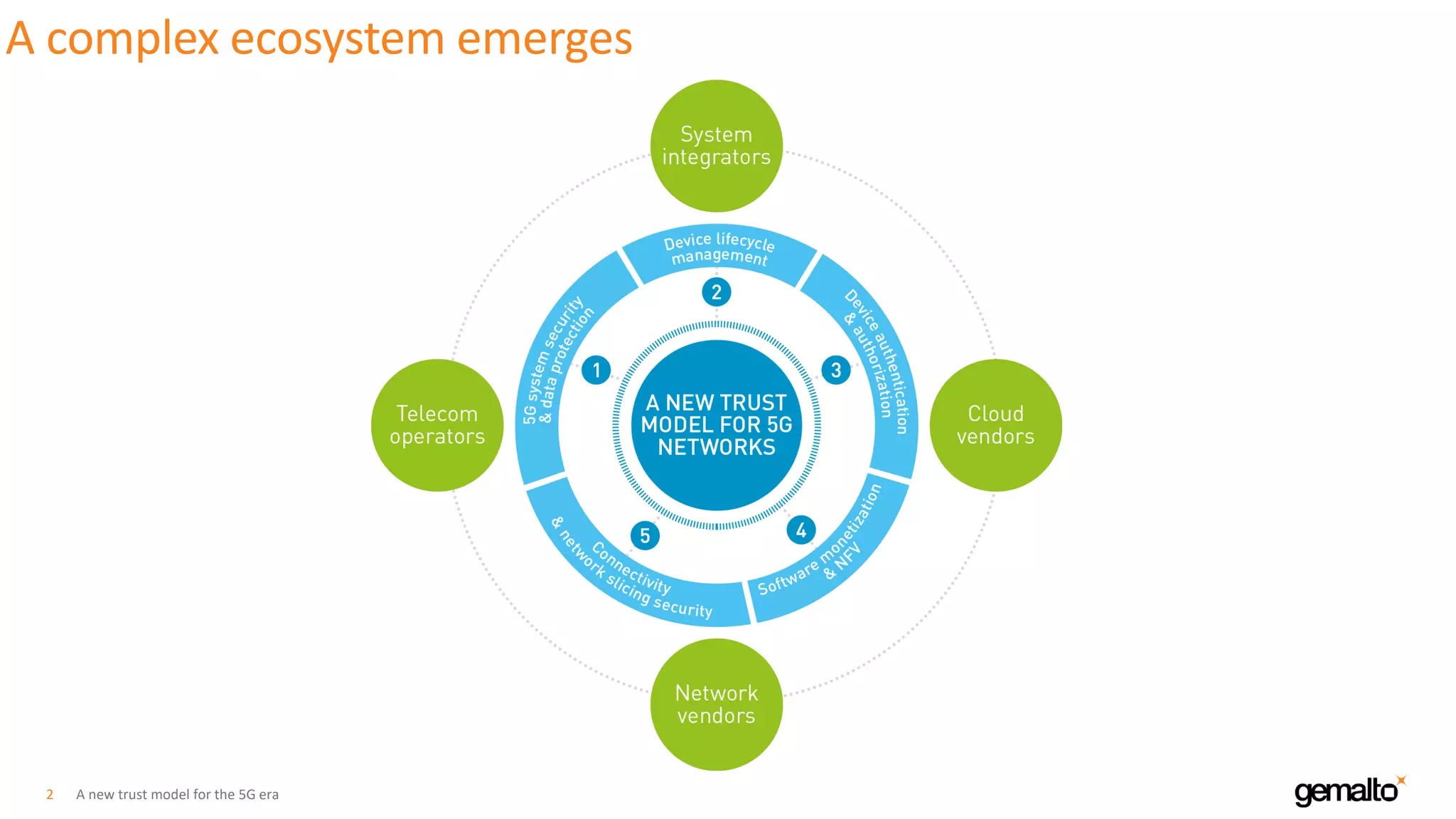
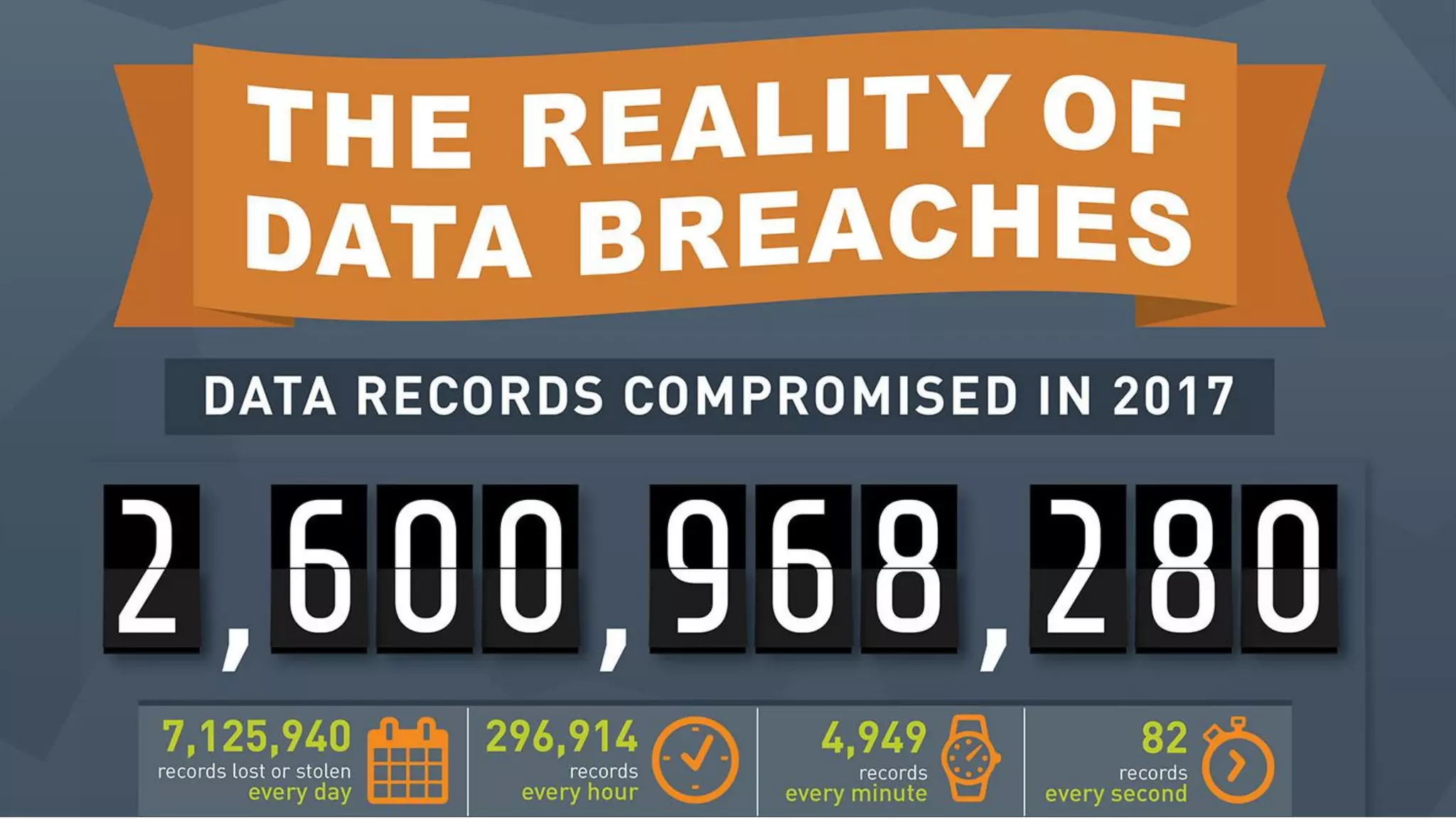
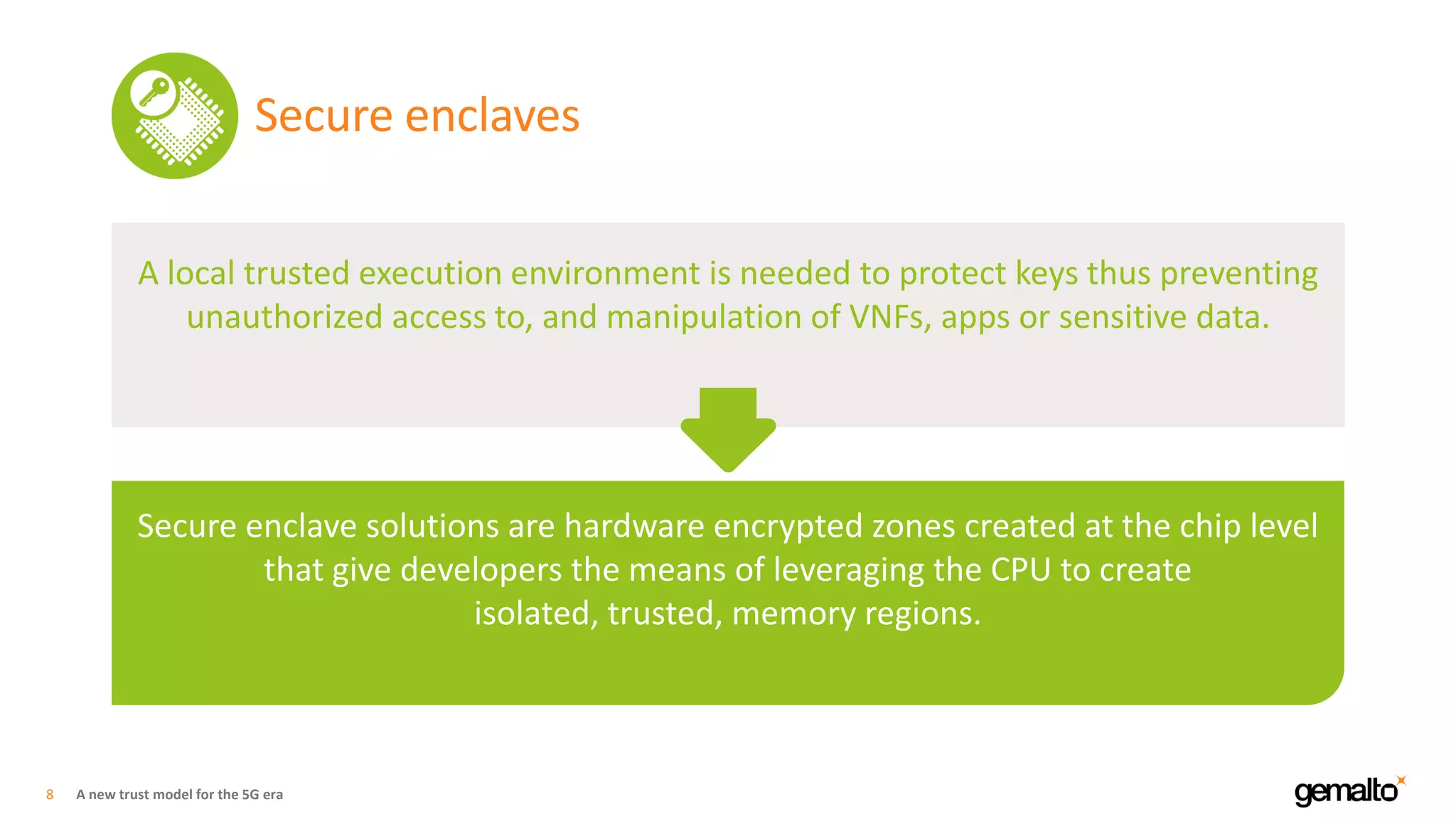
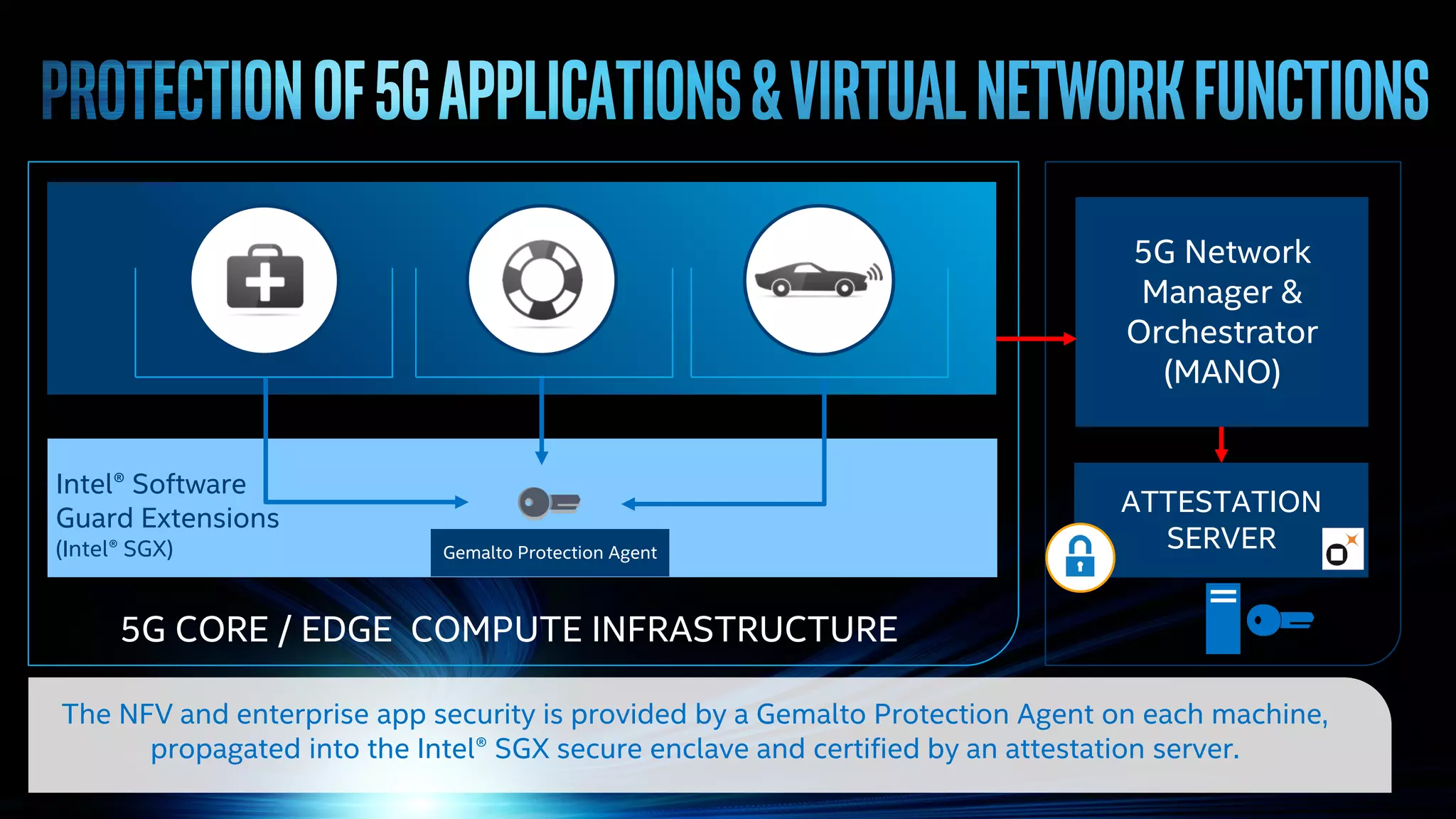
The document discusses a new trust model for 5G networks that addresses system security and data protection amidst the complexities of a 5G ecosystem. It emphasizes the importance of customer-controlled encryption, secure enclaves for sensitive data, and the role of virtualization and edge computing in creating trustworthy networks. Key technologies such as Intel® Software Guard Extensions (SGX) and dynamic provisioning are highlighted for securing network functions and applications.