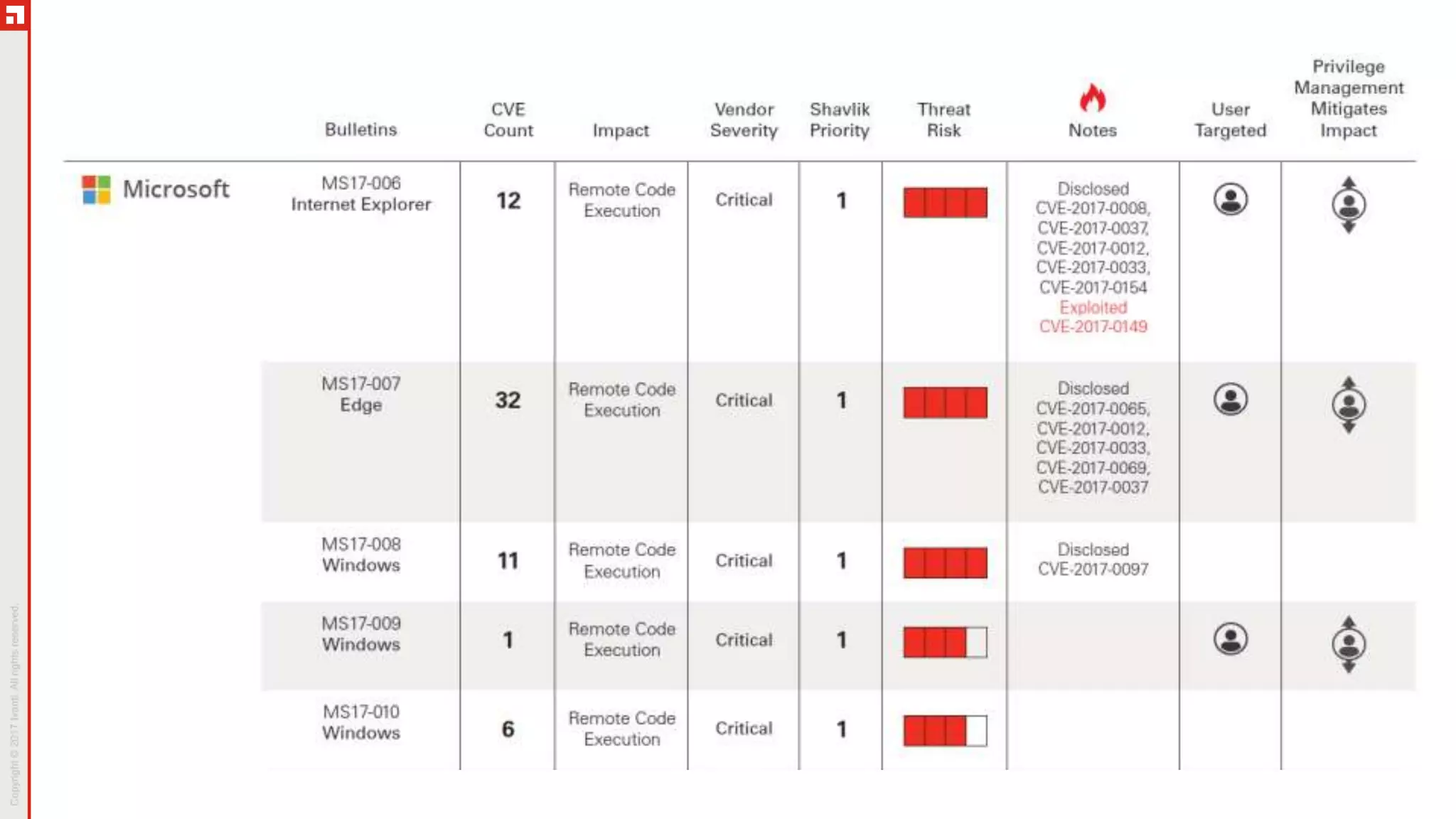
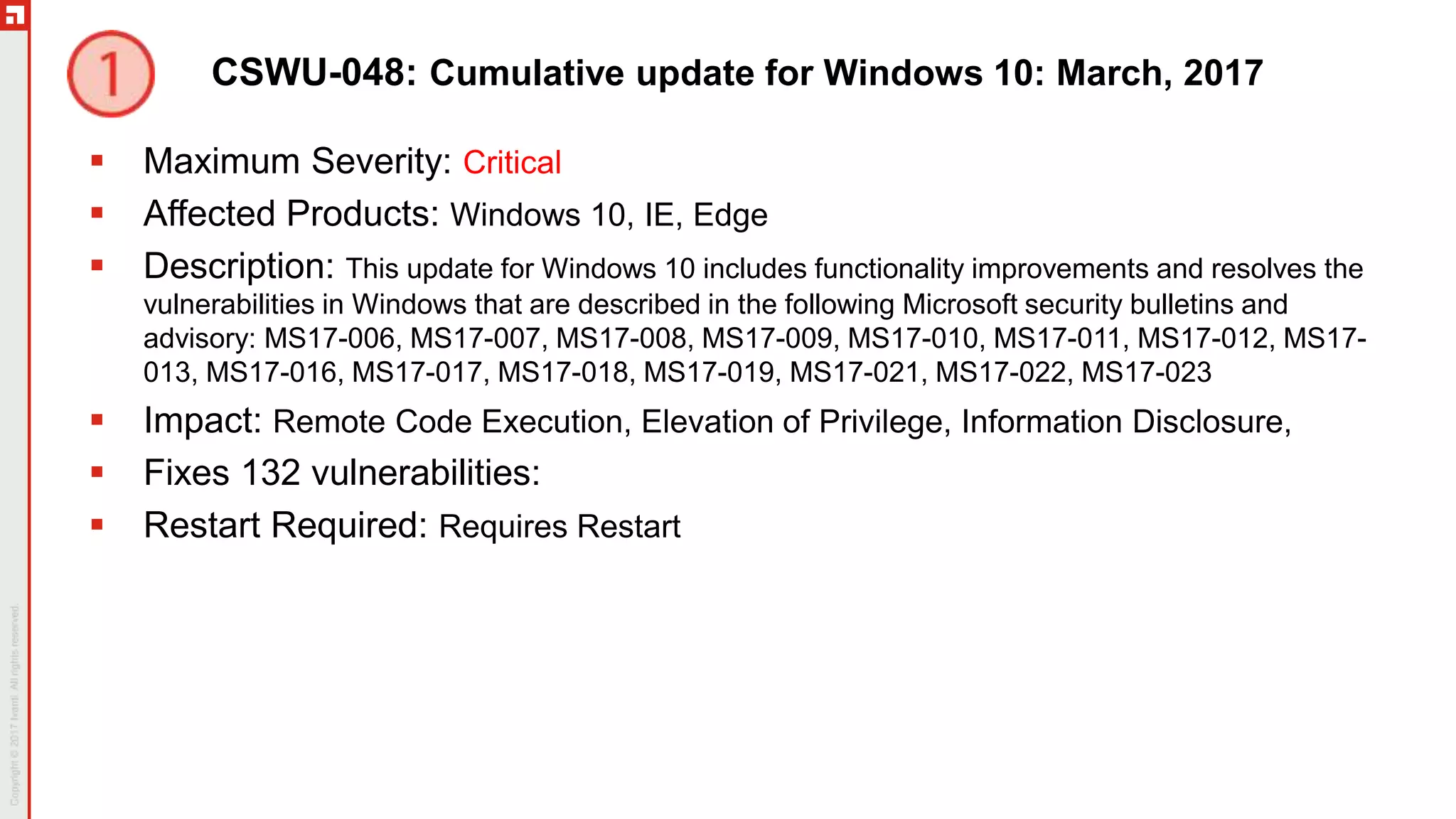
