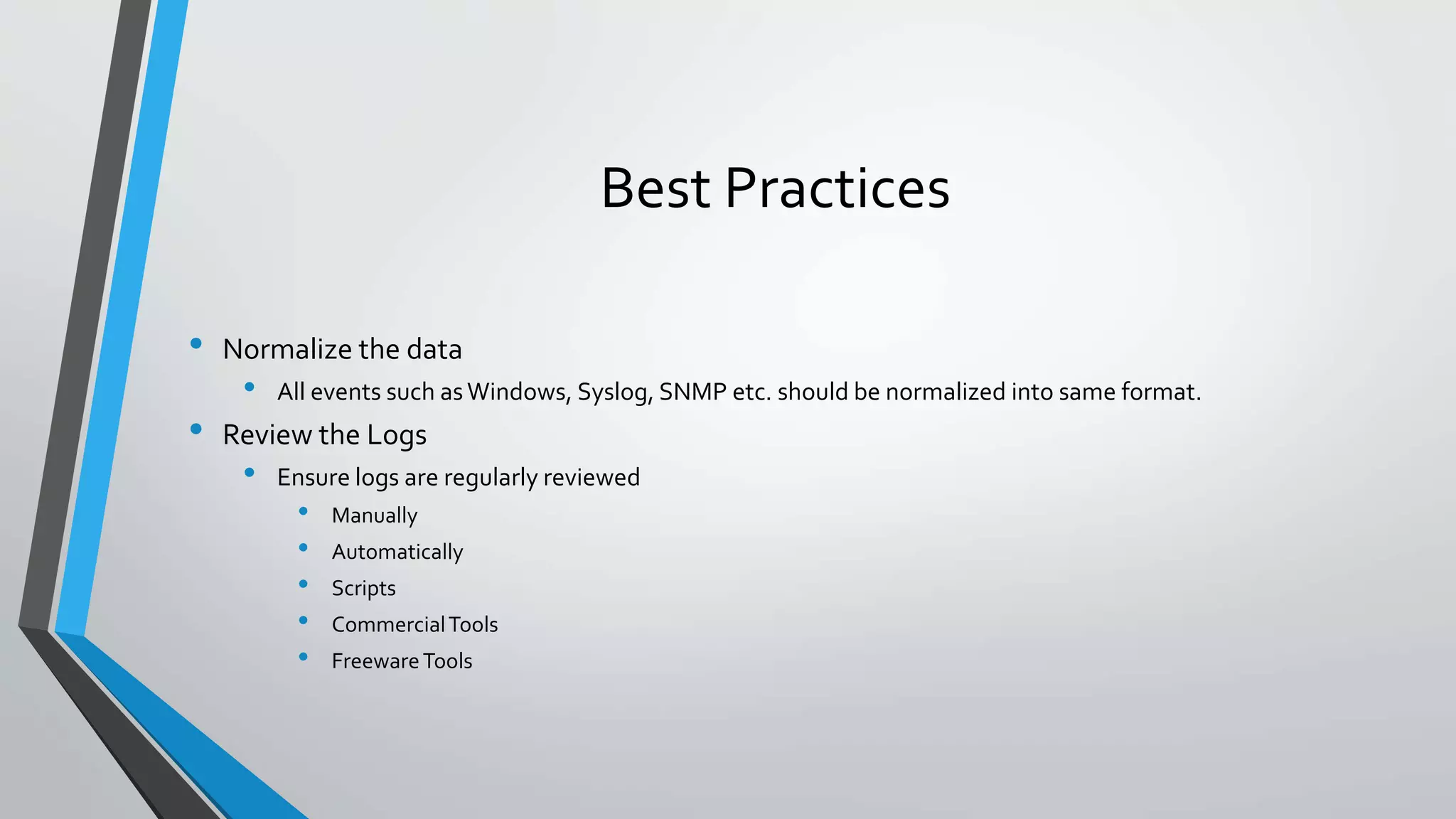
This document discusses log management and security incident and event management (SIEM). It defines what logs are, why they are important for tasks like intrusion detection, incident containment, and forensic analysis. It outlines the challenges of managing logs from different sources and formats. It provides best practices for developing logging policies, normalizing log data, centralizing, securing, and reviewing logs. It also discusses log retention, rotation, and tools like SIEM that provide real-time analysis and correlation of security events and alerts.