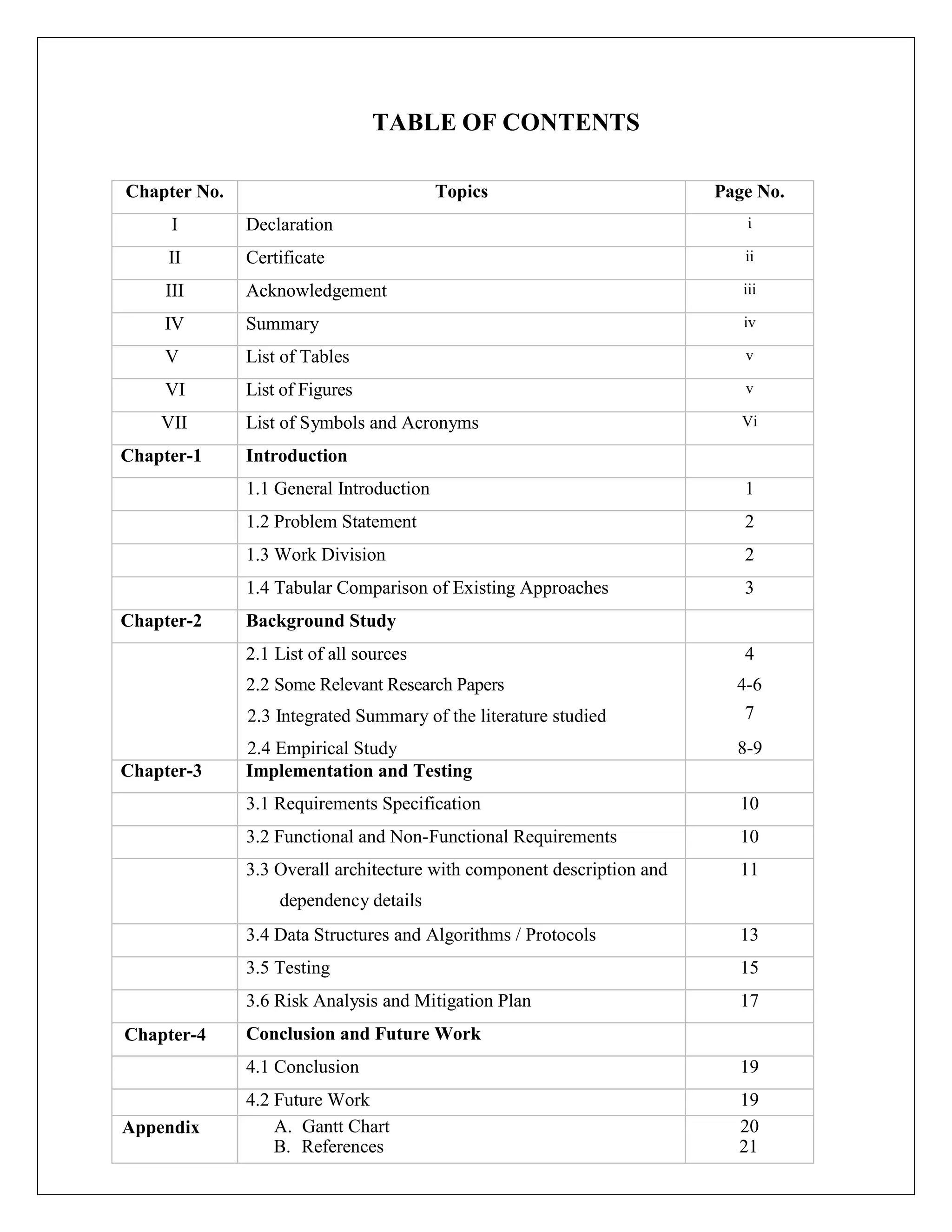
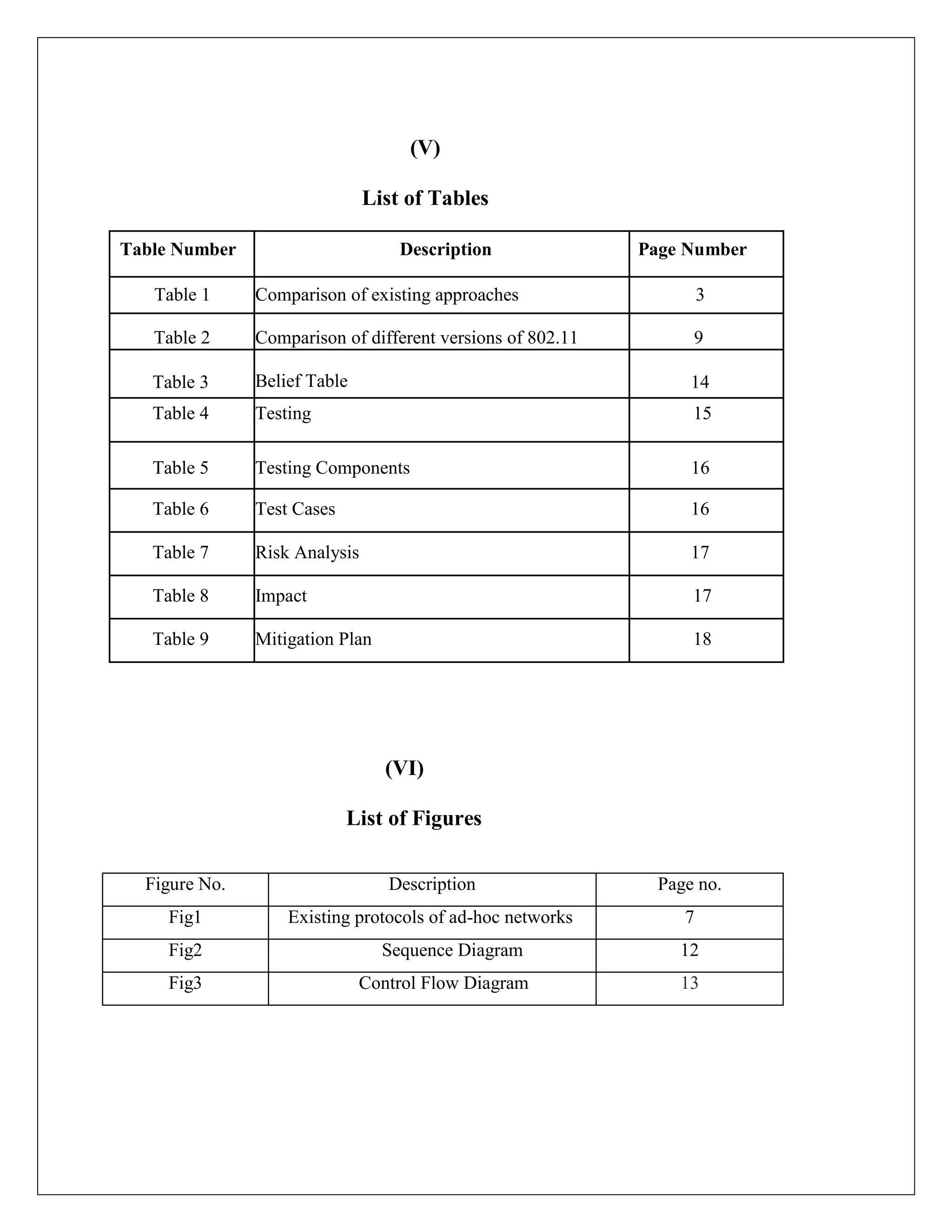
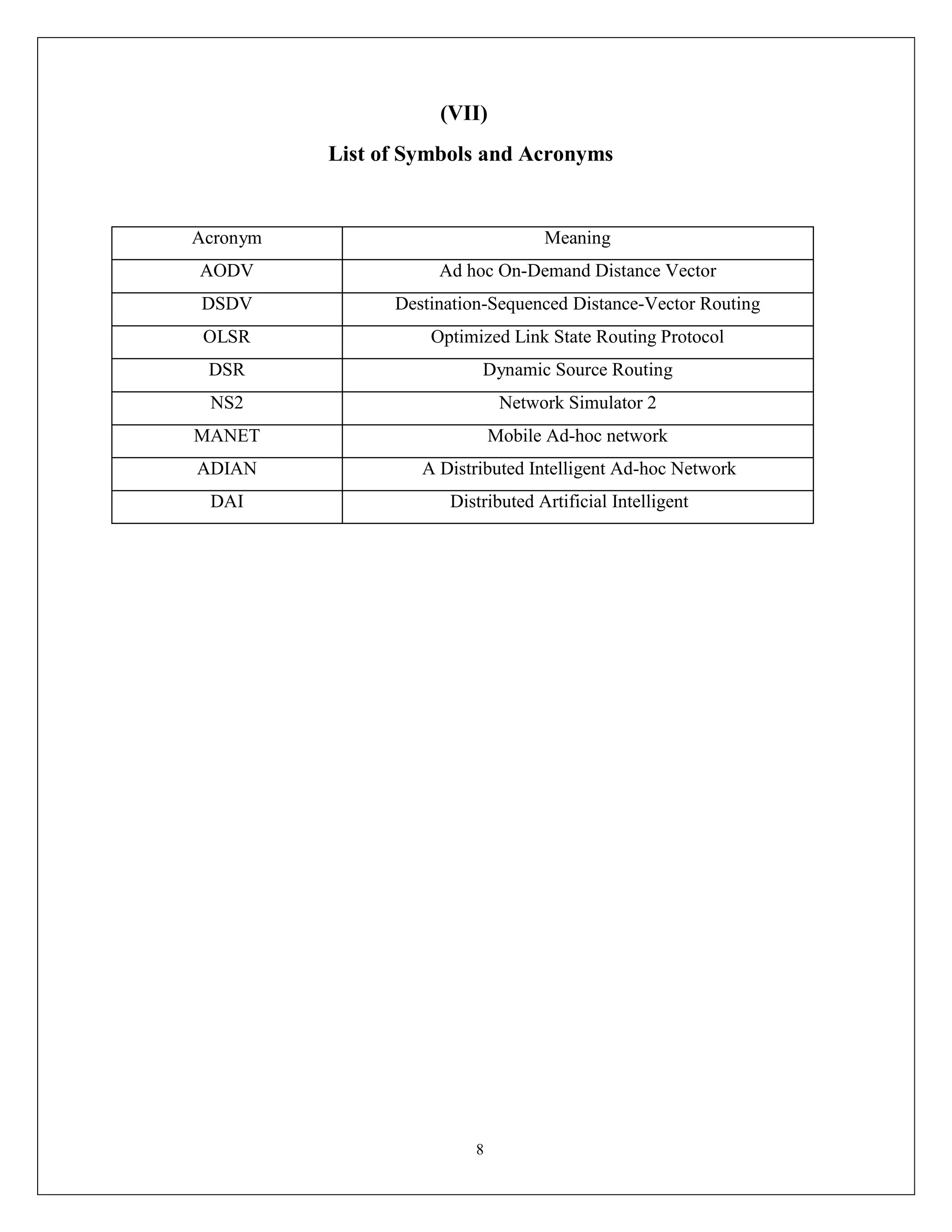
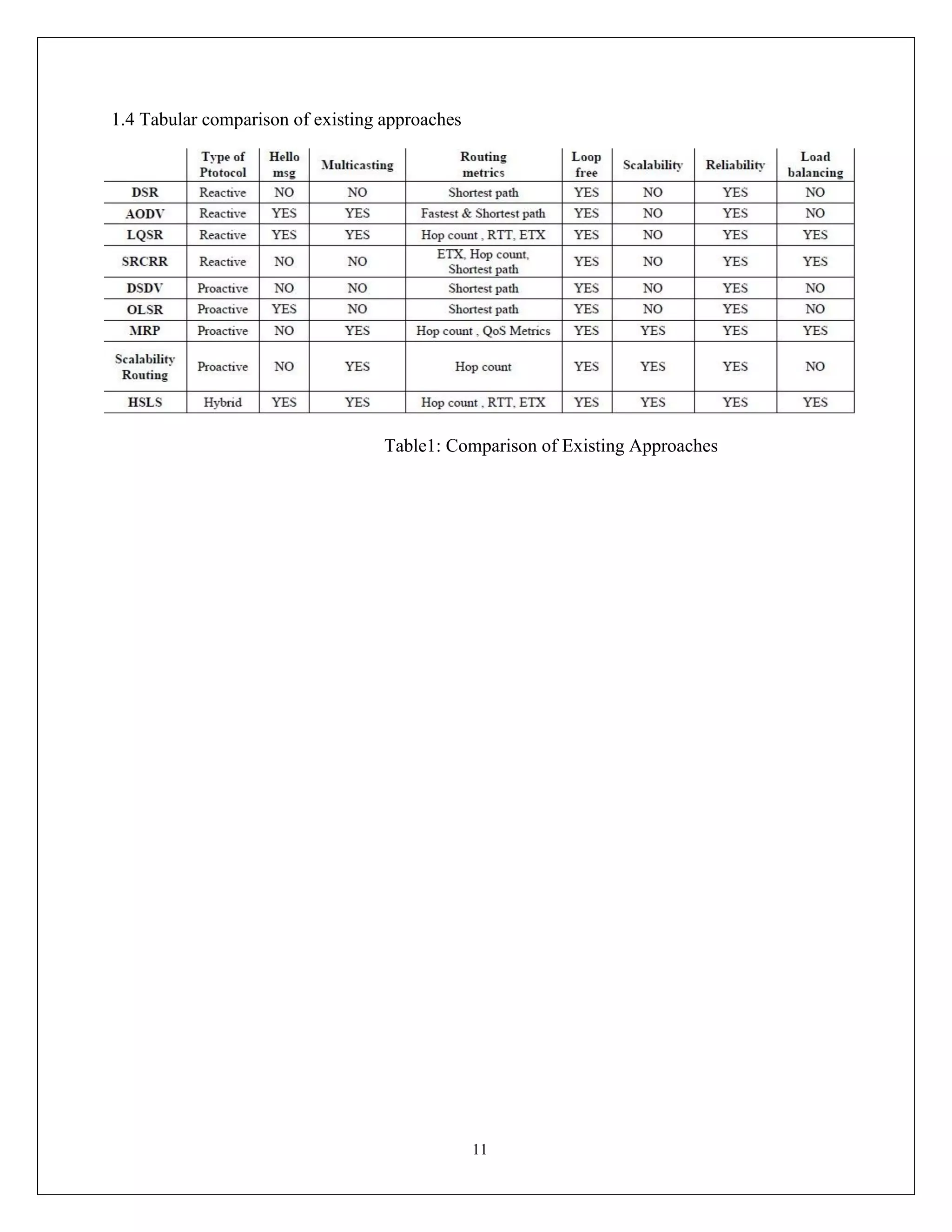
