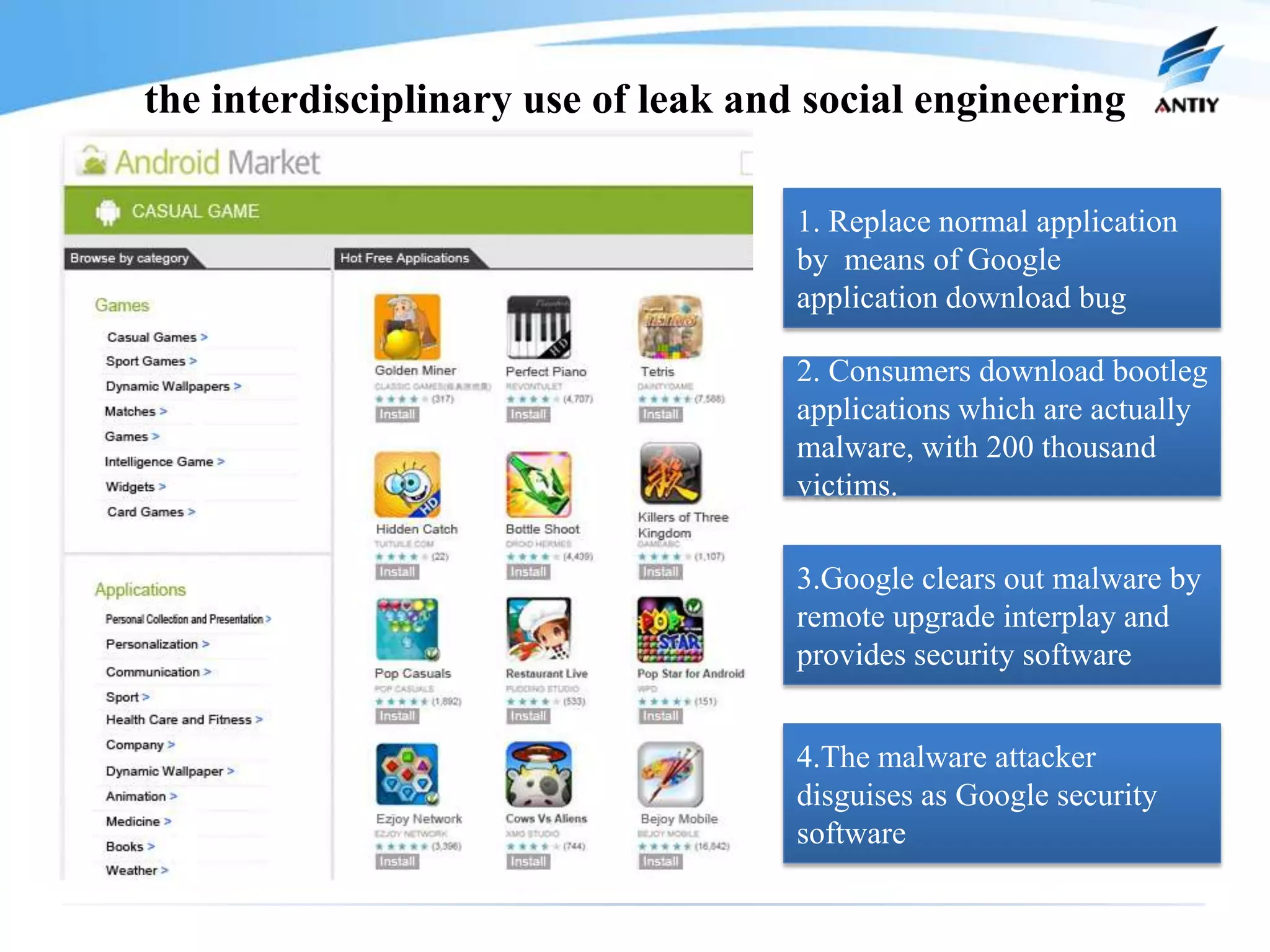
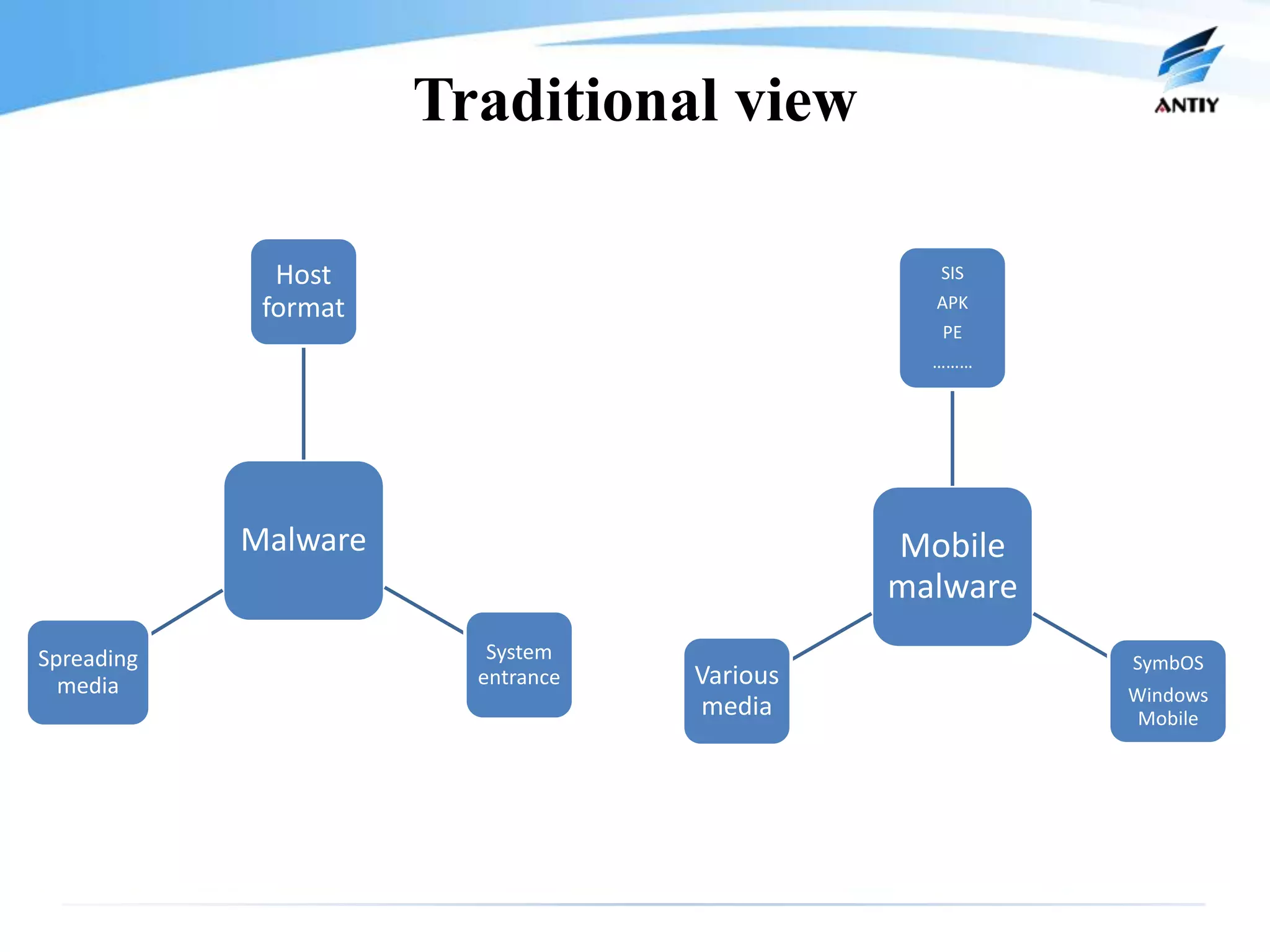
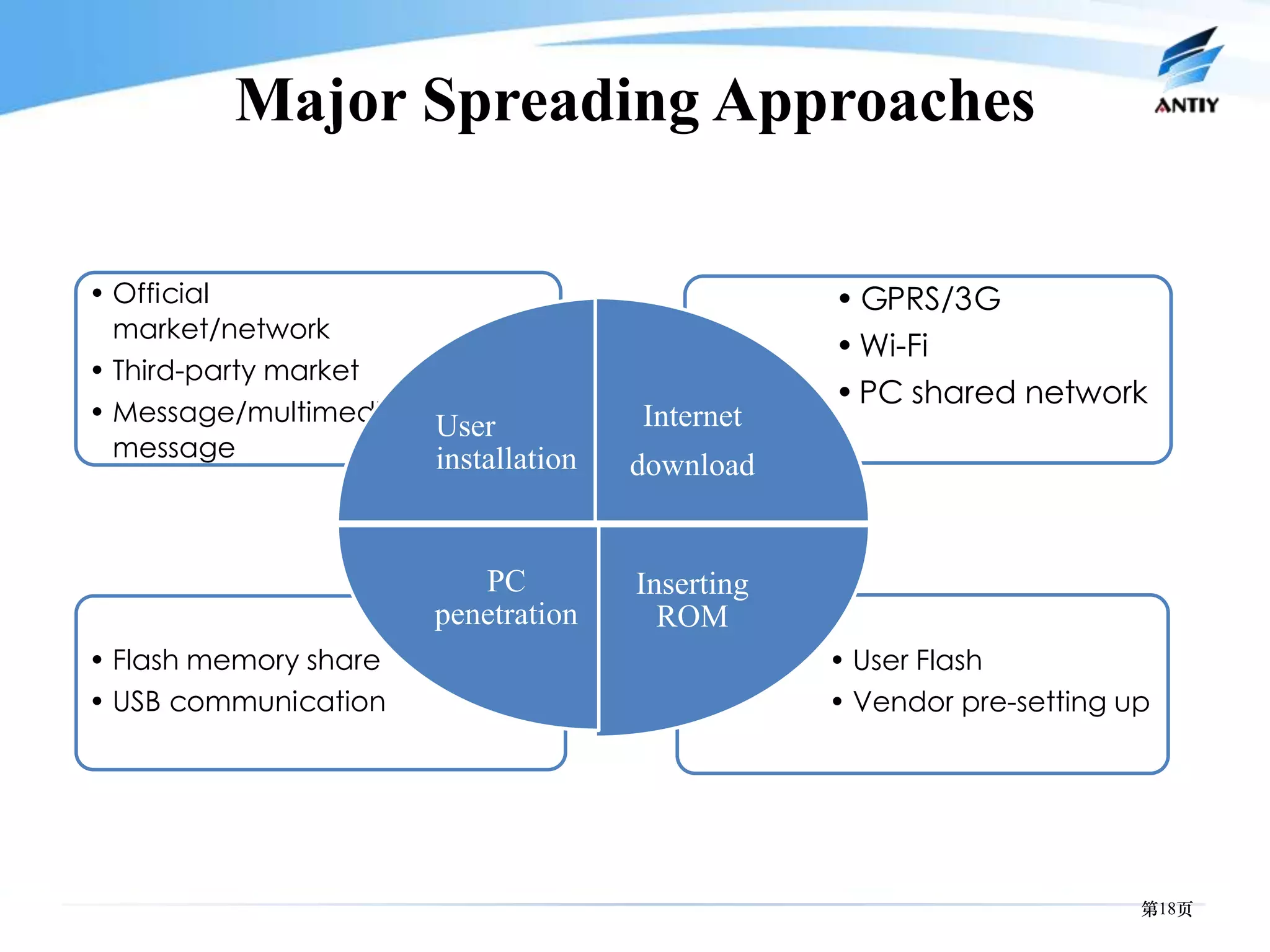
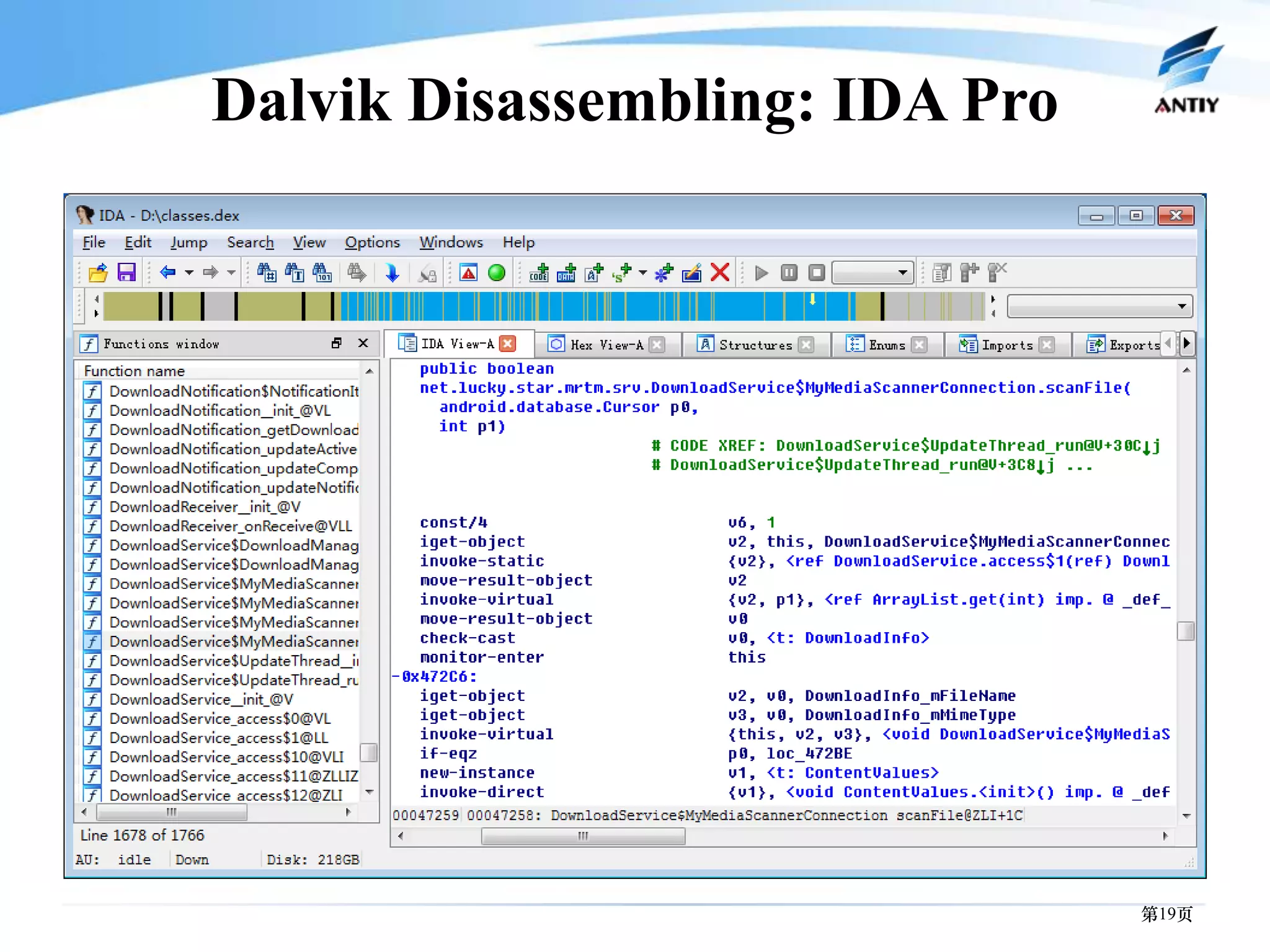
This document discusses malware threats on mobile platforms and provides 3 key points:
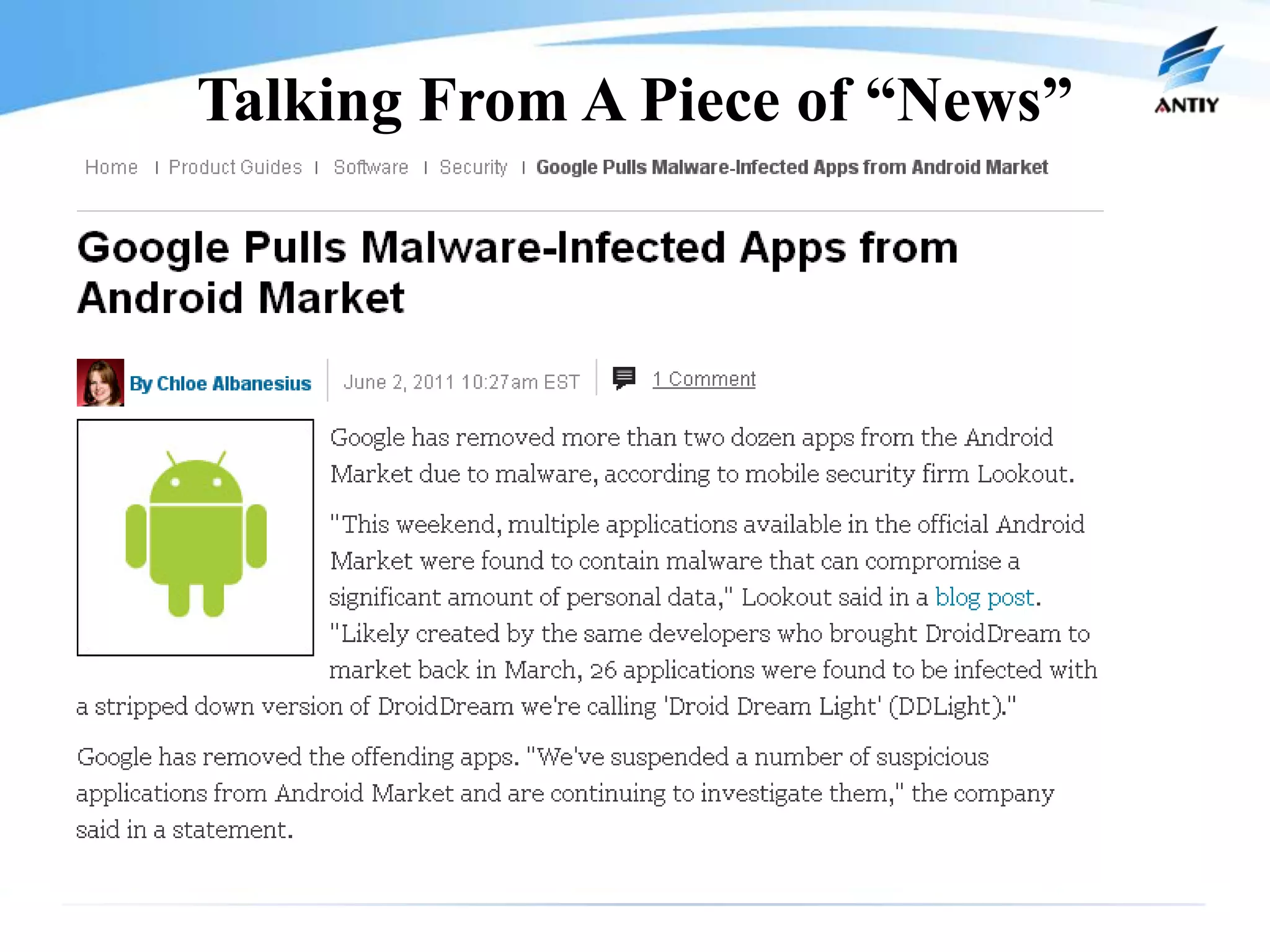
