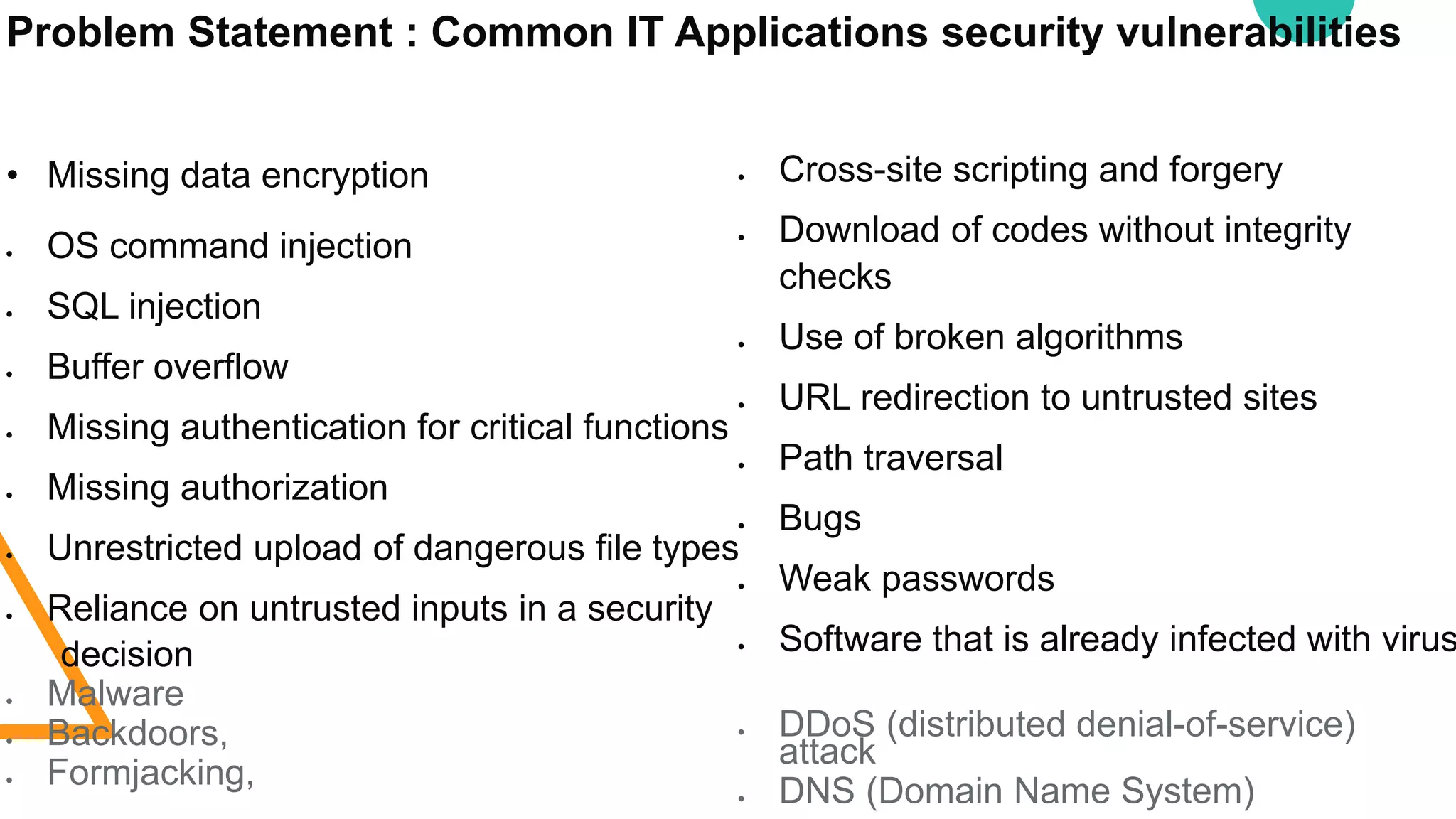
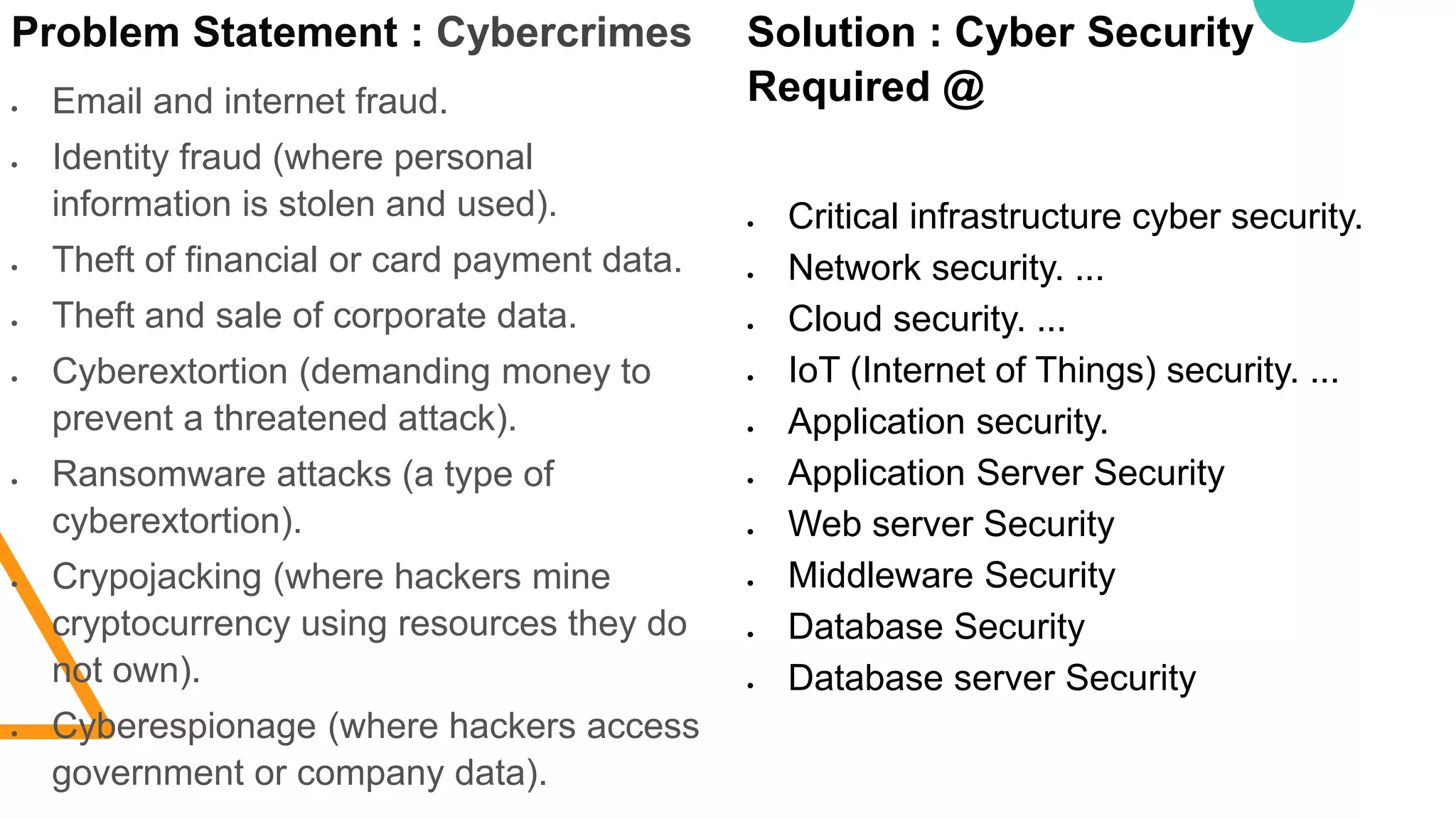
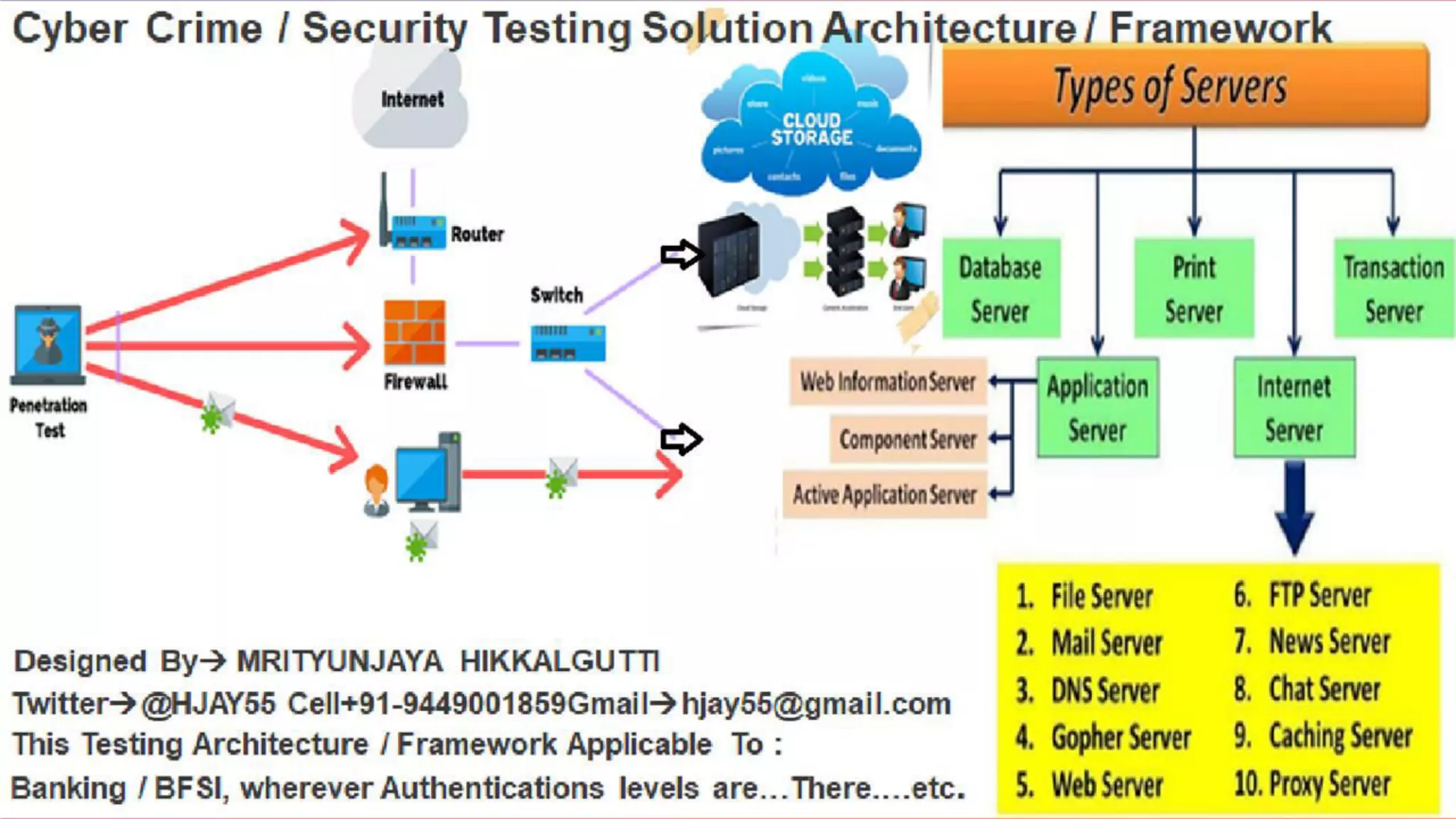
