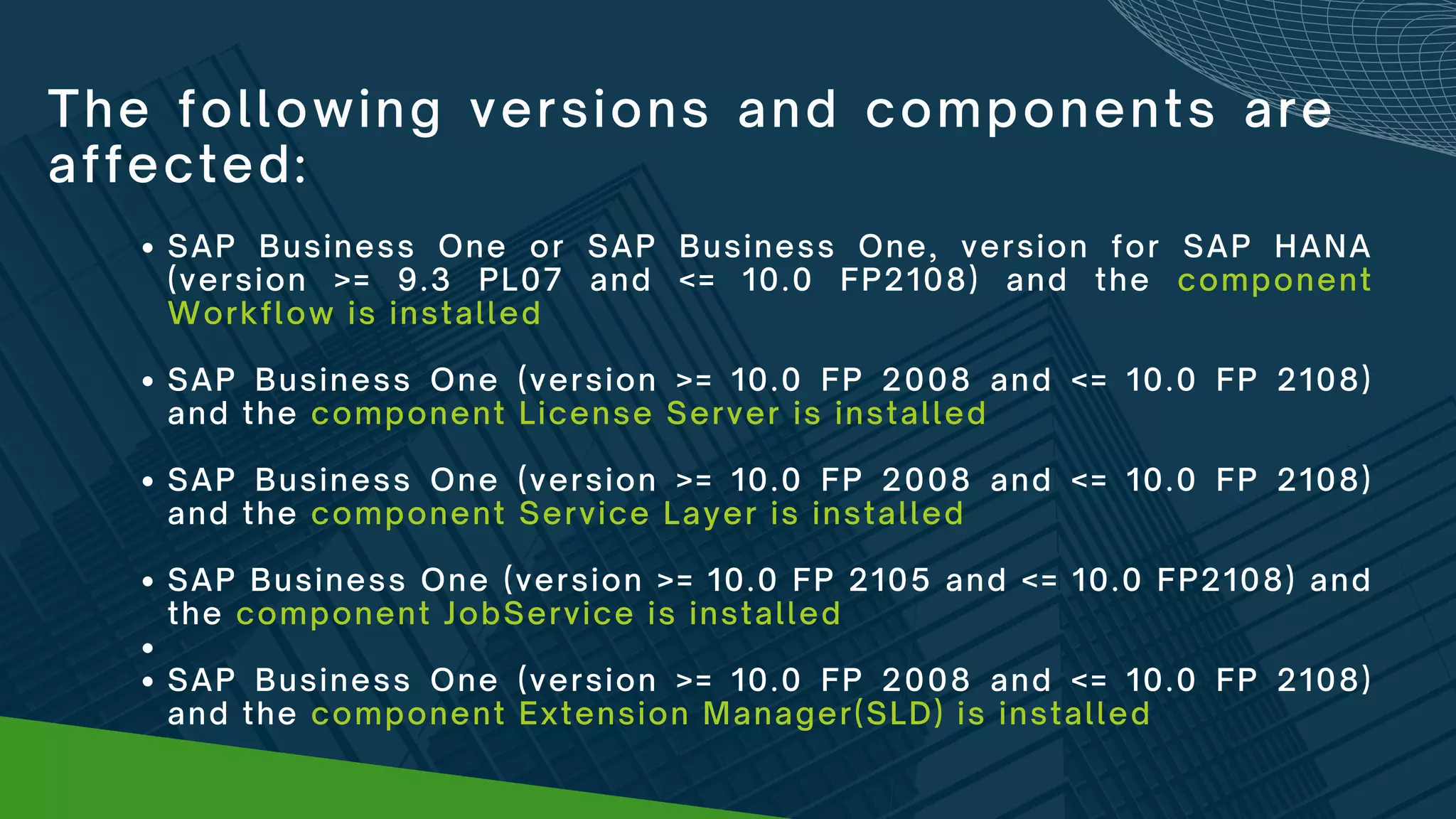
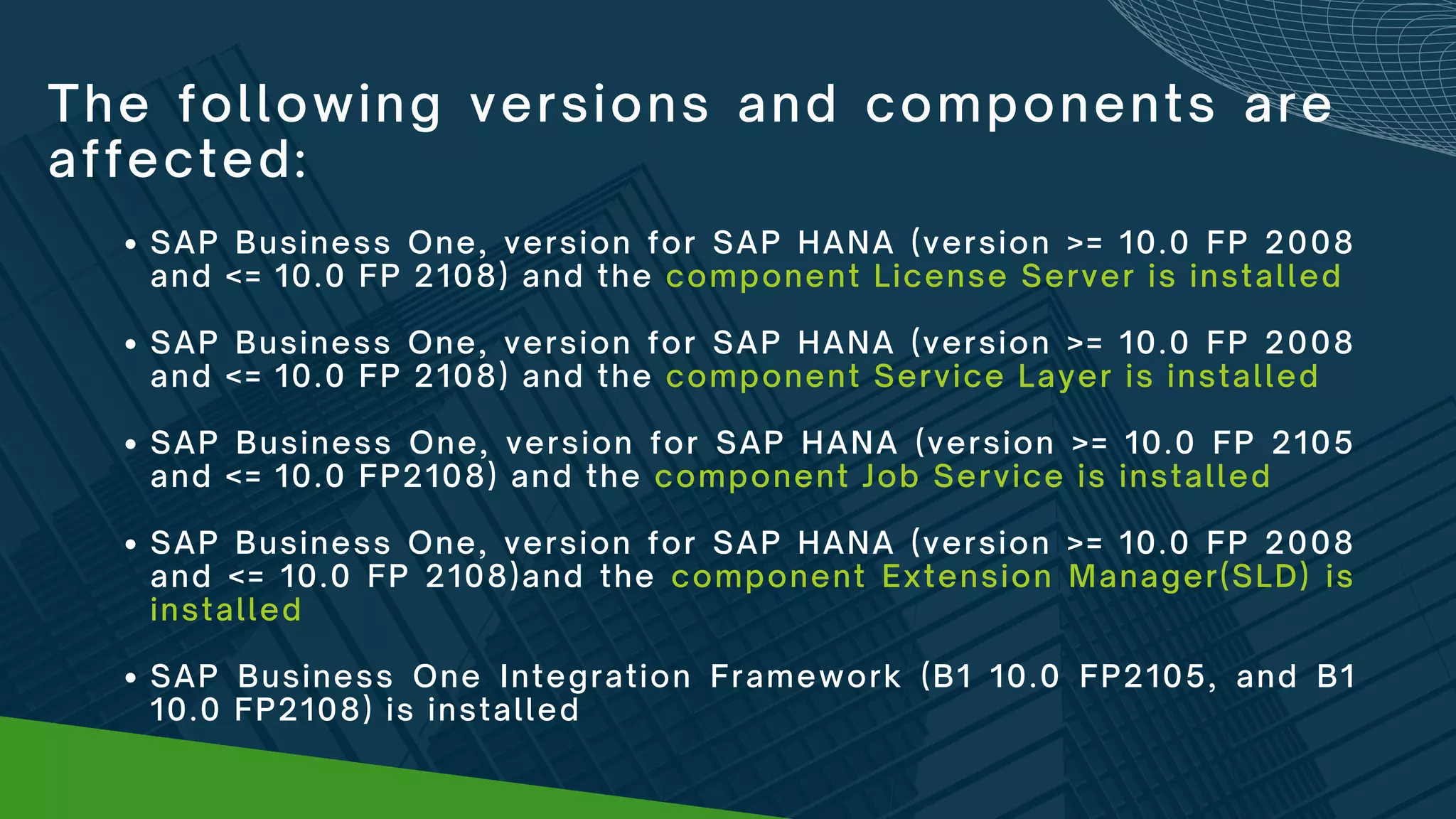
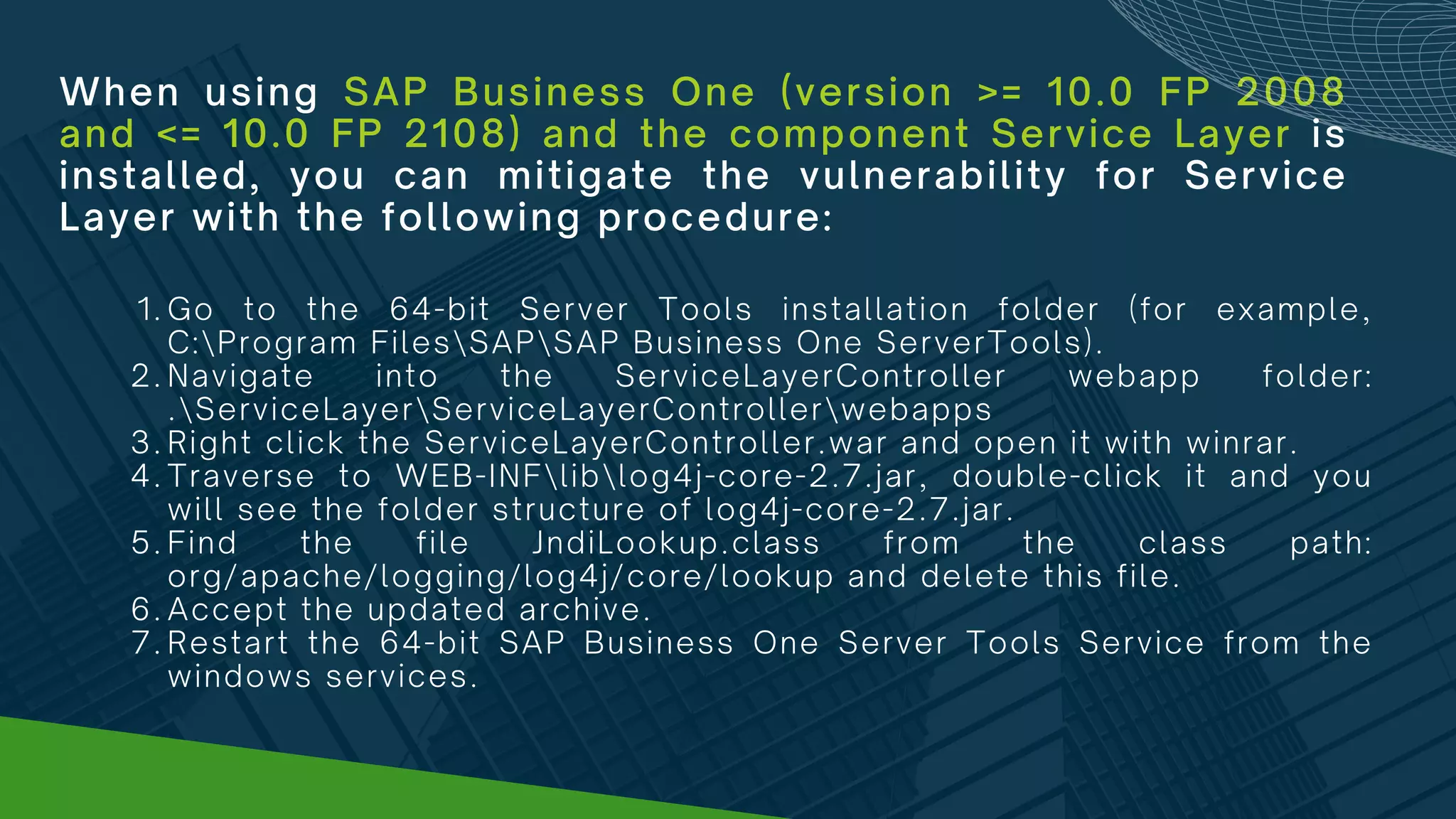
Log4j is widely used logging software that was found to have a vulnerability allowing malicious code execution. The vulnerability impacts many major software and internet services. Workarounds are provided to mitigate the vulnerability for various versions of SAP Business One and its components by removing or disabling the vulnerable class from the log4j library. Administrators are urged to apply the workarounds as the vulnerability poses a major security risk by enabling widespread hacking attempts.