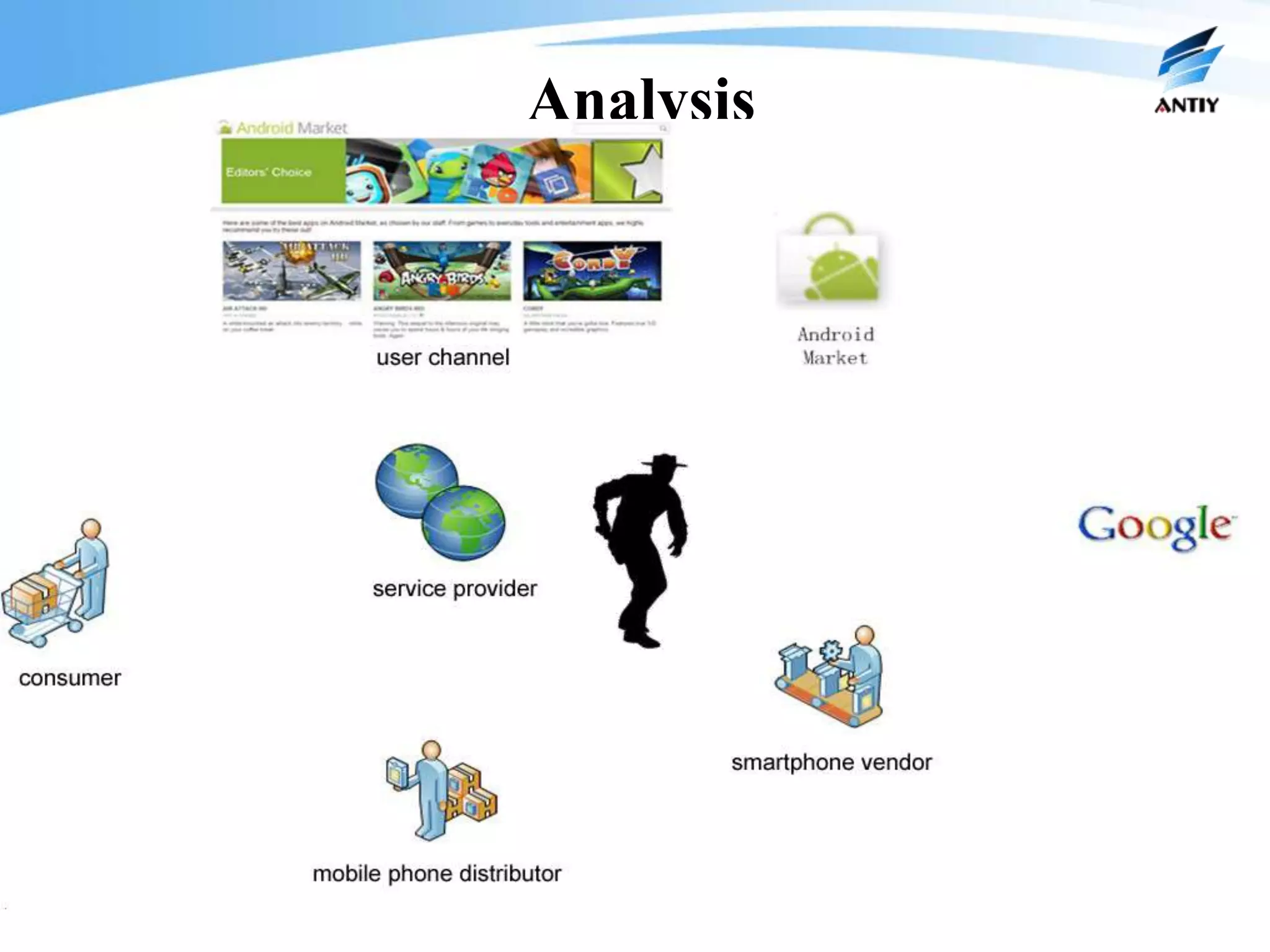
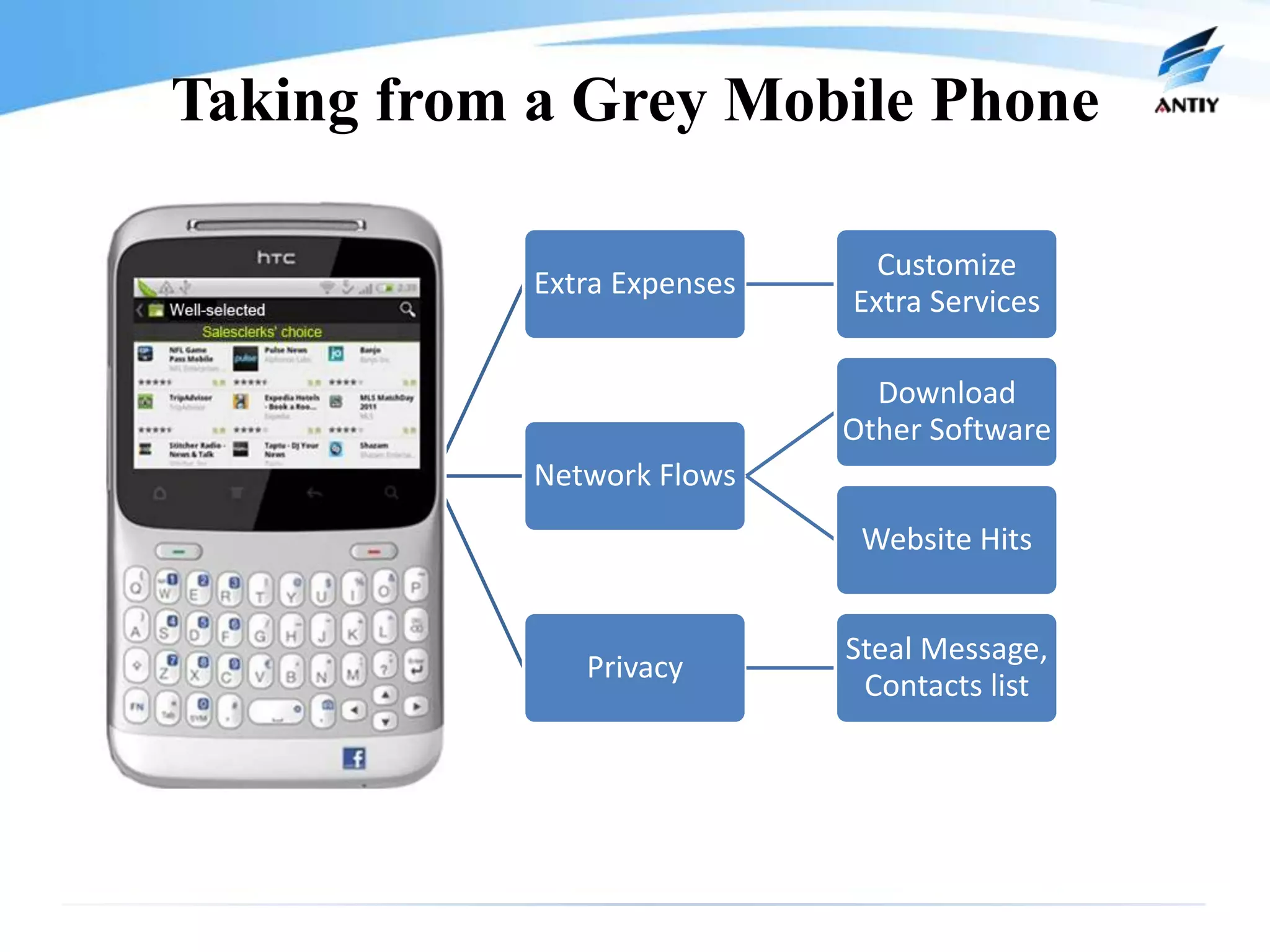
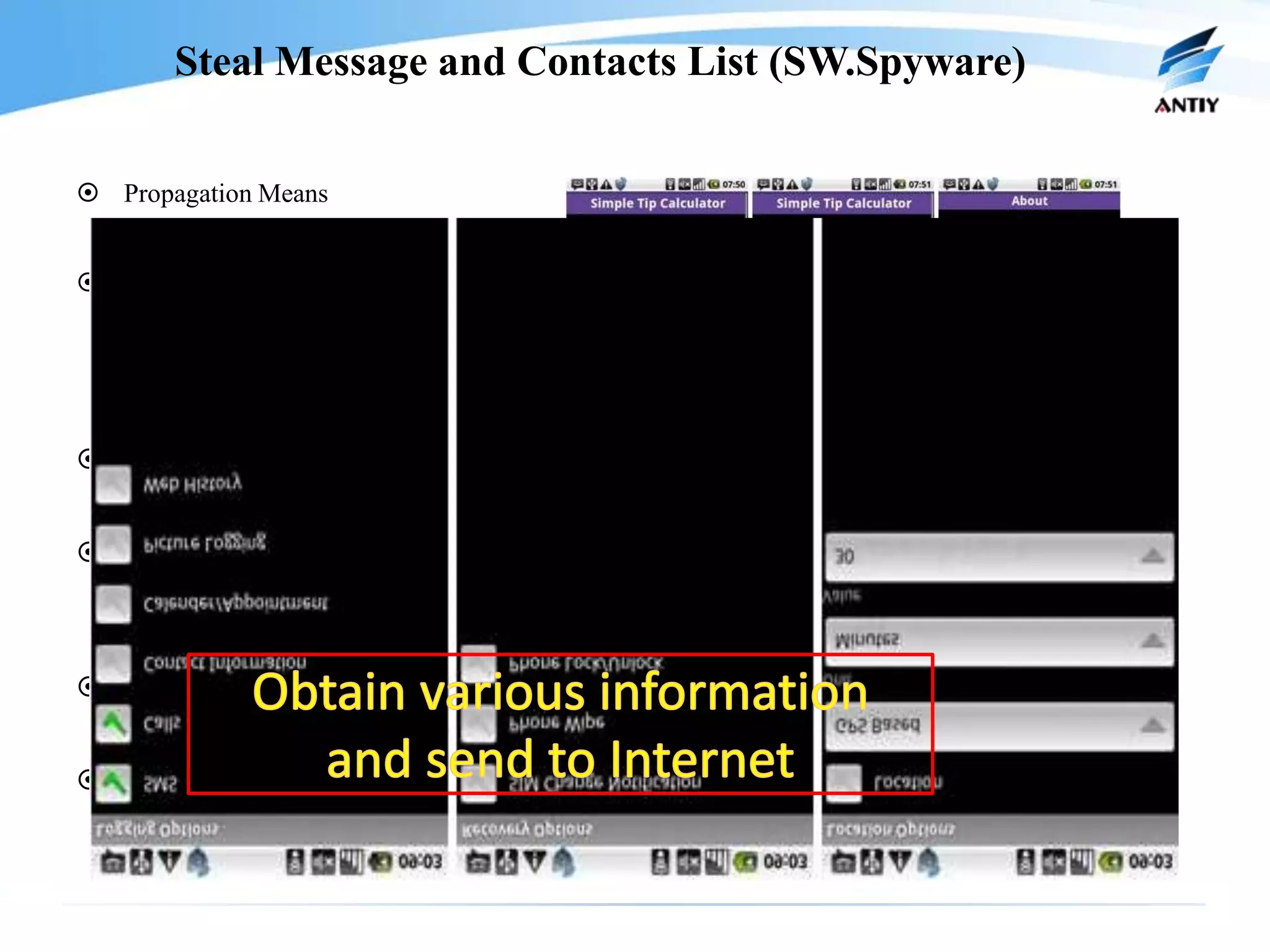
1. It describes new malware threats that disguise as news or other apps to install on mobile phones and steal private information like messages and contacts without the user's knowledge.
