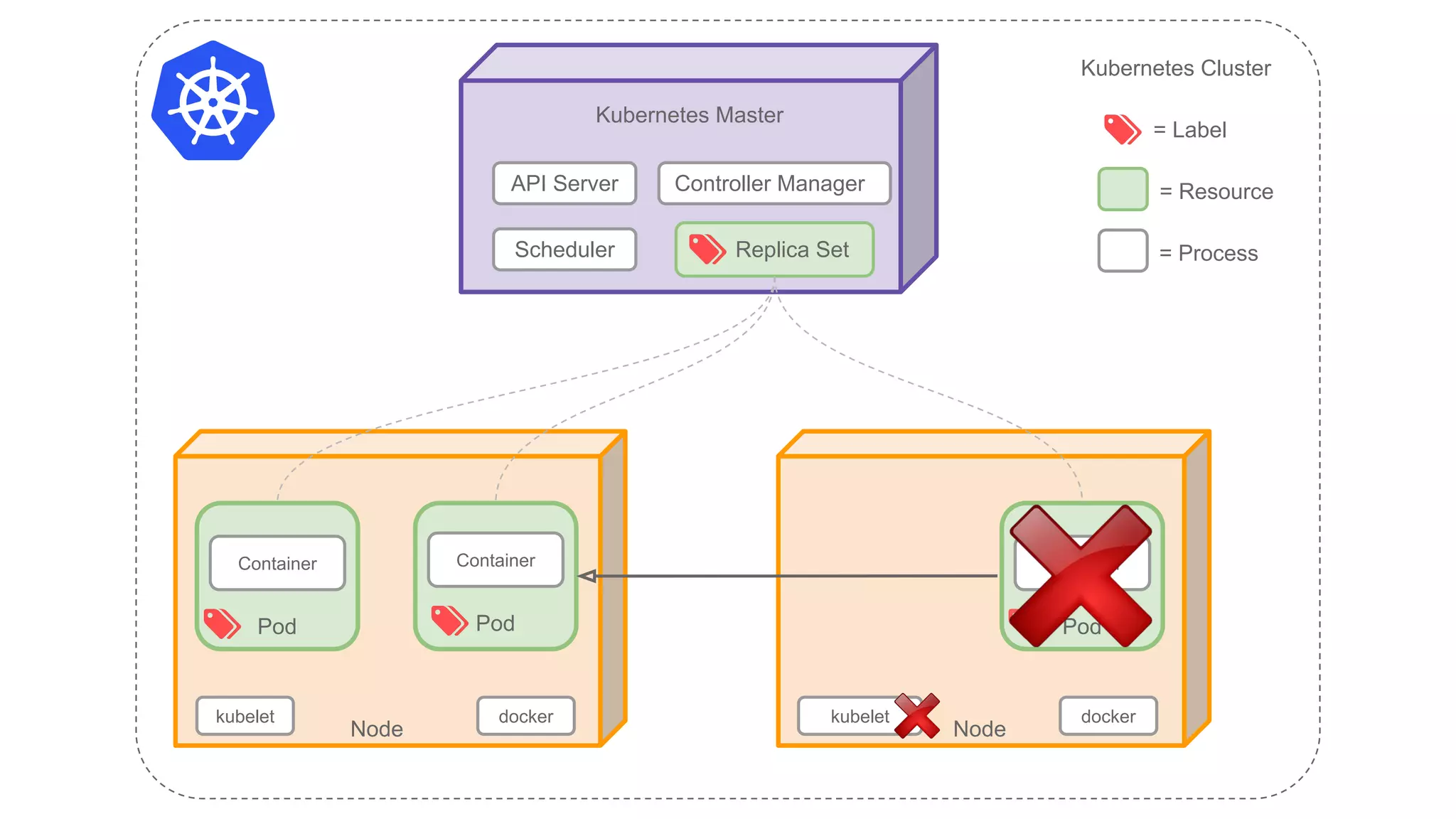
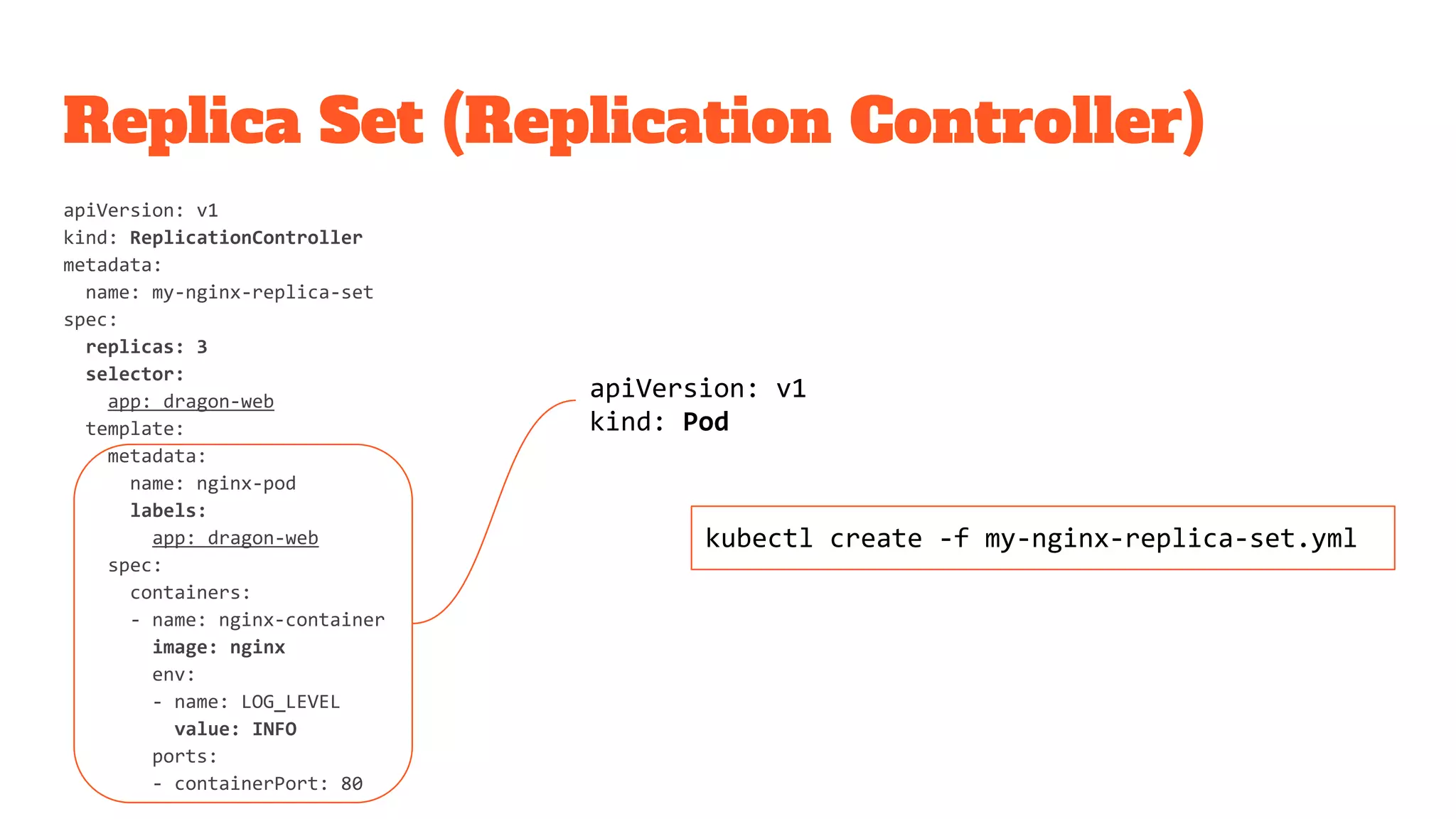
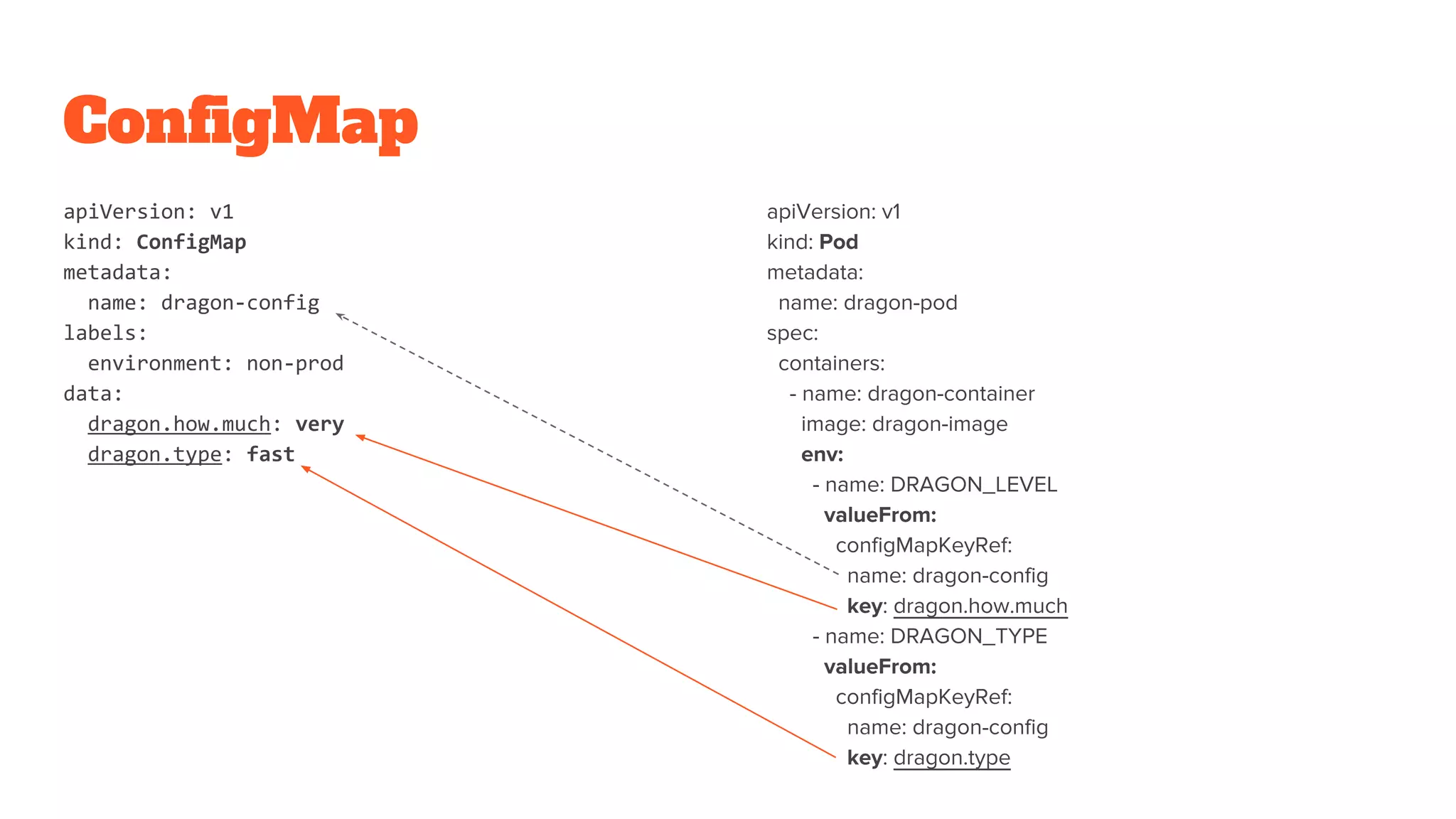
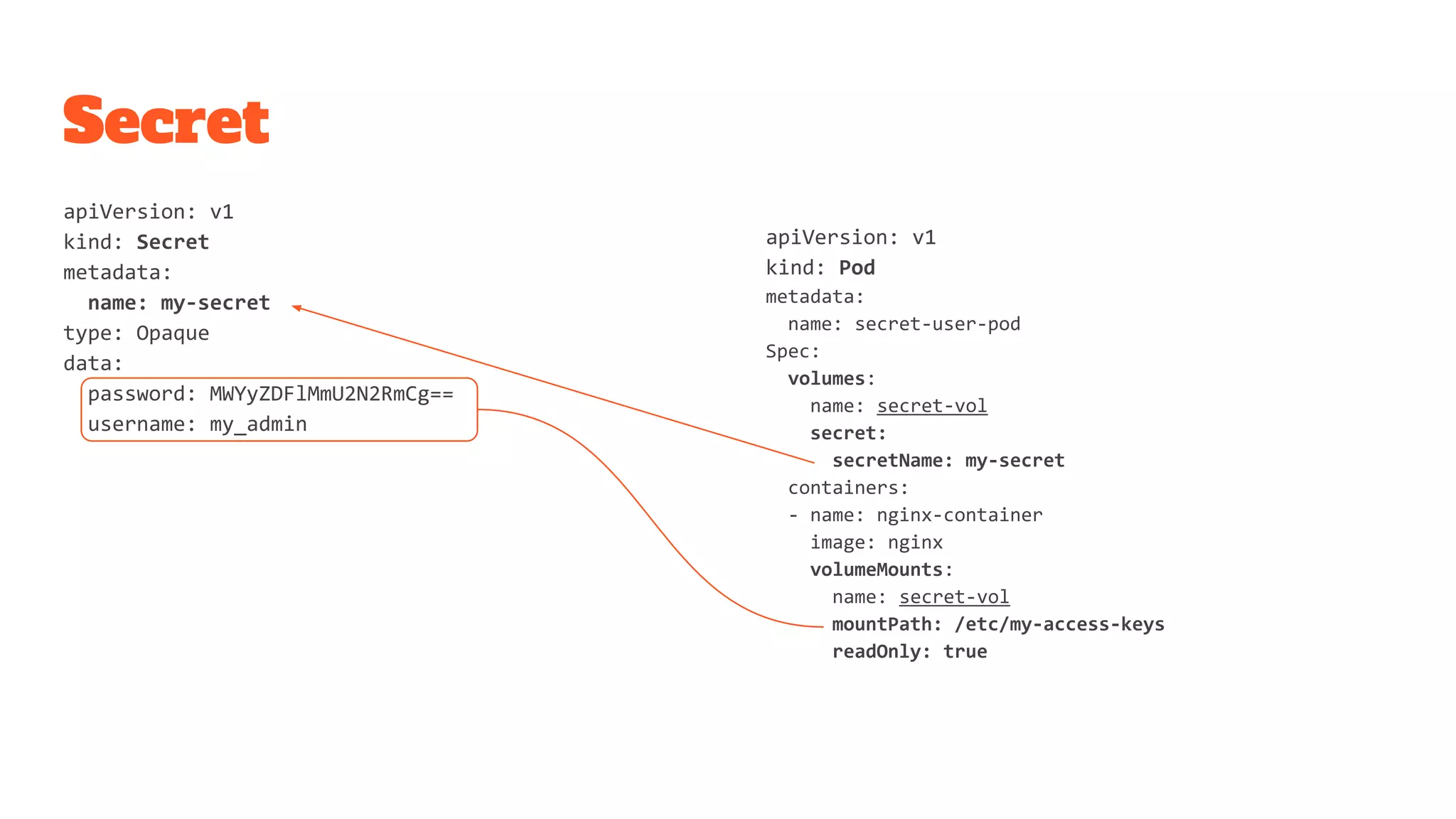
The document provides a comprehensive overview of Kubernetes and its application in microservices architecture, emphasizing the importance of consistent build artifacts, configuration management, and service discovery. It outlines the key resources and components within Kubernetes, such as pods, services, and secrets, and offers guidance on best practices for deployment and configuration. Additionally, it highlights the significance of using CI/CD pipelines and production strategies for effective cluster management and application health monitoring.






![Dockerfile
FROM debian:jessie
RUN apt-get update
&& apt-get install -y
openjdk-8-jre-headless
COPY my-app.jar /my-app.jar
ENV MY_APP_CONF_VAR default-value
CMD [“java”, “-jar”, “/my-app.jar”]
docker build -t registry/image_name .
docker push registry/image_name](https://image.slidesharecdn.com/kubernetes-trainingmicro-dragonsforaseriousbattle-170421124928/75/Kubernetes-training-micro-dragons-for-a-serious-battle-7-2048.jpg)




![Service
{
"apiVersion": "v1",
"kind": "Service",
"metadata": {
"name": "my-service"
},
"spec": {
"selector": {
"app": "dragon-web"
},
"ports": [{
"protocol": "TCP",
"port": 80,
"targetPort": 80
}]
}
}](https://image.slidesharecdn.com/kubernetes-trainingmicro-dragonsforaseriousbattle-170421124928/75/Kubernetes-training-micro-dragons-for-a-serious-battle-18-2048.jpg)