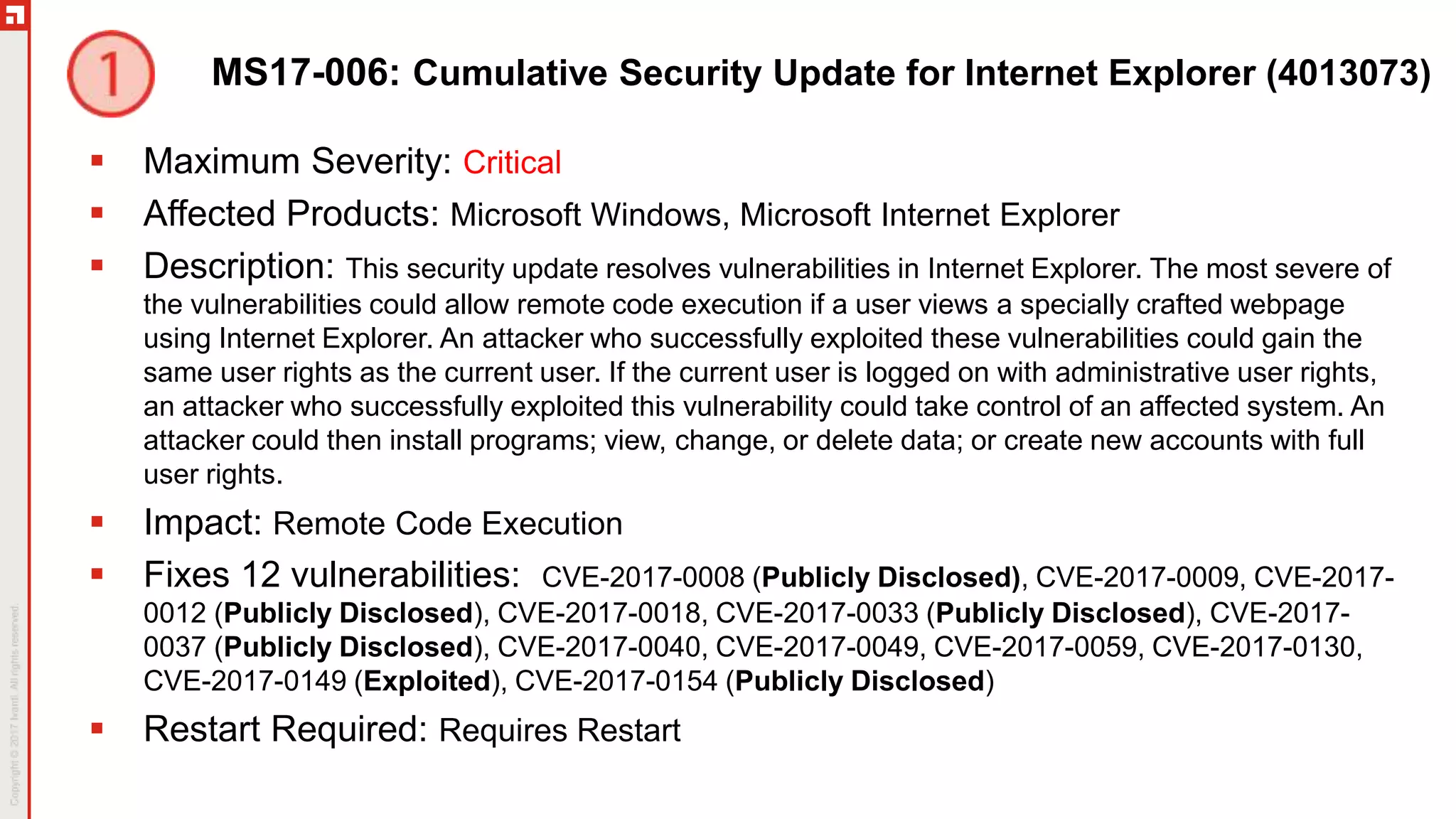
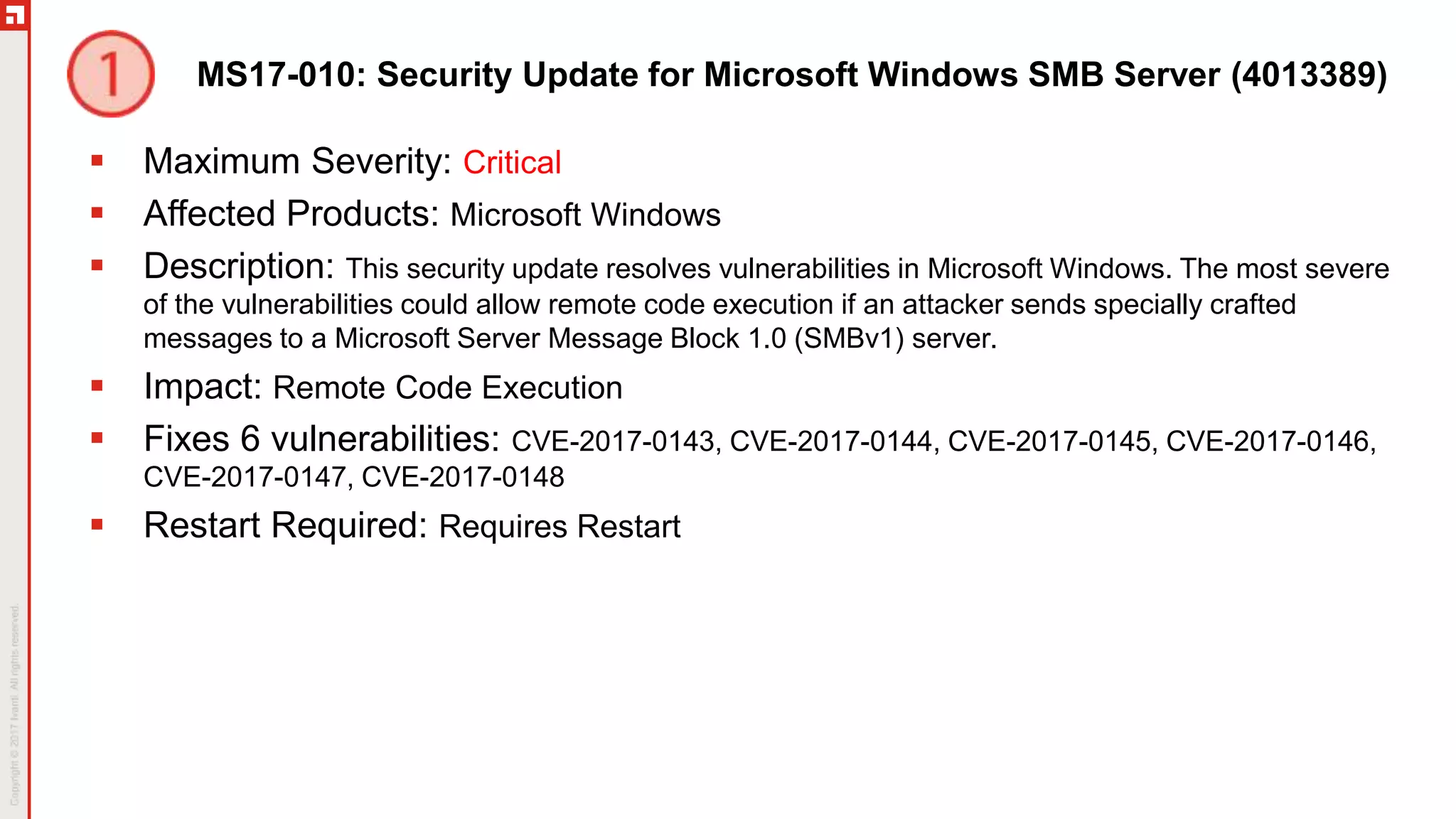
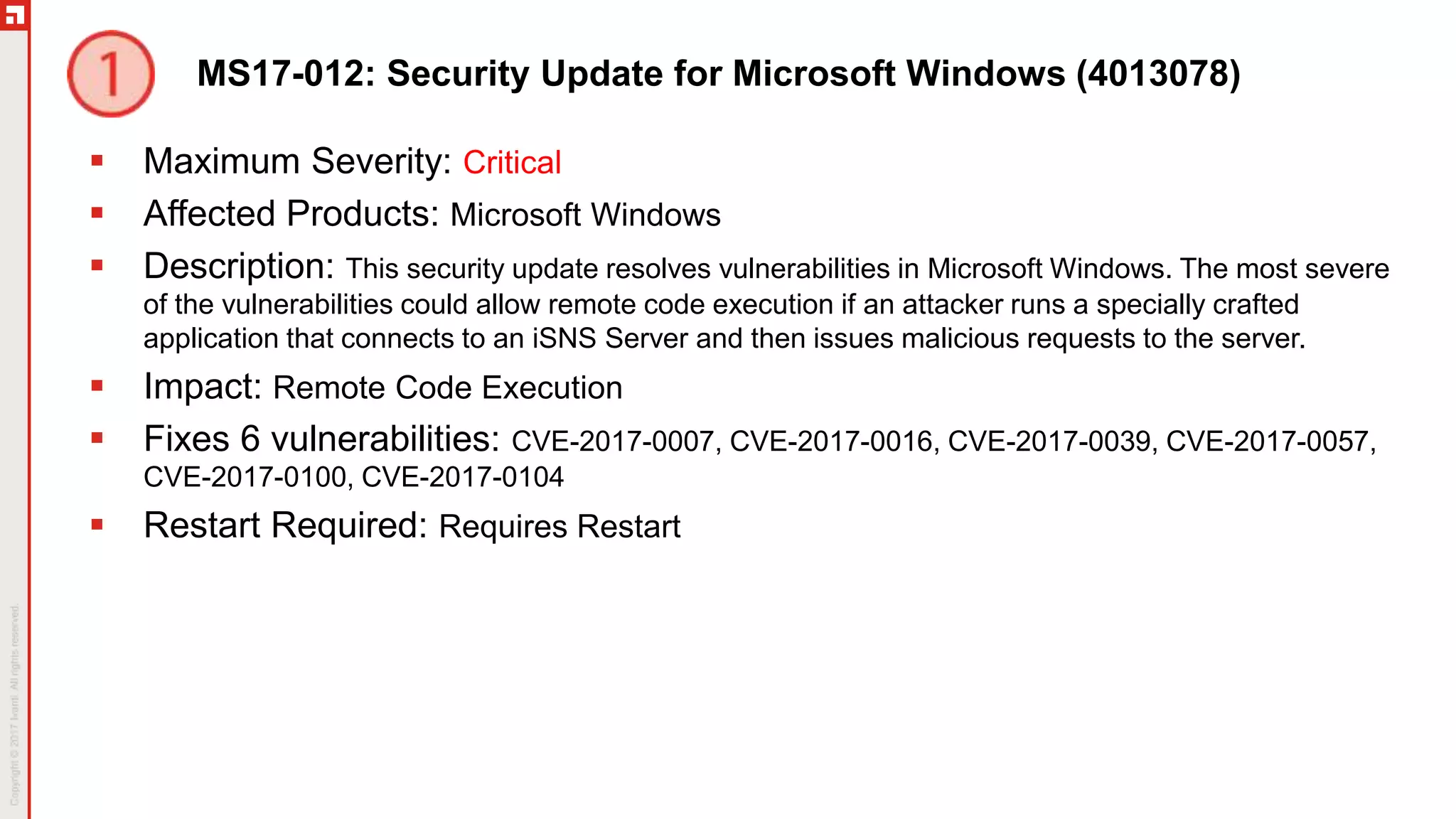