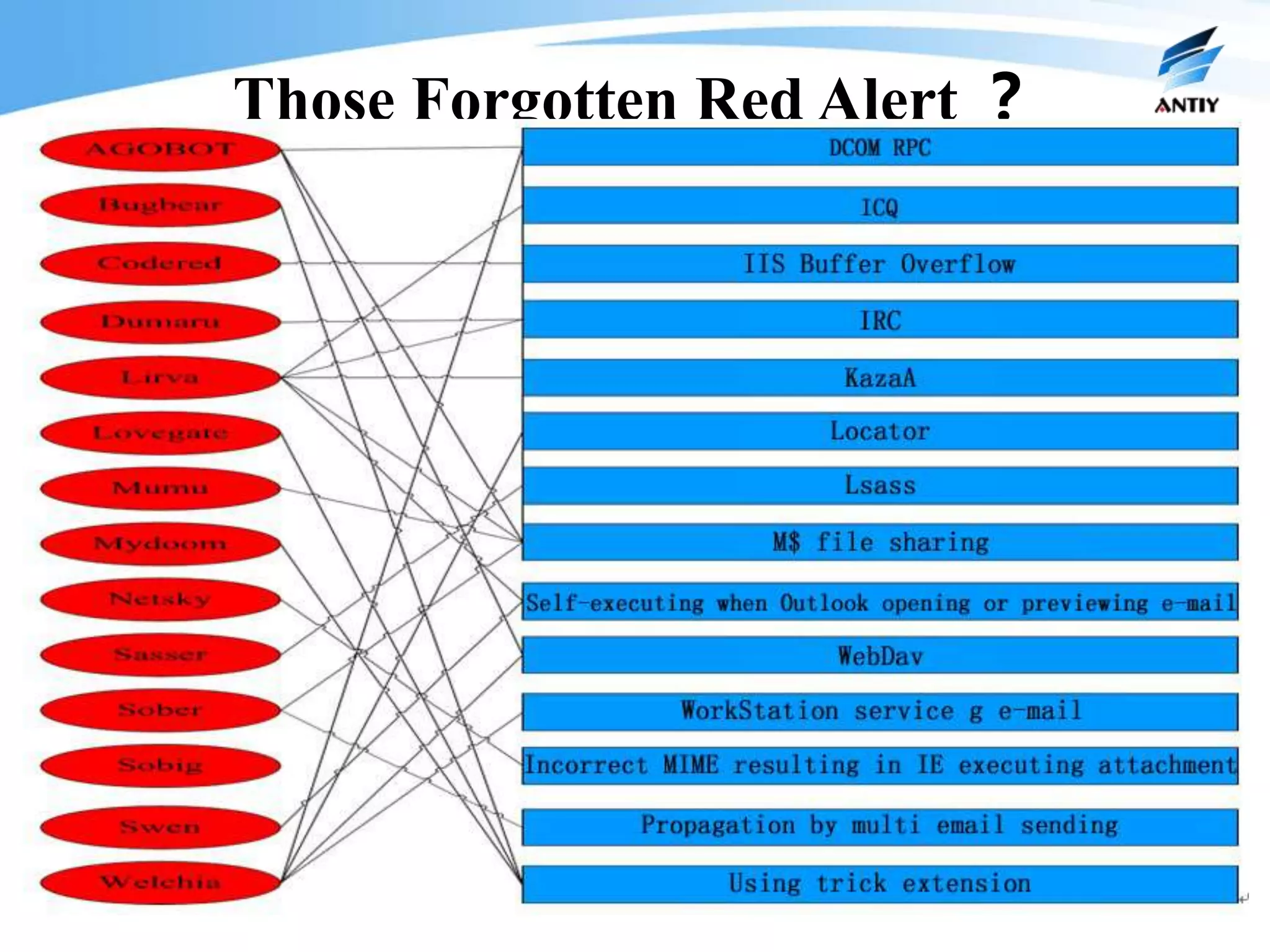
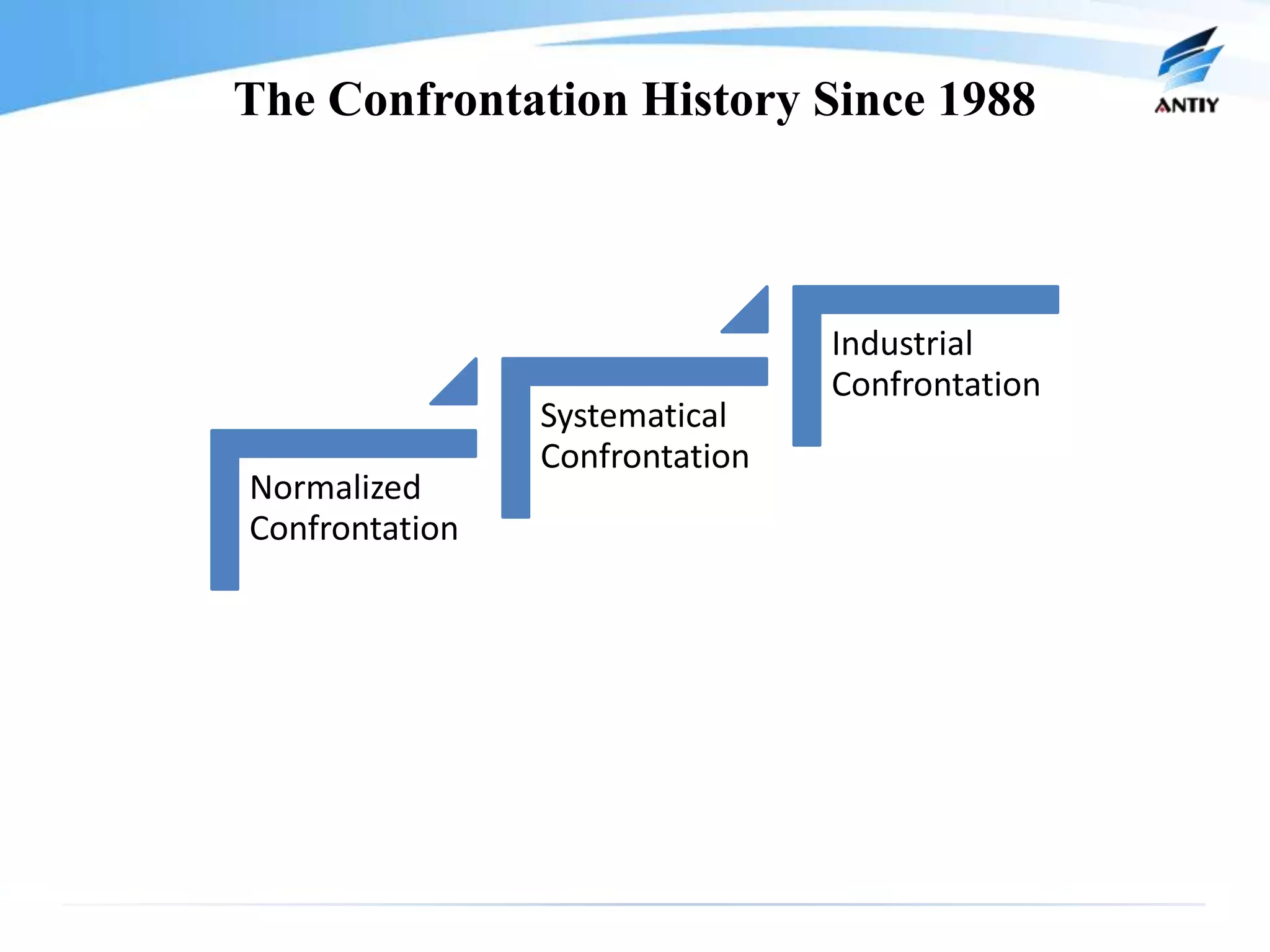
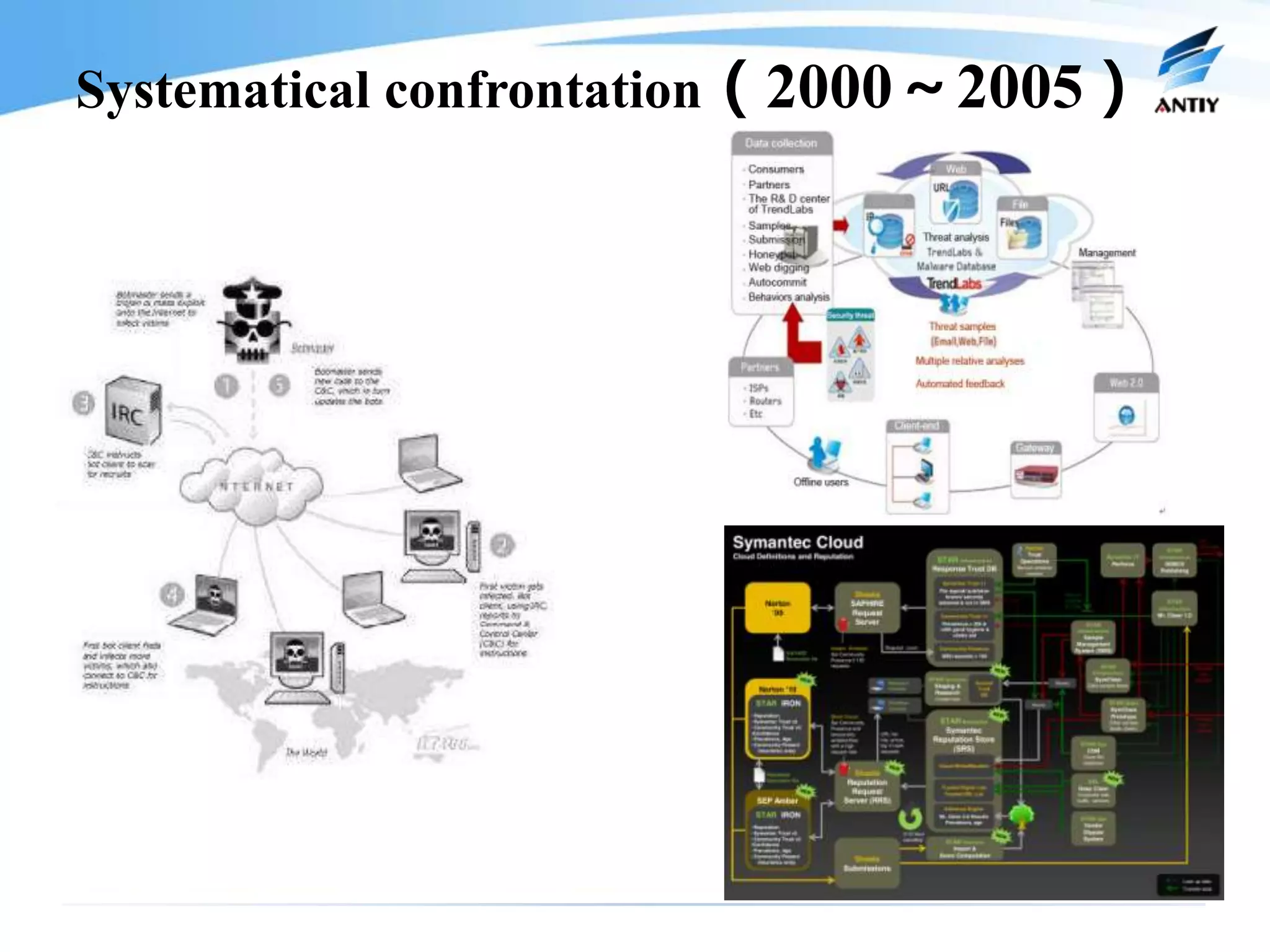
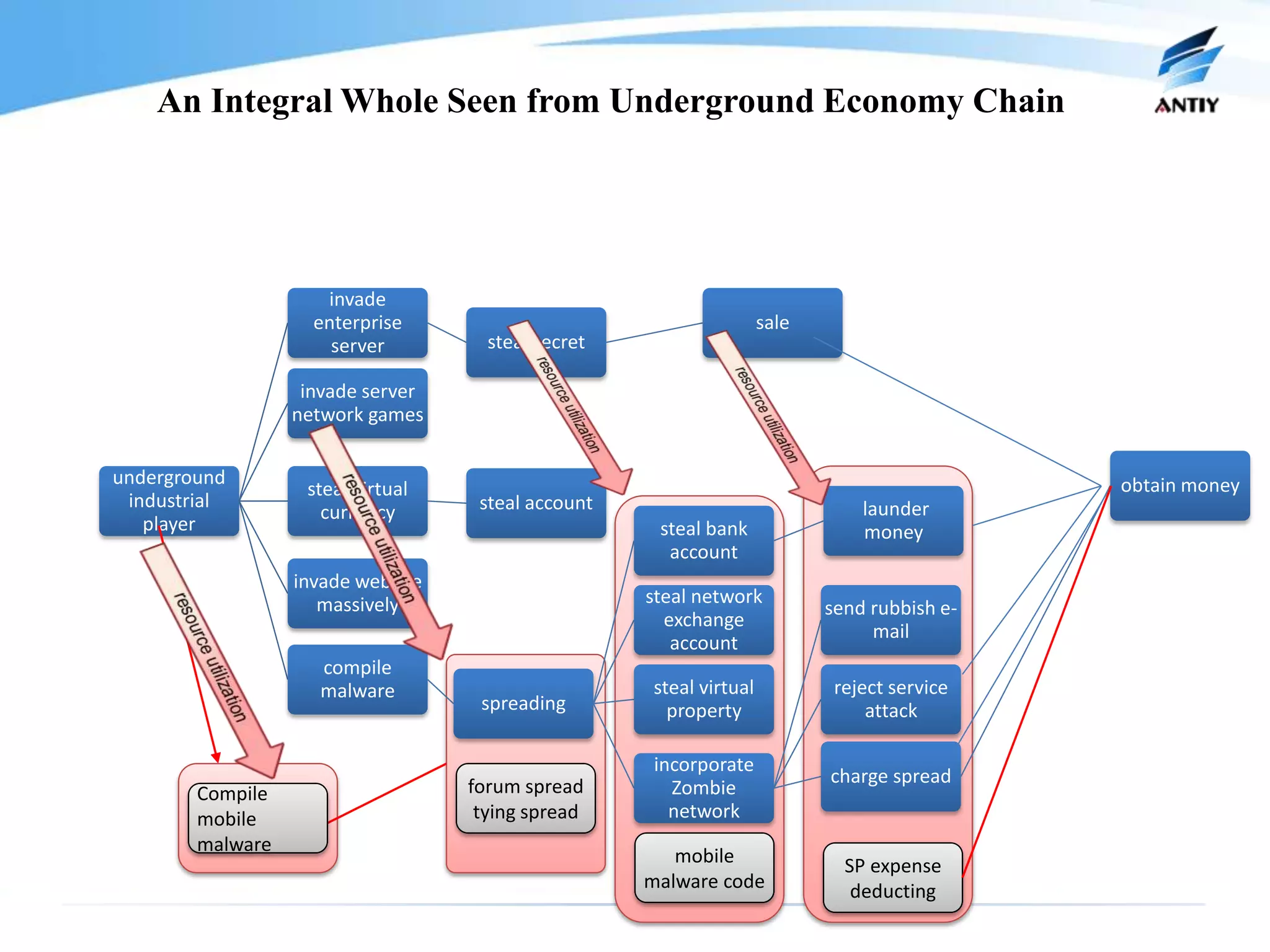
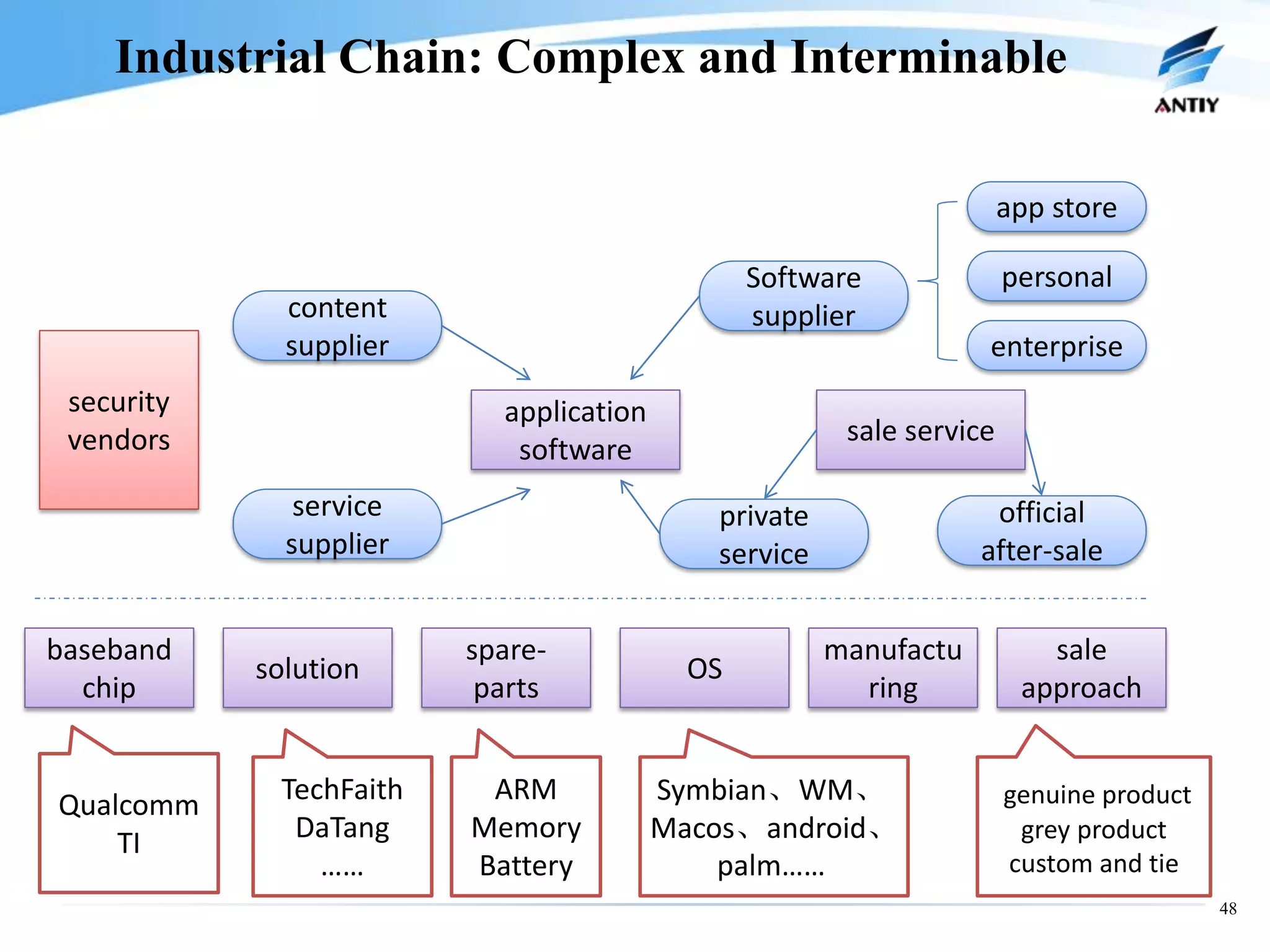
2. It analyzes the history of malware confrontation from the late 1980s to the present, noting the emergence of systematical confrontation using botnets in the 2000s and the current state of an underground industrial system.
