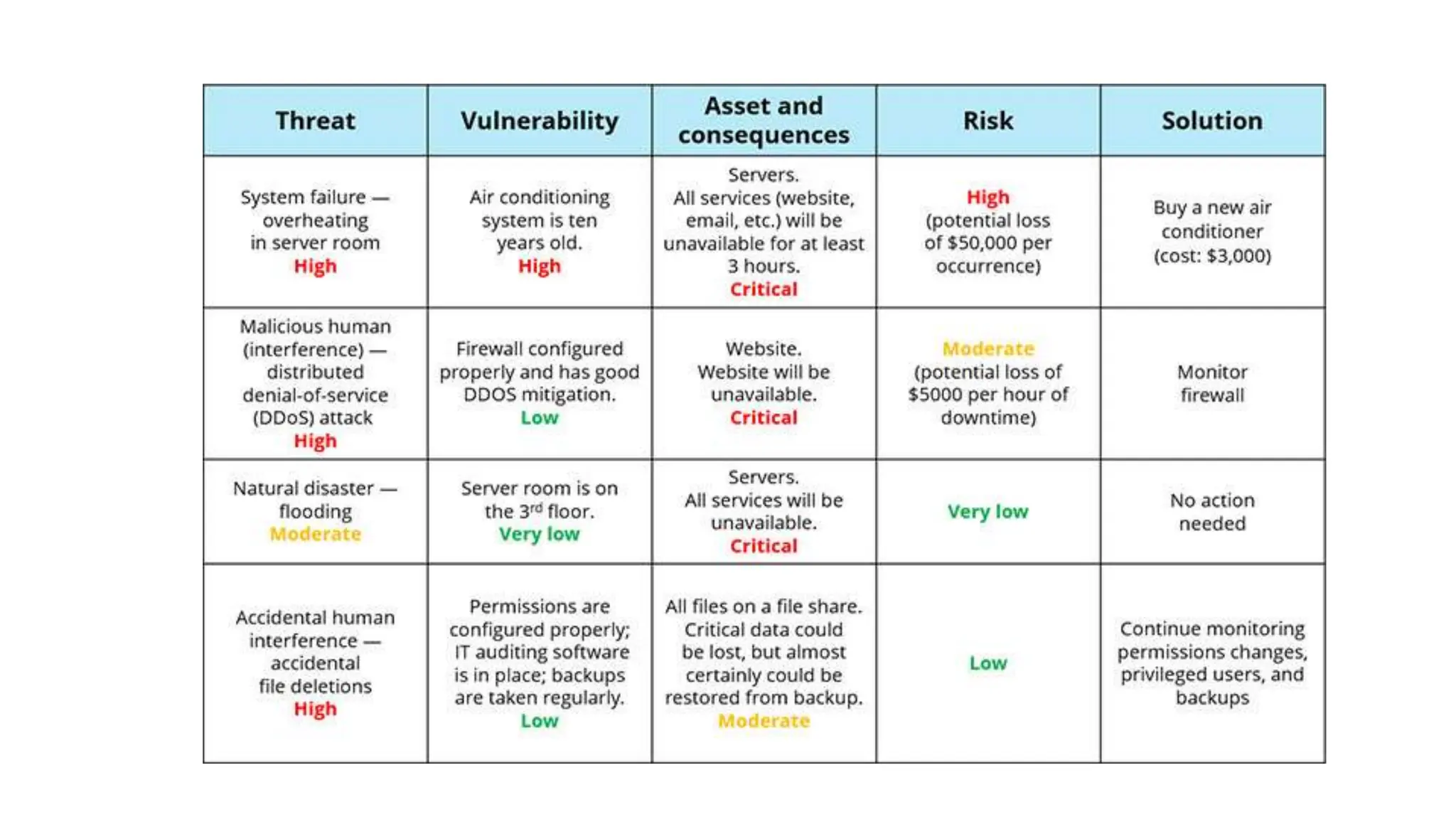
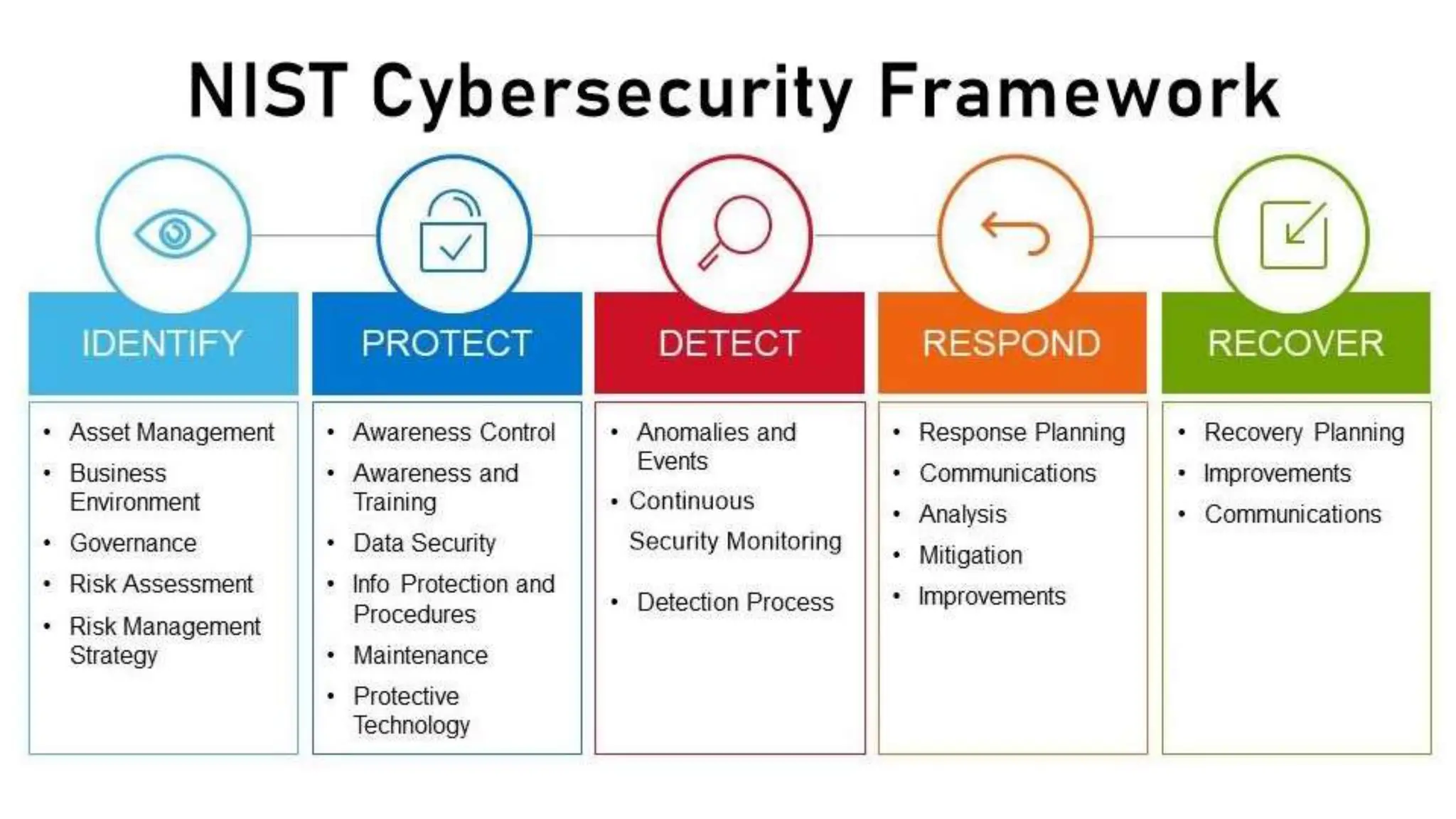
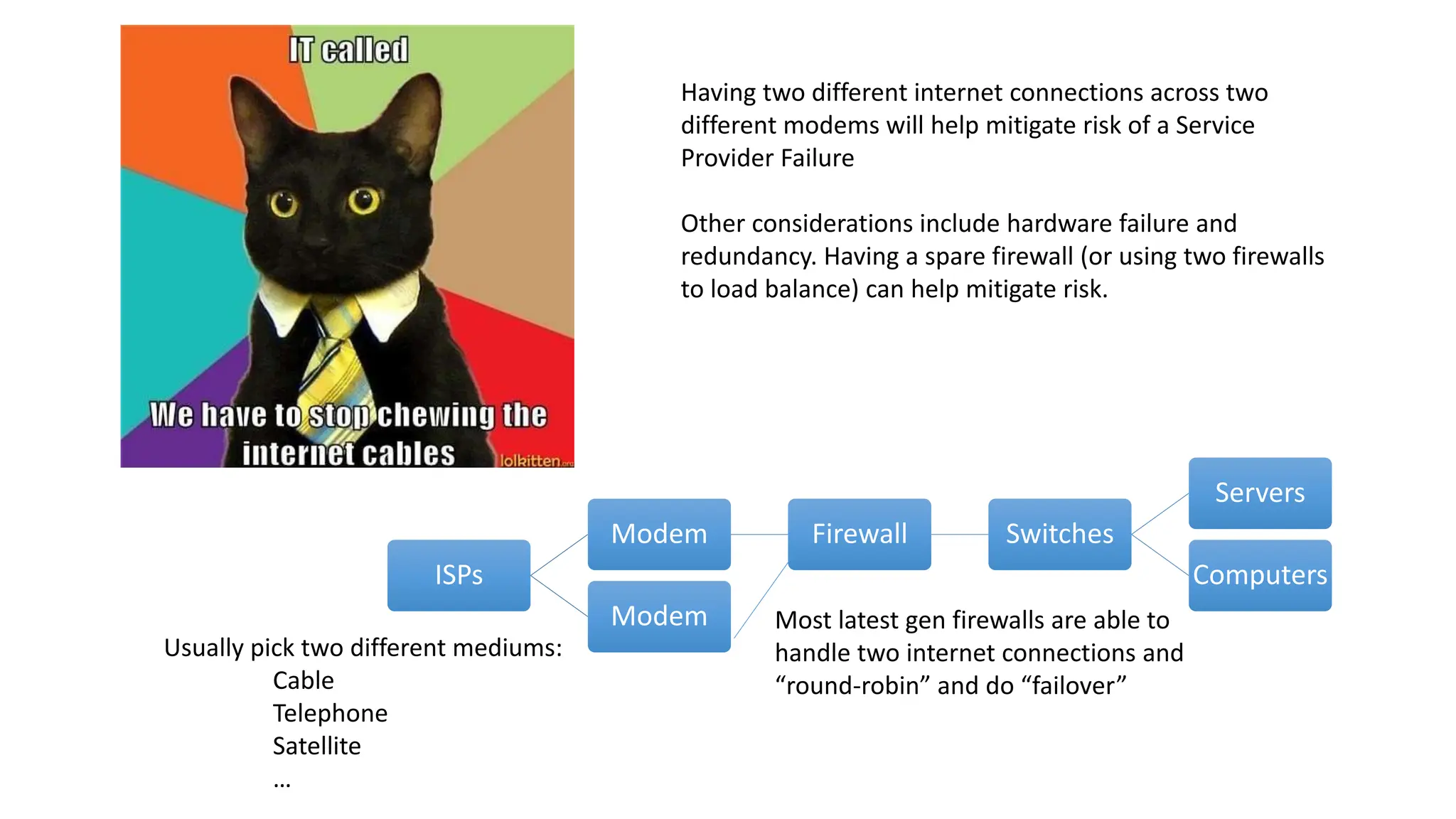
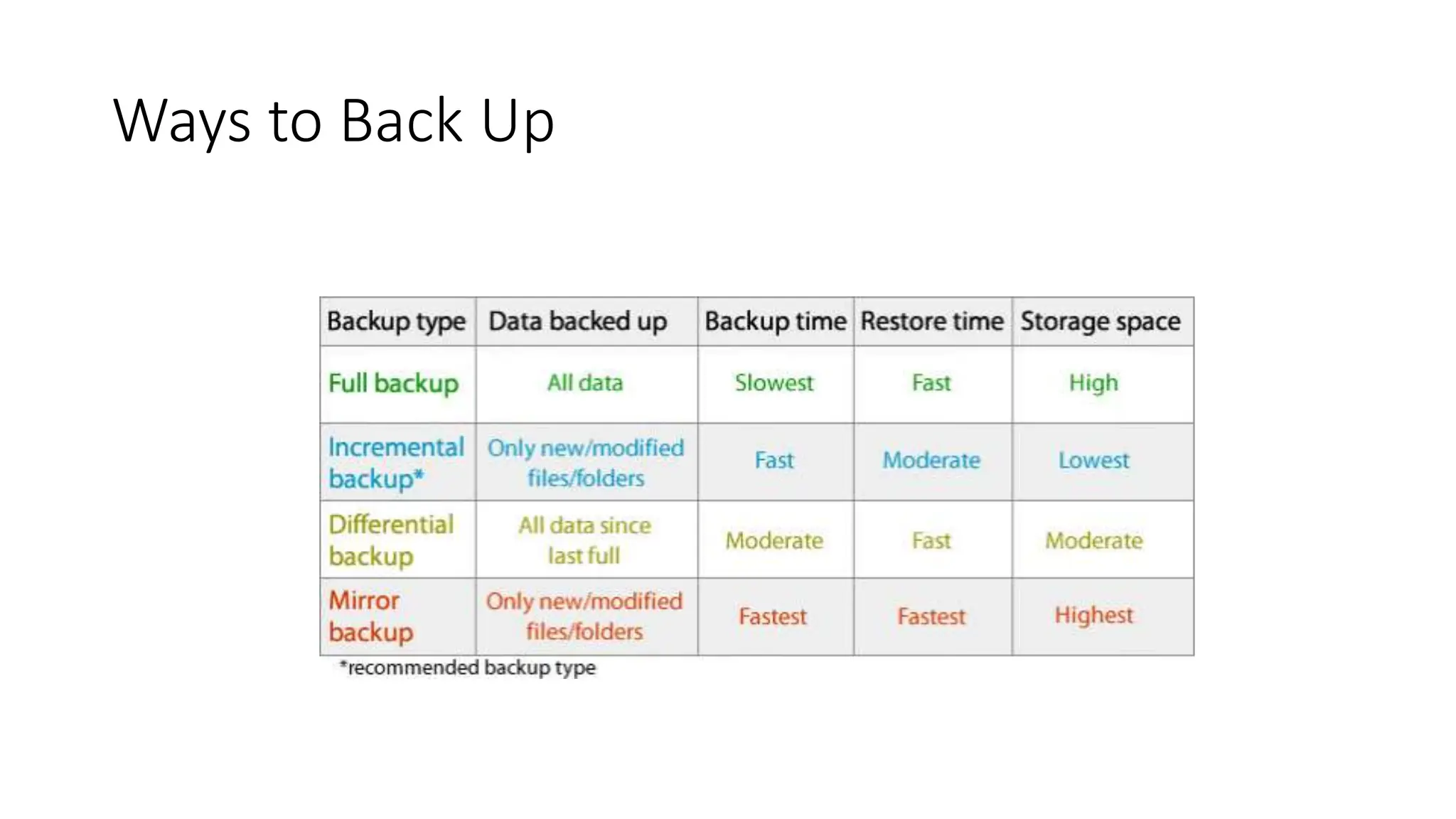
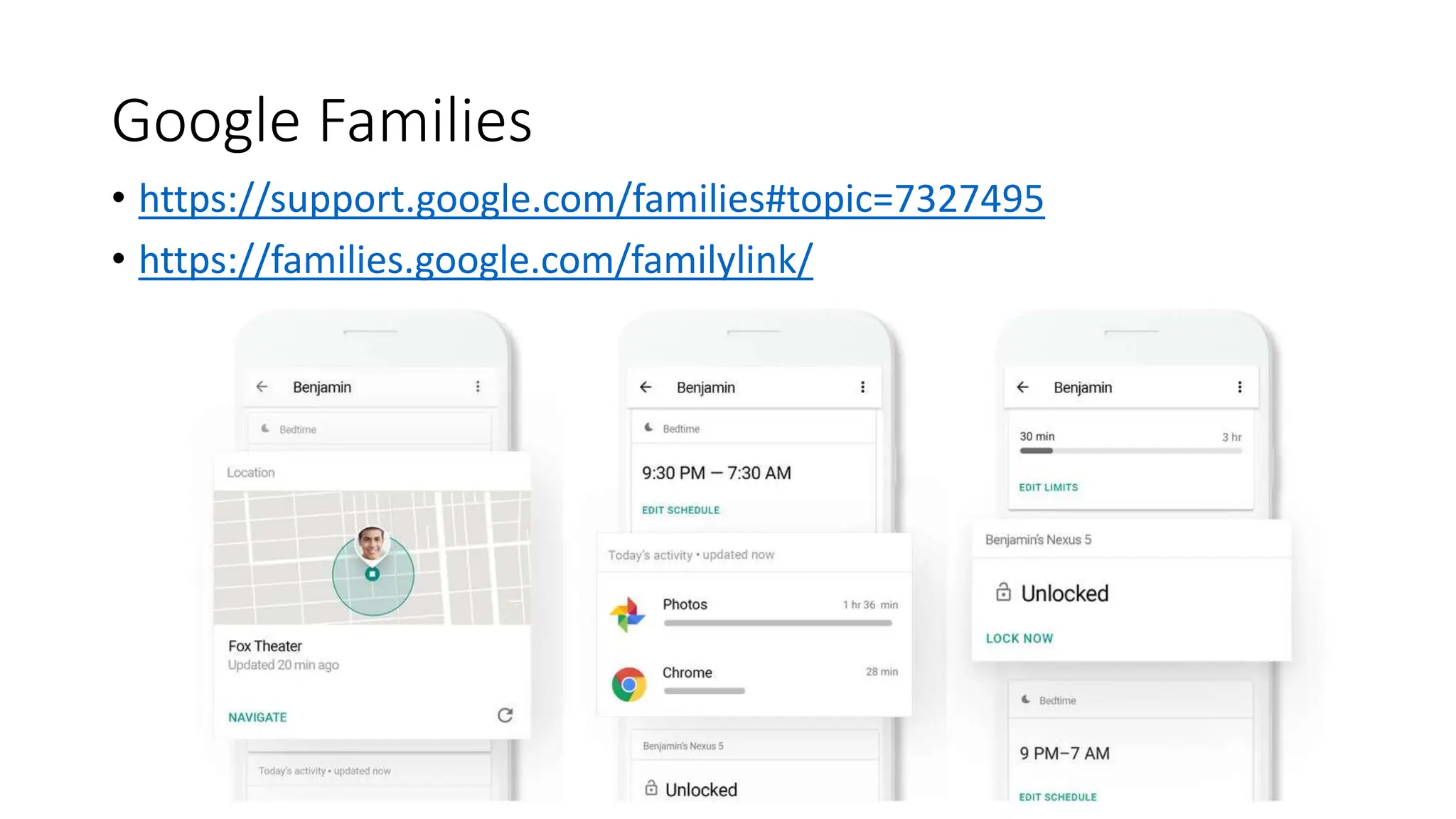
