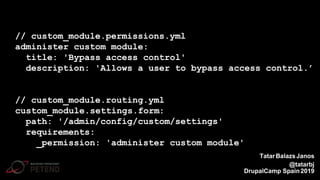
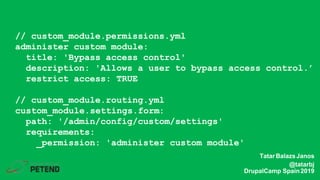
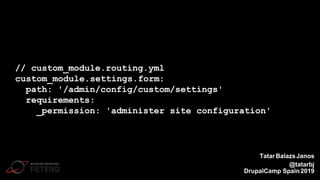
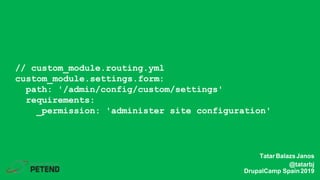
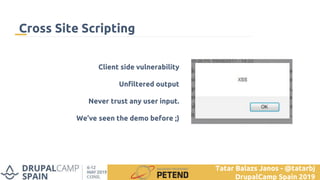
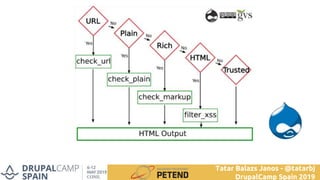
The document summarizes a presentation on writing secure Drupal code. It introduces the presenter Tatar Balazs Janos and his experience with Drupal. It then covers common types of vulnerabilities like cross-site scripting, access bypass, SQL injection and how to prevent them. Examples of vulnerable code are provided and improved upon. Best practices discussed include using database queries, input filtering, automated testing and restricting permissions.













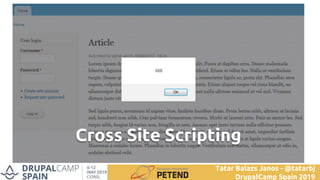


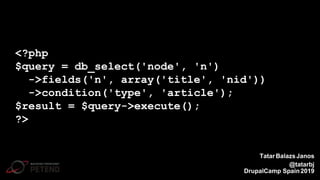
![function custom_field_formatter_view(...) {
foreach ($items as $key => $value) {
//...
$element[$key] = array(
'#type' => 'markup',
'#markup' => t('<img src="!src" alt="@alt" />',
array('!src' => $value['src'], ‚$alt’ => $value['alt'])),
);
//...
}
return $element;
}
TatarBalazsJanos
@tatarbj
DrupalCamp Spain2019](https://image.slidesharecdn.com/letswritesecuredrupalcodeconil2019-190524120348/85/Let-s-write-secure-Drupal-code-DrupalCamp-Spain-2019-22-320.jpg)
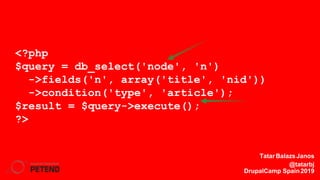
![function custom_field_formatter_view(...) {
foreach ($items as $key => $value) {
//...
$element[$key] = array(
'#type' => 'markup',
'#markup' => t('<img src="!src" alt="@alt" />',
array('!src' => $value['src'], ‚$alt’ => $value['alt'])),
);
//...
}
return $element;
}
TatarBalazsJanos
@tatarbj
DrupalCamp Spain2019](https://image.slidesharecdn.com/letswritesecuredrupalcodeconil2019-190524120348/85/Let-s-write-secure-Drupal-code-DrupalCamp-Spain-2019-23-320.jpg)
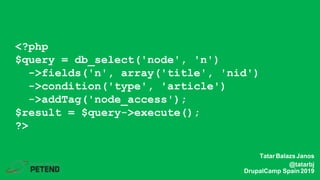
![function custom_field_formatter_view(...) {
foreach ($items as $key => $value) {
//...
$element[$key] = array(
'#type' => 'markup',
'#markup' => t('<img src="@src" alt="@alt" />',
array('@src' => $value['src'], ‚$alt’ => $value['alt'])),
);
//...
}
return $element;
}
TatarBalazsJanos
@tatarbj
DrupalCamp Spain2019](https://image.slidesharecdn.com/letswritesecuredrupalcodeconil2019-190524120348/85/Let-s-write-secure-Drupal-code-DrupalCamp-Spain-2019-24-320.jpg)
![foreach ($items as $delta => $item) {
$id = $item->getValue()['target_id'];
$content = Drupal::entityTypeManager()
->getStorage($entity_type_id)
->load($id);
$body = $content->get('body_field')->getValue()[0]['value'];
}
$elements[$delta] = array(
'#theme' => 'something_custom',
'#body' => $body,
);
return $elements;
TatarBalazsJanos
@tatarbj
DrupalCamp Spain2019](https://image.slidesharecdn.com/letswritesecuredrupalcodeconil2019-190524120348/85/Let-s-write-secure-Drupal-code-DrupalCamp-Spain-2019-27-320.jpg)
![foreach ($items as $delta => $item) {
$id = $item->getValue()['target_id'];
$content = Drupal::entityTypeManager()
->getStorage($entity_type_id)
->load($id);
$body = $content->get('body_field')->getValue()[0]['value'];
}
$elements[$delta] = array(
'#theme' => 'something_custom',
'#body' => $body,
);
return $elements;
TatarBalazsJanos
@tatarbj
DrupalCamp Spain2019](https://image.slidesharecdn.com/letswritesecuredrupalcodeconil2019-190524120348/85/Let-s-write-secure-Drupal-code-DrupalCamp-Spain-2019-28-320.jpg)
![foreach ($items as $delta => $item) {
$id = $item->getValue()['target_id'];
$content = Drupal::entityTypeManager()
->getStorage($entity_type_id)
->load($id);
$body = [
'#type' => 'processed_text',
'#text' => $content->get('body_field')->getValue()[0]['value'],
'#format' => $content->get('body_field')->getValue()[0]['format'], ];
}
$elements[$delta] = array(
'#theme' => 'something_custom',
'#body' => $body,
);
return $elements;
TatarBalazsJanos
@tatarbj
DrupalCamp Spain2019](https://image.slidesharecdn.com/letswritesecuredrupalcodeconil2019-190524120348/85/Let-s-write-secure-Drupal-code-DrupalCamp-Spain-2019-29-320.jpg)


