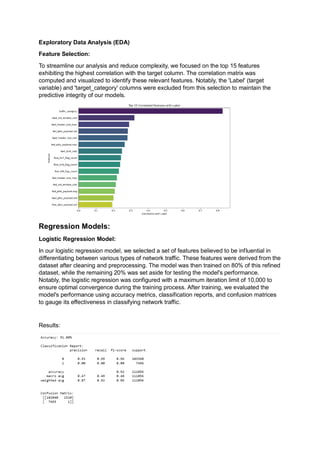
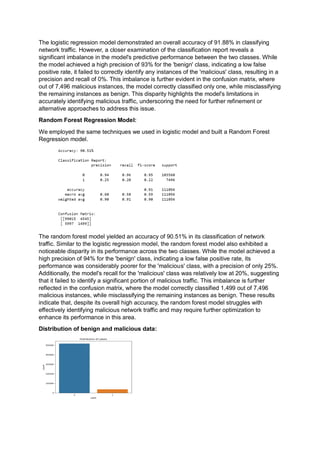
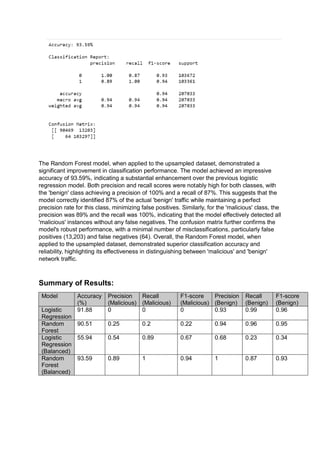
The document analyzes the effectiveness of machine learning algorithms, specifically logistic regression and random forest, in detecting malicious network traffic using the Hikari-2021 dataset. Initial models displayed high accuracy in classifying benign traffic but struggled significantly with malicious traffic, leading to the implementation of upsampling techniques to address class imbalances, resulting in improved performance. The enhanced random forest model achieved an impressive accuracy of 93.59% with high precision and recall for both classes, emphasizing the importance of machine learning in cybersecurity applications.