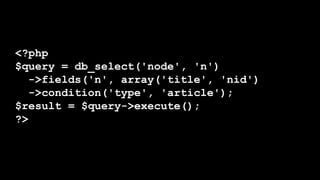
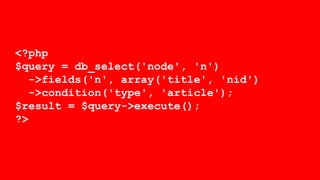
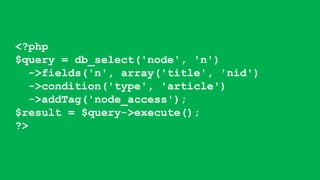
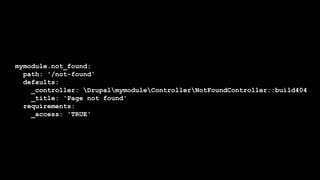
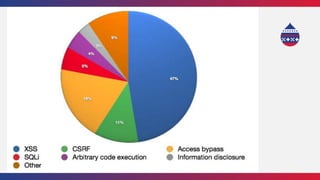
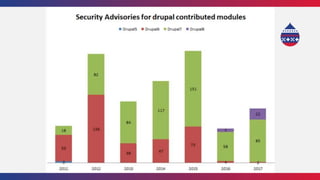
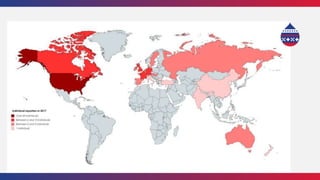
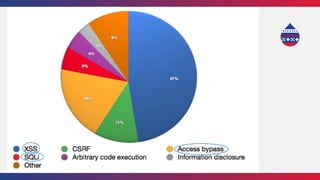
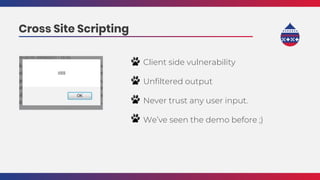
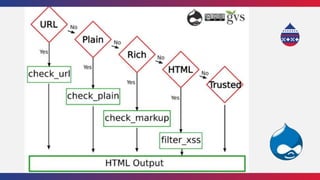
This document summarizes a presentation about writing secure Drupal code. It discusses common vulnerabilities like cross-site scripting, access bypass, and SQL injection. It provides examples of secure and vulnerable code and recommends best practices to prevent vulnerabilities, including input filtering, access control, and automated testing. It also discusses security improvements in Drupal 8 and learning from security advisories.















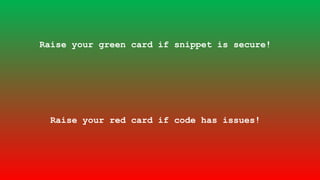
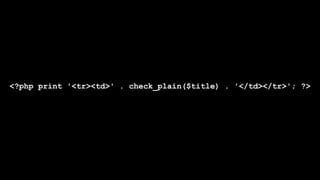
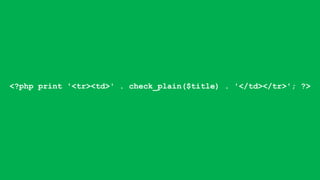
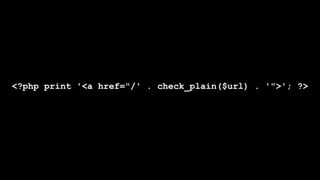

![foreach ($items as $delta => $item) {
$id = $item->getValue()['target_id'];
$content = Drupal::entityTypeManager()
->getStorage($entity_type_id)
->load($id);
$body = $content->get('body_field')->getValue()[0]['value'];
}
$elements[$delta] = array(
'#theme' => 'something_custom',
'#body' => $body,
);
return $elements;](https://image.slidesharecdn.com/letswritesecuredrupalcodeoslo-181110092805/85/Let-s-write-secure-Drupal-code-DrupalCamp-Oslo-2018-31-320.jpg)
![foreach ($items as $delta => $item) {
$id = $item->getValue()['target_id'];
$content = Drupal::entityTypeManager()
->getStorage($entity_type_id)
->load($id);
$body = $content->get('body_field')->getValue()[0]['value'];
}
$elements[$delta] = array(
'#theme' => 'something_custom',
'#body' => $body,
);
return $elements;](https://image.slidesharecdn.com/letswritesecuredrupalcodeoslo-181110092805/85/Let-s-write-secure-Drupal-code-DrupalCamp-Oslo-2018-32-320.jpg)
![foreach ($items as $delta => $item) {
$id = $item->getValue()['target_id'];
$content = Drupal::entityTypeManager()
->getStorage($entity_type_id)
->load($id);
$body = [
'#type' => 'processed_text',
'#text' => $content->get('body_field')->getValue()[0]['value'],
'#format' => $content->get('body_field')->getValue()[0]['format'], ];
}
$elements[$delta] = array(
'#theme' => 'something_custom',
'#body' => $body,
);
return $elements;](https://image.slidesharecdn.com/letswritesecuredrupalcodeoslo-181110092805/85/Let-s-write-secure-Drupal-code-DrupalCamp-Oslo-2018-33-320.jpg)





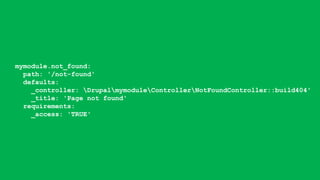
![<?php
function mymodule_menu() {
$items['admin/mymodule/settings'] = array(
'title' => 'Settings of my module',
'page callback' => 'drupal_get_form',
'page arguments' => array('mymodule_setting_form'),
'access arguments' => array('administer mymodule'),
'type' => MENU_LOCAL_ACTION,
);
return $items;
}
?>](https://image.slidesharecdn.com/letswritesecuredrupalcodeoslo-181110092805/85/Let-s-write-secure-Drupal-code-DrupalCamp-Oslo-2018-39-320.jpg)
![<?php
function mymodule_menu() {
$items['admin/mymodule/settings'] = array(
'title' => 'Settings of my module',
'page callback' => 'drupal_get_form',
'page arguments' => array('mymodule_setting_form'),
'access arguments' => array('administer mymodule'),
'type' => MENU_LOCAL_ACTION,
);
return $items;
}
?>](https://image.slidesharecdn.com/letswritesecuredrupalcodeoslo-181110092805/85/Let-s-write-secure-Drupal-code-DrupalCamp-Oslo-2018-40-320.jpg)