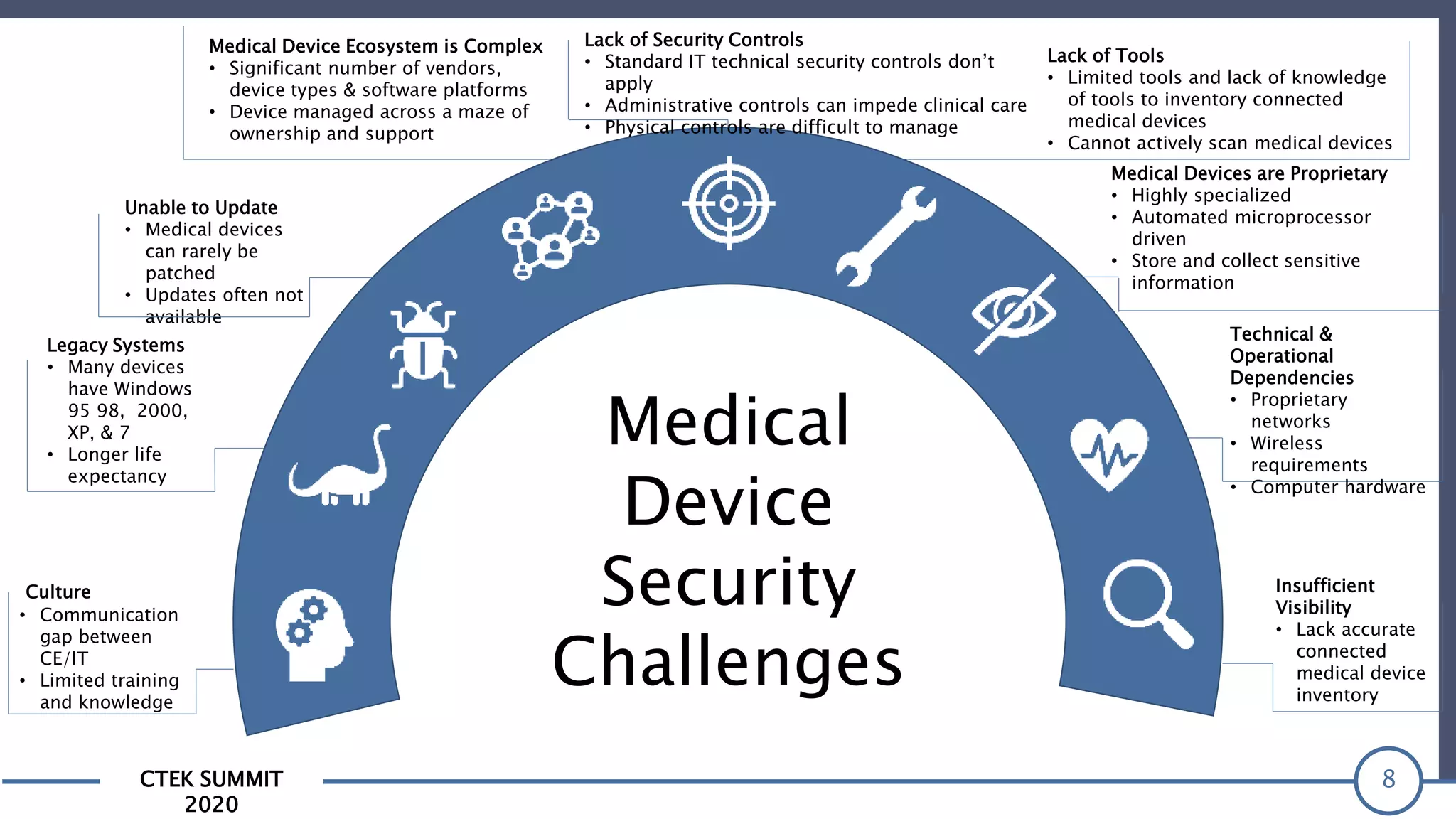
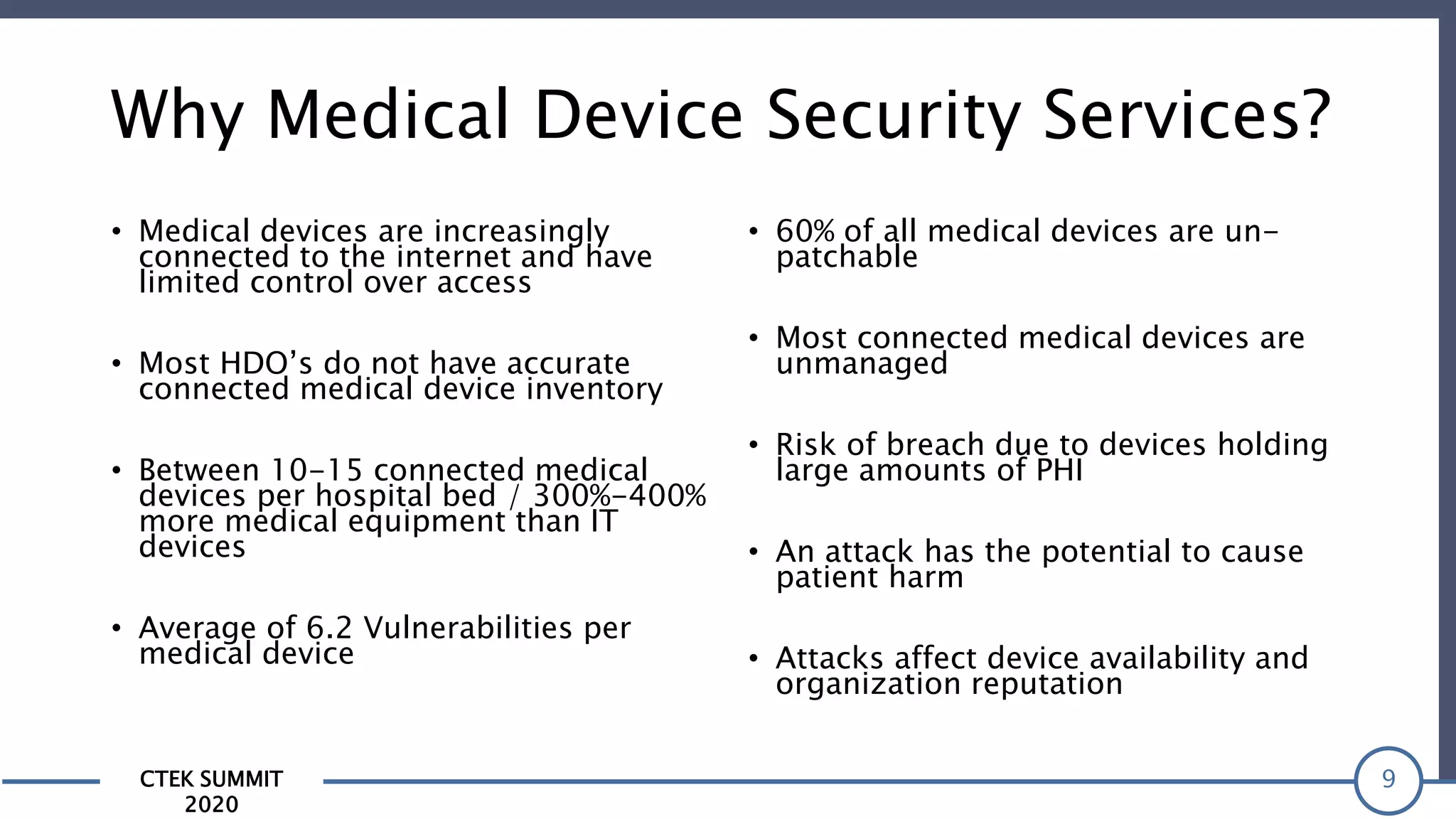
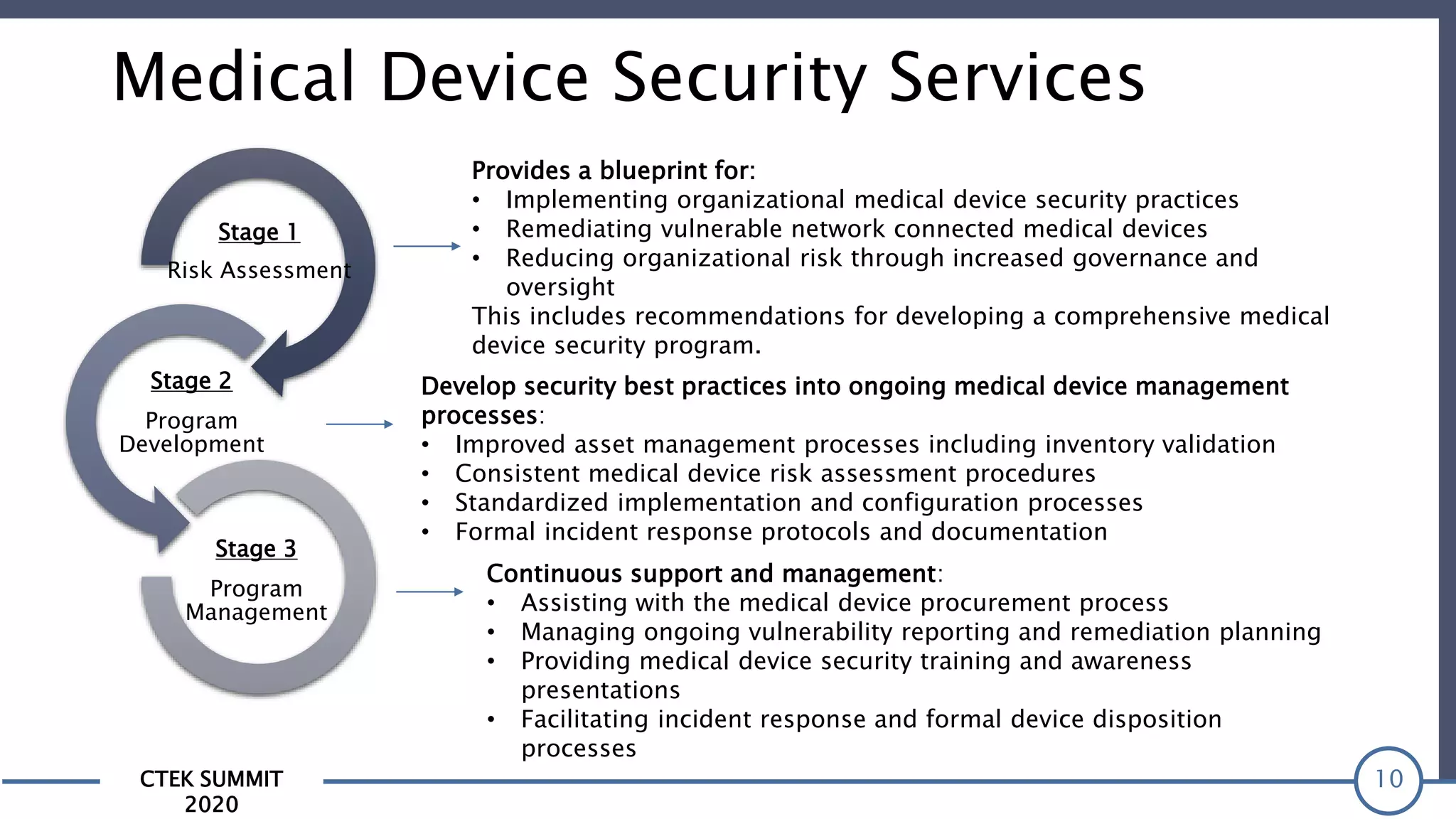
