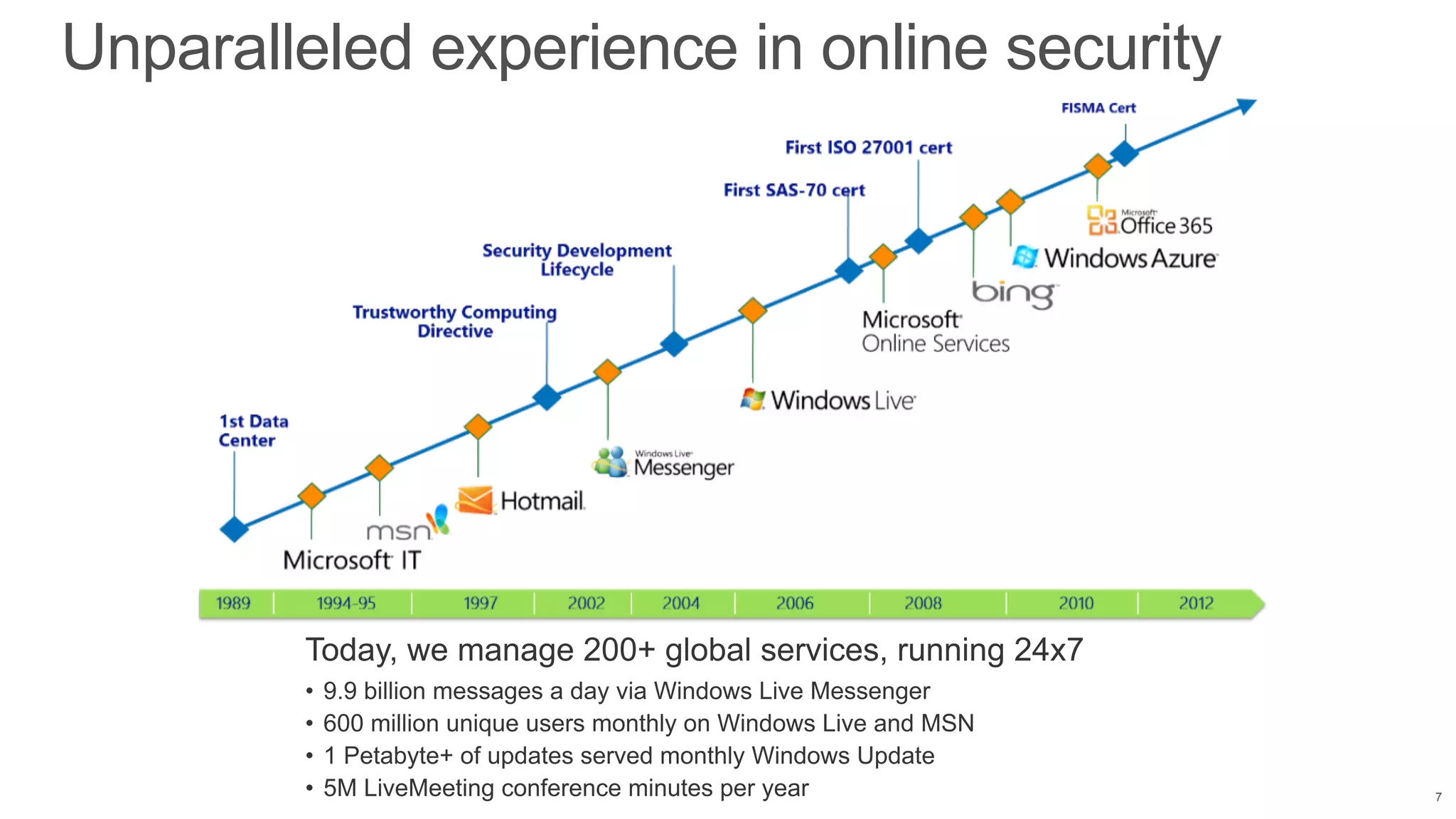