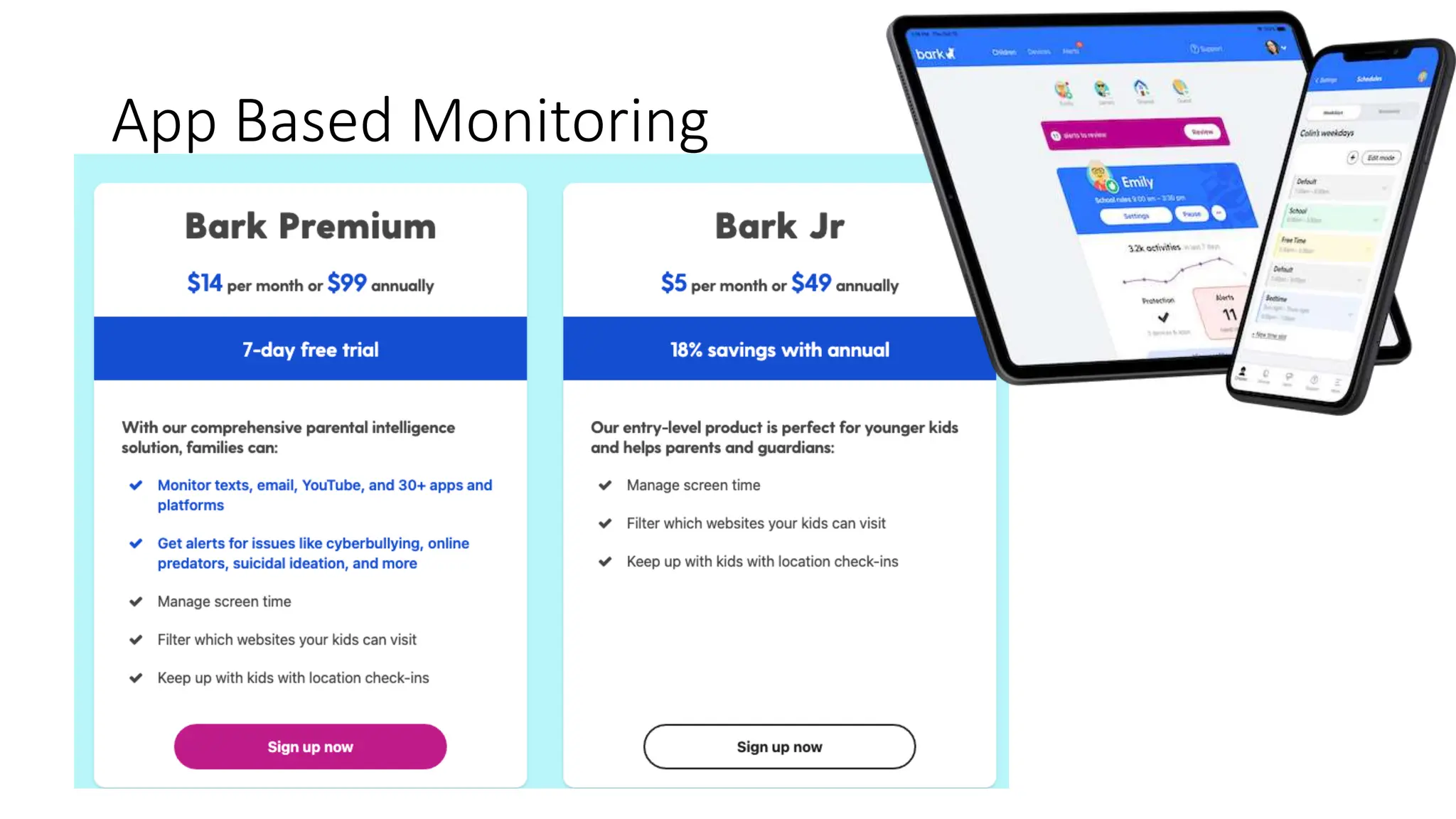
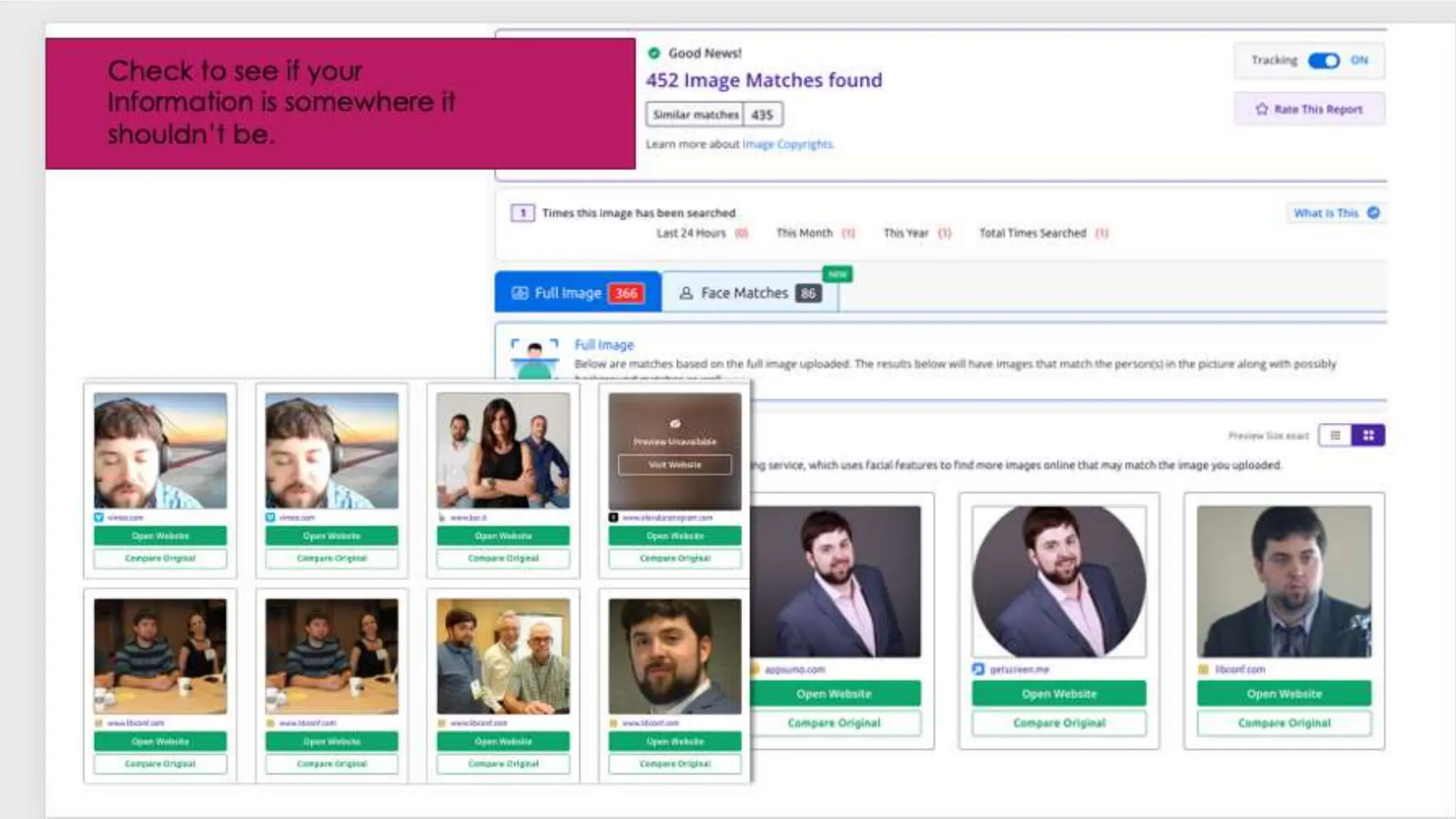
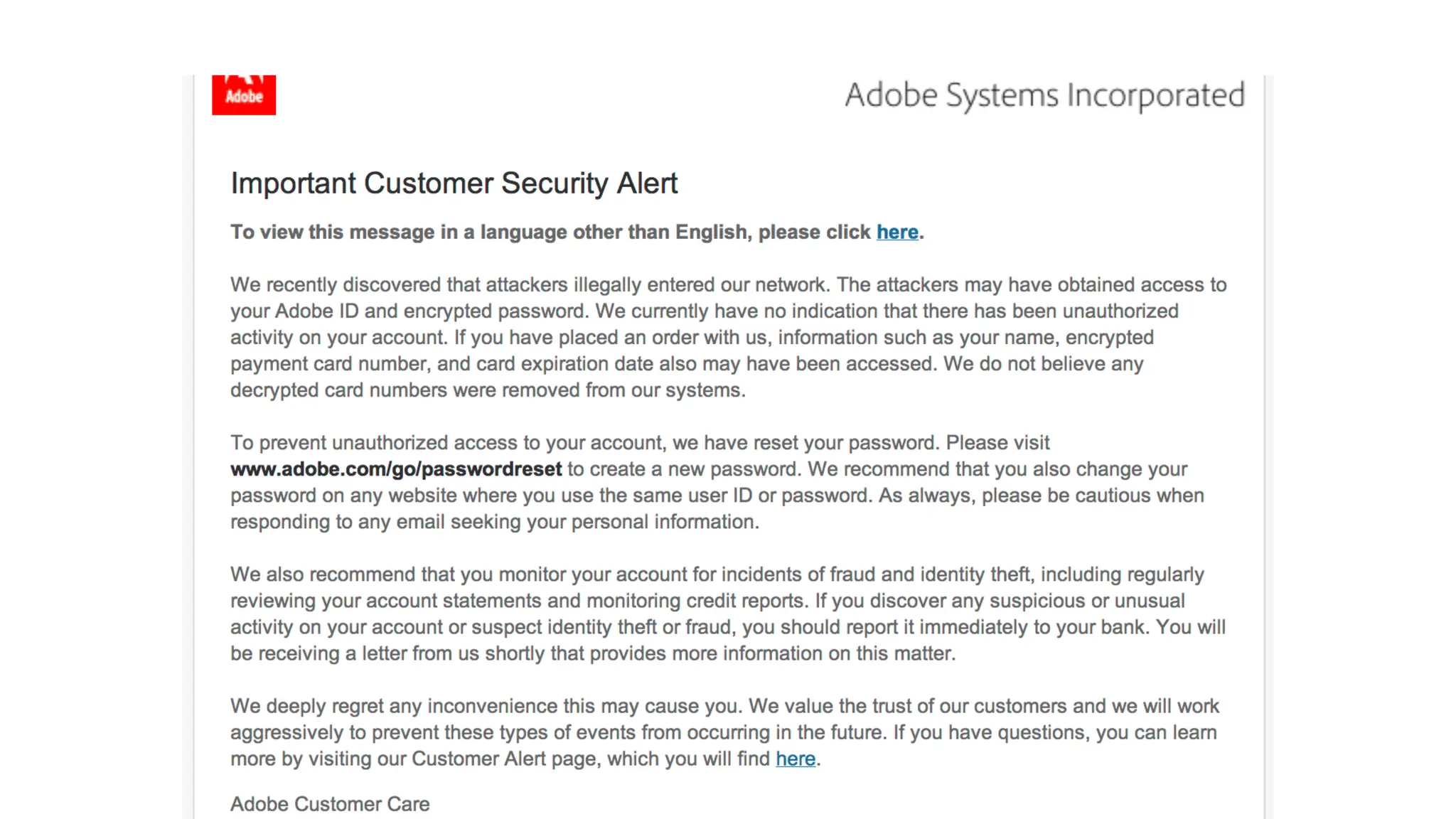
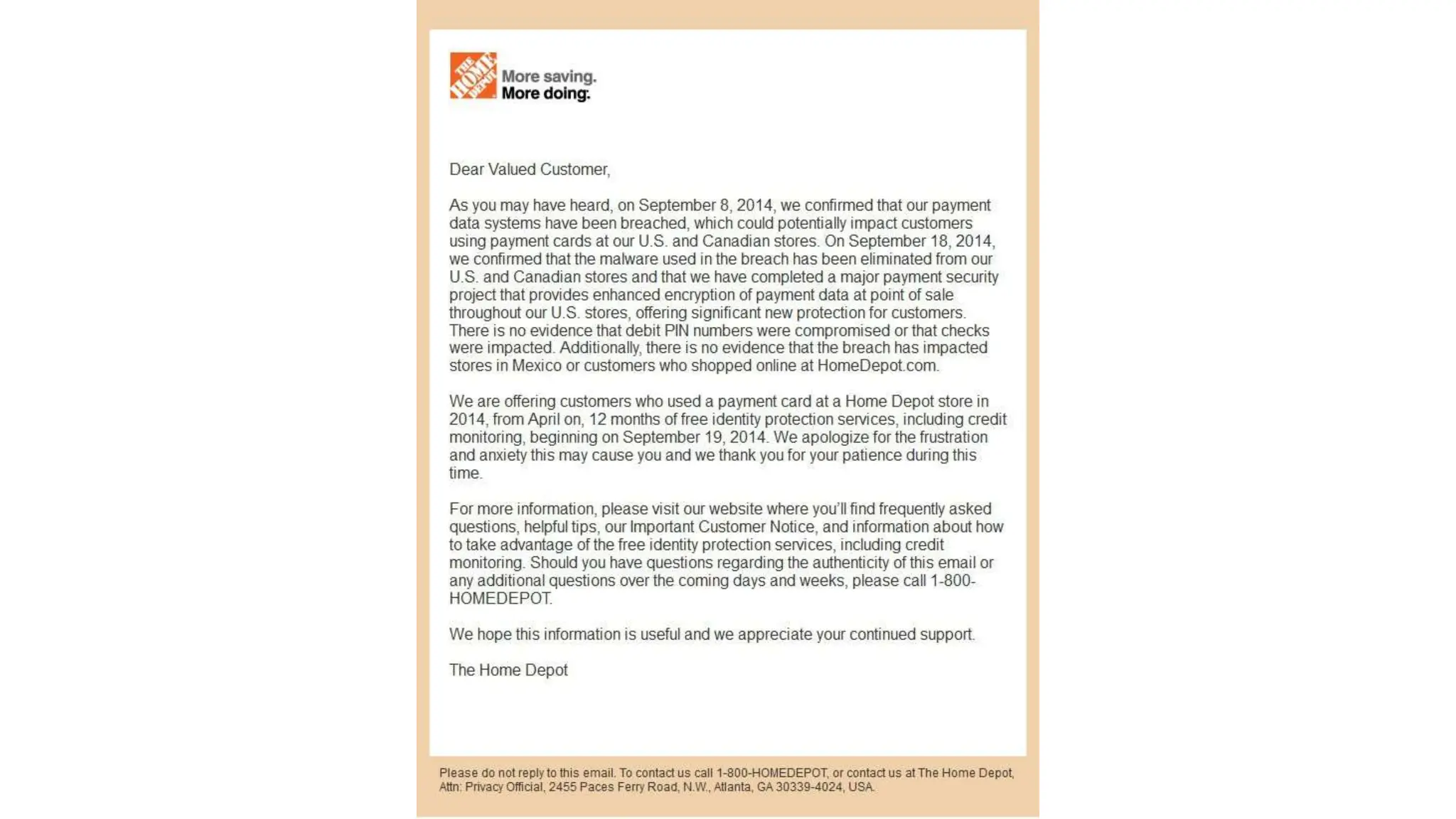
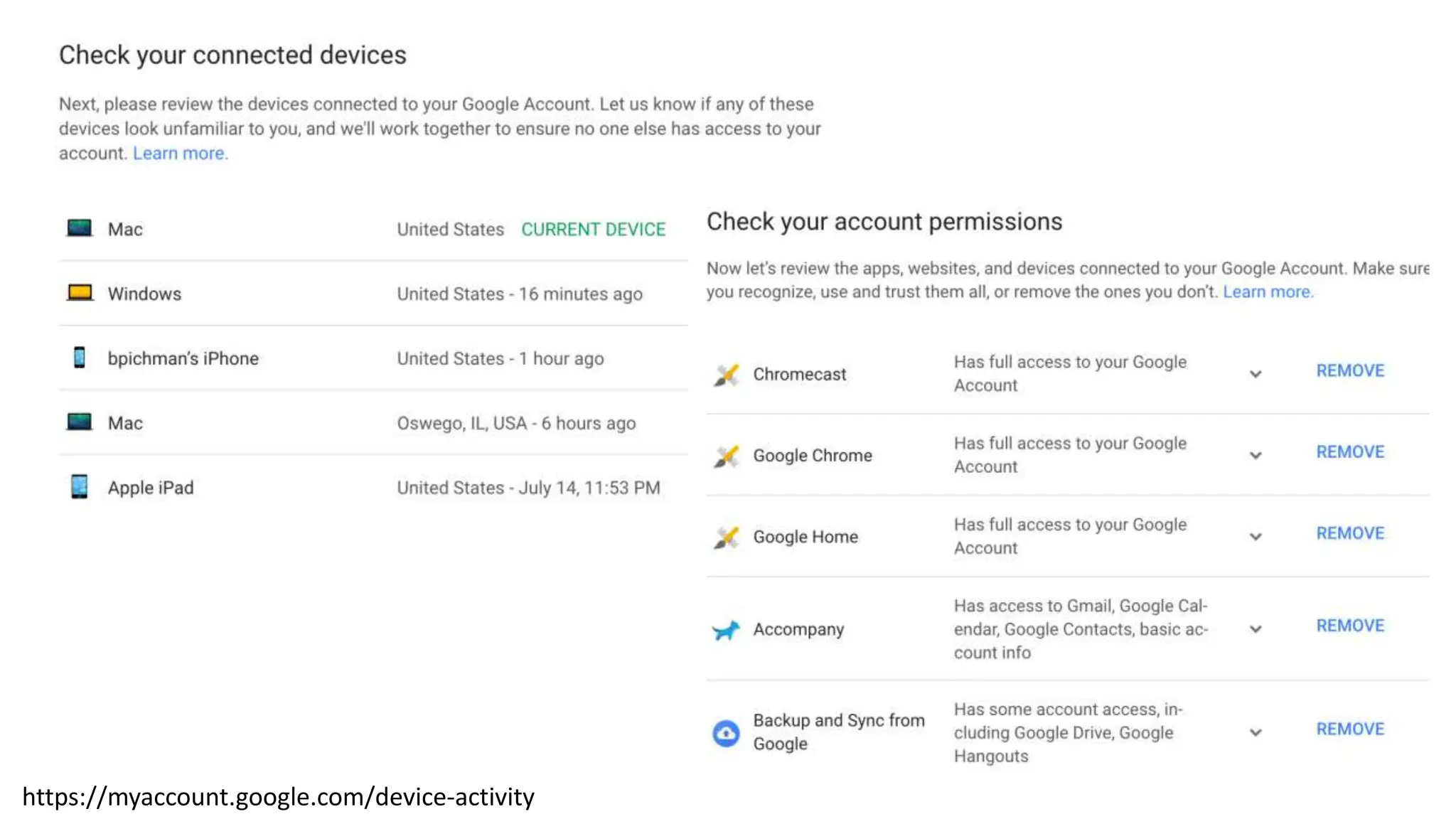