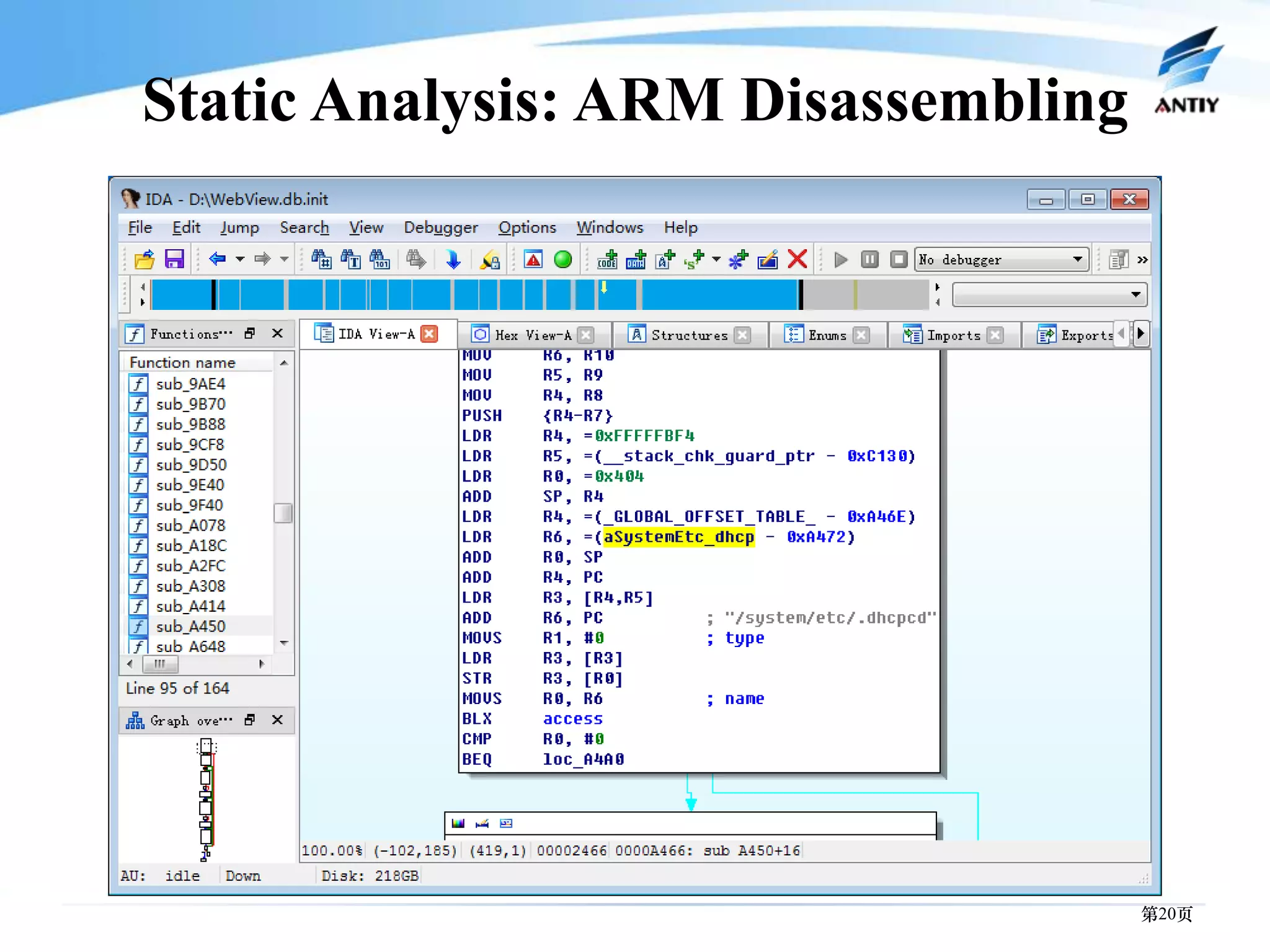
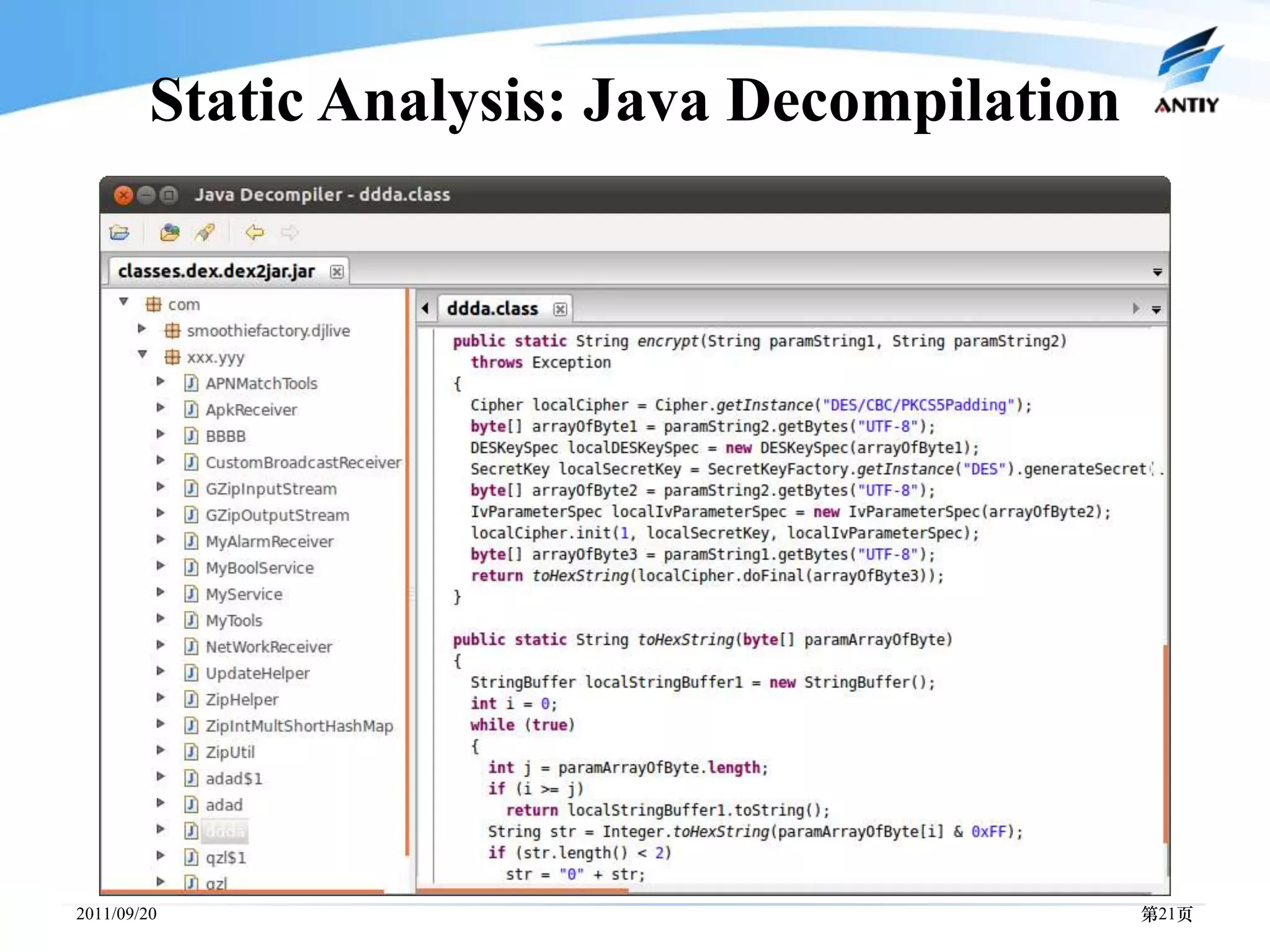
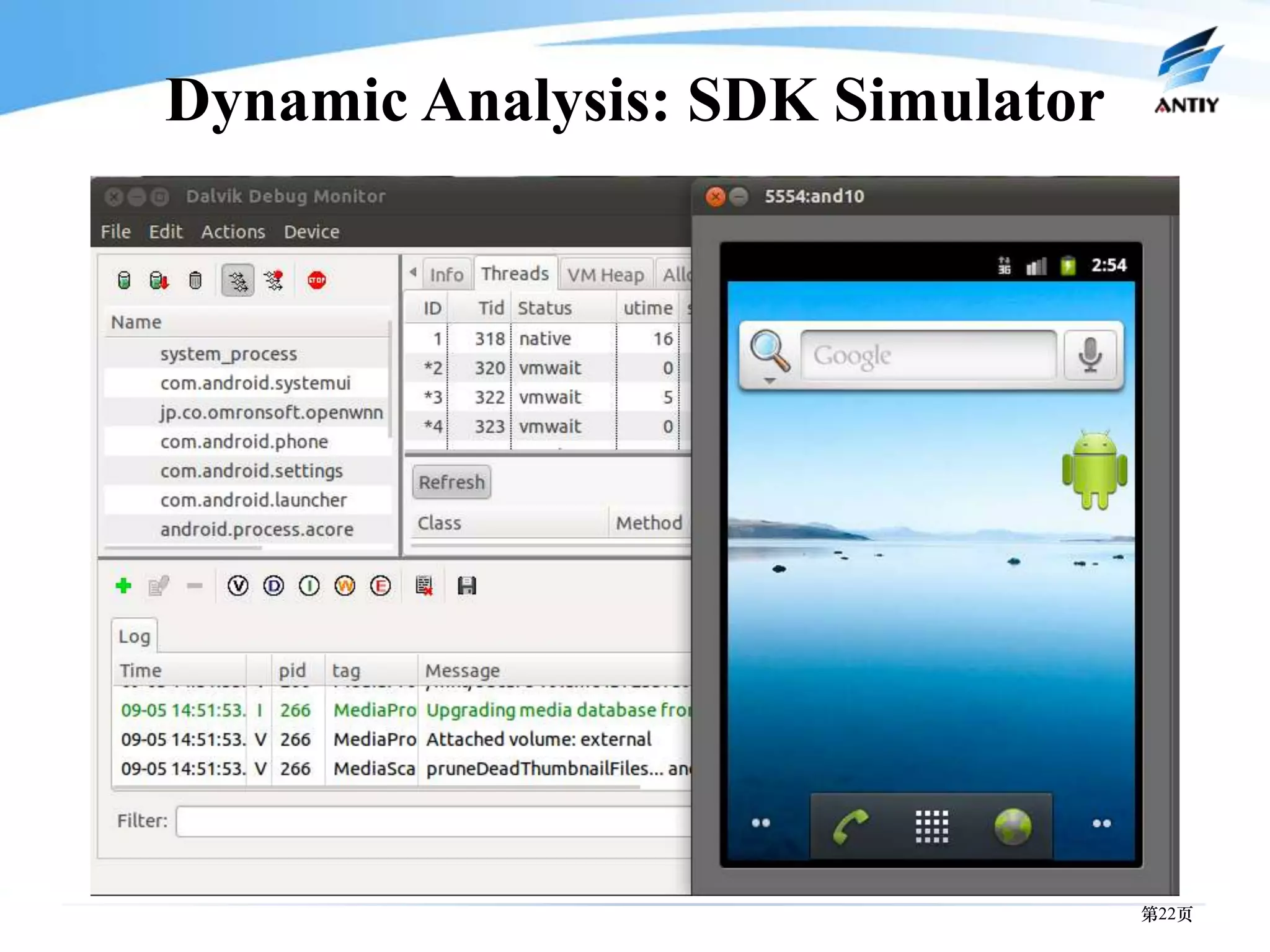
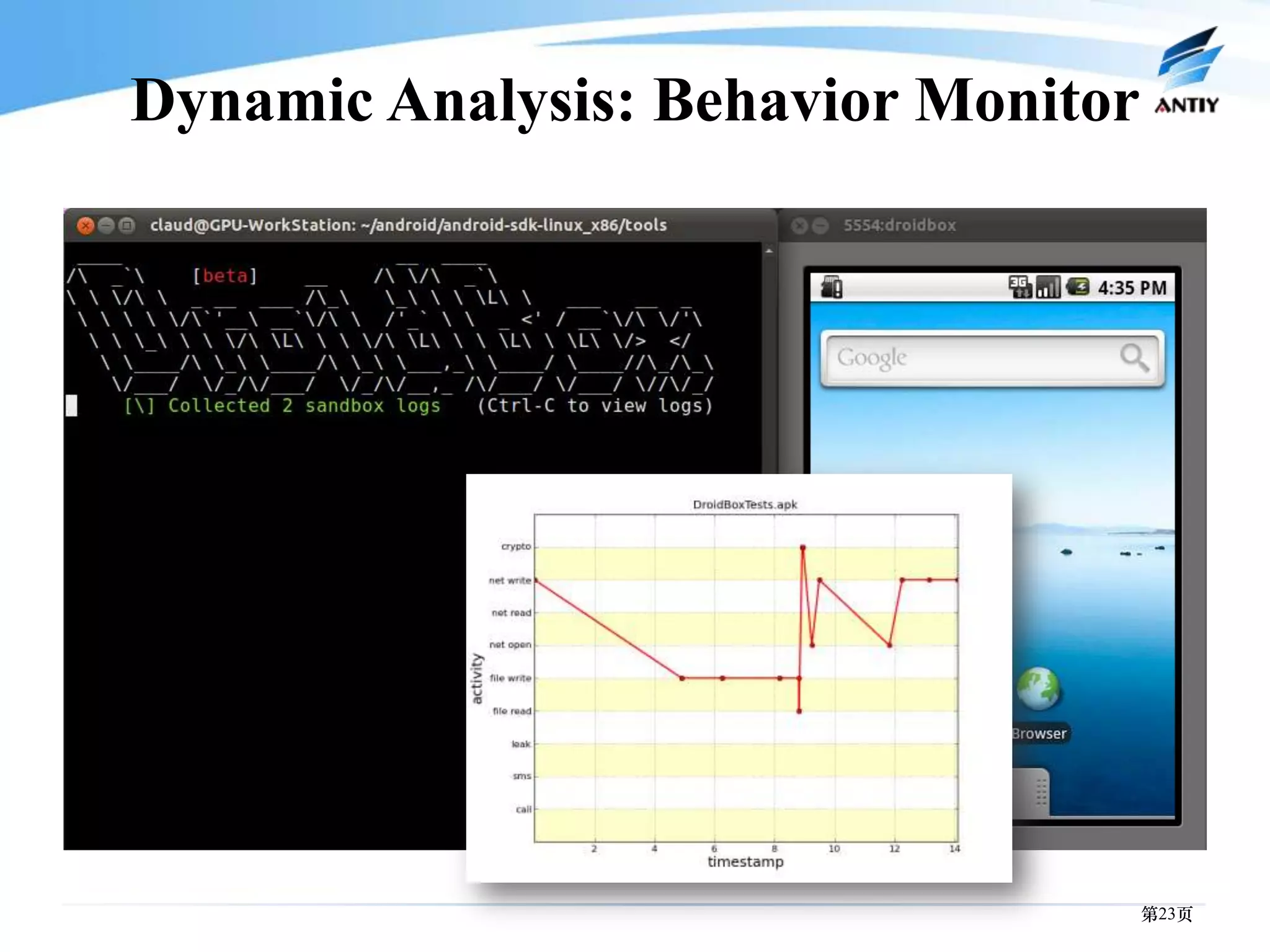
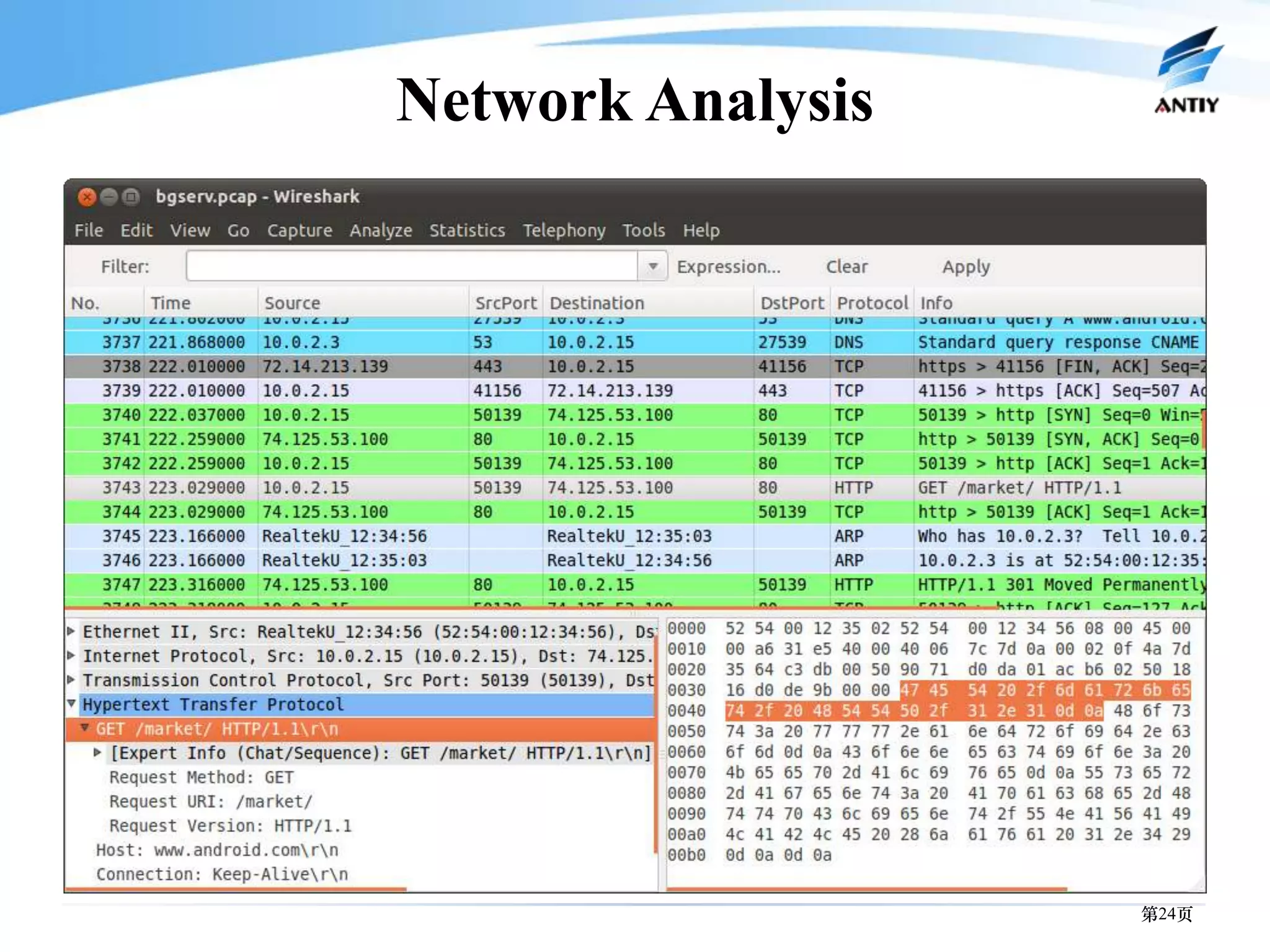
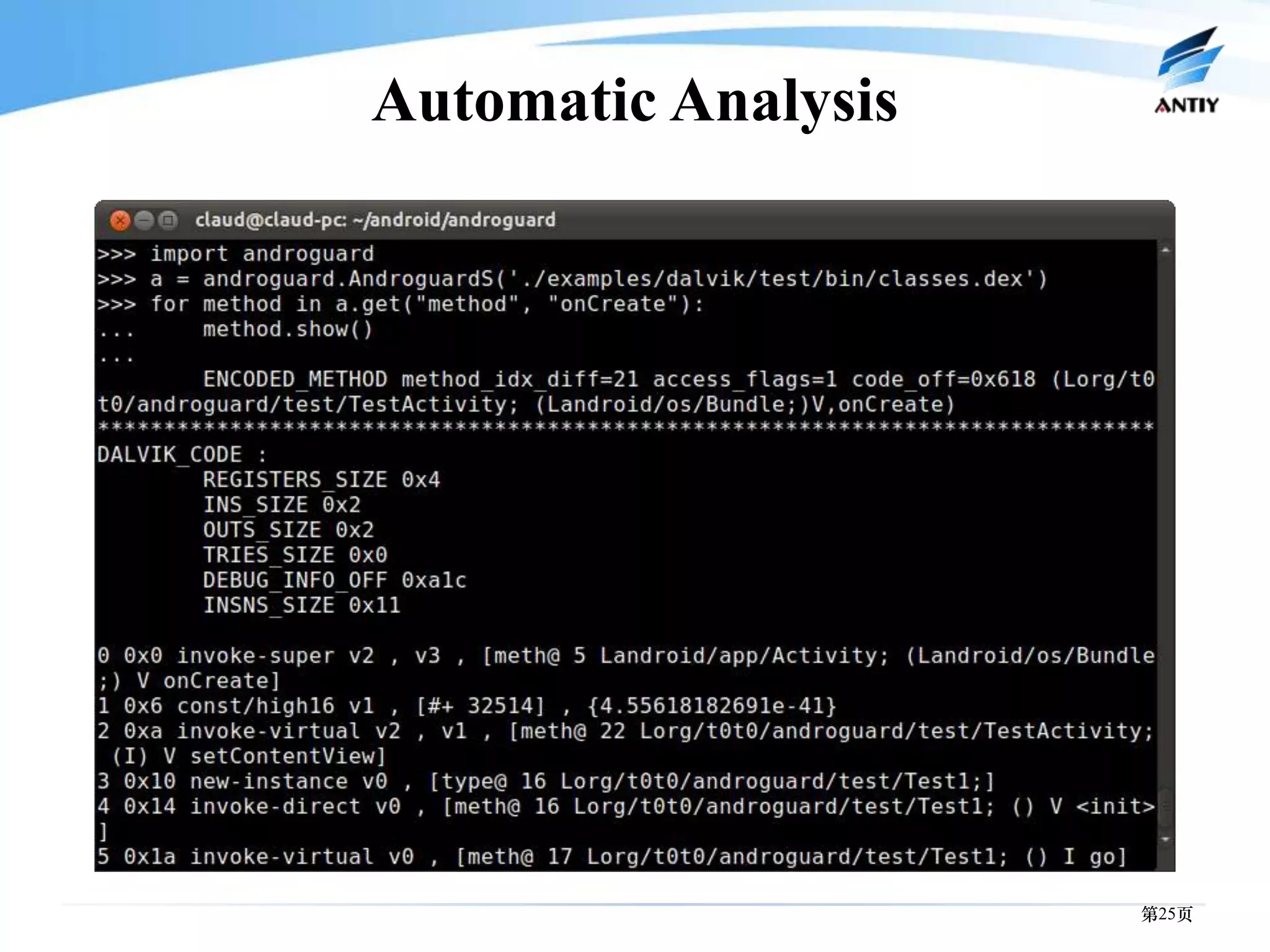
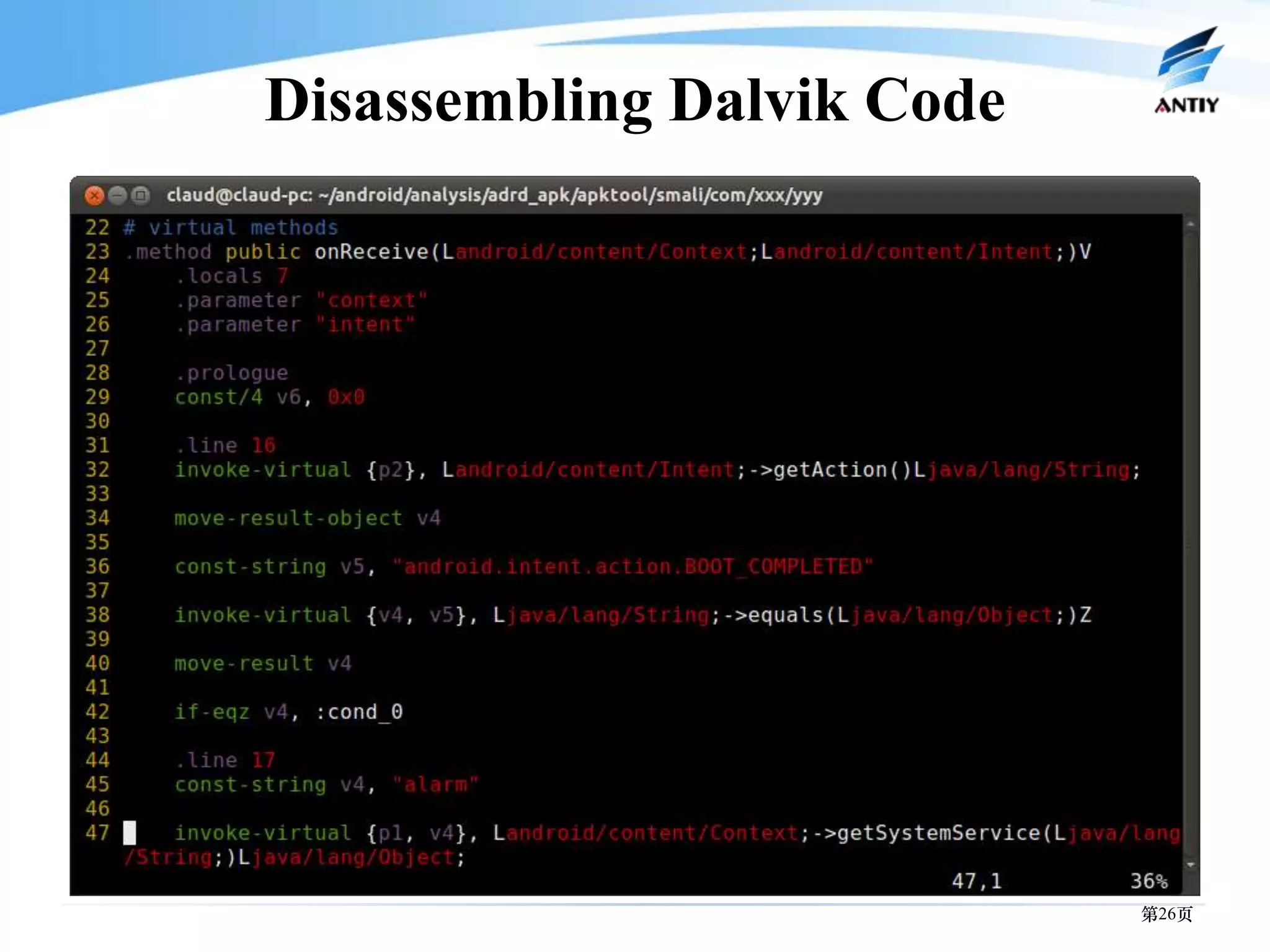
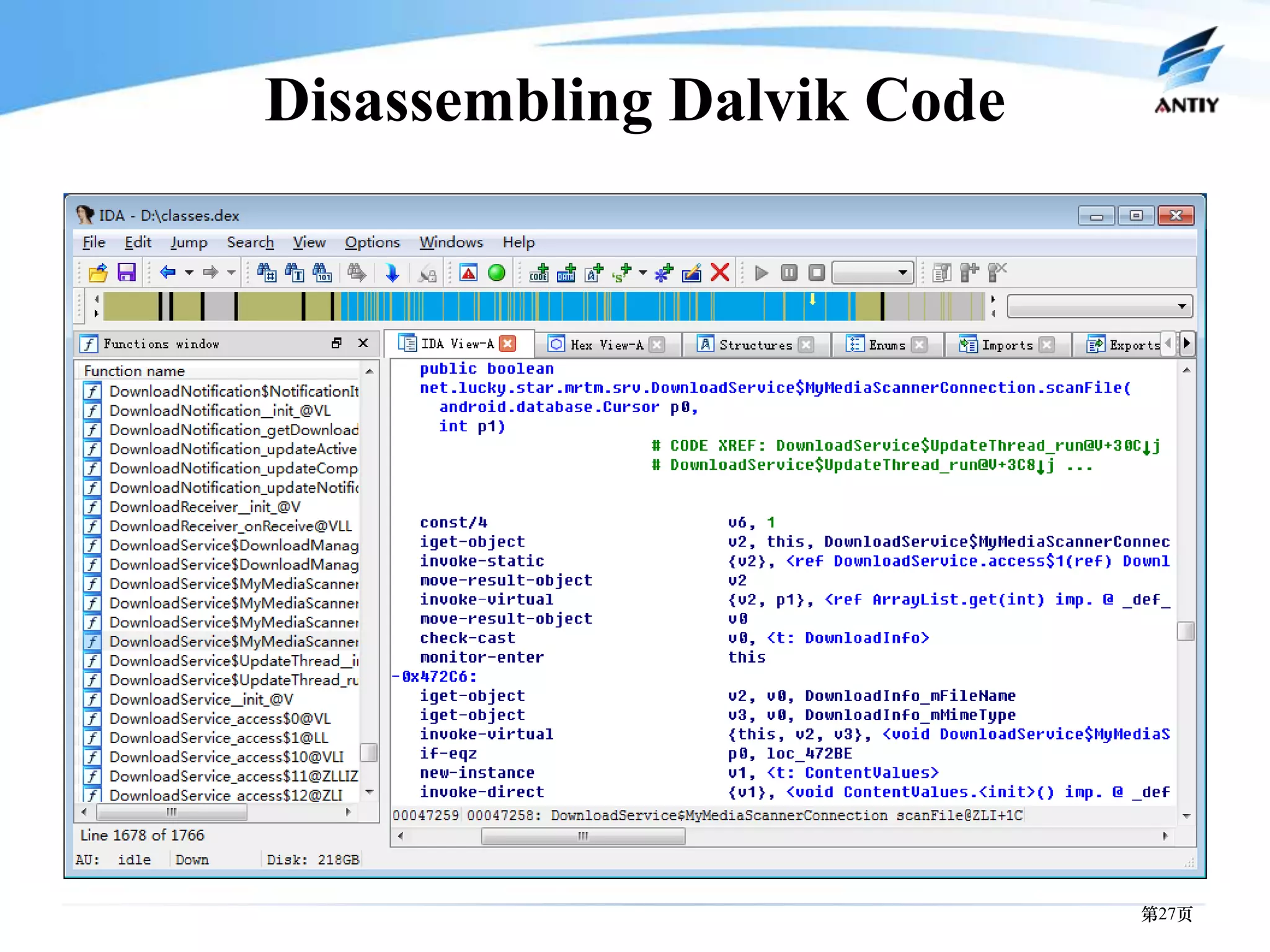
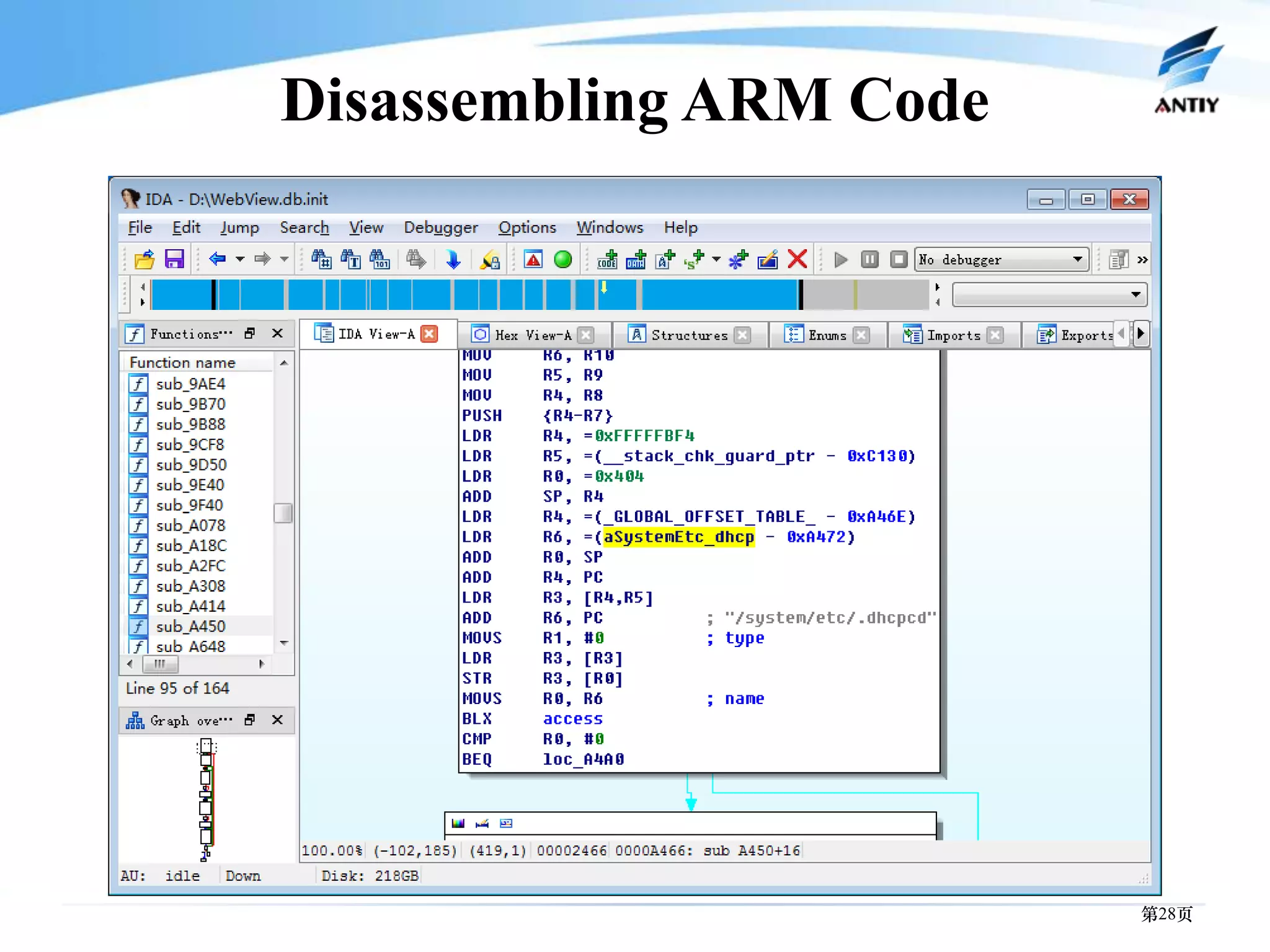