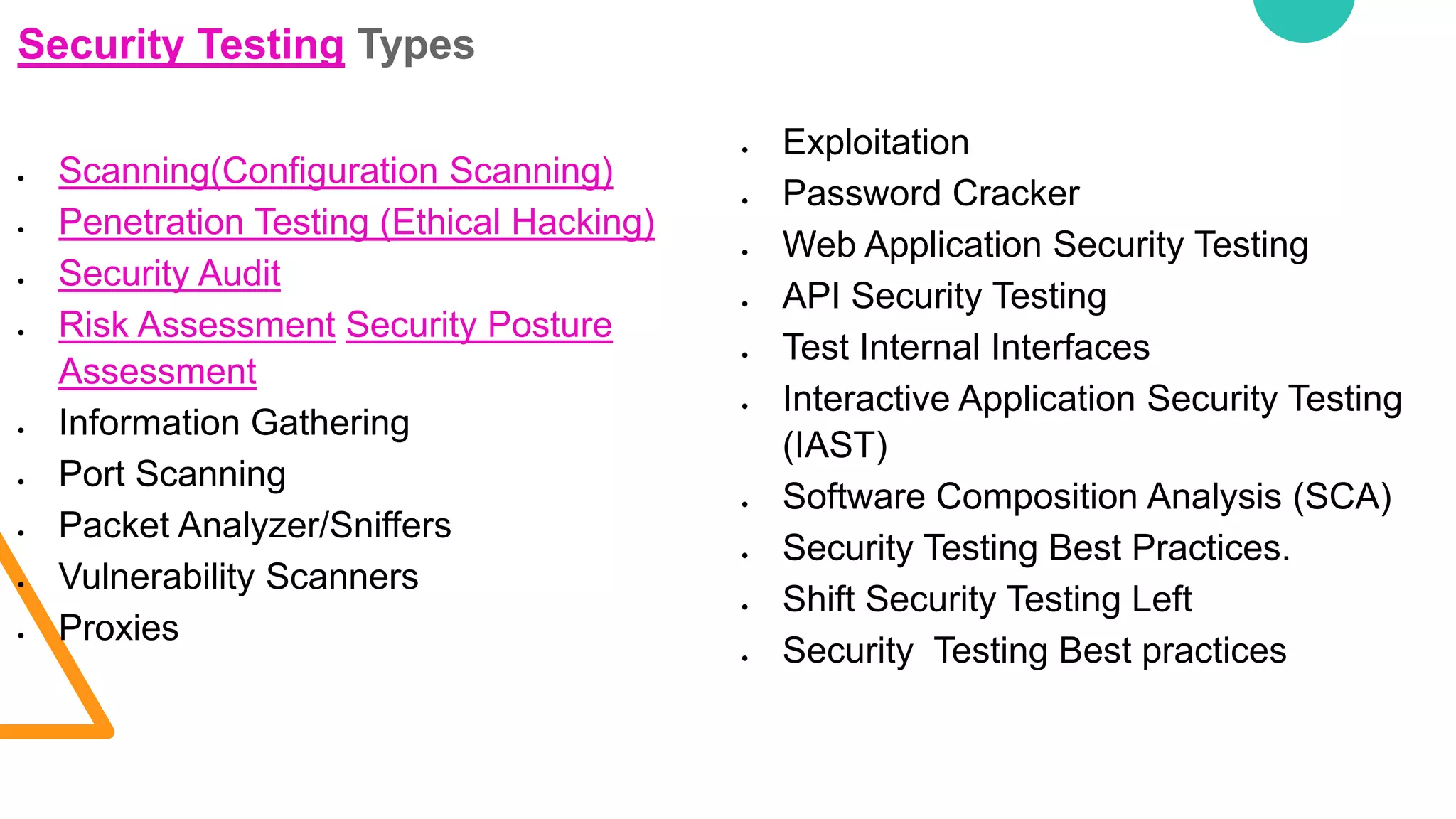
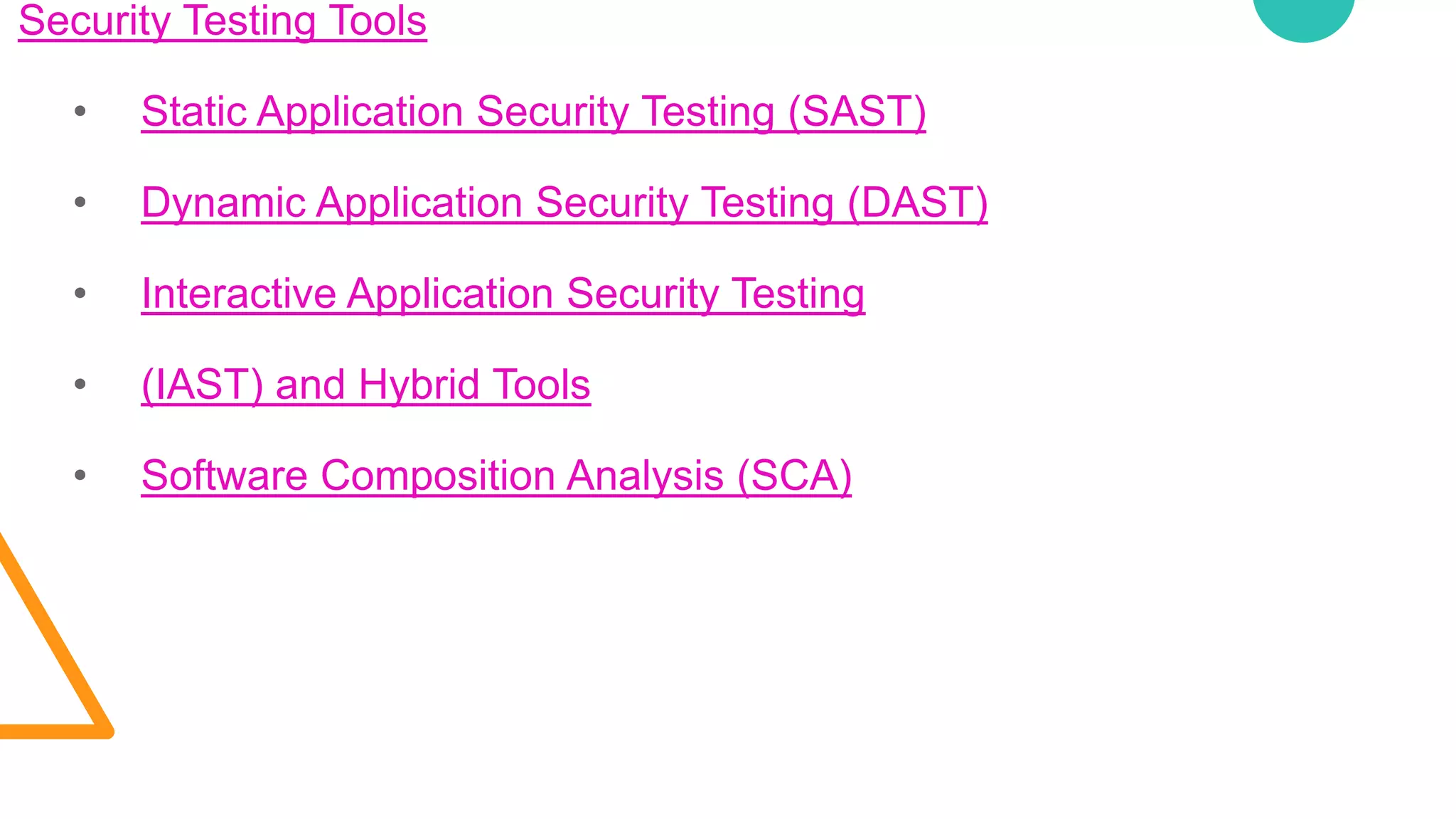
