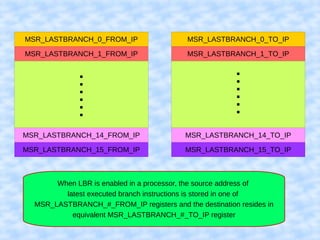
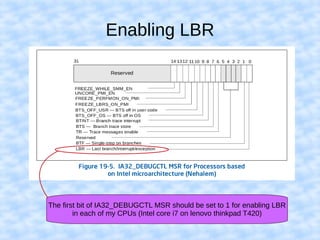
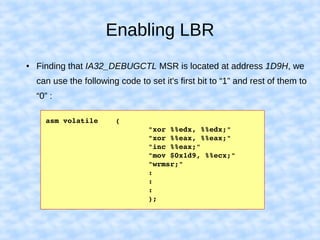
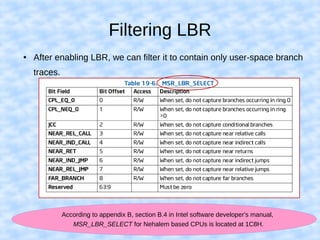
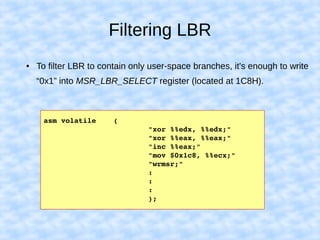
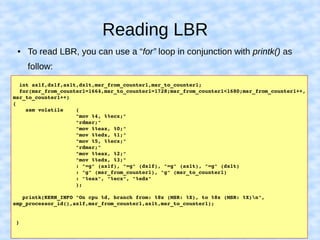
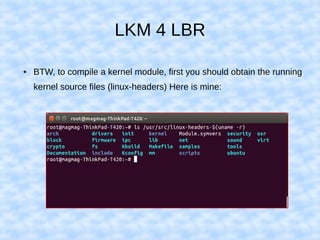
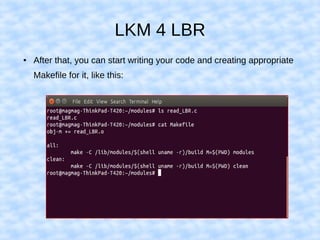
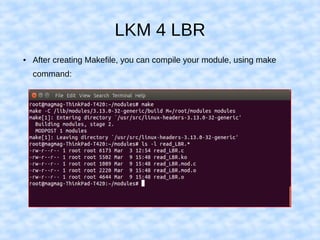
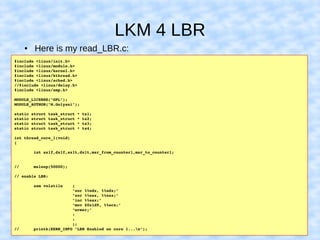
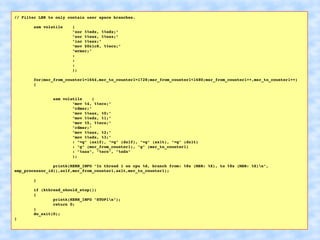
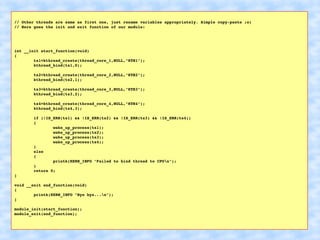
The document explains how to access Last Branch Record (LBR) contents on Intel x86 through a Linux kernel module, detailing concepts such as last branch records, branch instructions, and model-specific registers (MSRs). It describes the steps to enable LBR, including setting specific MSRs, filtering LBR for user-space branches, and illustrates reading LBR using assembly code within a kernel module context. The document is highly technical, targeting developers interested in low-level CPU monitoring techniques.