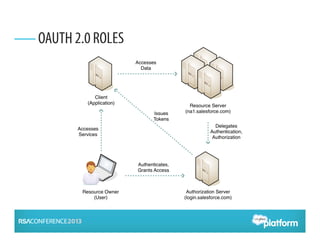
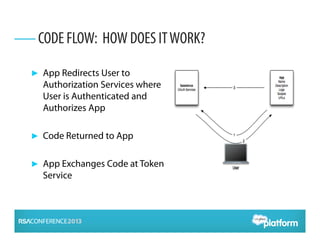
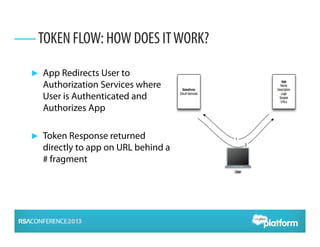
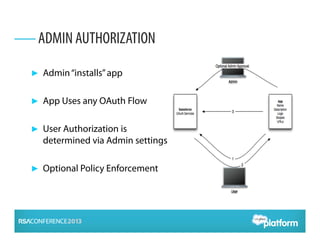
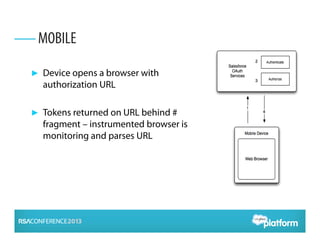
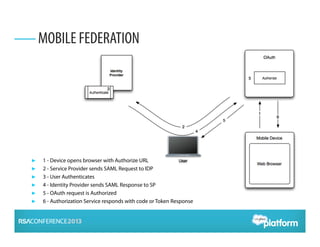
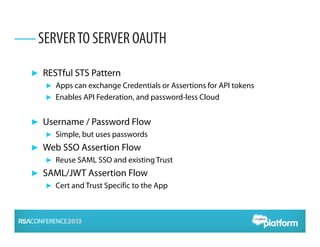
OAuth 2.0 is an open standard for authorization that enables apps to securely access APIs on behalf of users. It has become widely adopted for consumer apps but presents challenges for enterprise use cases. The presentation discusses adapting OAuth 2.0 for enterprises by supporting administrative authorization, mobile SSO federation, and server-to-server flows that exchange credentials or assertions for API tokens to enable API federation and password-less access across clouds. Future directions include further standardizing assertion flows and mobile app federation.