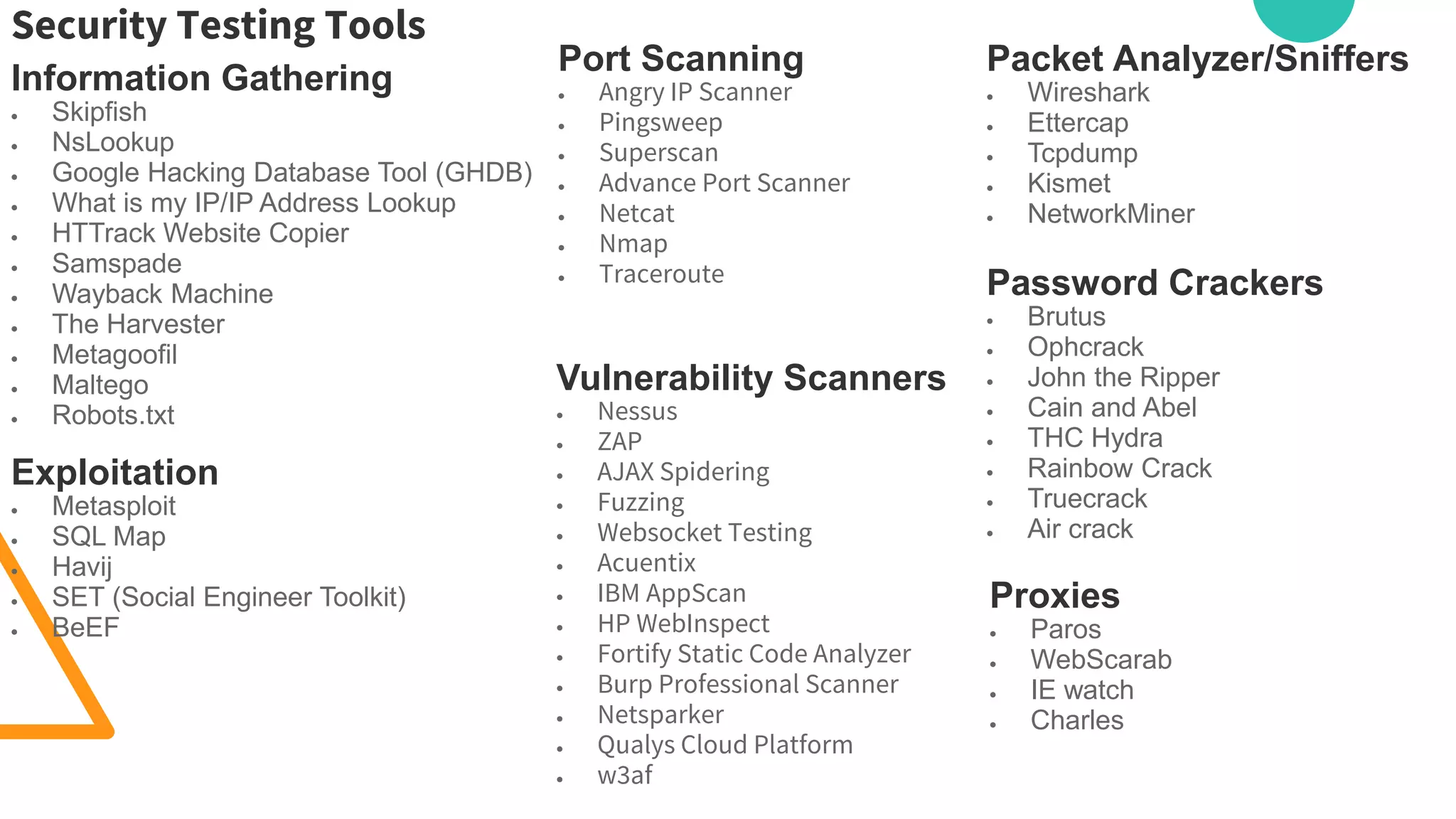
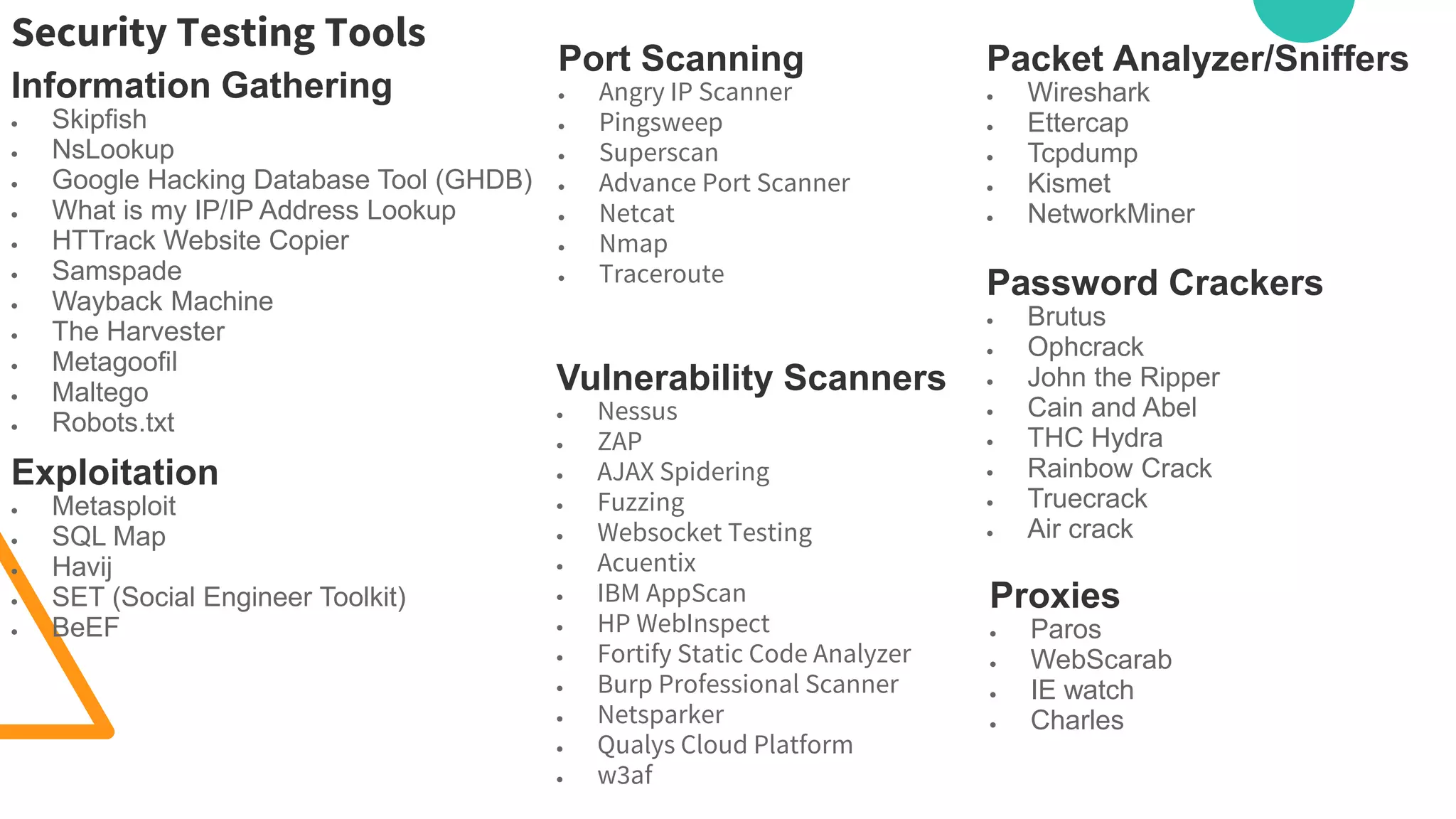
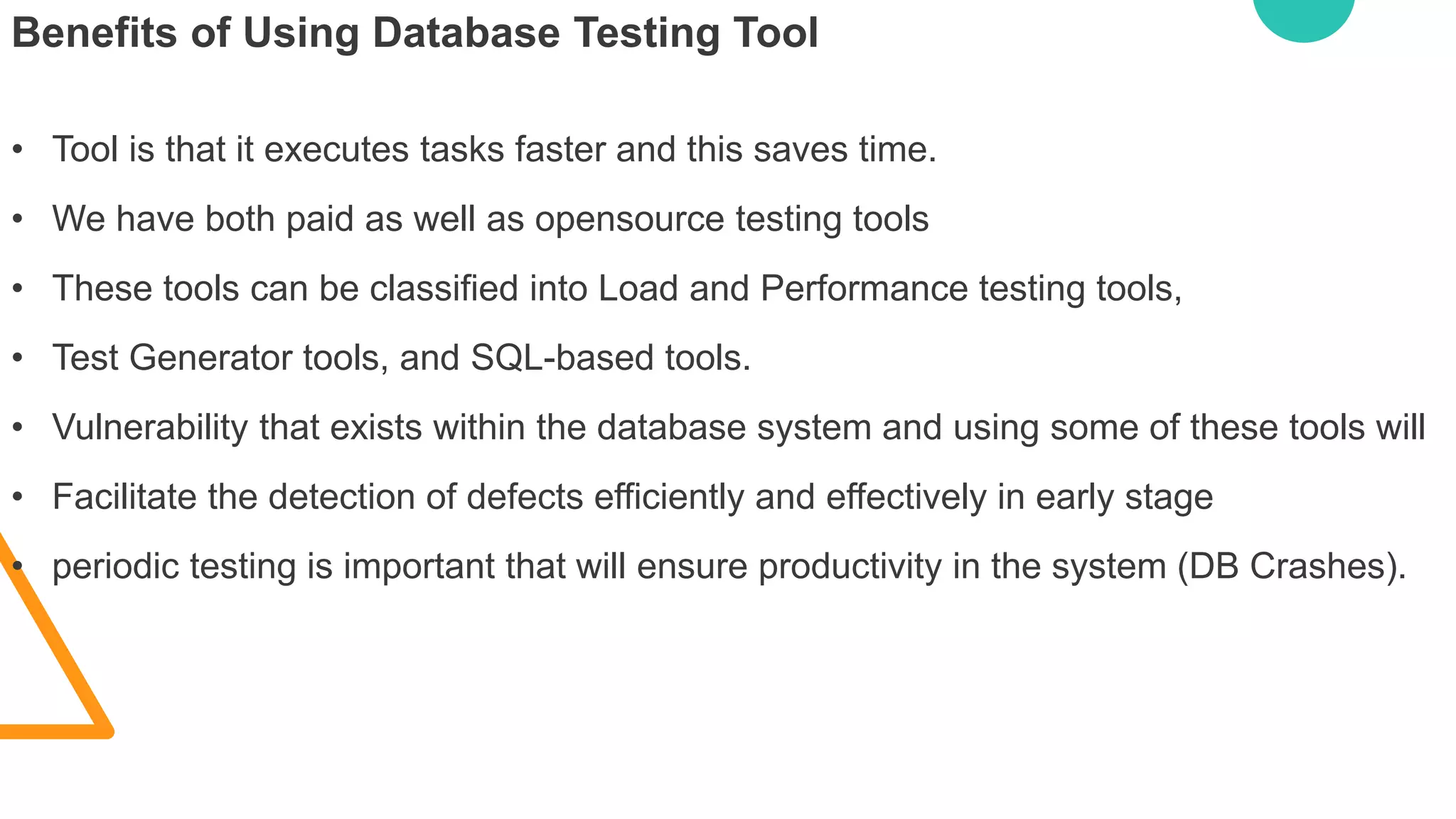
The document discusses various security vulnerabilities in IT applications, such as SQL injection and malware, and outlines the need for comprehensive cyber security measures across different domains. It details types of security testing including penetration testing and vulnerability scanning, along with various tools used for information gathering and exploitation. Additionally, it emphasizes the importance of database testing tools and techniques to efficiently detect and address vulnerabilities.