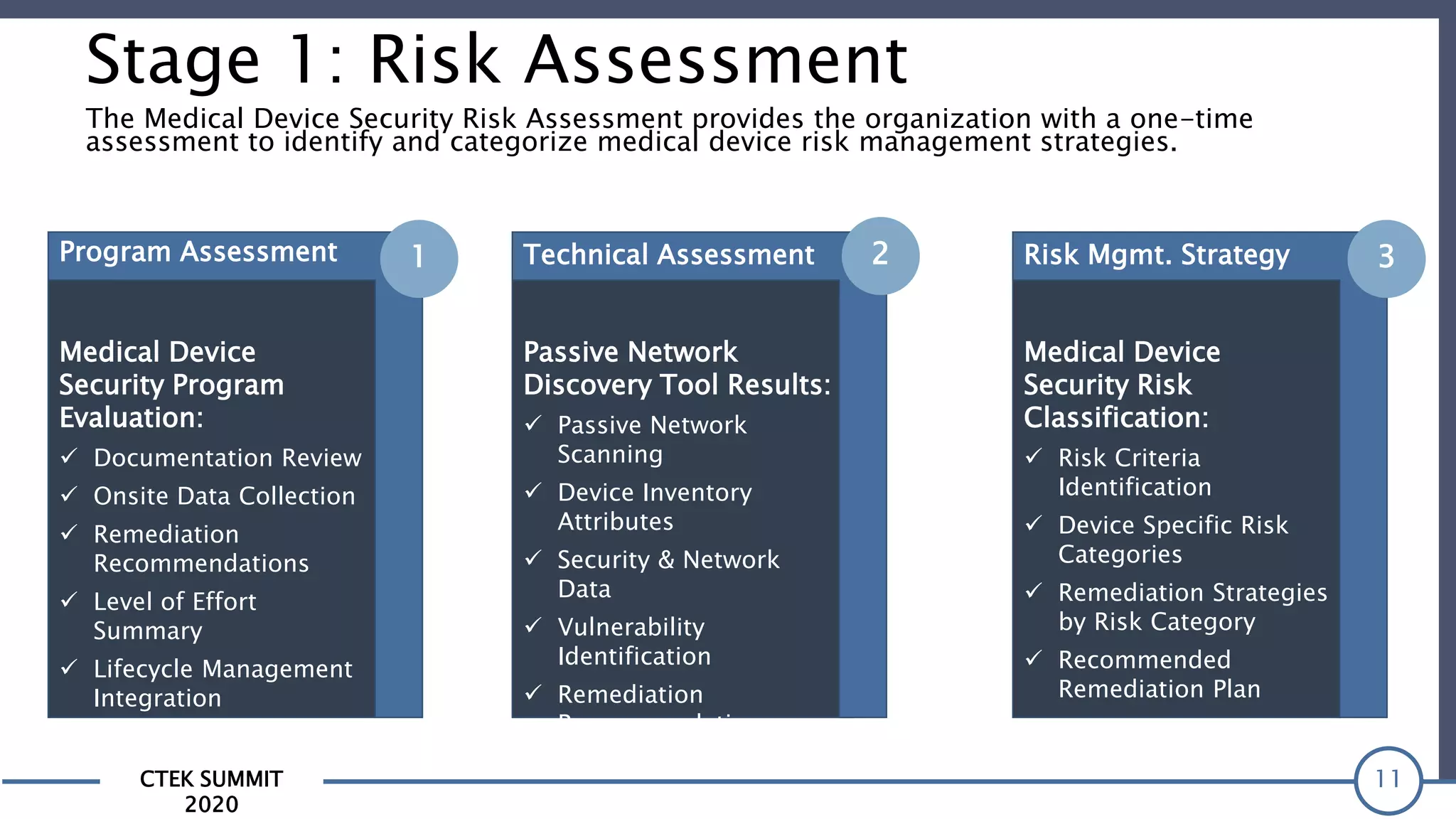
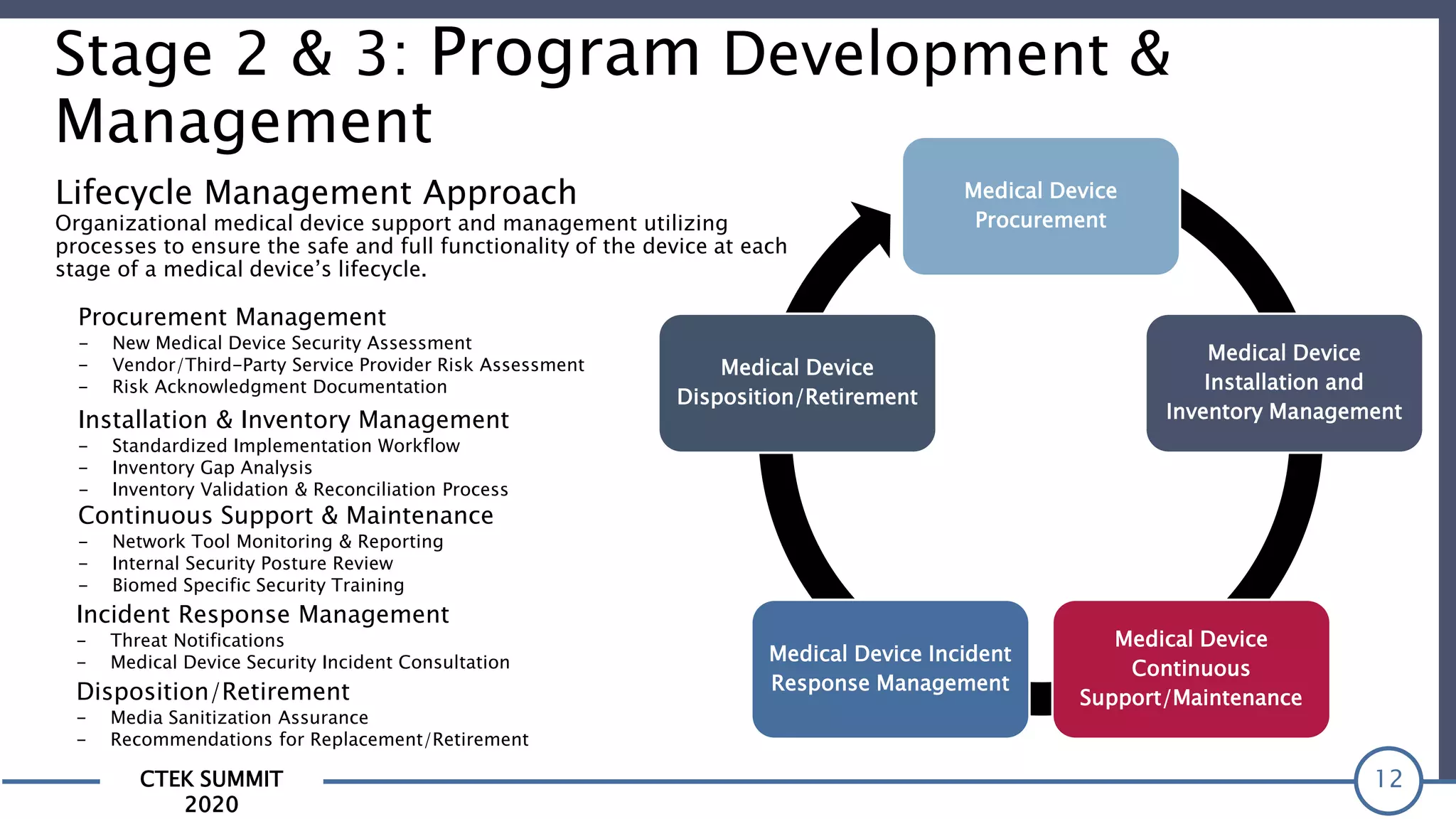
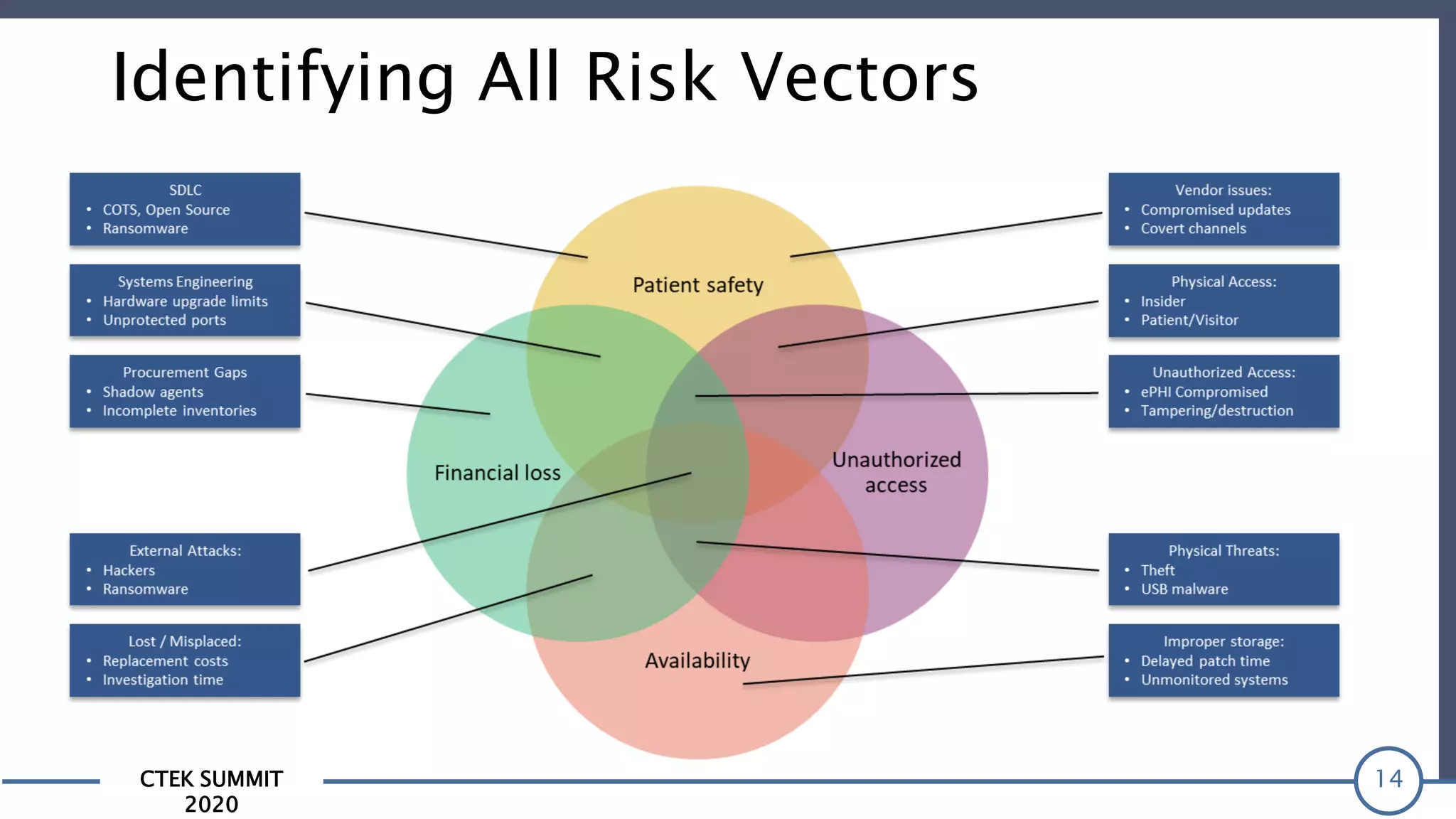
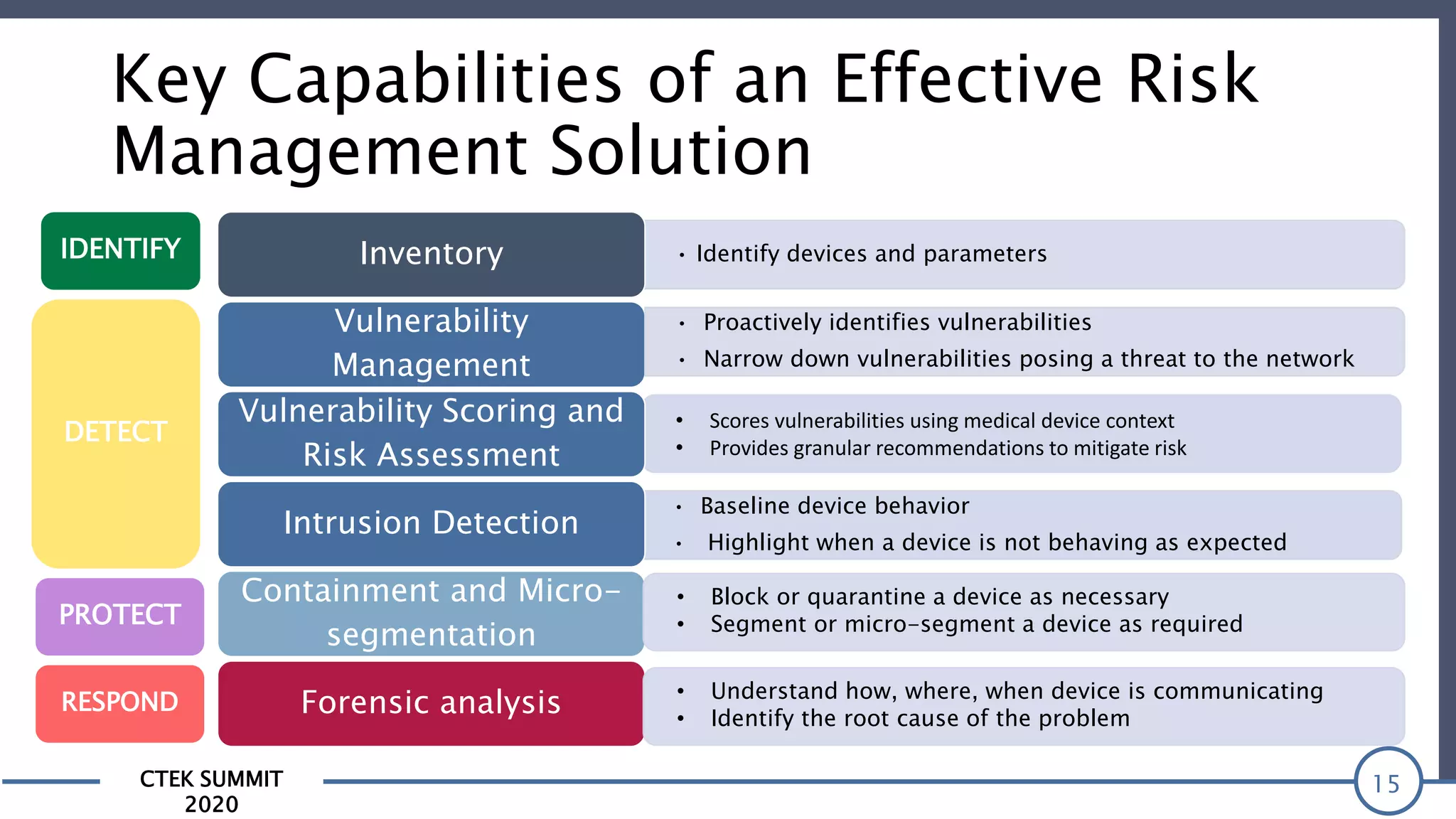
