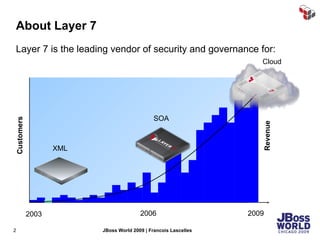
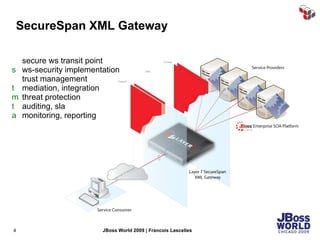
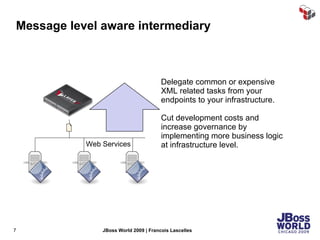
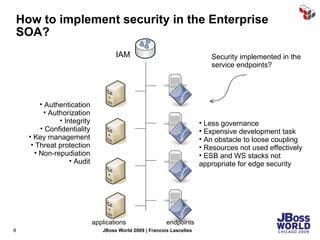
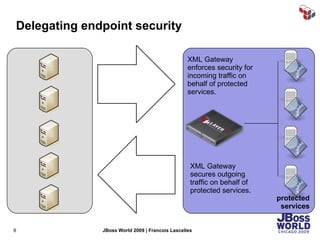
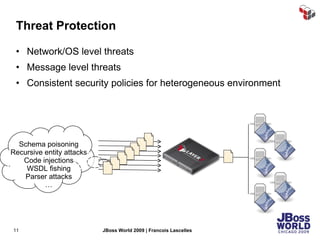
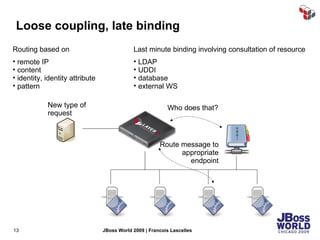
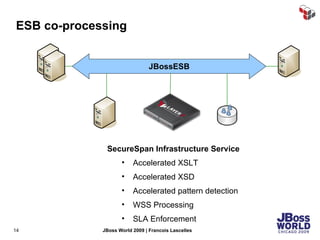
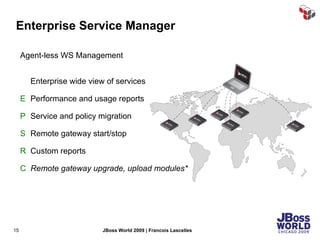
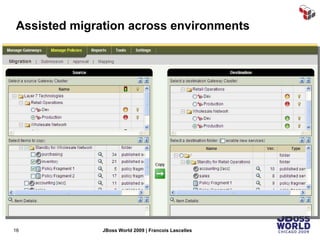
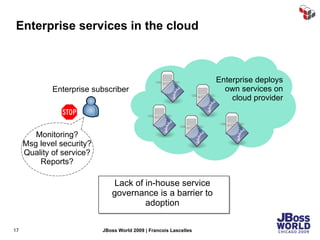
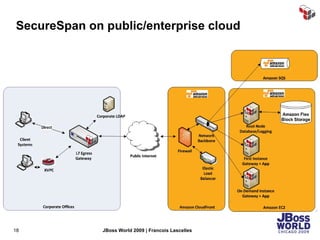
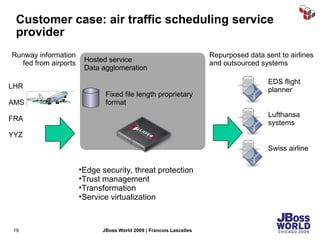
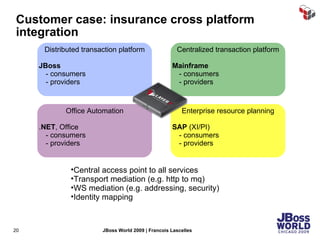
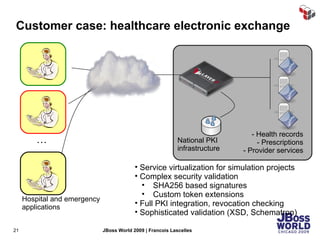
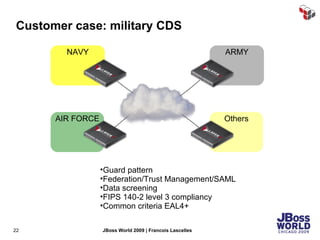
The document discusses SecureSpan, a product from Layer 7 Technologies that provides security and governance for SOA environments. SecureSpan acts as a secure intermediary for web services, implementing features like authentication, authorization, integrity, confidentiality and threat protection to enforce security policies on behalf of protected services. It can be deployed either as a hardware or virtual appliance.