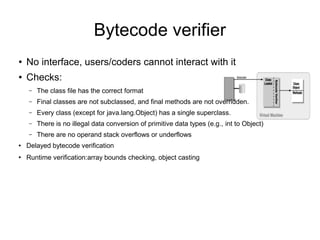
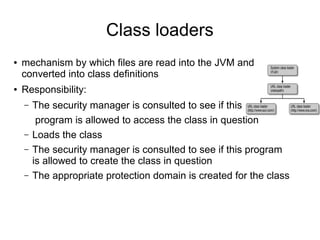
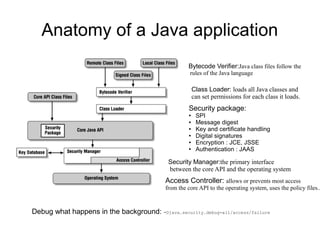
This document discusses Java security. It covers Java's original goals of being robust and secure. It describes the Java sandbox implementation and how it protects memory, files, and network access. It discusses various aspects of the Java security model including the bytecode verifier, class loaders, security manager, access controller, JAAS, JCE, and JSSE.






![What is this:
jre/lib/[arch]/client/clases.jsa](https://image.slidesharecdn.com/java-security-130410025601-phpapp02/85/Tollas-Ferenc-Java-security-9-320.jpg)