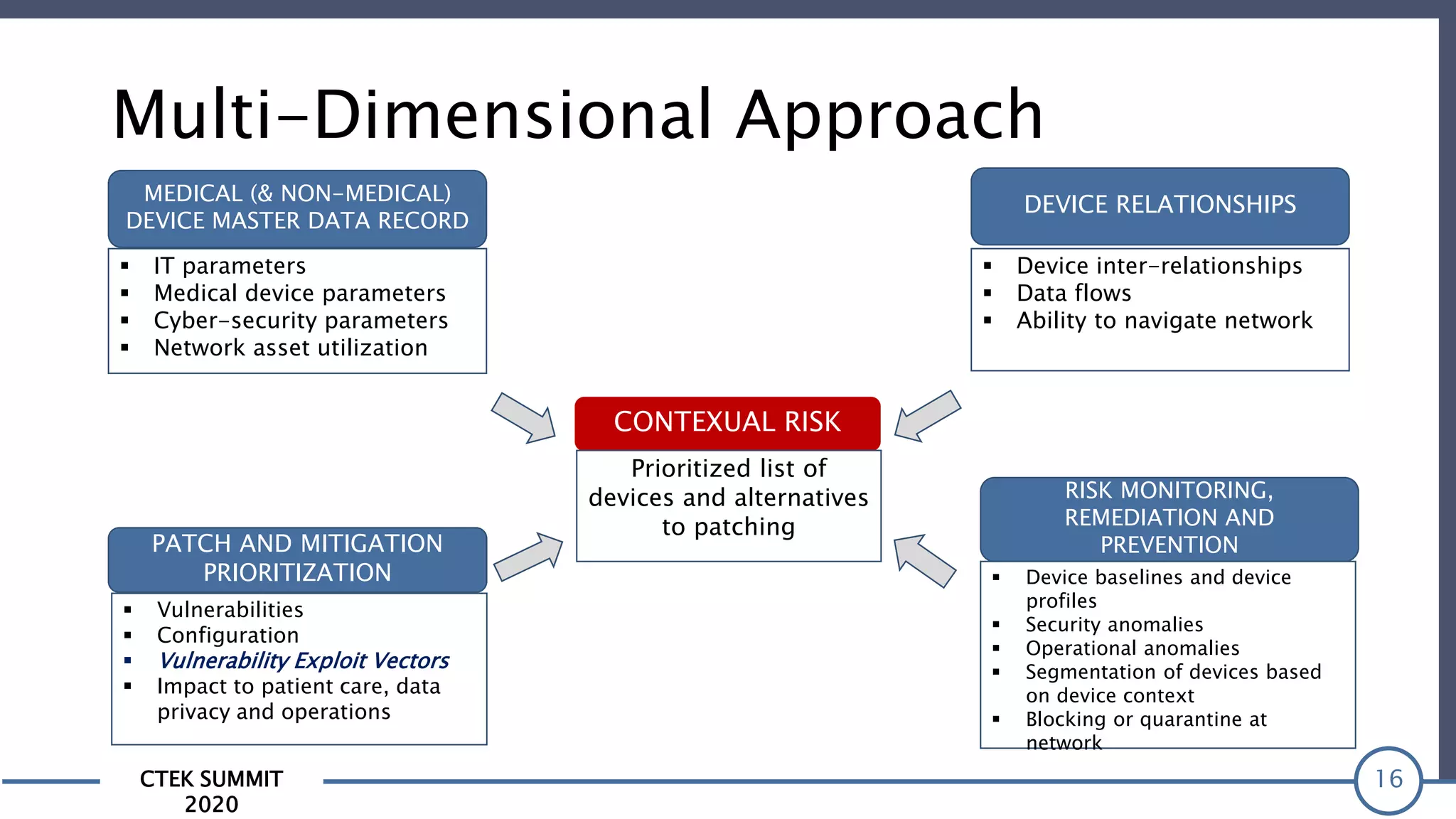
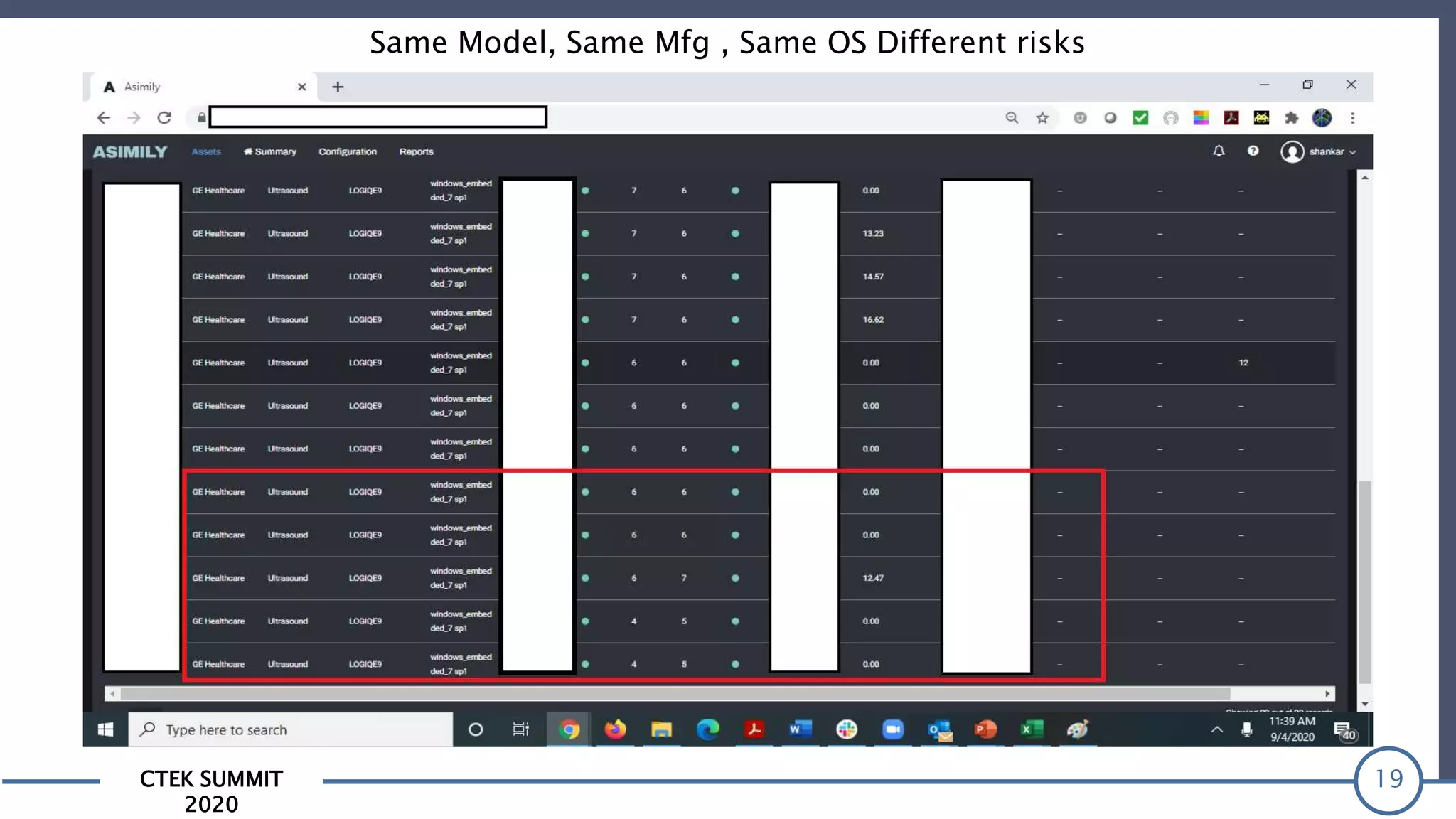
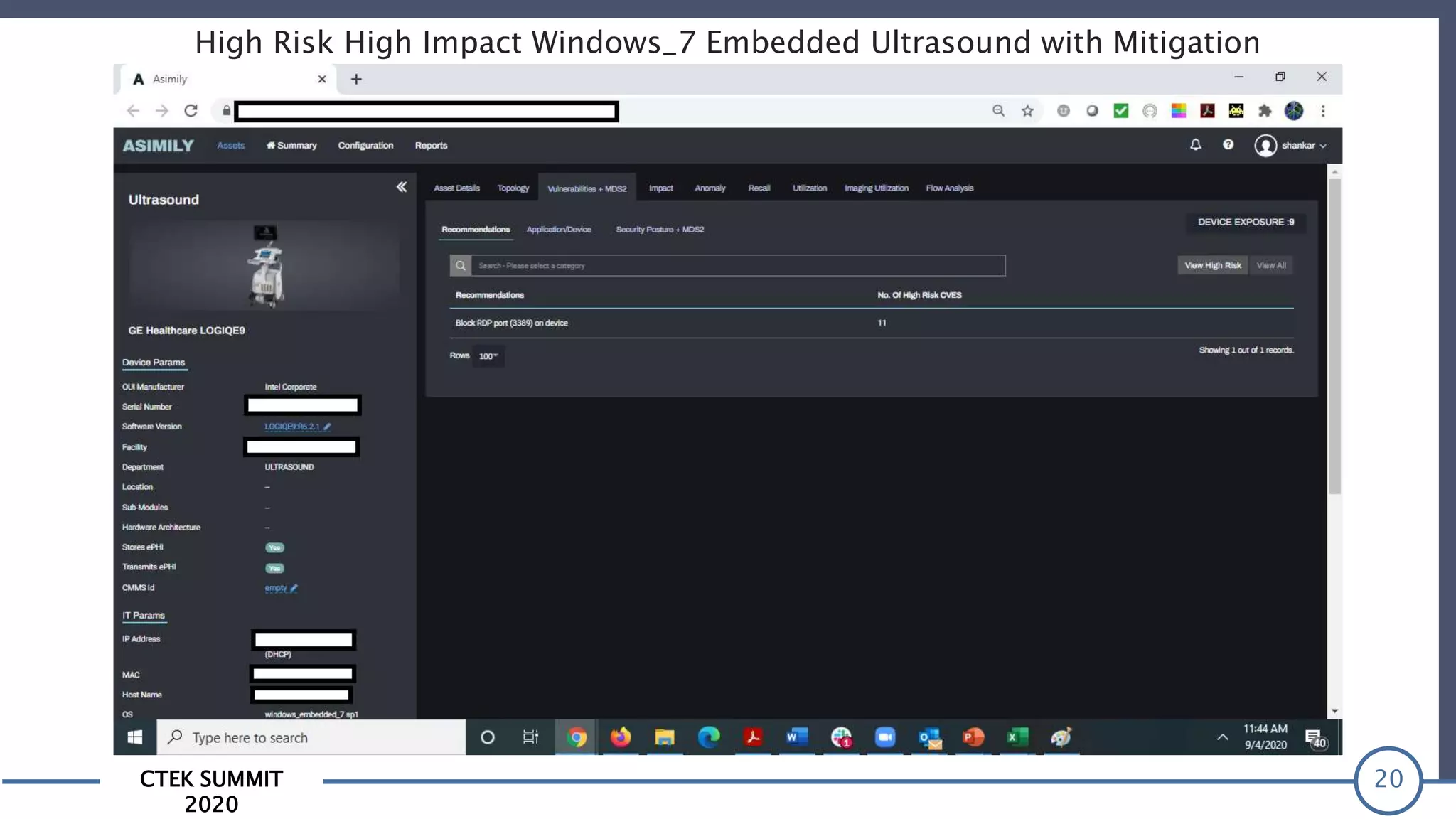