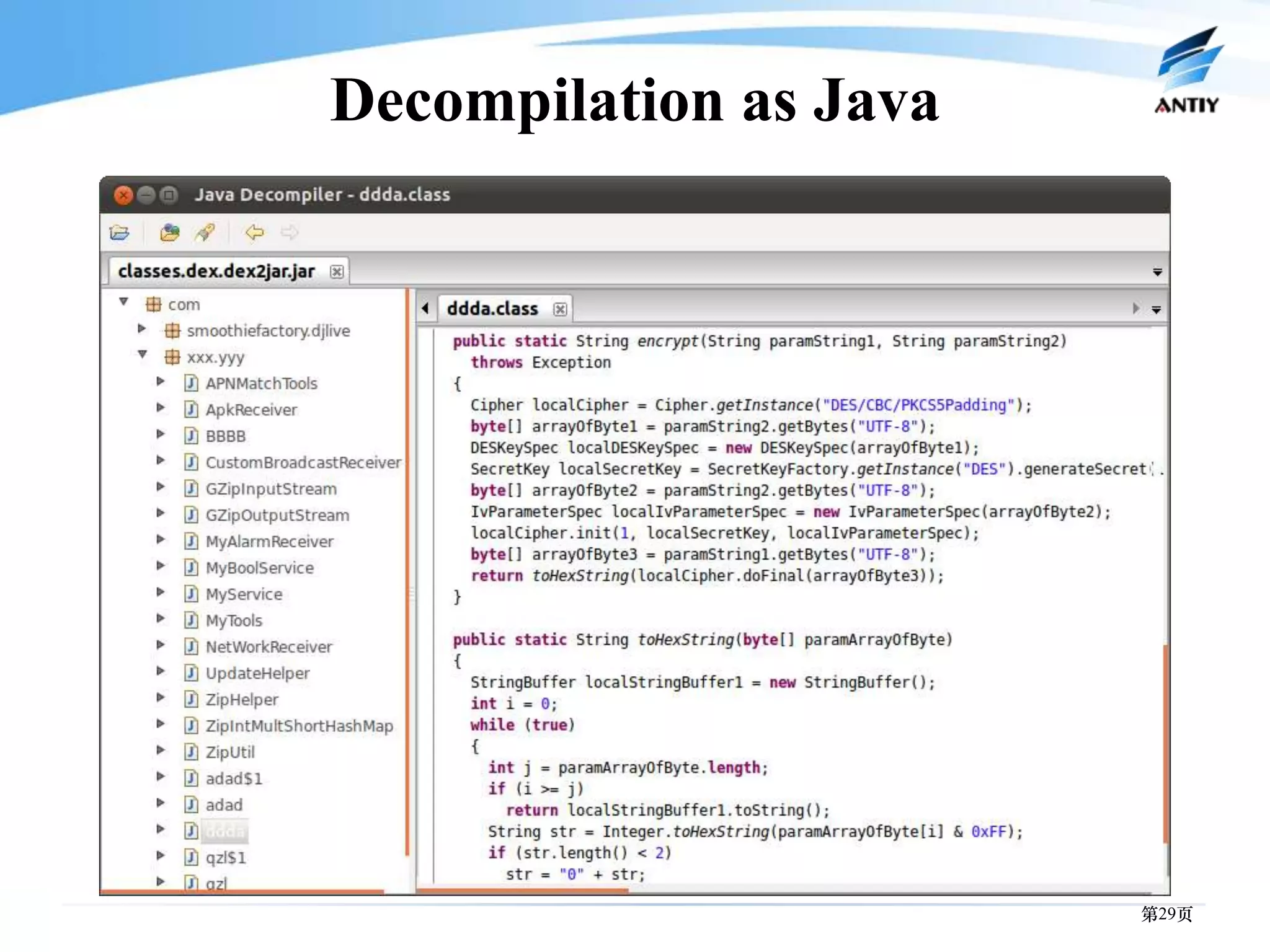
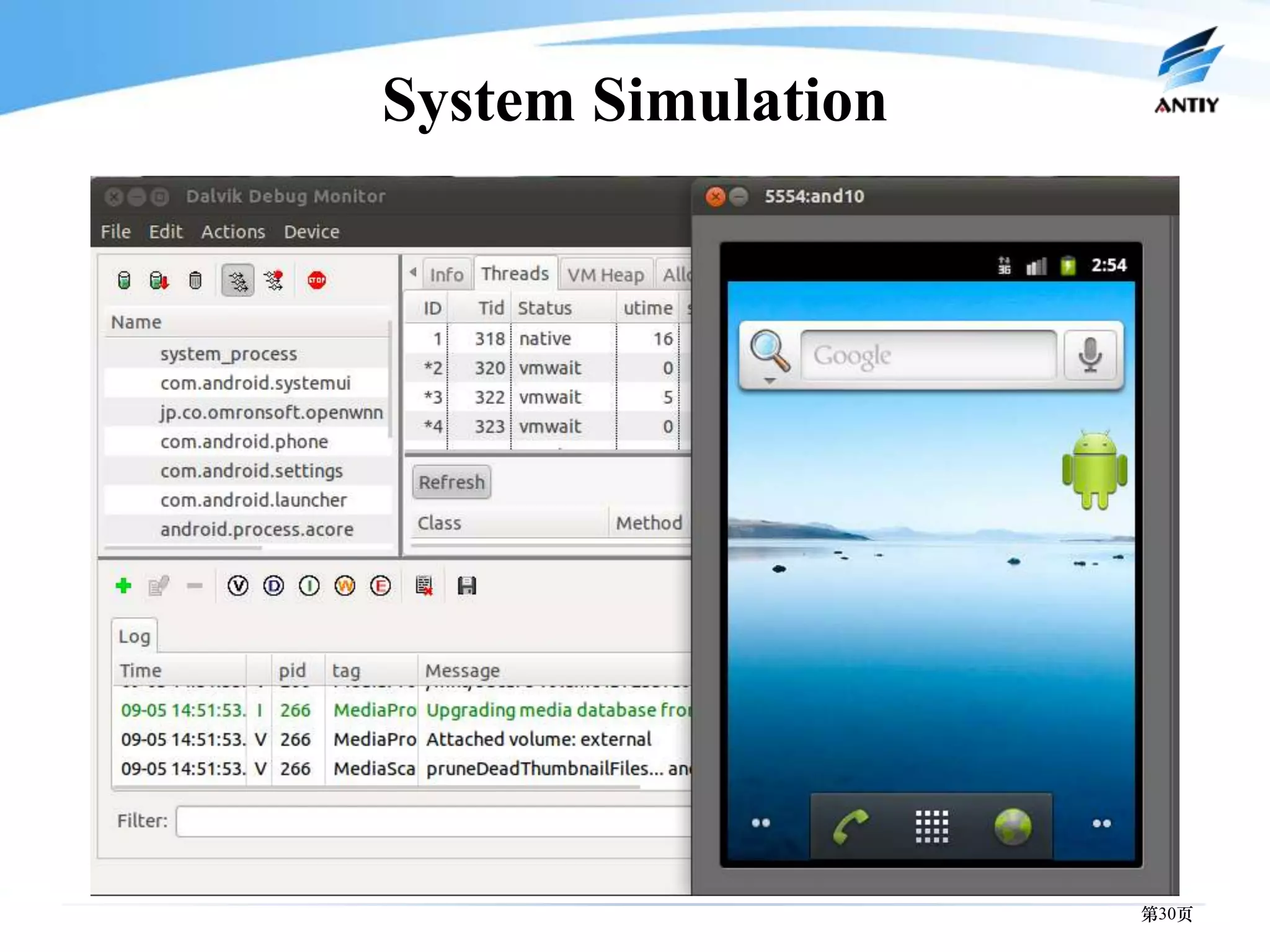
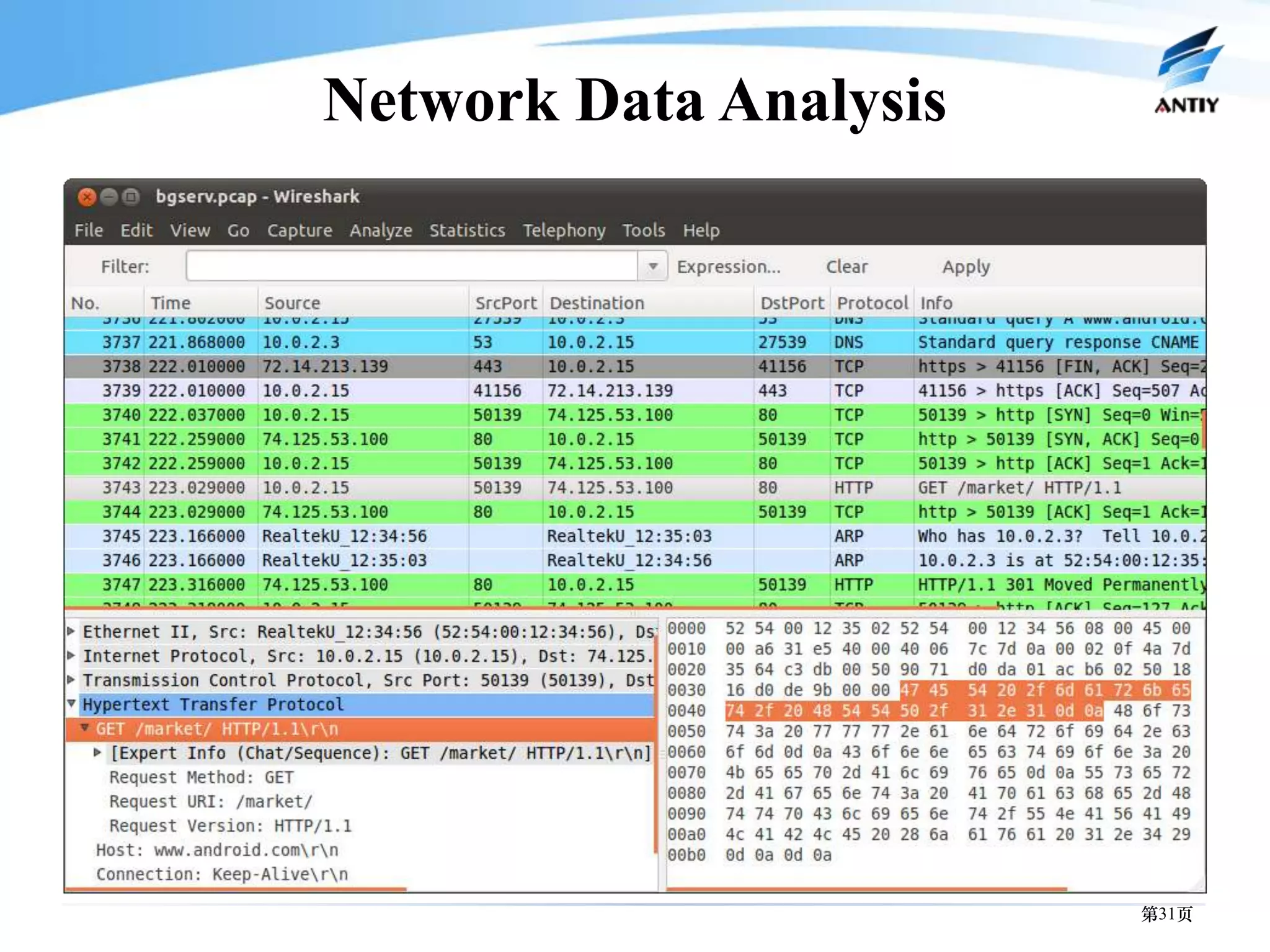
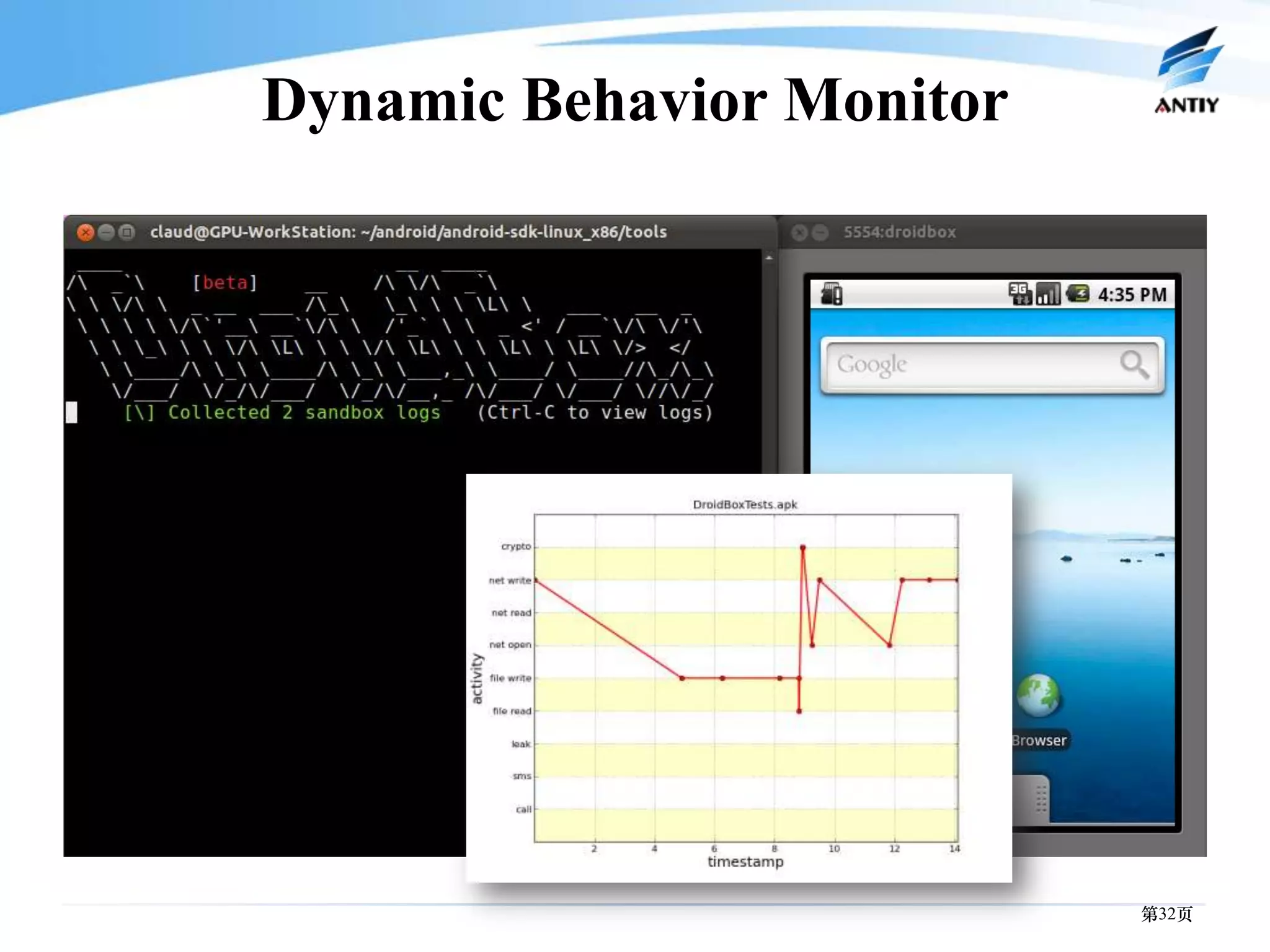
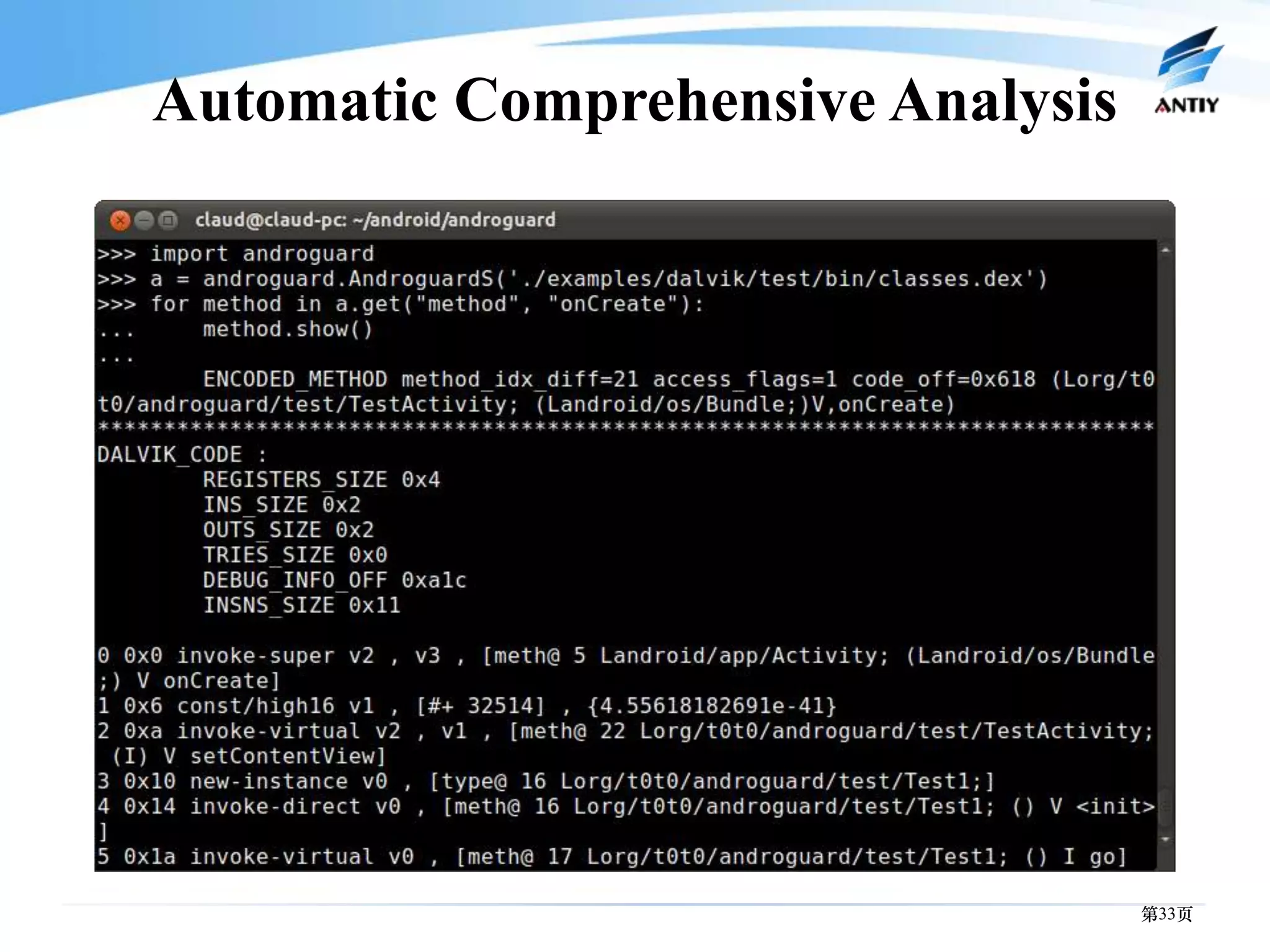
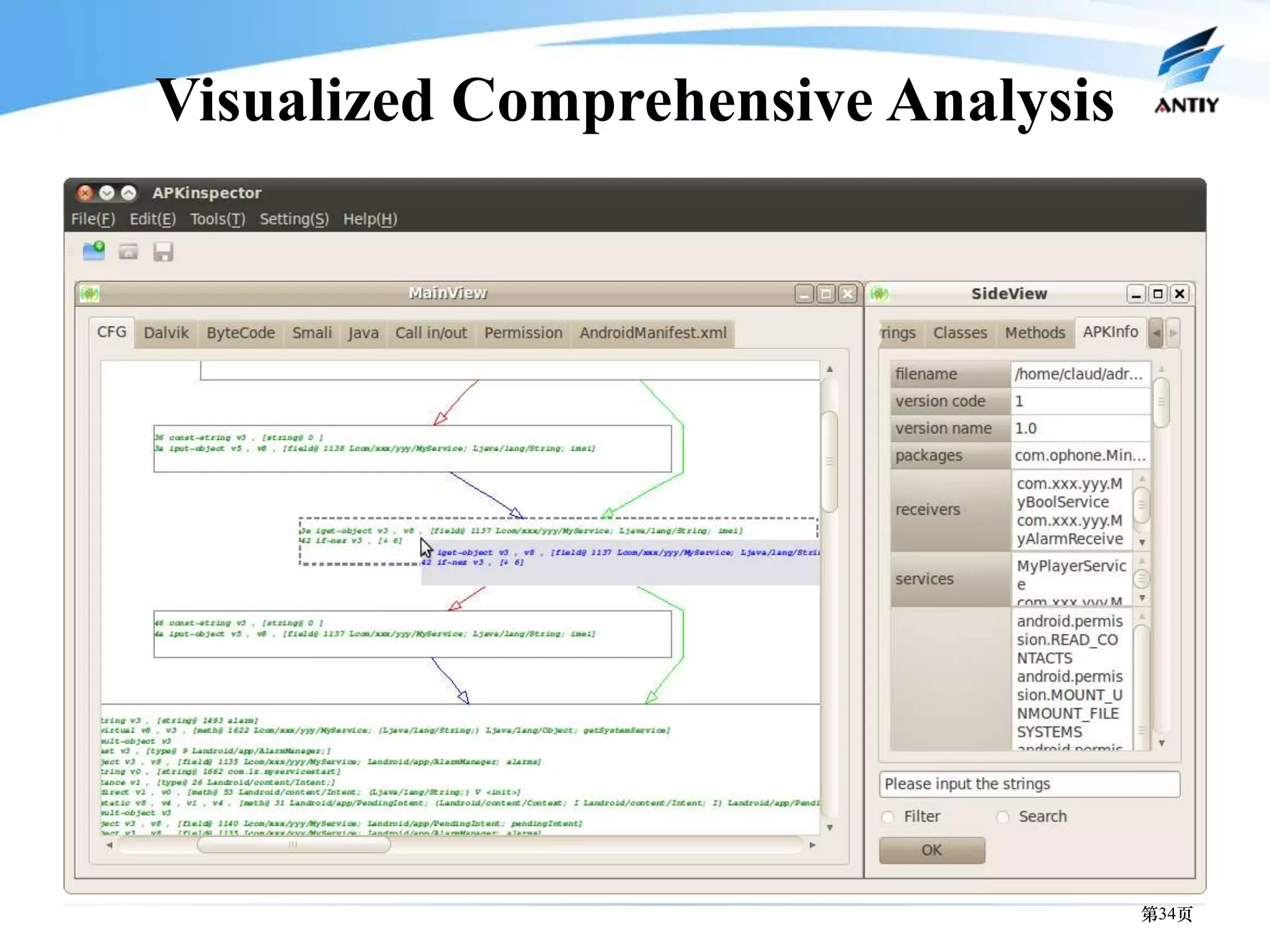
3. It outlines solutions for analyzing and detecting mobile malware through techniques like disassembling code, behavior monitoring, and automatic comprehensive