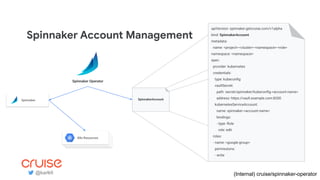
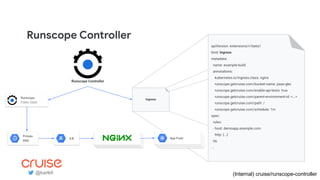
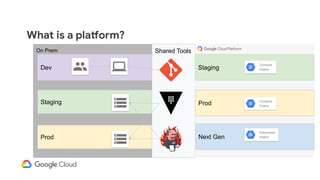
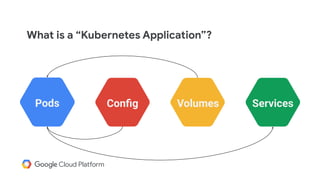
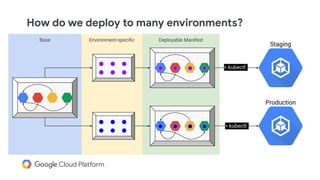
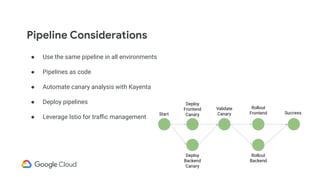
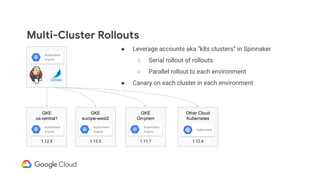
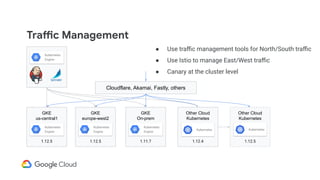
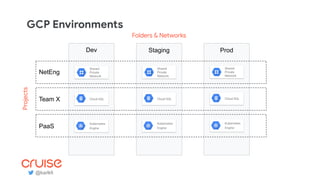
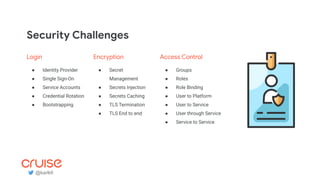
The document discusses the challenges and strategies of implementing CI/CD in multi-environment infrastructure using Kubernetes. It outlines the benefits of building a consistent platform, application rollout strategies, and tools like Helm and Kustomize for managing Kubernetes manifests. Additionally, it emphasizes the importance of automation, traffic management, and security considerations while managing deployments across various environments, including on-premises and multi-cloud scenarios.












![apiVersion: v1
kind: Pod
metadata:
name: myapp-pod
labels:
app: myapp
spec:
containers:
- name: myapp-container
image: busybox
command: ['myapp']
apiVersion: apps/v1
kind: Deployment
metadata:
name: nginx-deployment
labels:
app: nginx
spec:
replicas: 3
selector:
matchLabels:
app: nginx
template:
metadata:
labels:
app: nginx
spec:
containers:
- name: nginx
image: nginx:1.7.9
ports:
- containerPort: 80
kind: Service
apiVersion: v1
metadata:
name: my-service
spec:
selector:
app: MyApp
ports:
- protocol: TCP
port: 80
targetPort: 9376
apiVersion: v1
kind: ConfigMap
metadata:
name: game-config
namespace: default
data:
game.properties: |
enemies=aliens
lives=3
ui.properties: |
color.good=purple
color.bad=yellow
allow.textmode=true
how.nice.to.look=fairlyNice
kind: Endpoints
apiVersion: v1
metadata:
name: my-service
subsets:
- addresses:
- ip: 1.2.3.4
ports:
- port: 9376
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: test-ingress
spec:
rules:
- http:
paths:
- path: /testpath
backend:
serviceName: test
servicePort: 80](https://image.slidesharecdn.com/hyb205cicdacrossmultipleenvironments-190412044630/85/CI-CD-Across-Multiple-Environments-17-320.jpg)







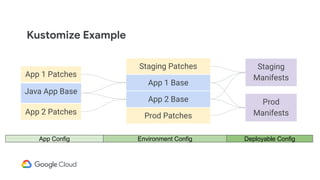
![Kustomize
apiVersion: v1
kind: Pod
metadata:
name: myapp-pod
labels:
app: myapp
spec:
containers:
- name: myapp-container
image: busybox
command: ['app']
apiVersion: v1
kind: Pod
metadata:
name: myapp-pod
spec:
containers:
- name: myapp
command: ['app', '--dev']
apiVersion: v1
kind: Pod
metadata:
name: myapp-pod
labels:
app: myapp
spec:
containers:
- name: myapp-container
image: busybox
command: ['app', '--dev']
base.yaml dev-patch.yaml output.yaml](https://image.slidesharecdn.com/hyb205cicdacrossmultipleenvironments-190412044630/85/CI-CD-Across-Multiple-Environments-27-320.jpg)

















![Image Building
apiVersion: build.knative.dev/v1alpha1
kind: Build
metadata:
name: example-build
spec:
serviceAccountName: build-auth-example
source:
git:
url: https://github.com/example/build-example.git
revision: master
steps:
- name: ubuntu-example
image: ubuntu
args: [“ubuntu-build-example”, “SECRETS-example.md”]
steps:
- image: gcr.io/example-builders/build-example
args: [“echo”, “hello-example”, “build”]
Build
GCR
Container Registry
(OSS) https://github.com/knative/build
Github
Source Control
Knative Build
@karlkfi](https://image.slidesharecdn.com/hyb205cicdacrossmultipleenvironments-190412044630/85/CI-CD-Across-Multiple-Environments-54-320.jpg)