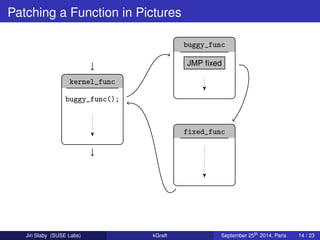
Kgraft is a live patching technology developed by SUSE Labs for the Linux kernel that enables quick response to security issues without requiring a system reboot. It allows for fixing critical bugs and simple changes while maintaining a stable build environment, though it has limitations regarding complex changes and third-party support. The technology leverages existing Linux infrastructure and aims to provide a standard for live kernel patching in collaboration with other development groups.