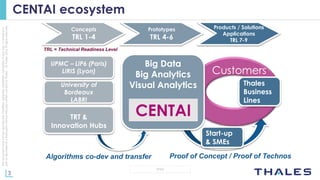
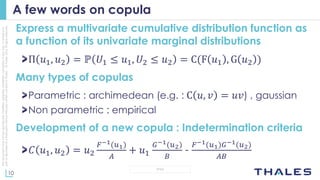
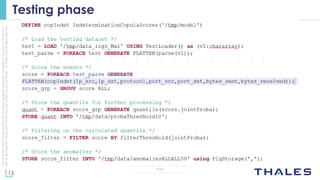
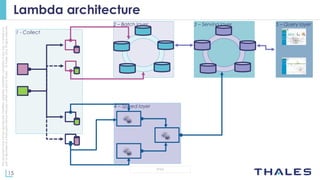
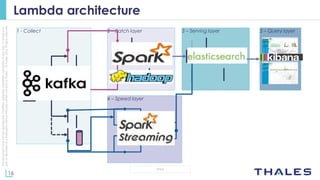
The document discusses using big data analytics and machine learning techniques for cybersecurity applications like anomaly detection. It describes Thales' CENTAI lab and its work developing batch and real-time anomaly detection algorithms using techniques like copula-based density estimation. The algorithms were initially developed as Pig UDFs and then ported to Spark to enable both batch and streaming analysis on large logs. The goal is to improve detection of targeted and non-targeted cyber attacks.