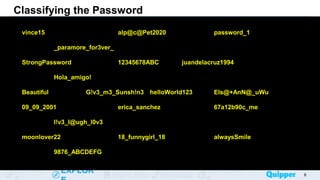
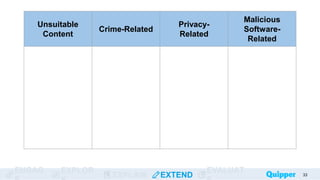
This document provides an overview of online safety and ethics. It defines key concepts like the cyber world, passwords, and online threats. The learning objectives are to define the cyber world, identify online threats, and learn ways to stay safe online. Various online dangers are explained, such as hacking, identity theft, cyberbullying, and malware. The document also gives tips for strong passwords and staying safe, including not sharing personal information and reporting issues to guardians. Practice activities classify threats and describe how to handle online situations safely.