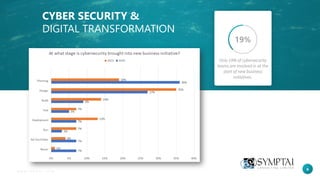
The document discusses the critical relationship between cyber security and digital transformation, highlighting that businesses must consider security from the start of transformation initiatives to avoid significant risks. It outlines the rising costs of data breaches, challenges faced by cyber security teams, and emerging threats associated with rapid technological changes. Recommendations include aligning security strategies with business goals, adopting secure-by-design principles, and fostering a secure culture within organizations.