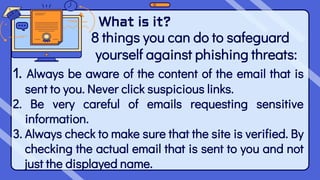
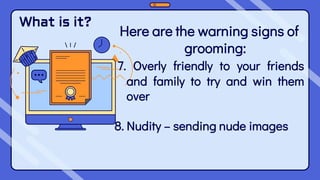
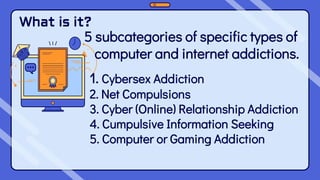
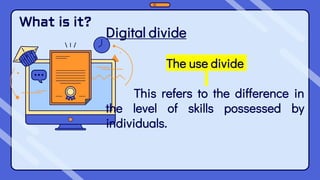
This document outlines the content and learning objectives for Quarter 1 Module 9 and Quarter 2 Modules 1 and 2 of a Media and Information Literacy course. In Quarter 1 Module 9, students will learn about opportunities and challenges in media and information, and cite an example of how media can affect change. In Quarter 2 Modules 1 and 2, students will define Massive Open Online Courses, describe trends in media/information education, and predict future innovations. The modules cover topics like cybercrime, computer addiction, cyberbullying, and the digital divide. Students are expected to understand these concepts and discuss how cybercrime impacts society and how individuals can be victimized or protect themselves.