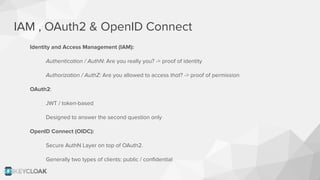
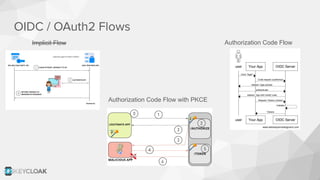
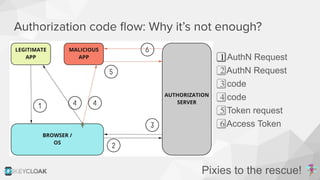
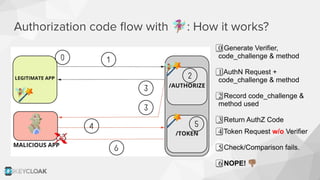
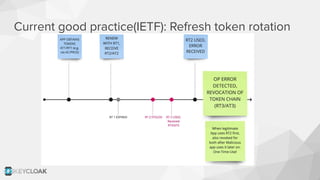
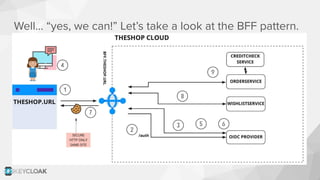
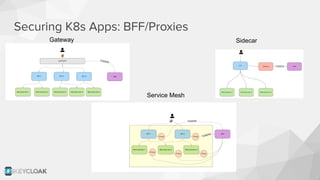
The document discusses key security concepts in cloud-native application development, particularly focusing on identity and access management (IAM) related to OAuth2 and OpenID Connect. It highlights best practices such as using PKCE to enhance security, and introduces the Backend for Frontend (BFF) pattern to mitigate risks associated with token exposure in browsers. The authors emphasize that while improvements can be made, security remains an architectural trade-off with no perfect solution.