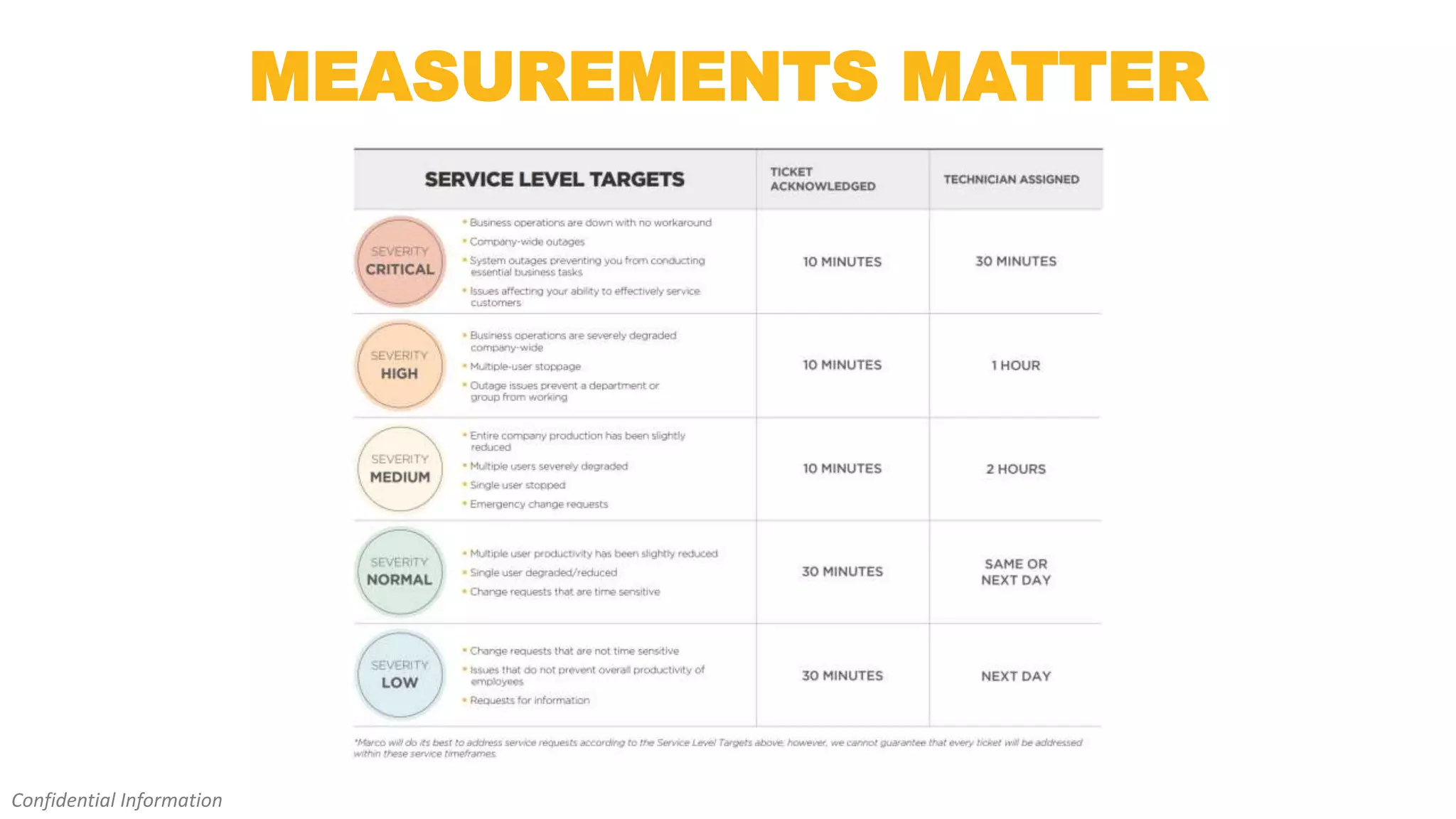
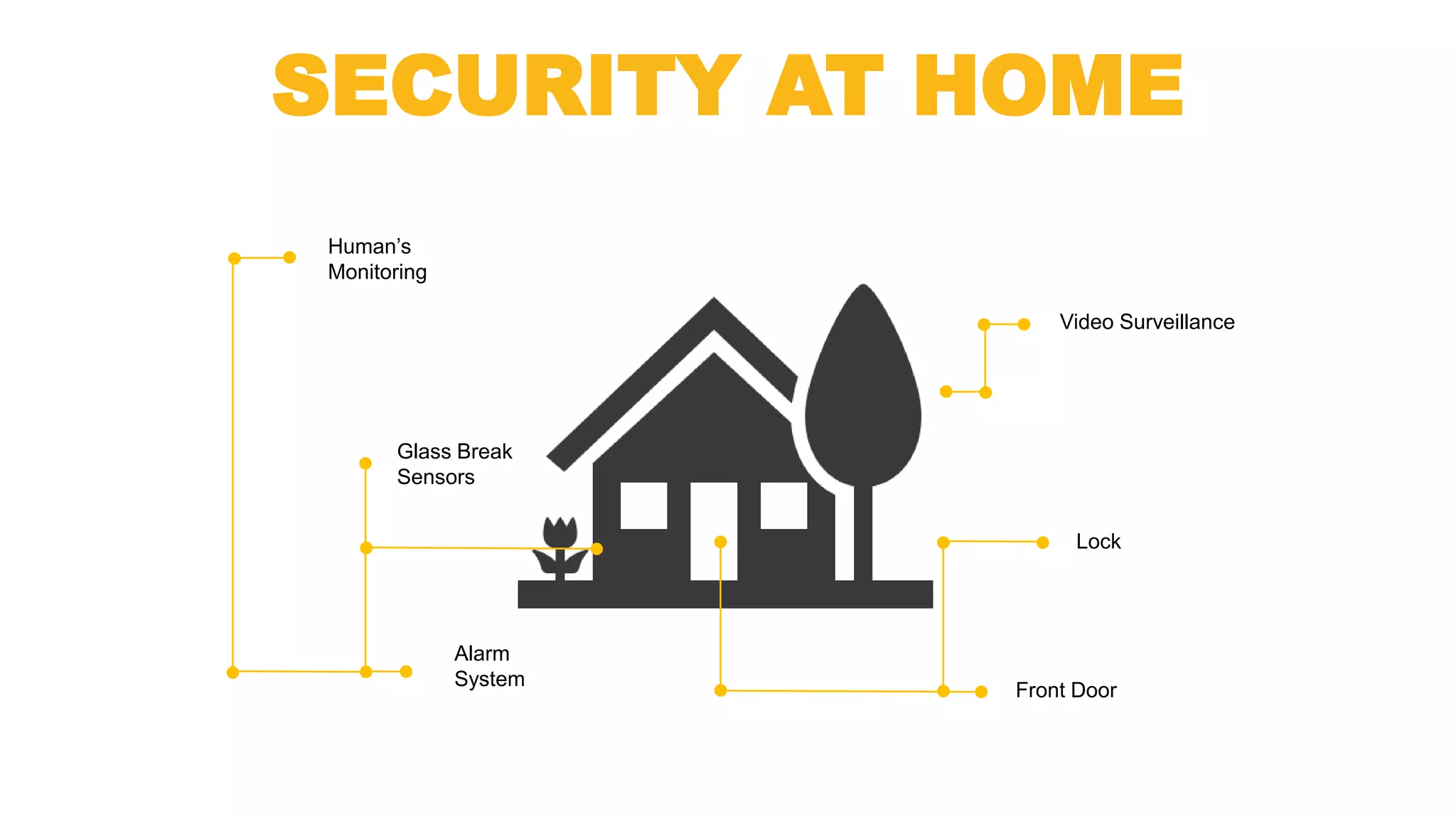
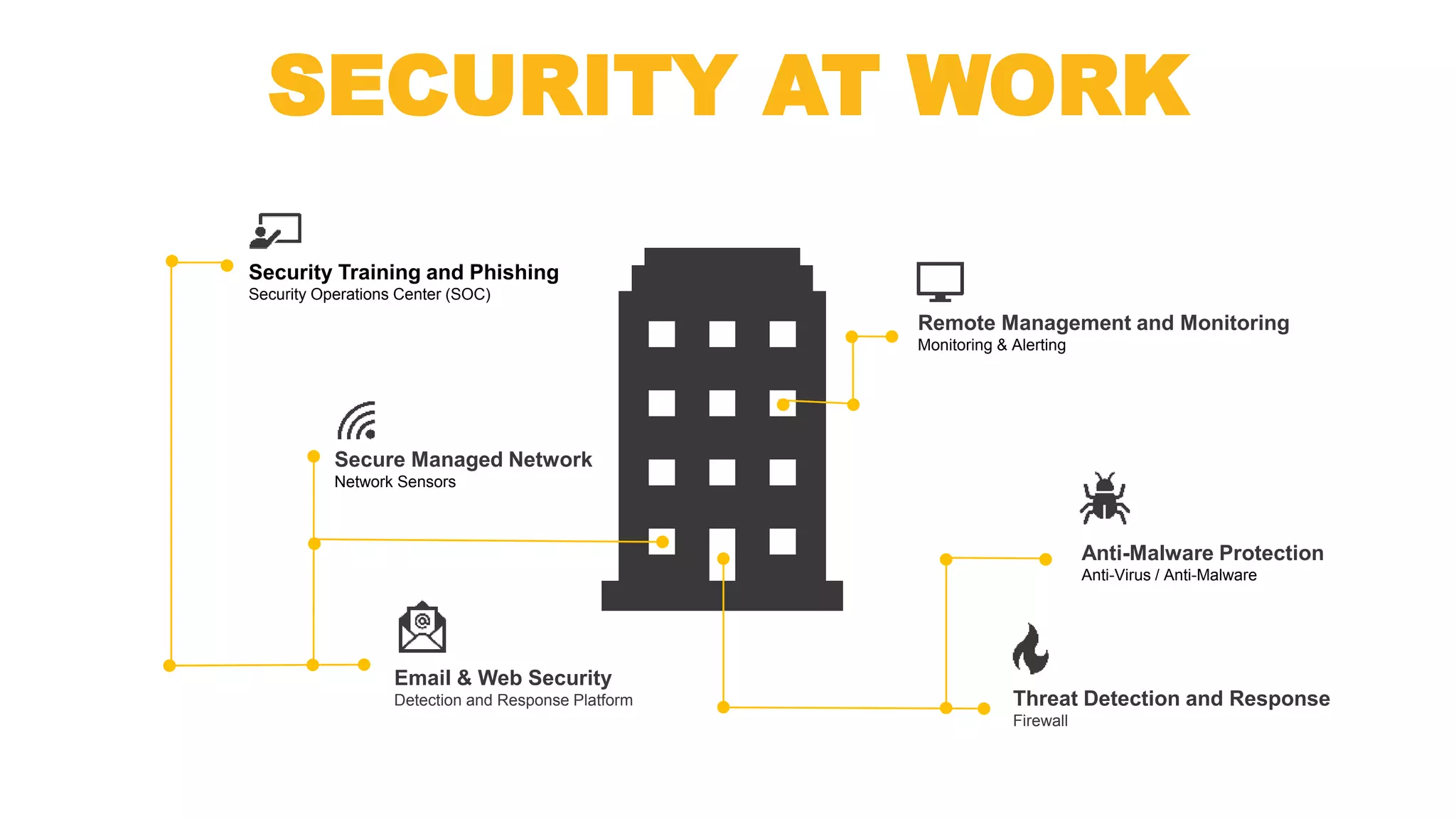
This document discusses managed IT services from Marconet. It notes that businesses want their technology to work without issues so they can focus on their core business. It also mentions concerns about security, unpredictable costs, and difficulty staffing an in-house IT department. The document then outlines the various managed IT services Marconet provides, including unlimited support, security monitoring, network management, and help with budgeting. It emphasizes Marconet's experience and various resources that allow it to offer big-company IT support with a small company feel.