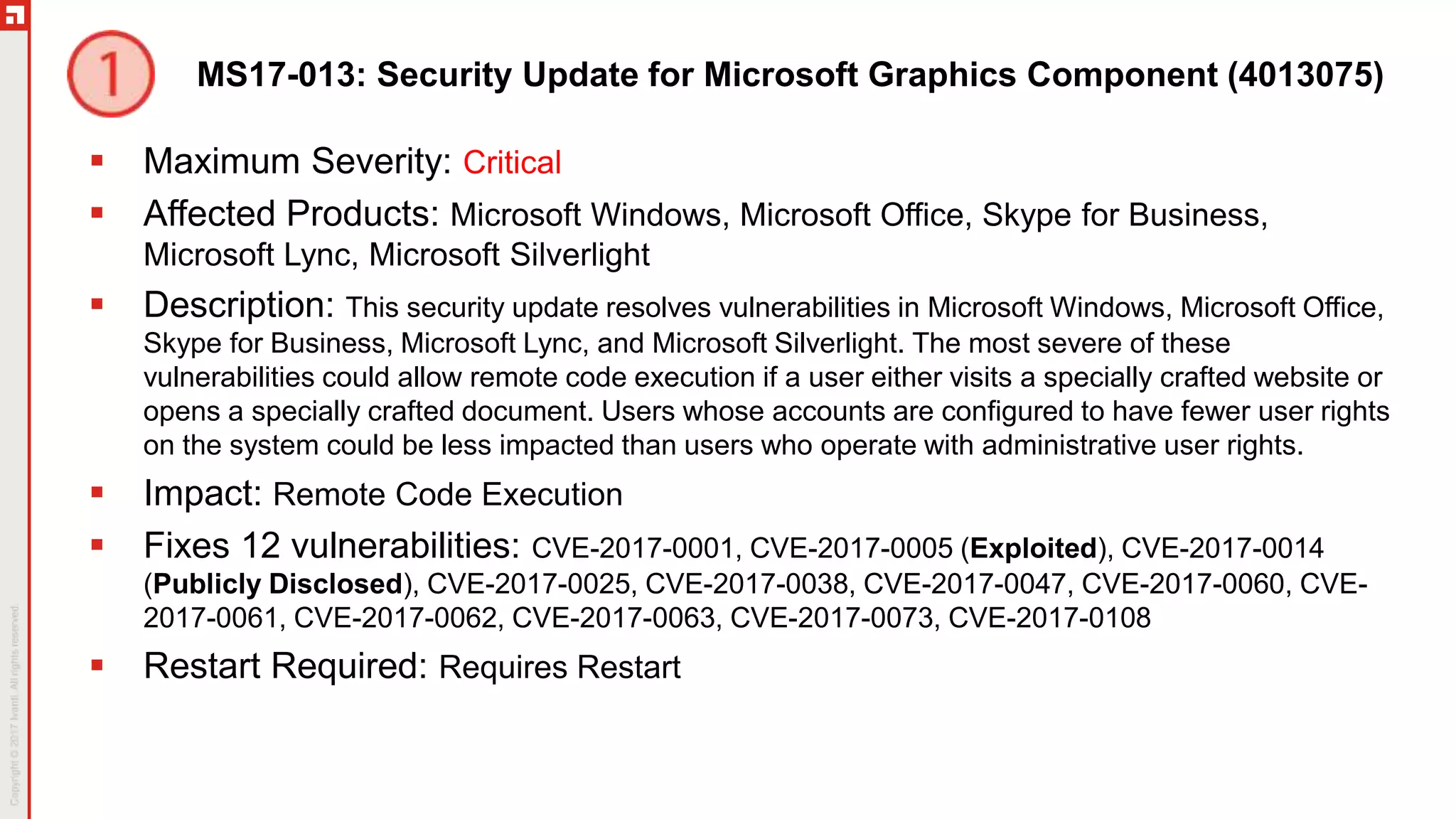
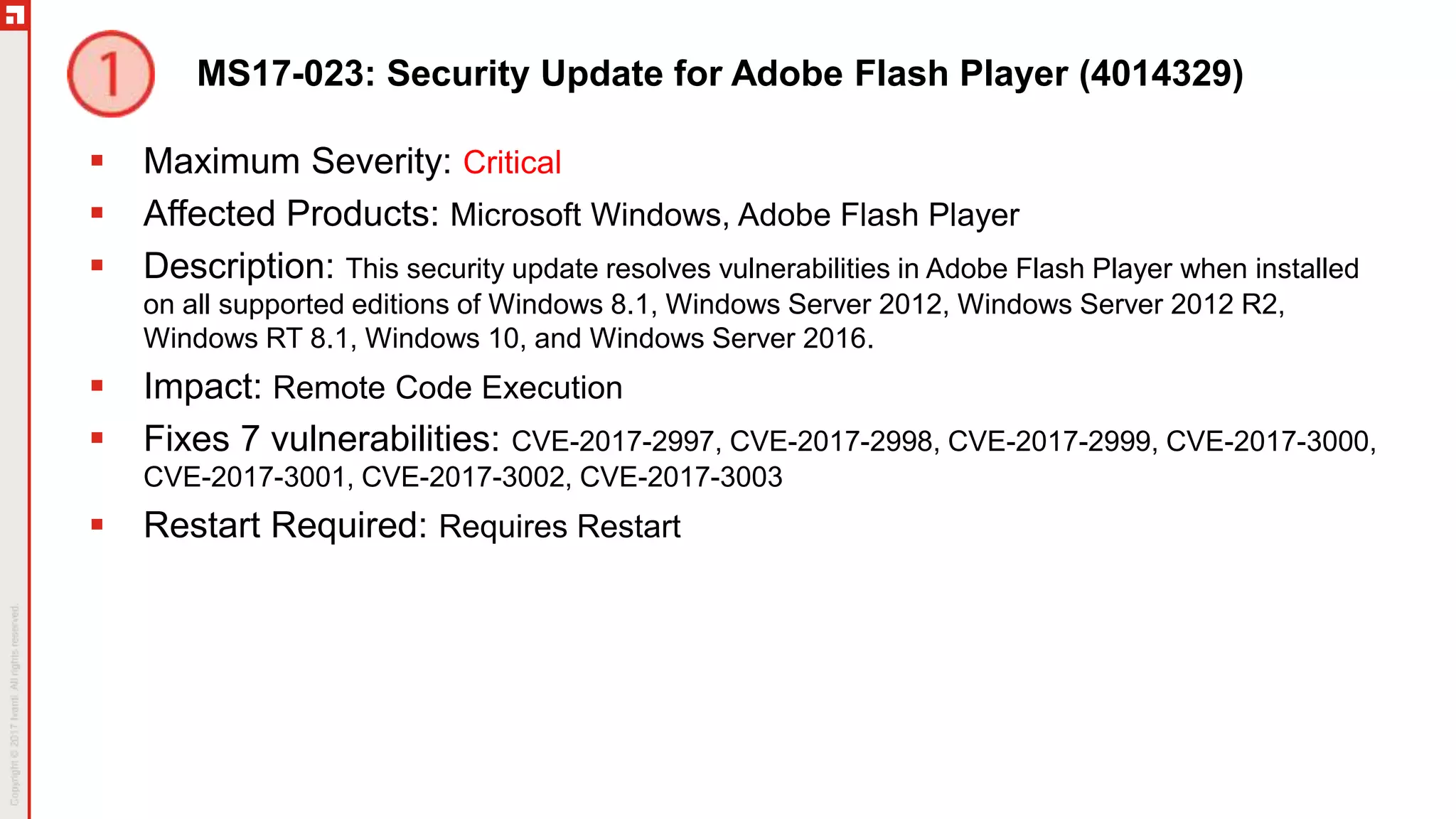