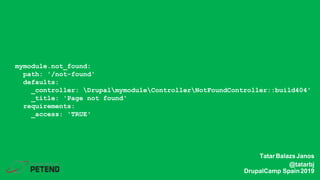



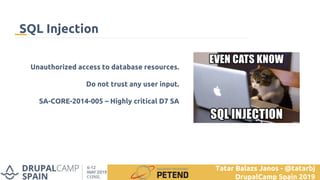
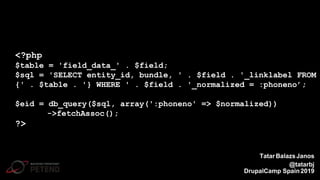

![<?php
function _generate_password($length = 8) {
$pass = ’’;
for ($i = 0; $i < $length; $i++) {
// Each iteration, pick a random character from the
// allowable string and append it to the password:
$pass .= $allowable_characters[mt_rand(0, $len)];
}
}
?>
TatarBalazsJanos
@tatarbj
DrupalCamp Spain2019](https://image.slidesharecdn.com/letswritesecuredrupalcodeconil2019-190524120348/85/Let-s-write-secure-Drupal-code-DrupalCamp-Spain-2019-51-320.jpg)
![<?php
function _generate_password($length = 8) {
$pass = ’’;
for ($i = 0; $i < $length; $i++) {
// Each iteration, pick a random character from the
// allowable string and append it to the password:
$pass .= $allowable_characters[mt_rand(0, $len)];
}
}
?>
TatarBalazsJanos
@tatarbj
DrupalCamp Spain2019](https://image.slidesharecdn.com/letswritesecuredrupalcodeconil2019-190524120348/85/Let-s-write-secure-Drupal-code-DrupalCamp-Spain-2019-52-320.jpg)
![<?php
function _generate_password($length = 8) {
$pass = ’’;
for ($i = 0; $i < $length; $i++) {
do {
// Find a secure random number within the range needed.
$index = ord(drupal_random_bytes(1));
} while ($index > $len);
$pass .= $allowable_characters[$index];
}
}
?>
TatarBalazsJanos
@tatarbj
DrupalCamp Spain2019](https://image.slidesharecdn.com/letswritesecuredrupalcodeconil2019-190524120348/85/Let-s-write-secure-Drupal-code-DrupalCamp-Spain-2019-53-320.jpg)