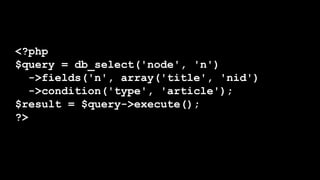
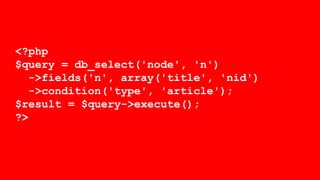
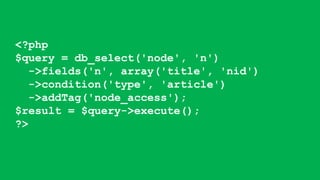
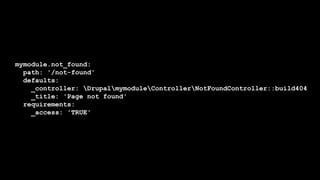
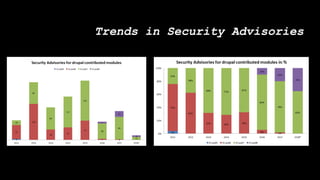
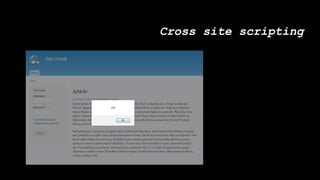
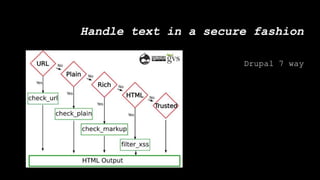
This document discusses secure coding practices for Drupal. It begins with an introduction of the presenter and covers topics like cross-site scripting, sanitization, access control, SQL injection, and CSRF. Code snippets are provided and attendees are asked to evaluate if they are secure. Recommendations are given around using Drupal APIs, filtering input, and reviewing security advisories. The importance of code reviews, testing, and learning from past issues is stressed.






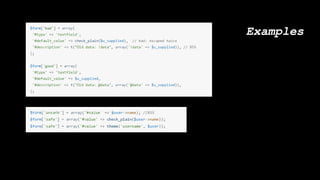

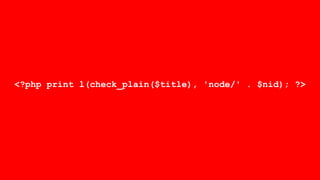
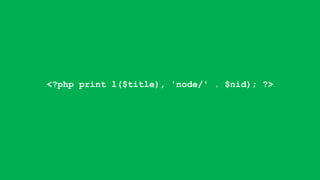
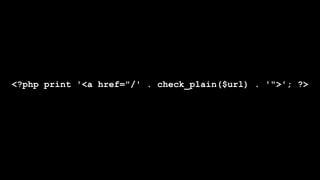

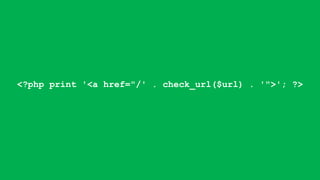
![foreach ($items as $delta => $item) {
$id = $item->getValue()['target_id'];
$content = Drupal::entityTypeManager()
->getStorage($entity_type_id)
->load($id);
$body = $content->get('body_field')->getValue()[0]['value'];
}
$elements[$delta] = array(
'#theme' => 'something_custom',
'#body' => $body,
);
return $elements;](https://image.slidesharecdn.com/letswritesecuredrupalcodeessen1-180319153201/85/Let-s-write-secure-Drupal-code-24-320.jpg)
![foreach ($items as $delta => $item) {
$id = $item->getValue()['target_id'];
$content = Drupal::entityTypeManager()
->getStorage($entity_type_id)
->load($id);
$body = $content->get('body_field')->getValue()[0]['value'];
}
$elements[$delta] = array(
'#theme' => 'something_custom',
'#body' => $body,
);
return $elements;](https://image.slidesharecdn.com/letswritesecuredrupalcodeessen1-180319153201/85/Let-s-write-secure-Drupal-code-25-320.jpg)
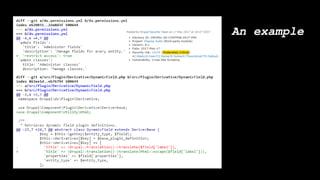
![foreach ($items as $delta => $item) {
$id = $item->getValue()['target_id'];
$content = Drupal::entityTypeManager()
->getStorage($entity_type_id)
->load($id);
$body = [
'#type' => 'processed_text',
'#text' => $content->get('body_field')->getValue()[0]['value'],
'#format' => $content->get('body_field')->getValue()[0]['format'], ];
}
$elements[$delta] = array(
'#theme' => 'something_custom',
'#body' => $body,
);
return $elements;](https://image.slidesharecdn.com/letswritesecuredrupalcodeessen1-180319153201/85/Let-s-write-secure-Drupal-code-26-320.jpg)





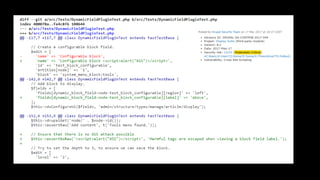
![<?php
function mymodule_menu() {
$items['admin/mymodule/settings'] = array(
'title' => 'Settings of my module',
'page callback' => 'drupal_get_form',
'page arguments' => array('mymodule_setting_form'),
'access arguments' => array('administer mymodule'),
'type' => MENU_LOCAL_ACTION,
);
return $items;
}
?>](https://image.slidesharecdn.com/letswritesecuredrupalcodeessen1-180319153201/85/Let-s-write-secure-Drupal-code-33-320.jpg)
![<?php
function mymodule_menu() {
$items['admin/mymodule/settings'] = array(
'title' => 'Settings of my module',
'page callback' => 'drupal_get_form',
'page arguments' => array('mymodule_setting_form'),
'access arguments' => array('administer mymodule'),
'type' => MENU_LOCAL_ACTION,
);
return $items;
}
?>](https://image.slidesharecdn.com/letswritesecuredrupalcodeessen1-180319153201/85/Let-s-write-secure-Drupal-code-34-320.jpg)