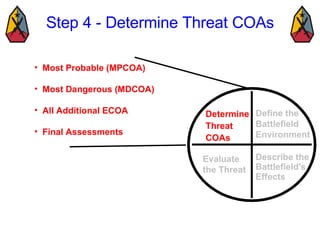
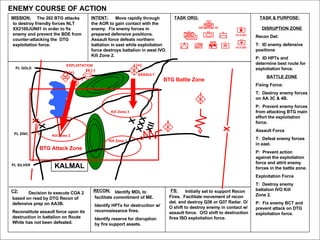
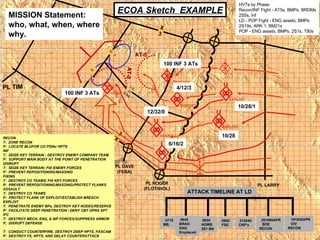
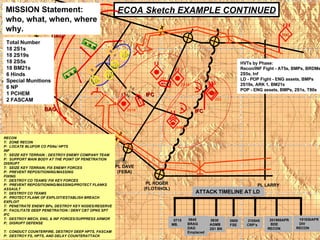
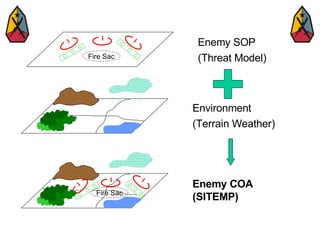
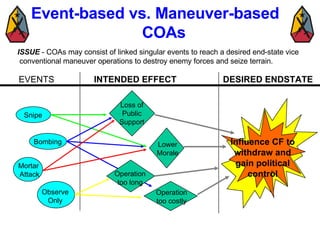
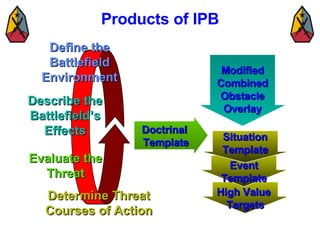
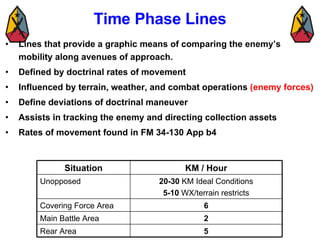
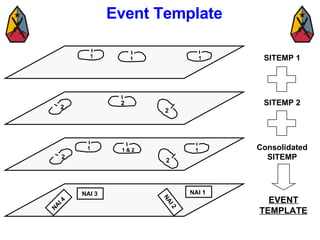
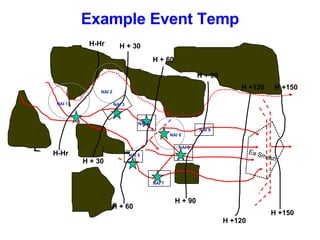
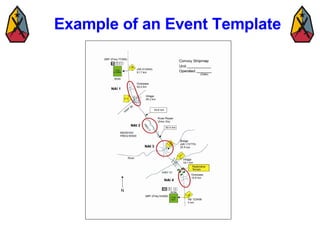
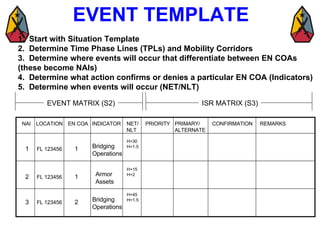
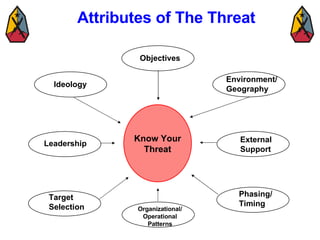
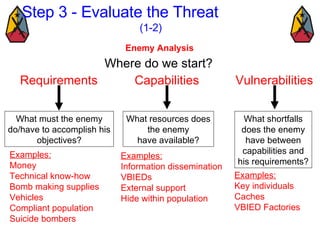
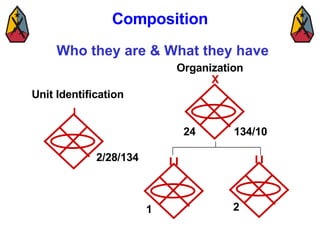
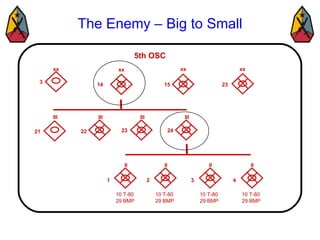
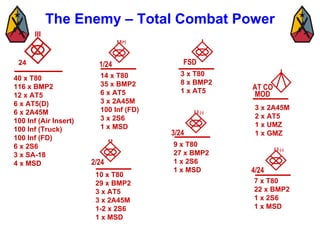
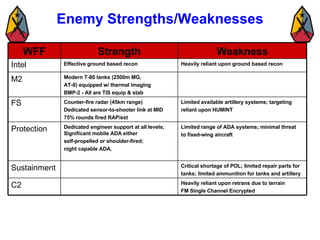
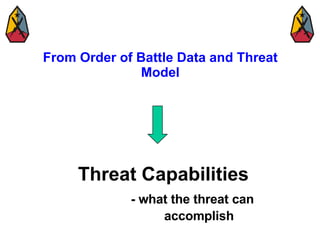
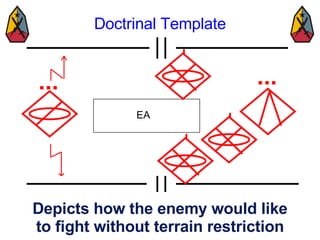
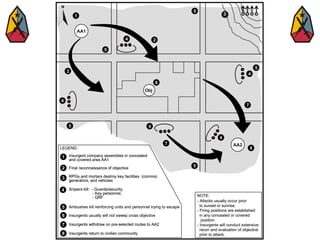
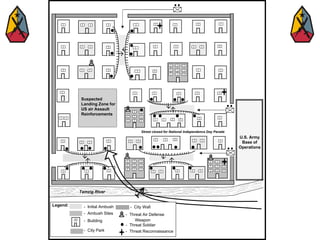
The document provides information on identifying and evaluating threats, including determining the threat's objectives, analyzing capabilities and weaknesses, developing possible courses of action (COAs), and modeling threat COAs. Key steps discussed are identifying the threat and why it fights, studying the insurgency's organization and tactics, capturing the disposition and composition of forces, and prioritizing the most probable and most dangerous COAs.











![Determine Threat COAs Identification and development of likely threat COAs that will influence accomplishment of the friendly mission Identification of those areas and activities that, when observed, will discern which COA the threat commander has chosen Determine Threat COAs [Situation Templates & Event Template] Identify the threats likely objectives and desired end state Identify the full set of COAs available to the threat Evaluate and prioritize each COA Develop each COA in the amount of detail time allows Identify initial collection requirements FM 34-130, 1994, p. 2-39 thru 2-40 IPB Step 4](https://image.slidesharecdn.com/militarydecisionmakingprocessmar082-124026311937-phpapp01/85/Military-Decision-Making-Process-Mar-08-2-22-320.jpg)