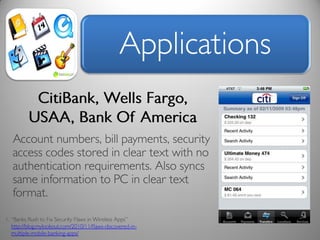
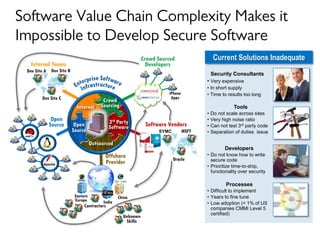
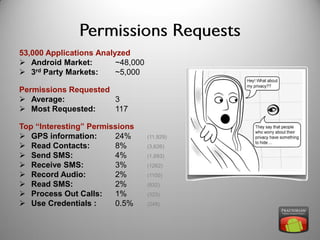
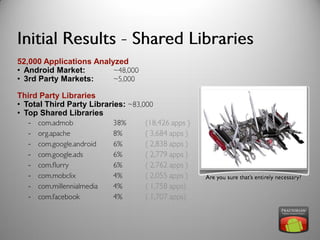
The document discusses risk and defines it as the possibility of loss or injury. It then discusses crowd sourcing security testing and outlines some of the current inadequate solutions such as expensive security consultants, tools that don't scale, and developers who prioritize functionality over security. The document then summarizes the results of analyzing over 53,000 Android applications, finding most request GPS and contact permissions and lists the top third party libraries used. It concludes by proposing a whitelisting approach to security testing using static analysis and an unbiased third party.