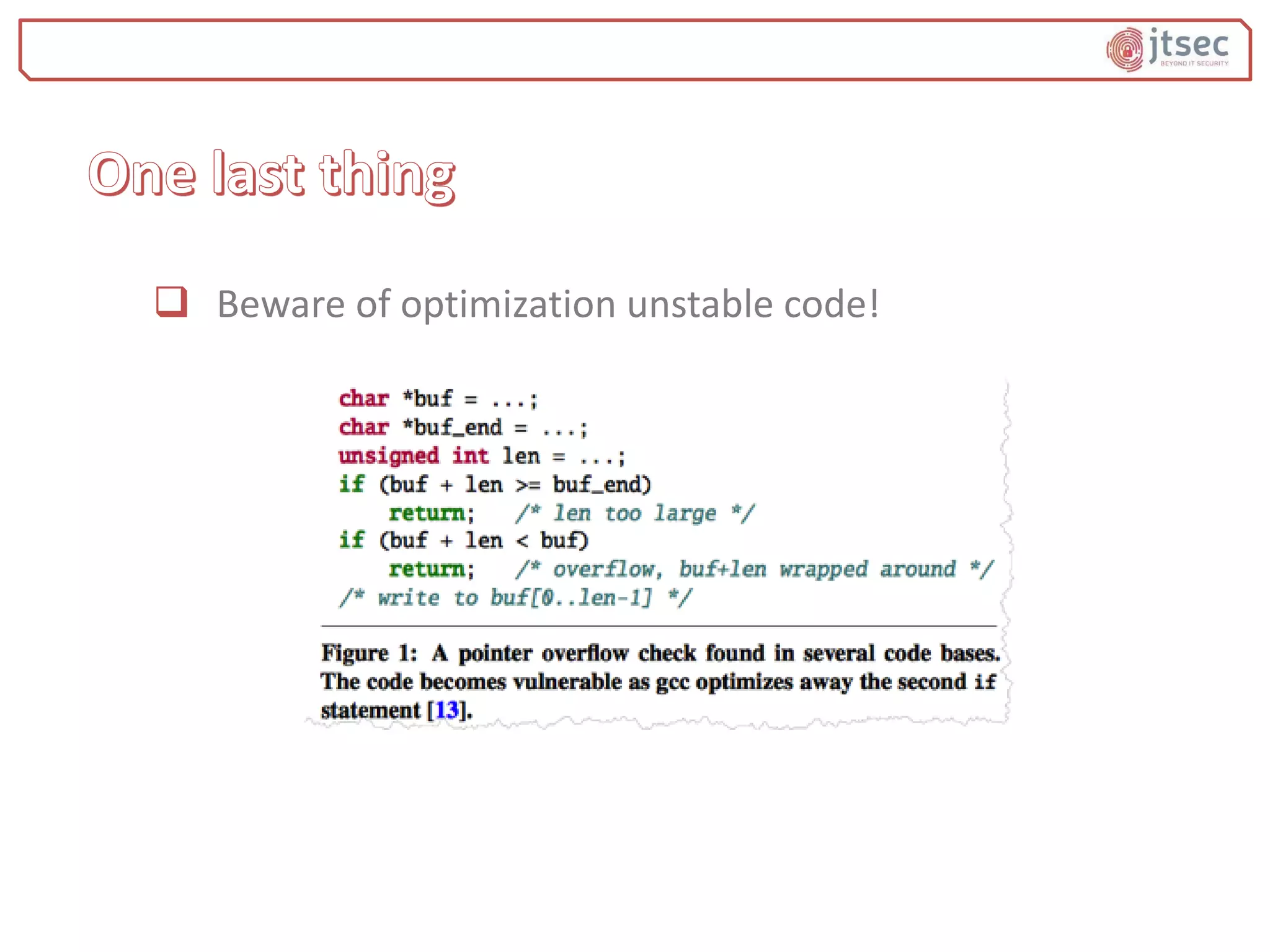
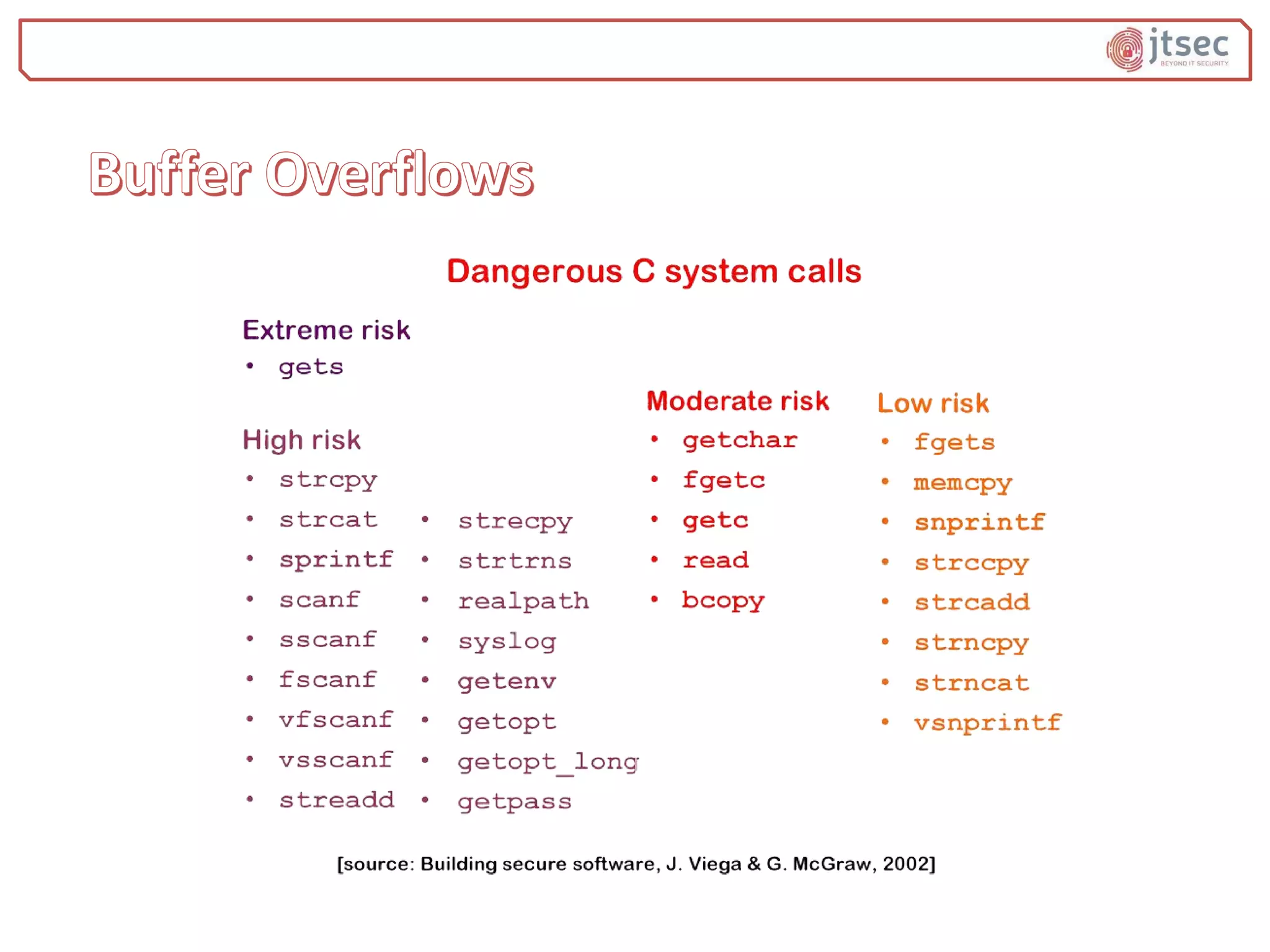
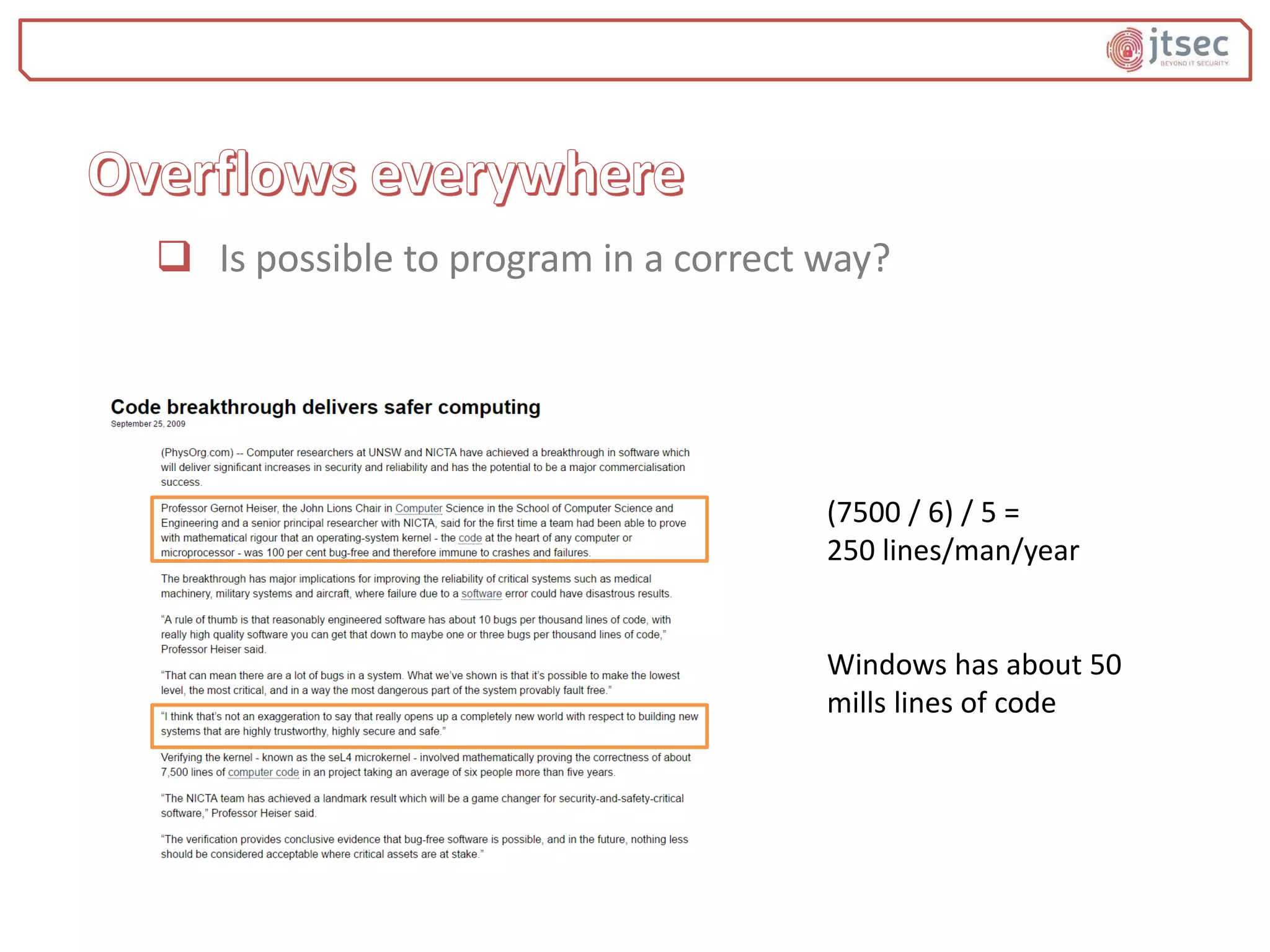
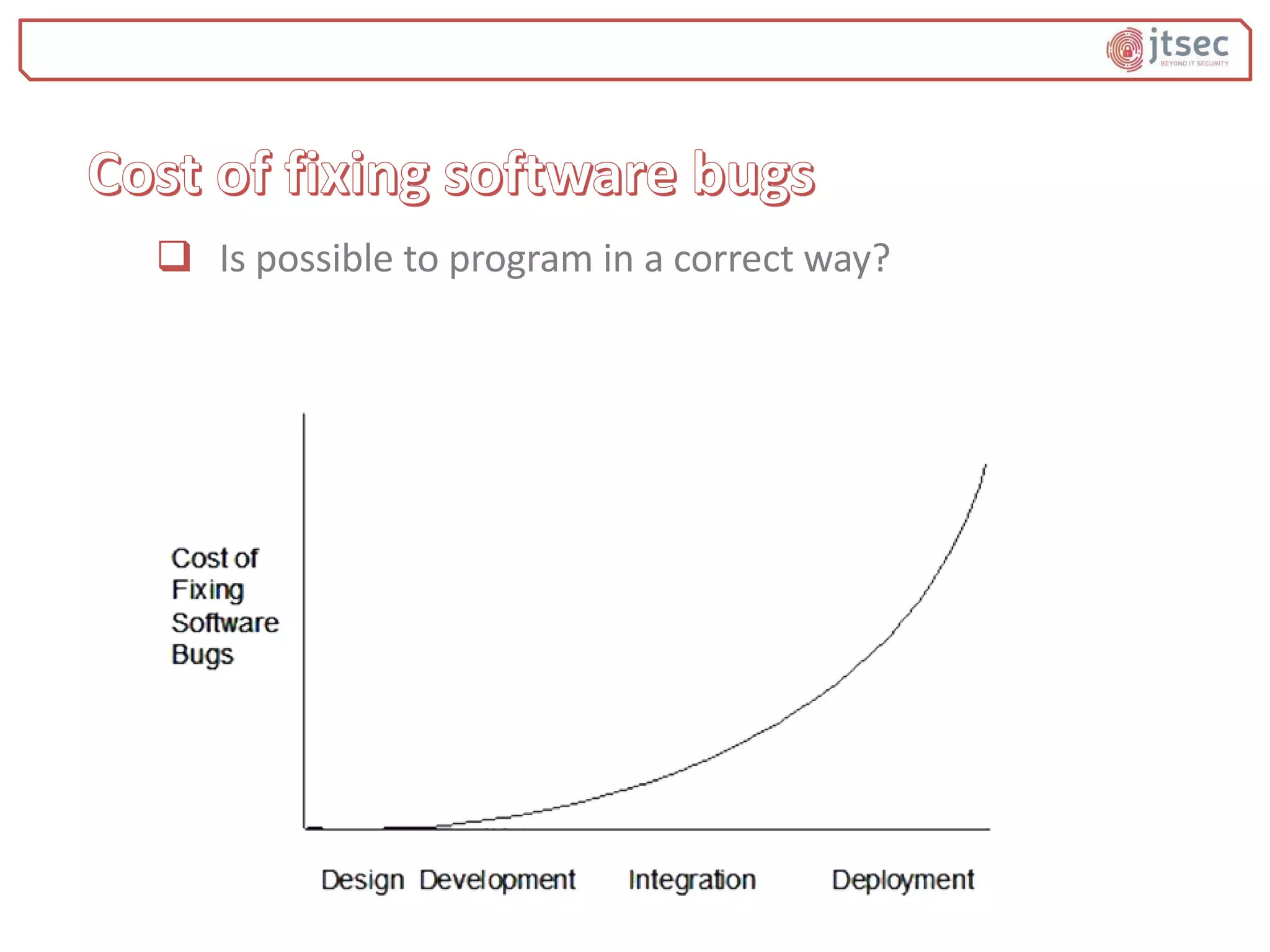
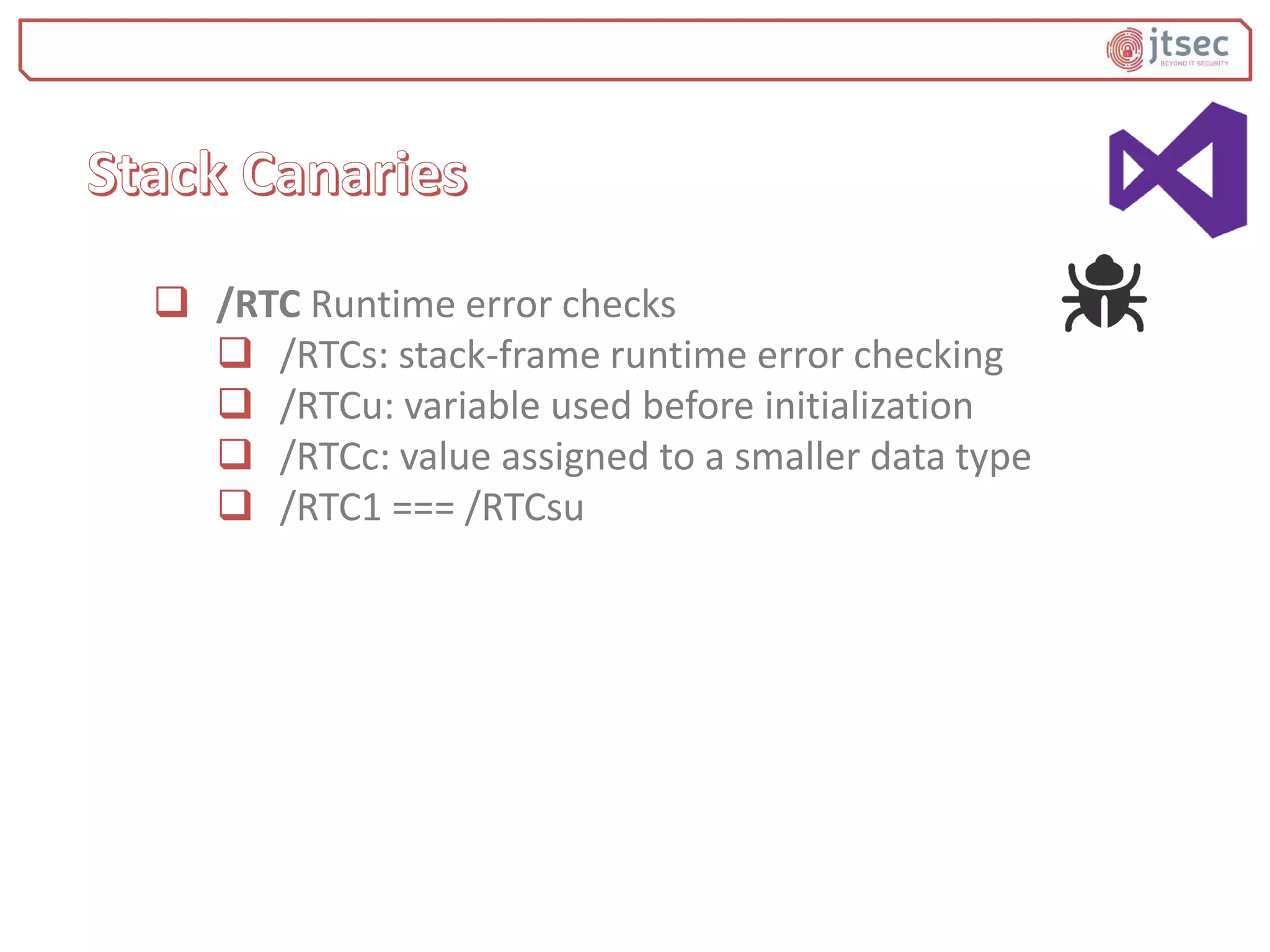
The document discusses various methods and practices for programming secure code, emphasizing security measures such as buffer overflow detection and protection mechanisms in compilers. It covers tools and flags in different compilers, including Microsoft Visual C++ and GCC, that help in identifying vulnerabilities and ensuring code safety. Additionally, it explores advanced topics like control flow integrity and vtable verification to prevent control-flow hijacking and other types of security exploits.






![ Extra entry added to vtable
ASLR makes this entry’s value unknown to the
attacker
Check added:
if vtable[vtguard_vte] != vtguard then
terminate the process
Celement::`vftable´
VirtualMethod1
VirtualMethod2
…
vtguard](https://image.slidesharecdn.com/mitigatingoverflowsusingdefense-in-depth-180514163410/75/Mitigating-overflows-using-defense-in-depth-What-can-your-compiler-do-for-you-32-2048.jpg)