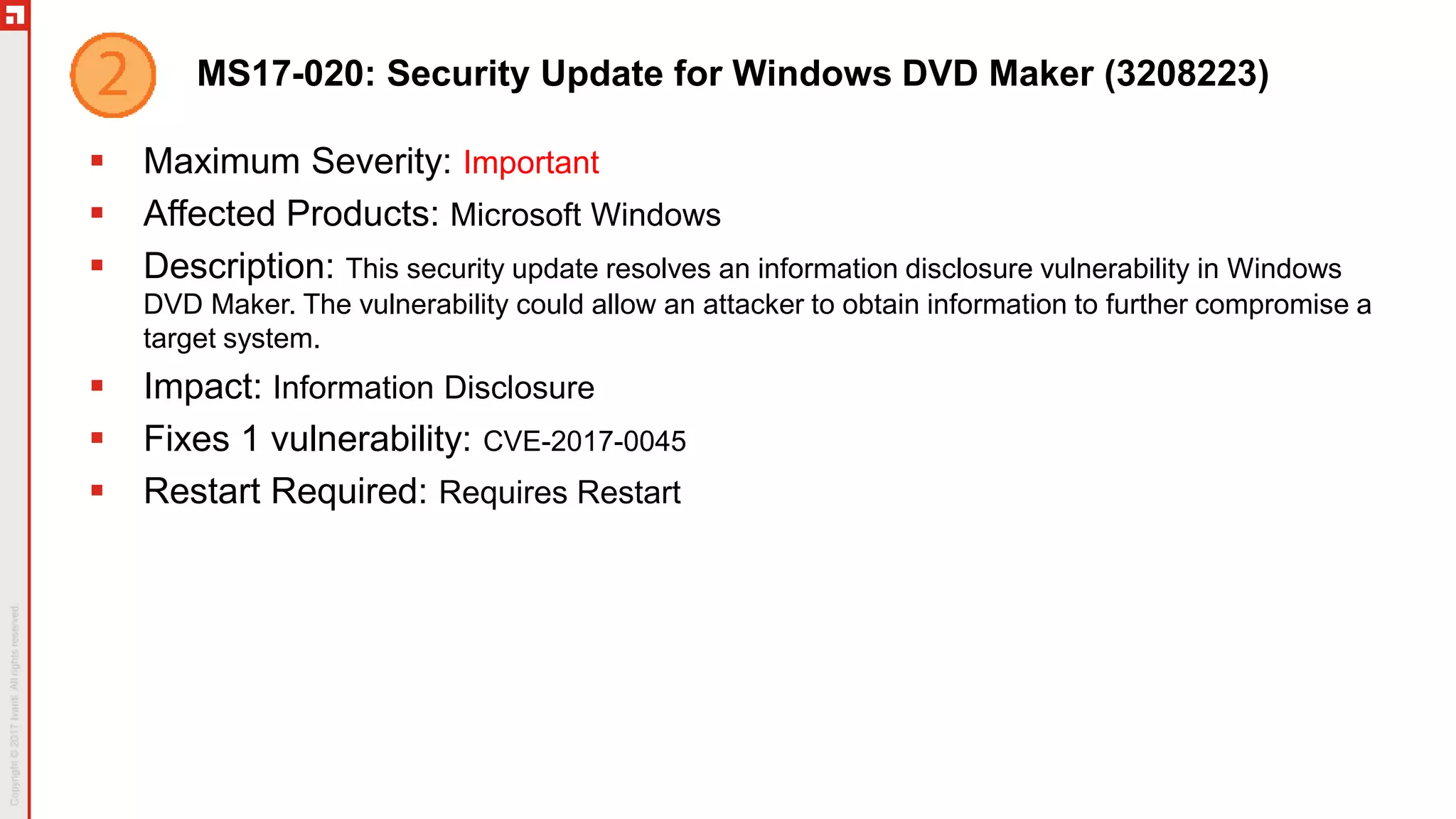
This document summarizes the March 2017 Patch Tuesday updates from Microsoft and other vendors. It describes several security bulletins affecting Windows, Internet Explorer, Edge, Hyper-V, and other Microsoft products that fix over 130 vulnerabilities including remote code execution issues. Updates are also provided for Adobe Flash Player, VMware Workstation, and Exchange Server addressing critical remote code execution vulnerabilities.