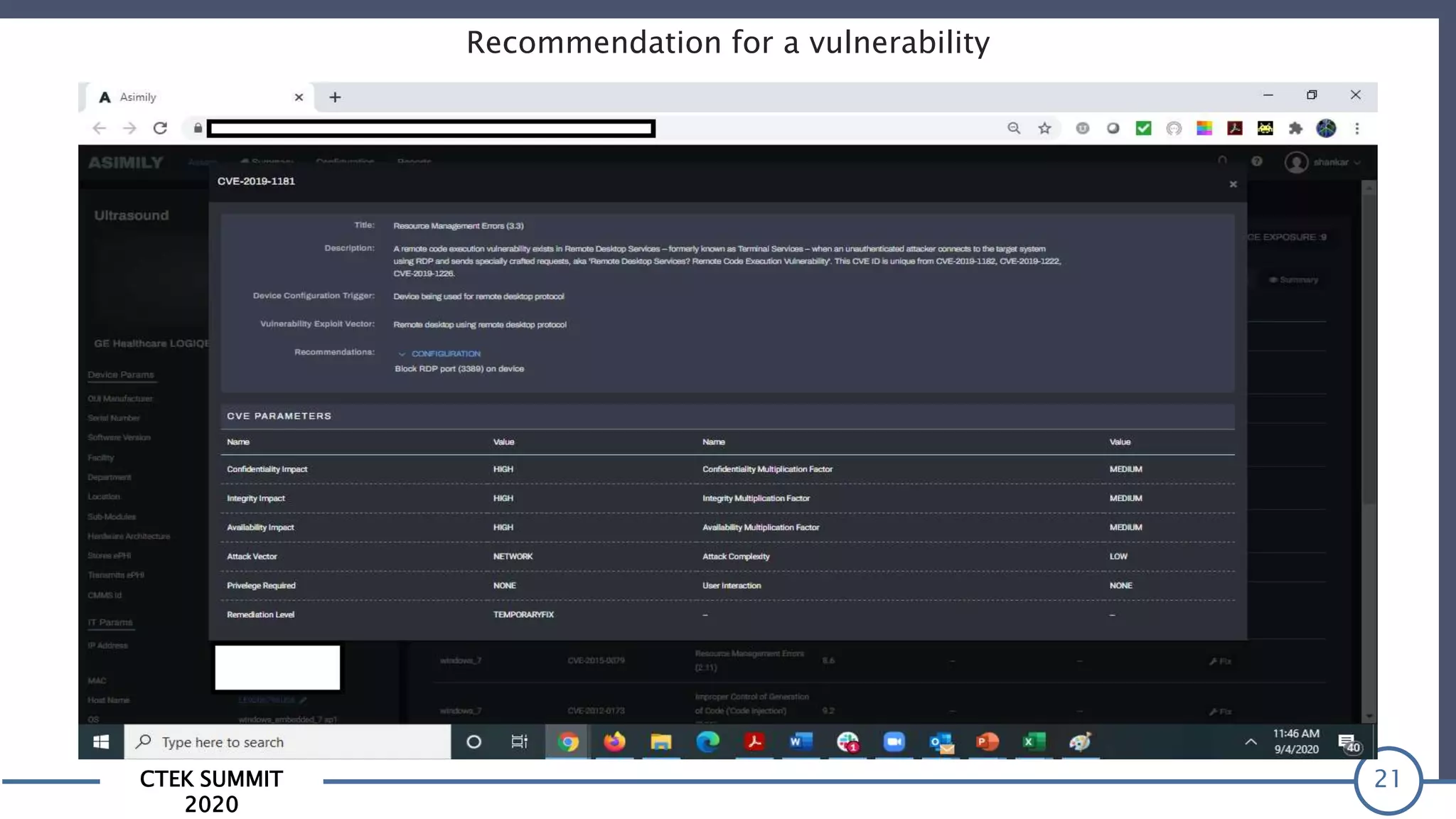
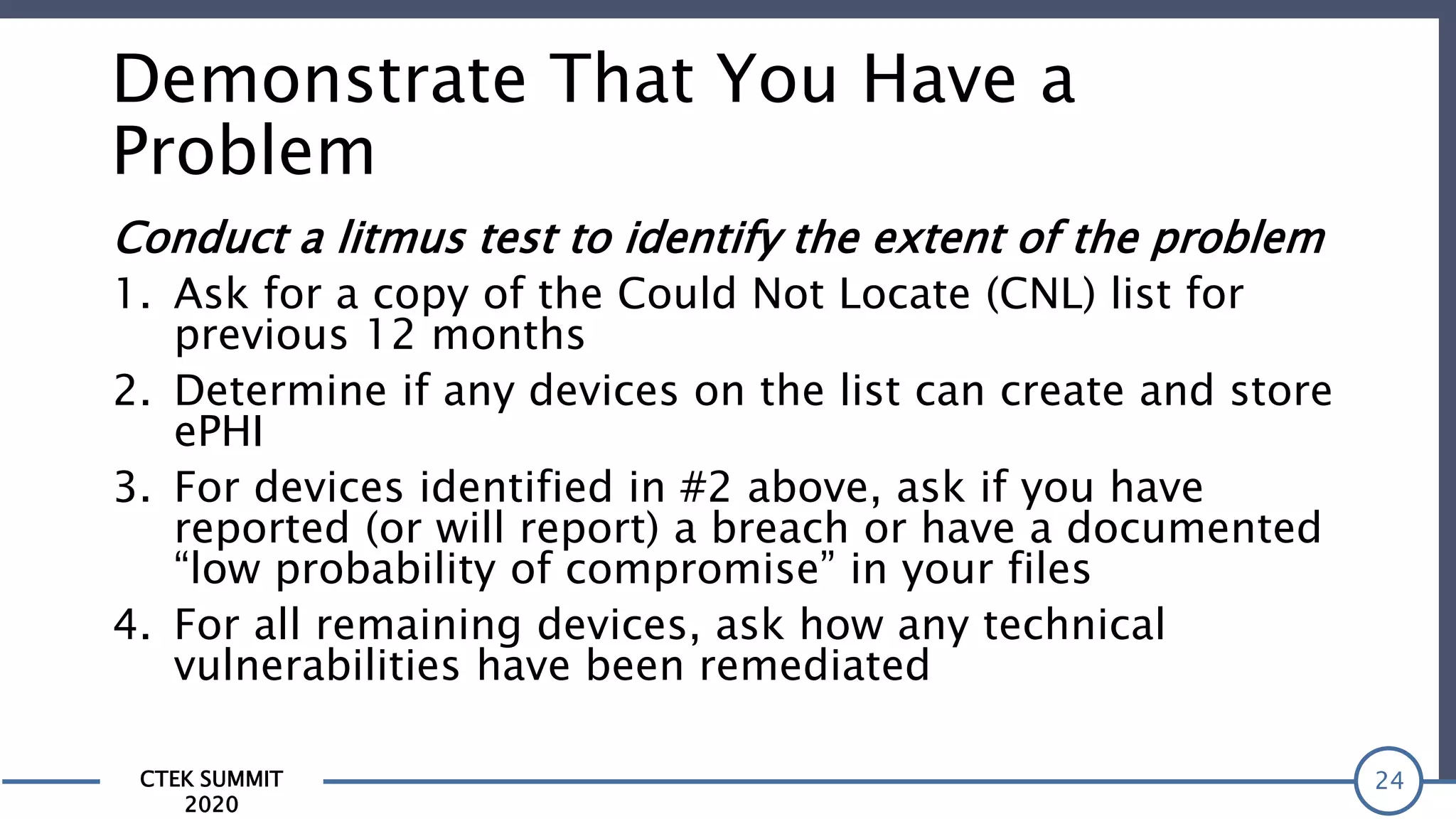
The CTEK Summit 2020 focused on medical device security services, highlighting the challenges posed by insufficient visibility and cybersecurity issues related to connected medical devices in healthcare settings. Key speakers included Priya Upendra from Banner Health, Shankar Somasundaram from Asimily, and Carrie Whysall from Cynergistek, who addressed the importance of risk assessments and program development for effective medical device security management. It emphasized the need for ongoing monitoring, proactive vulnerability management, and cross-department collaboration to mitigate risks associated with these critical healthcare devices.