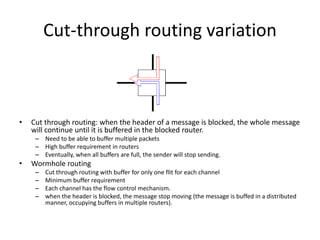
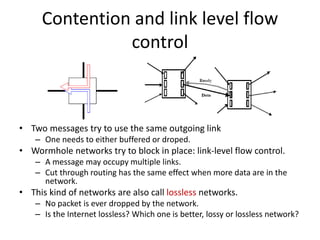
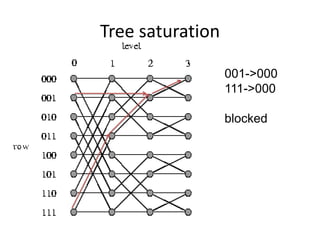
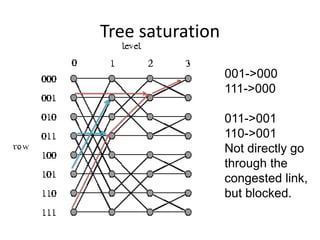
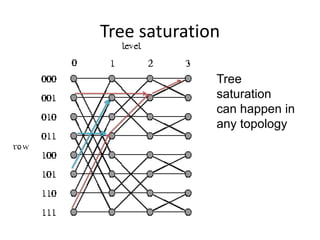
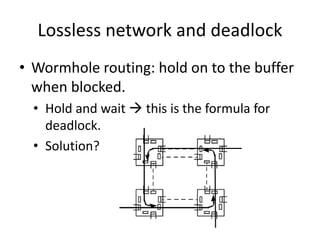
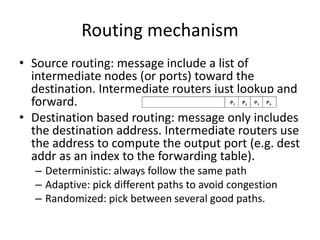
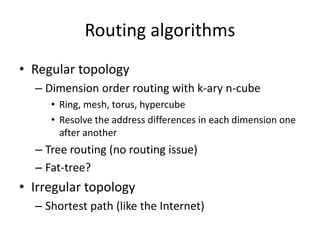
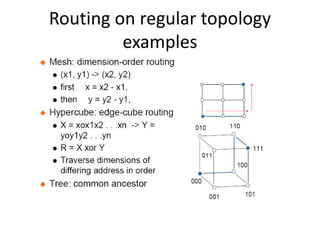
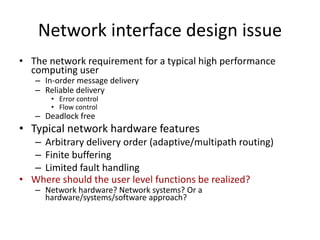
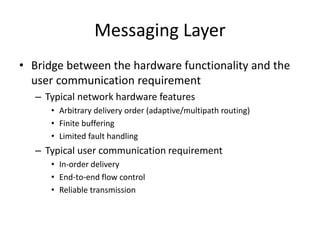
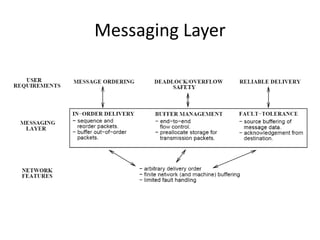
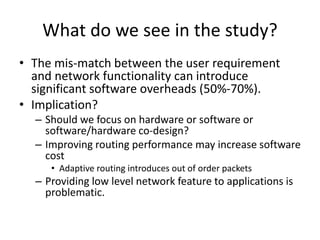
This document discusses switching, routing, and flow control in interconnection networks. It covers different switching mechanisms like packet switching and circuit switching. It also discusses routing algorithms and techniques to avoid deadlocks like virtual channels and deadlock-free routing. The key topics are how packets are routed through switches, challenges like tree saturation and deadlocks, and approaches to provide reliable communication while matching the capabilities of the network hardware.