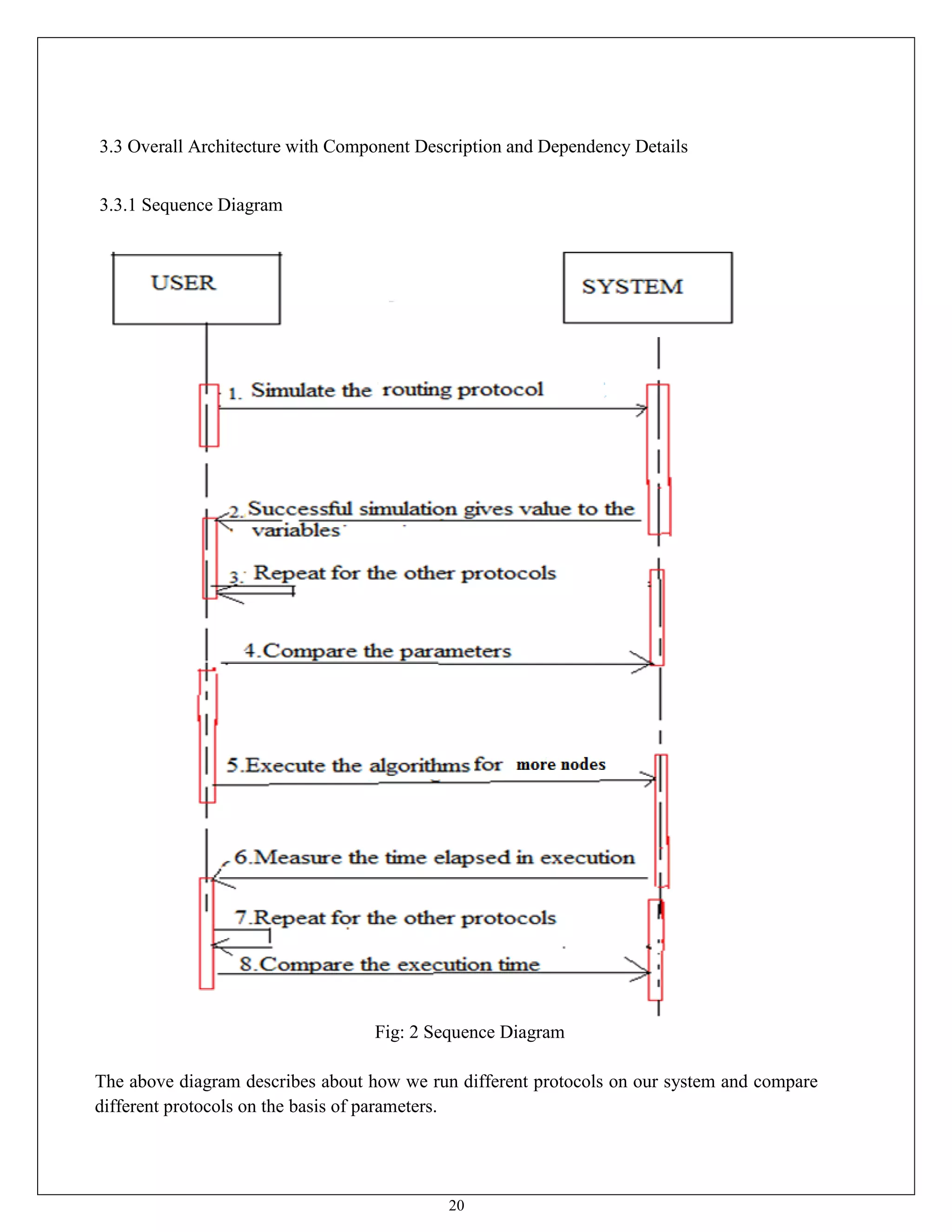
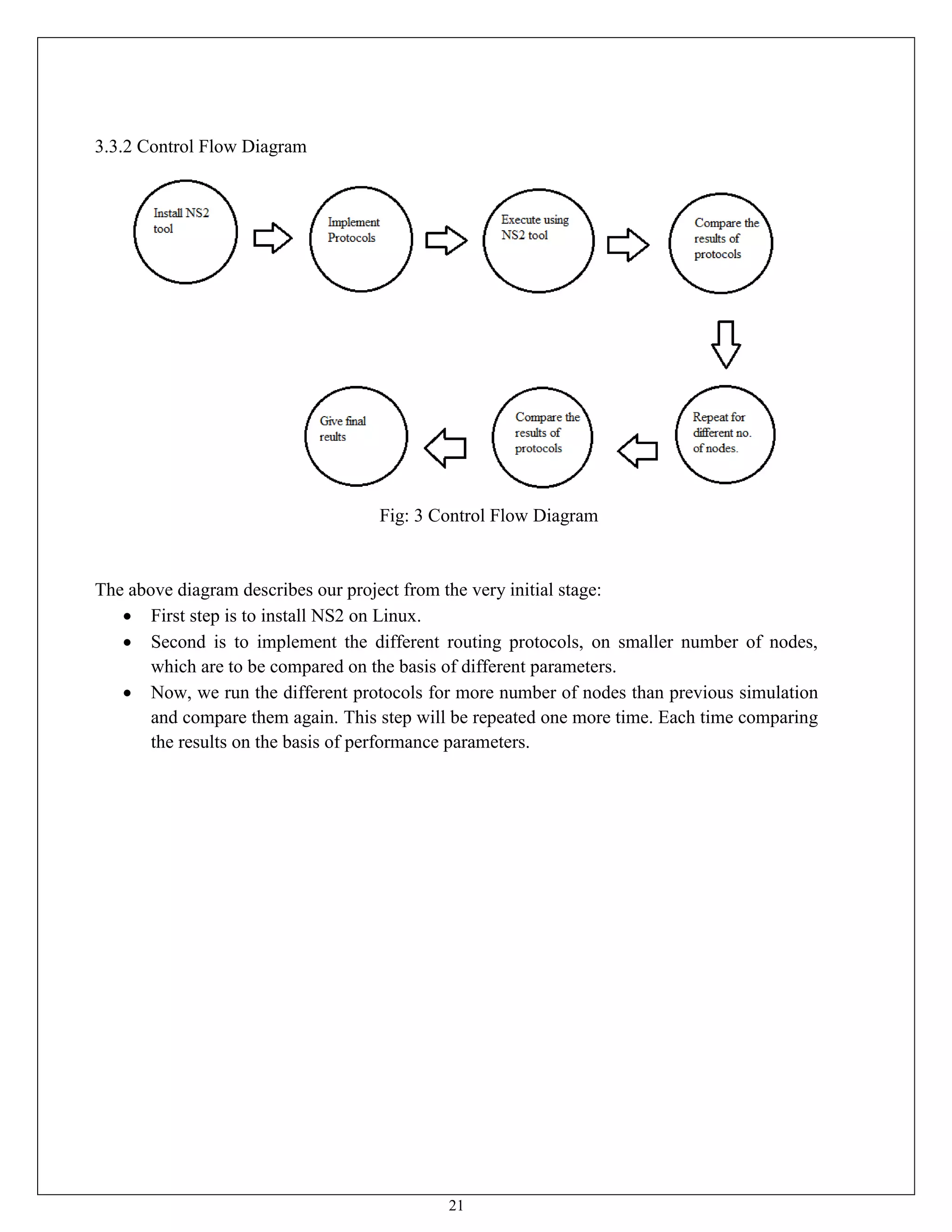
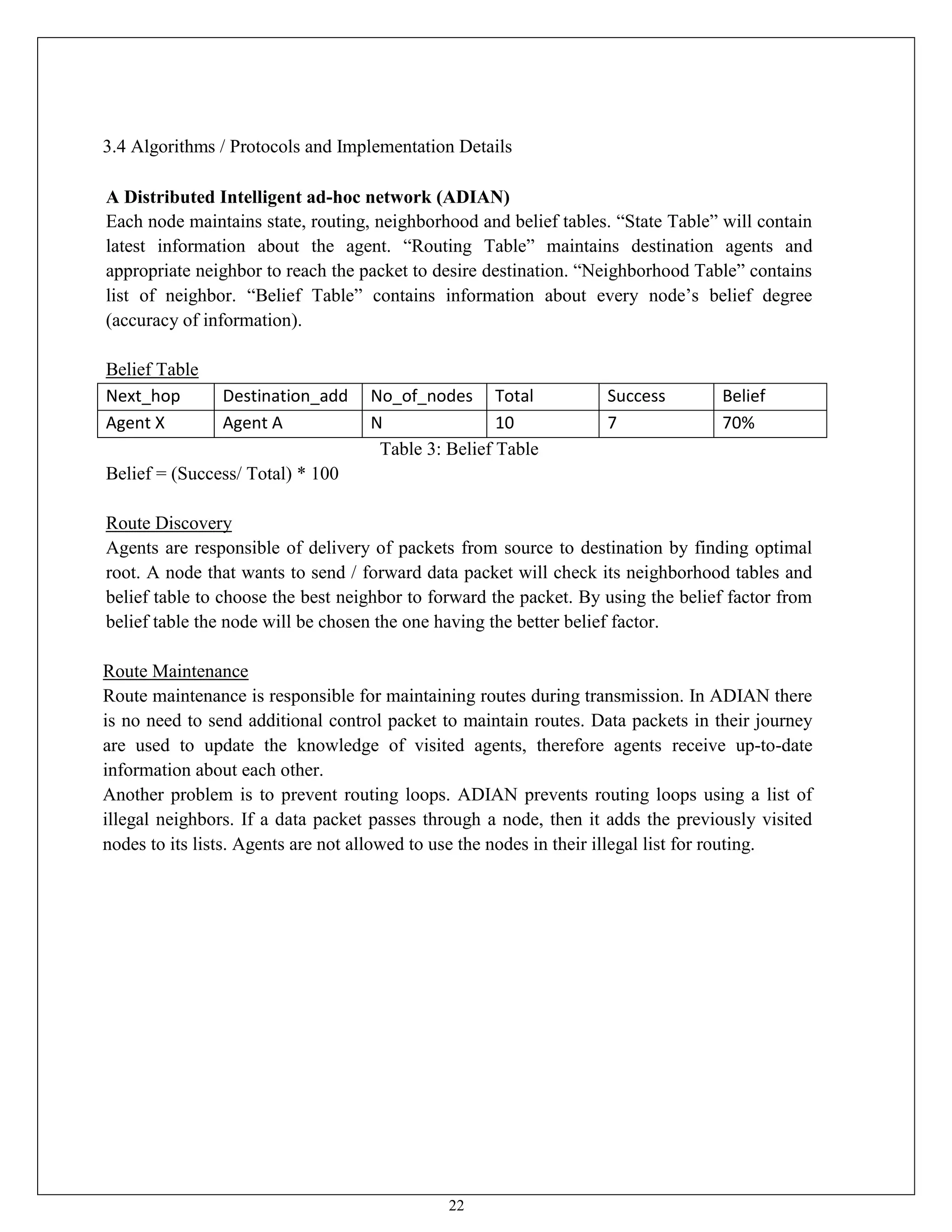