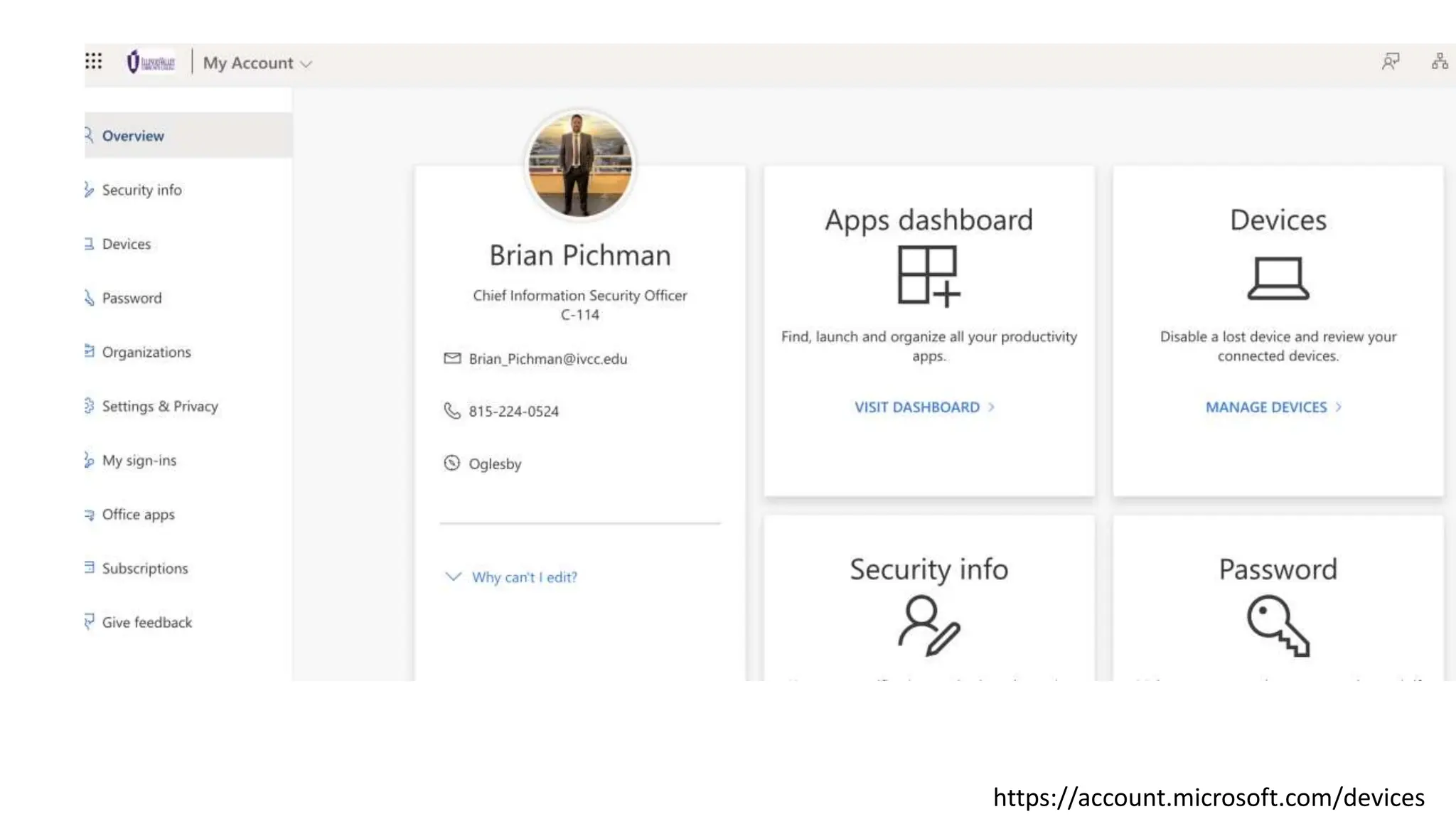
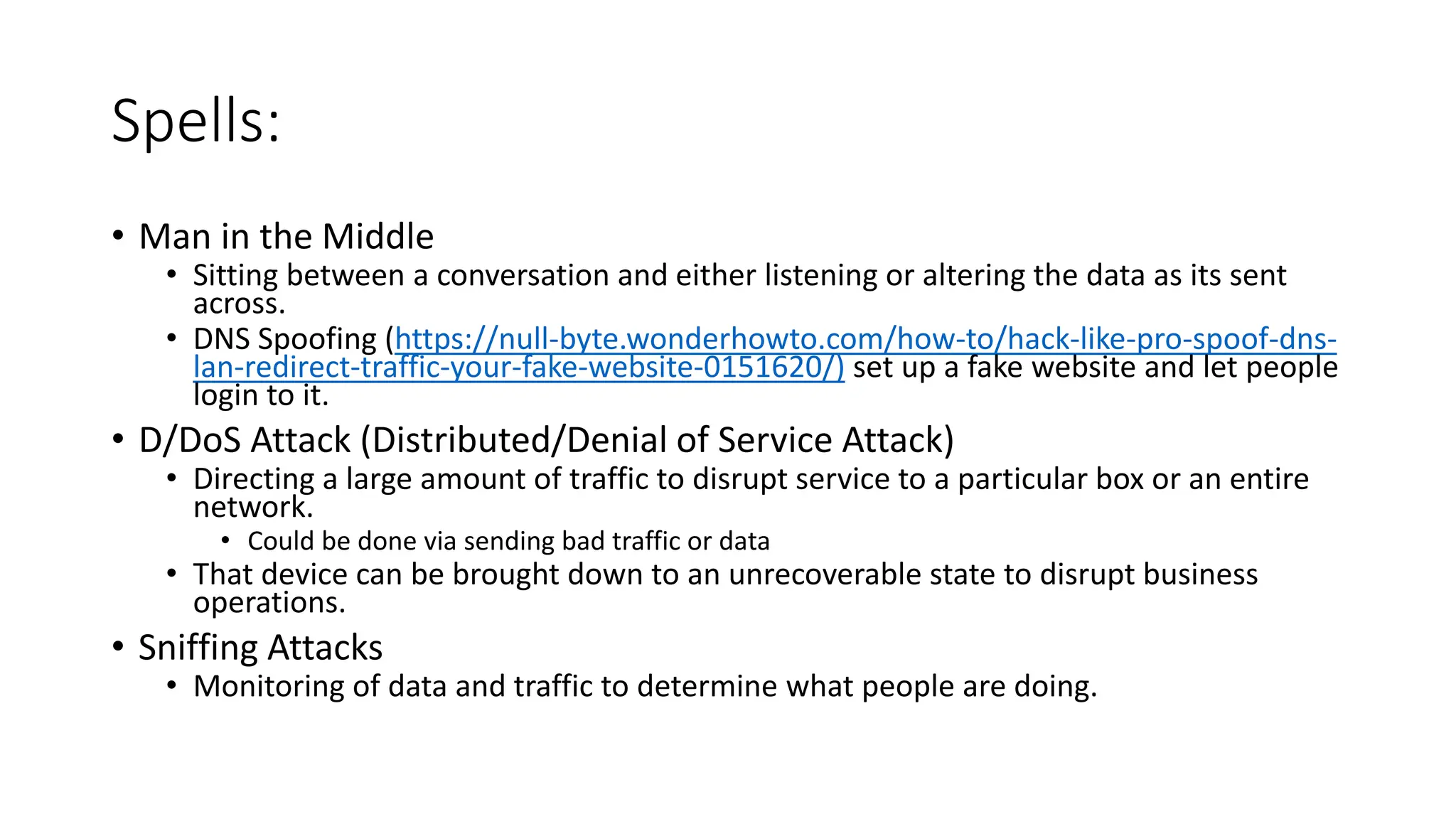
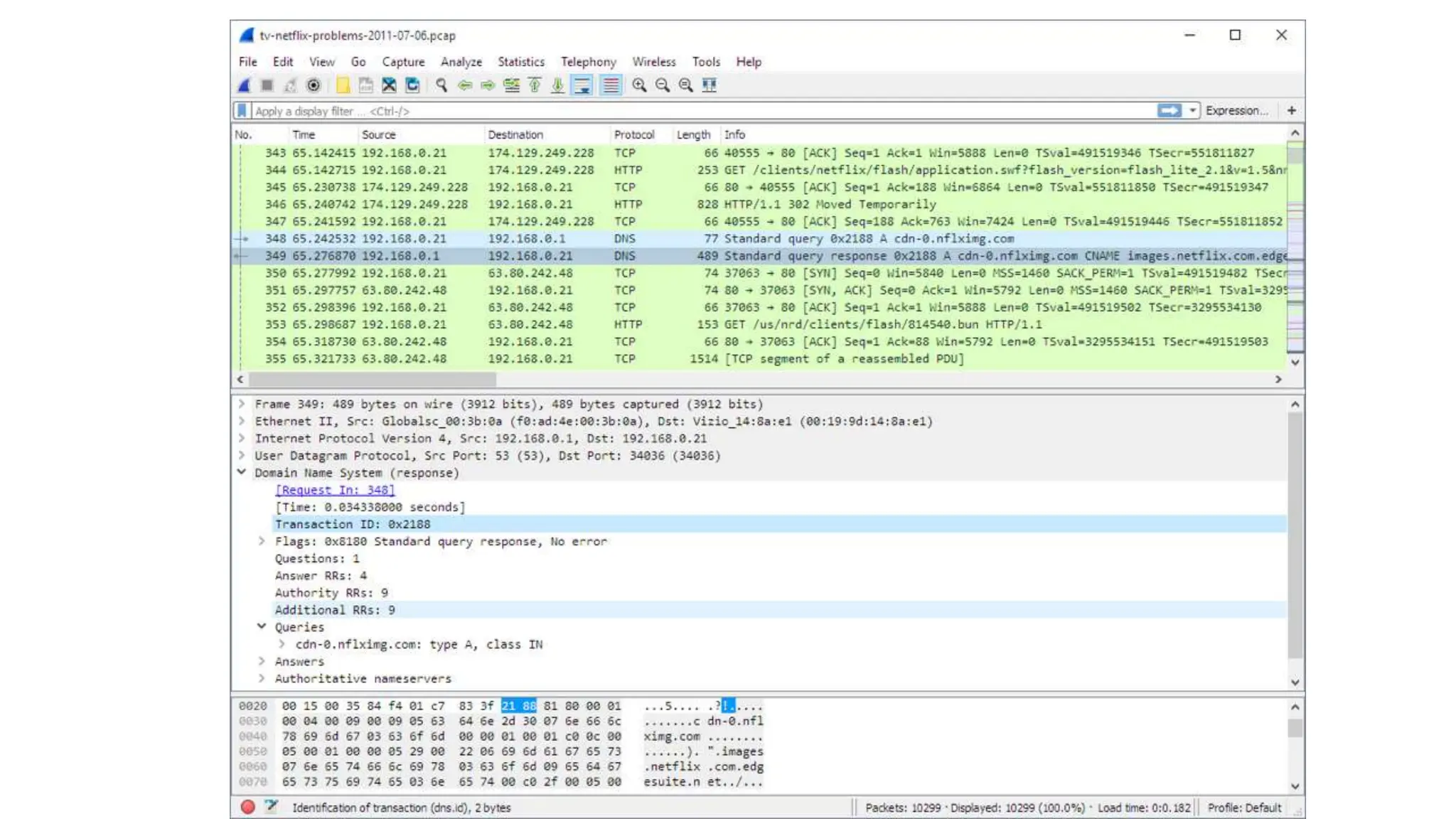
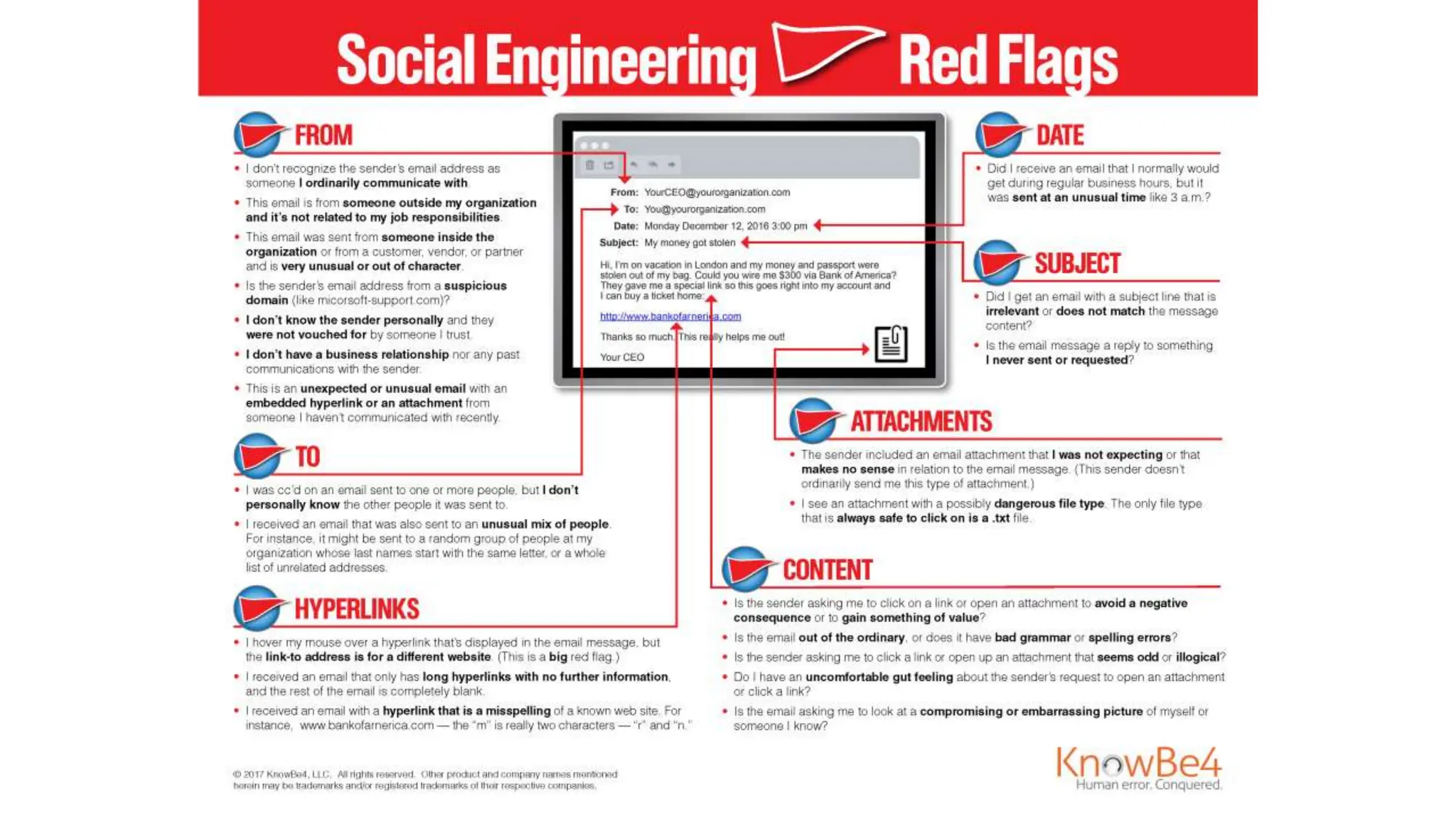
The document provides an extensive overview of cybersecurity training, focusing on methods for ensuring anonymity and protecting personal information online through tools like VPNs, Tor, and best practices to follow. It discusses the implications of data breaches, legal obligations for organizations, and offers advice on communication and handling incidents effectively. Additionally, the document emphasizes the need for established security policies within organizations to mitigate risks and educate employees on cybersecurity measures.

















































![Updates, Patches, Firmware
• Keeping your system updated is important.
• Being on the latest and greatest
[software/update/firmware] isn’t always
good.
• Need to test and vet all updates before
implementation
• If you can – build a dev environment to
test and validate.](https://image.slidesharecdn.com/itsession-cybersecurity-bccls-231013163032-f11ae360/75/Cybersecurity-Defense-Against-The-Dark-Arts-Harry-Potter-Style-84-2048.jpg)