analysis to understand malware behavior and provide security.



![Information
Analysis on Malware
Name com.google.android.providers.enhancedgooglesearch
Chinese Name
Original Name a.apk
URL Source
Collection
Source
System
Android
Platform
Format apk
MD5 Value BFBB58D0F8B487869393A0244AE71AFC
CRC32 Value C1C12A99
SHA1 Value 59EE114166CDBCDDB88B38299934021080053D86
Bytes
Malware Information
Name Trojan/Android.droiddg.a[rmt,sys]
CNCERT Name a.remote.droiddg.a
Chines Name
Other Names None
Original/Tied Firmware embedding
Threat type remote system](https://image.slidesharecdn.com/mobile-malware-industrial-viewslide-121105005331-phpapp01/75/Malware-in-Mobile-Platform-from-Panoramic-Industrial-View-7-2048.jpg)

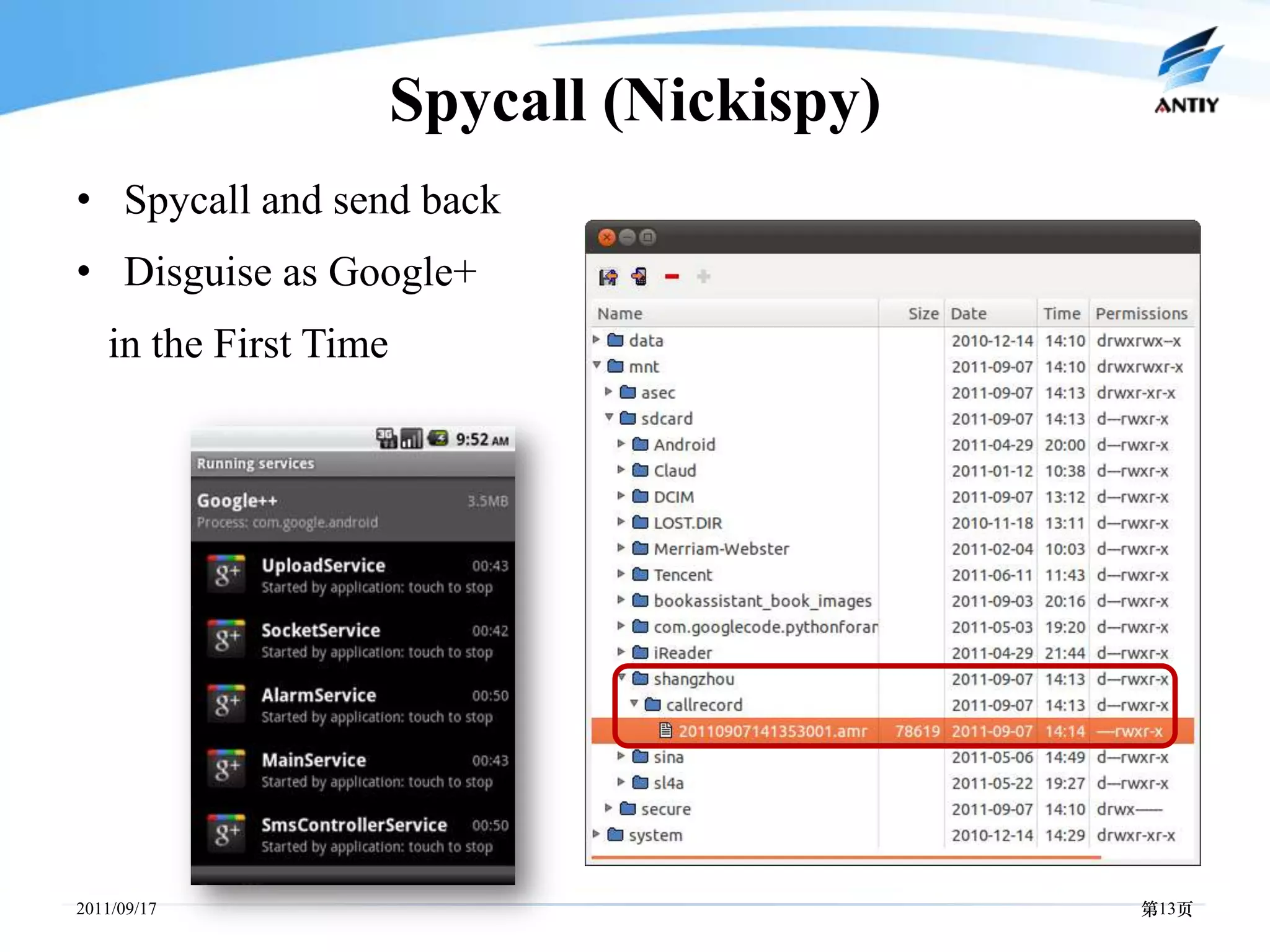
![Form Control System(Adrd)
• Trojan/Android.Adrd.a[exp]
Issue the control command
and the malware trigger
command
Provide the data-accessing
address URL needed by
malware behavior
Provide the parameter data
needed by malware behavior
Provide updating service for
malware files](https://image.slidesharecdn.com/mobile-malware-industrial-viewslide-121105005331-phpapp01/75/Malware-in-Mobile-Platform-from-Panoramic-Industrial-View-14-2048.jpg)