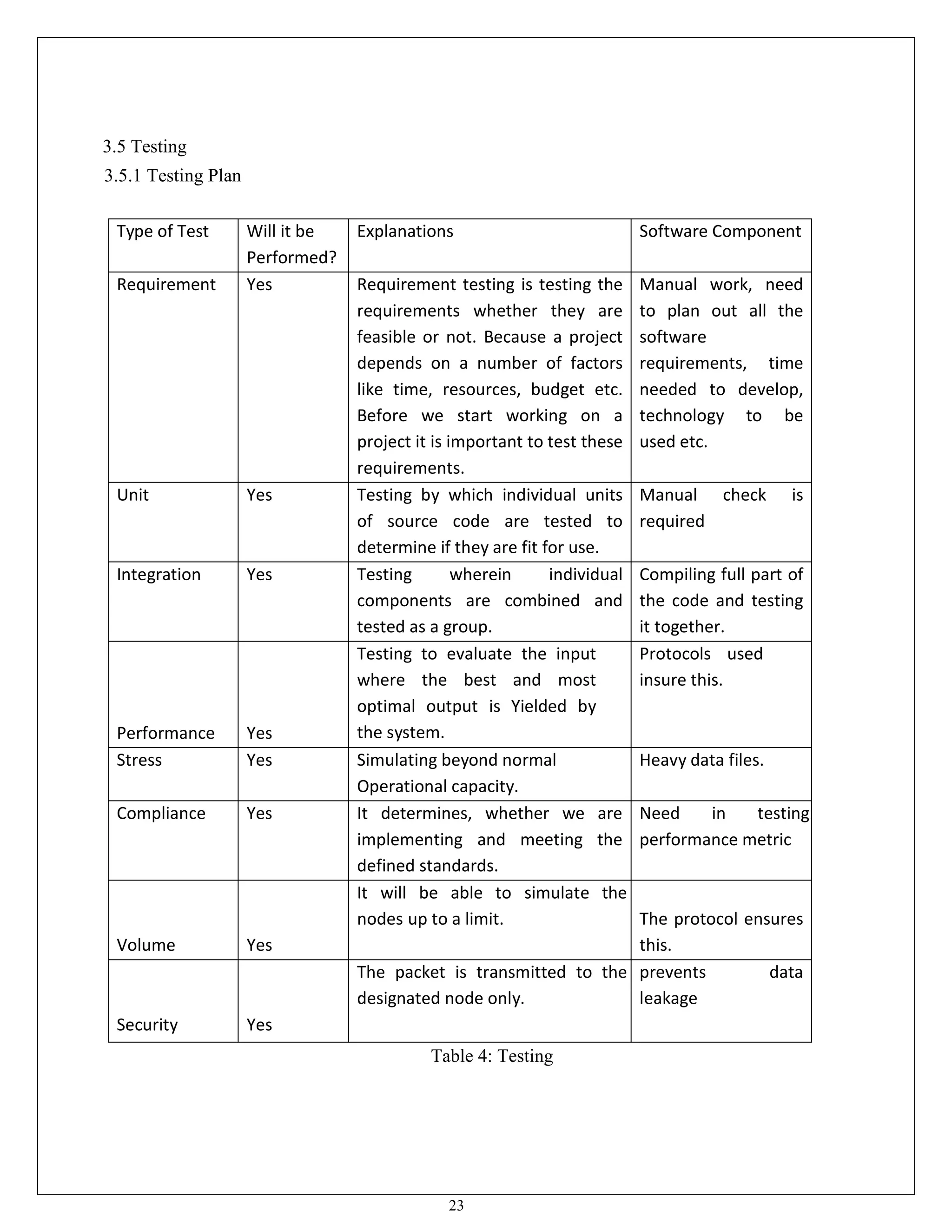
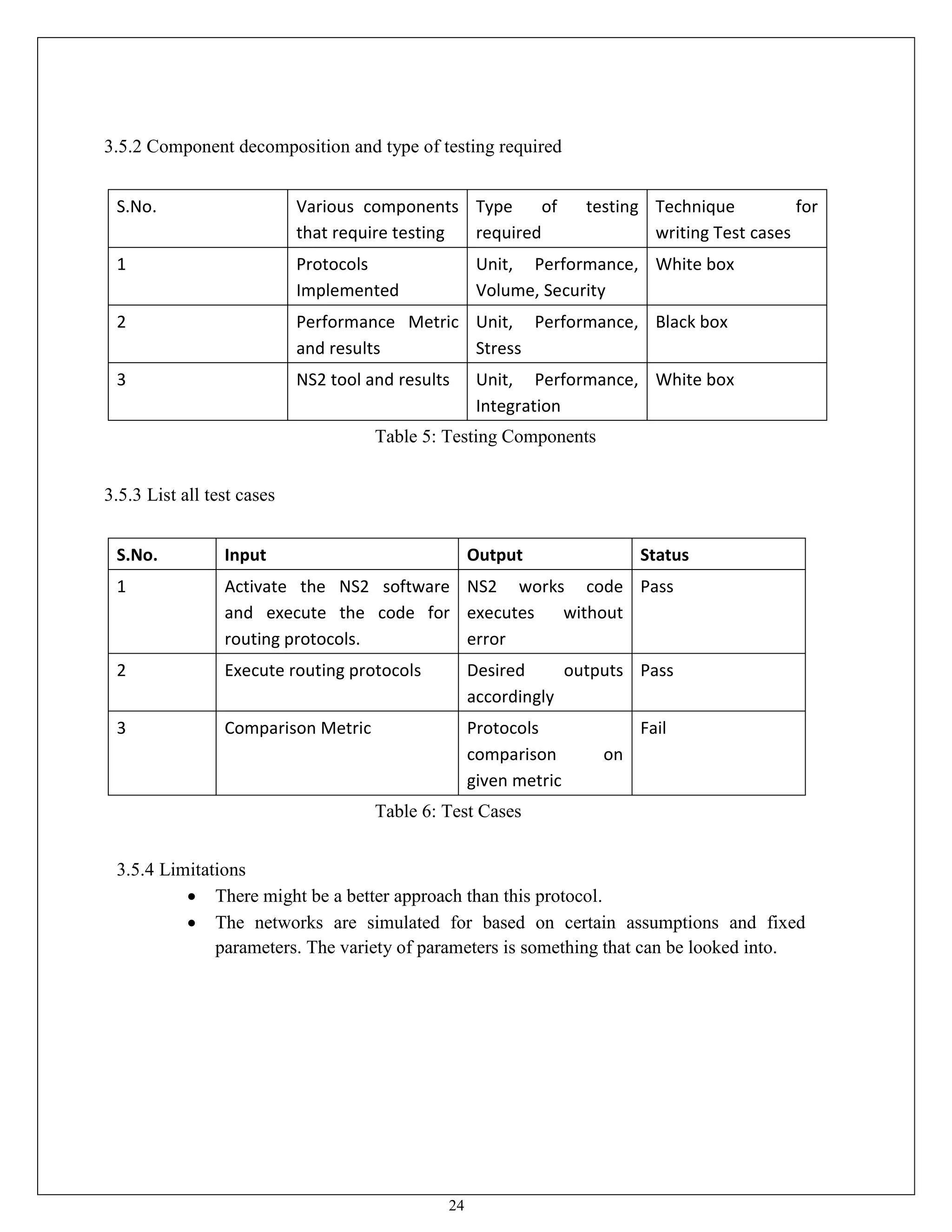
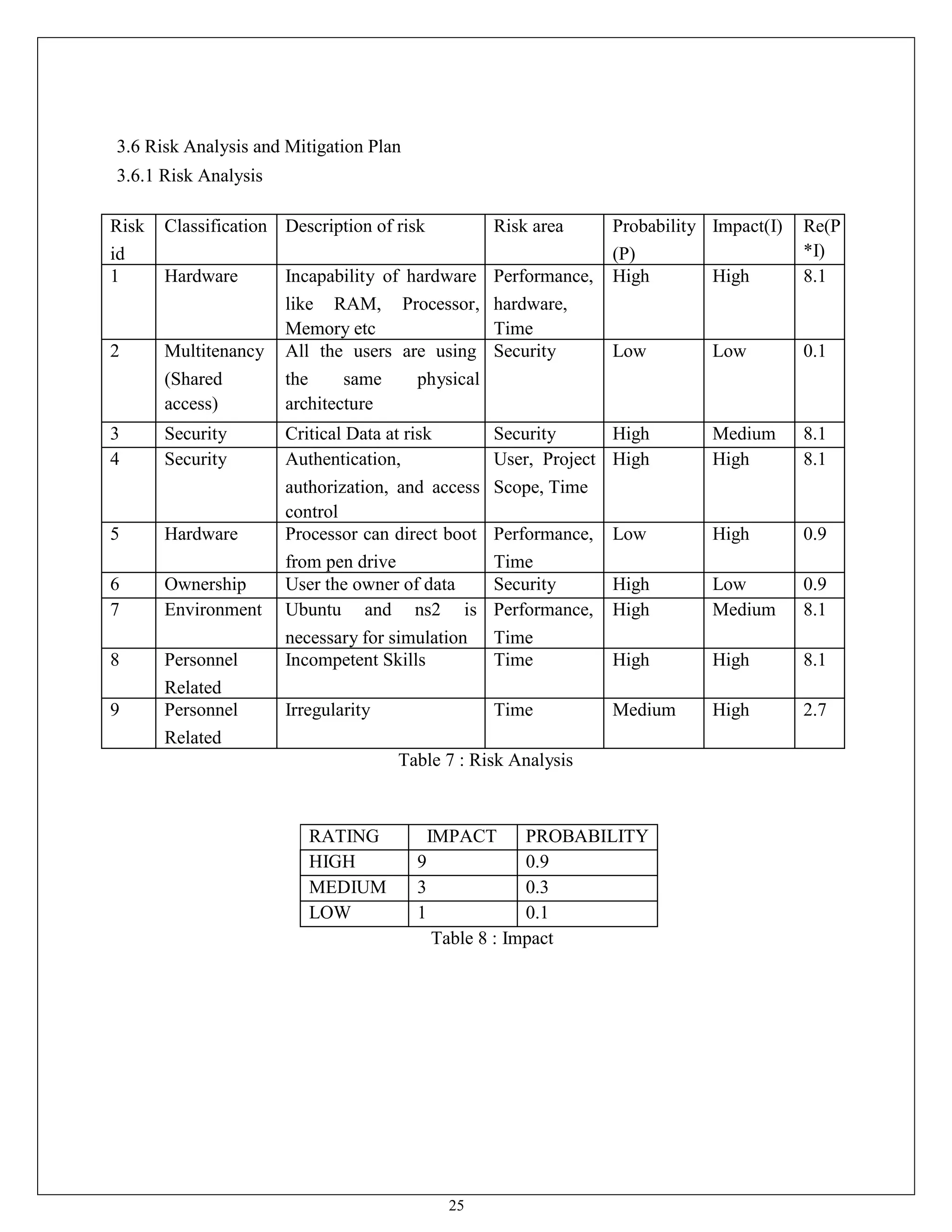
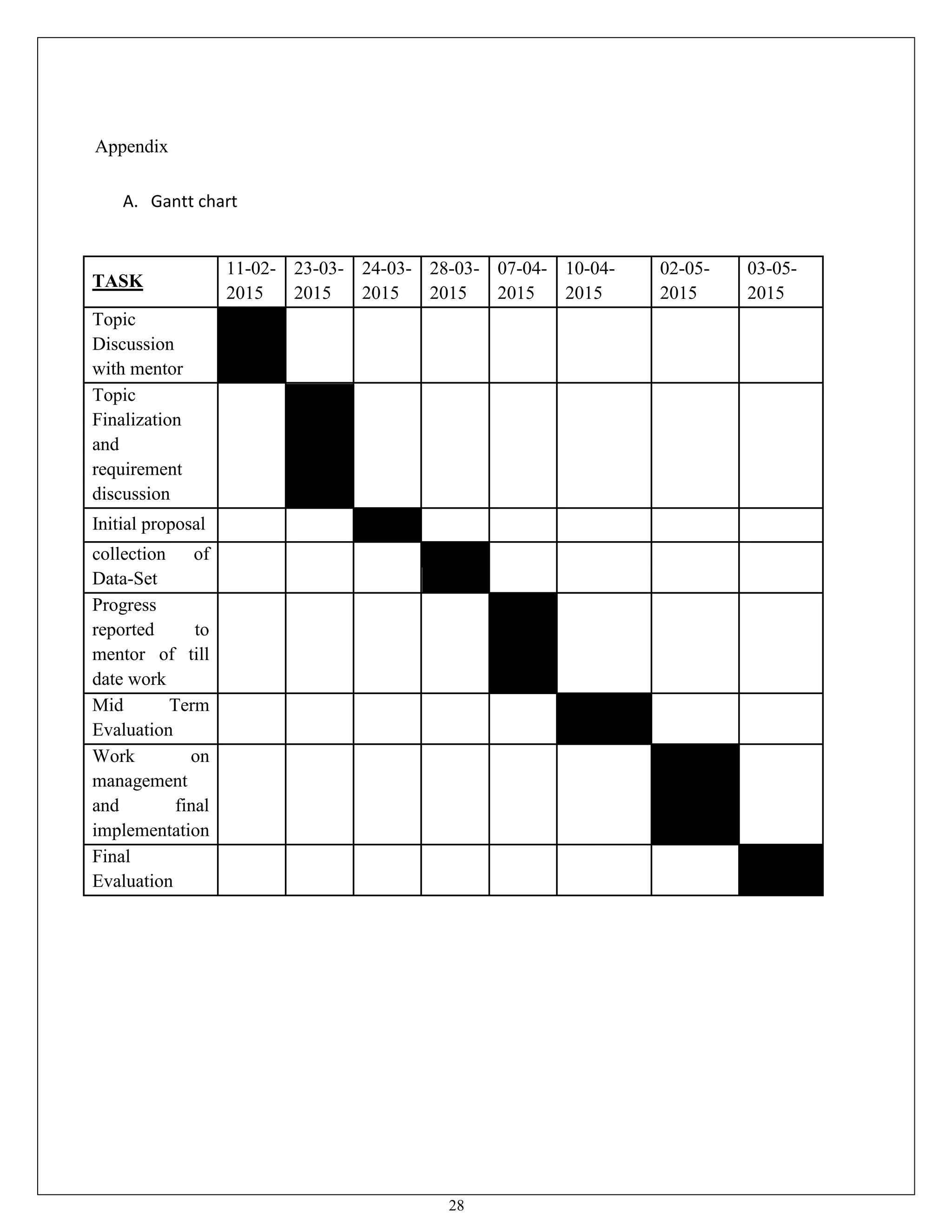
This document appears to be a project report submitted by two students for their Bachelor of Technology degree. It summarizes their simulation of ADIAN, a new ad-hoc network routing protocol based on distributed intelligence. The report includes chapters on introduction, background study of existing protocols, implementation details of ADIAN using NS2, and plans for conclusion and future work. The background study analyzes research papers on ad-hoc routing protocols and compares the performance of protocols like AODV, DSR, DSDV and OLSR. It also discusses networking simulation tools with a focus on NS2. The implementation chapter outlines the requirements, architecture, data structures, testing approach and risk mitigation plan for simulating ADIAN in NS2