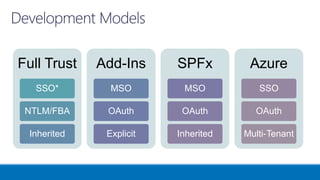
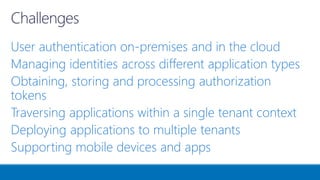
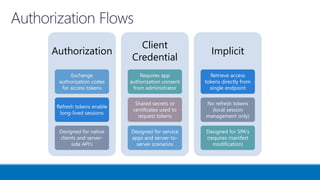
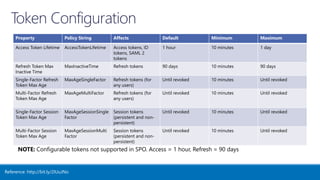
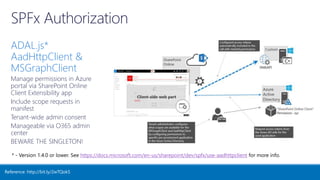
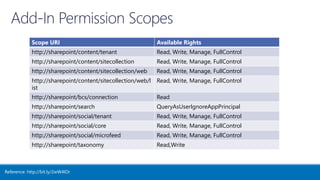
The document outlines various authentication and authorization methods utilized in Microsoft Azure and SharePoint services, including single sign-on (SSO), OAuth, and permissions management. It details deployment across multi-tenant applications, management of access tokens, and specifics on requesting and granting permissions. Additionally, it provides references and links to further resources for implementing these systems.