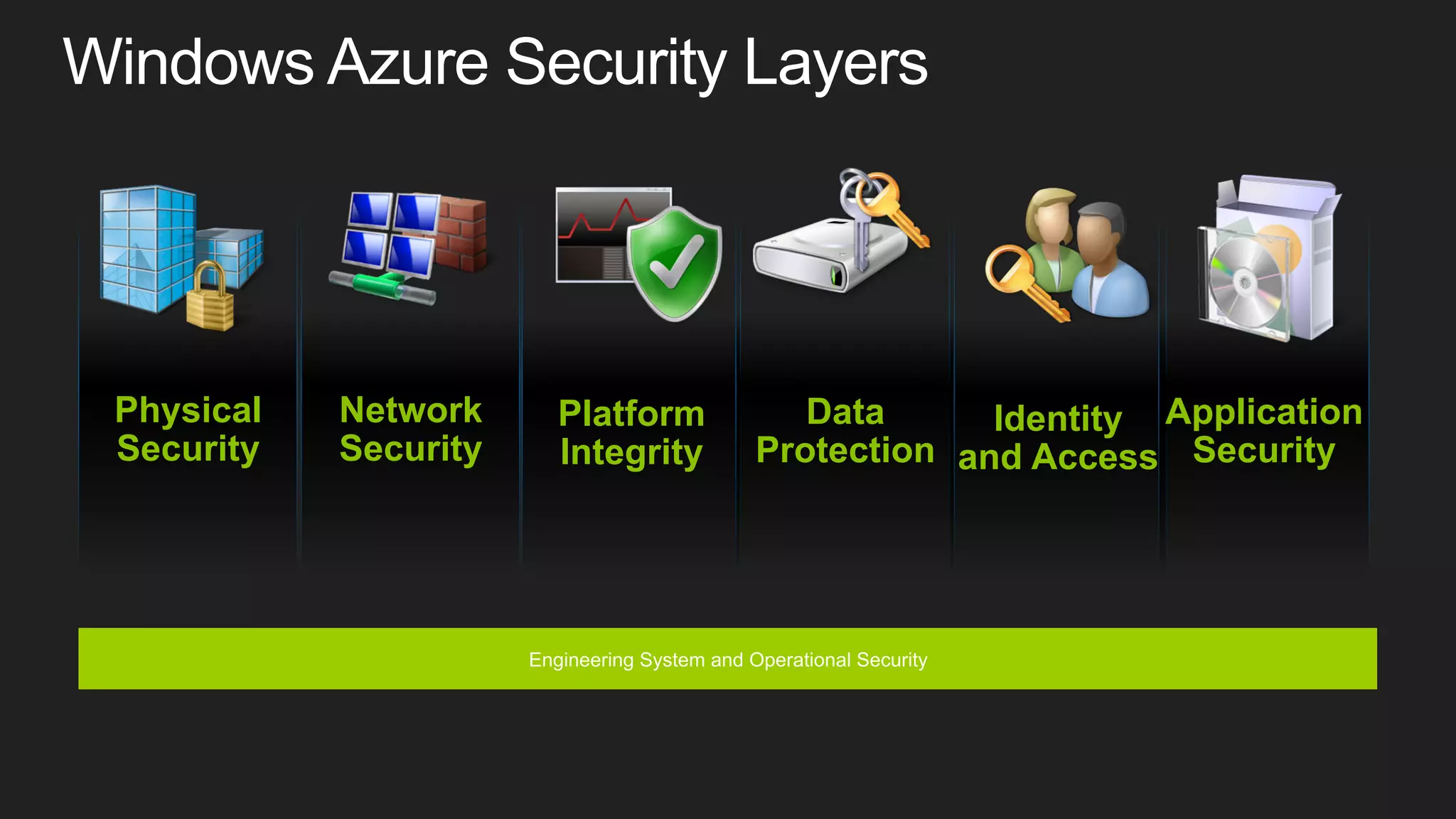
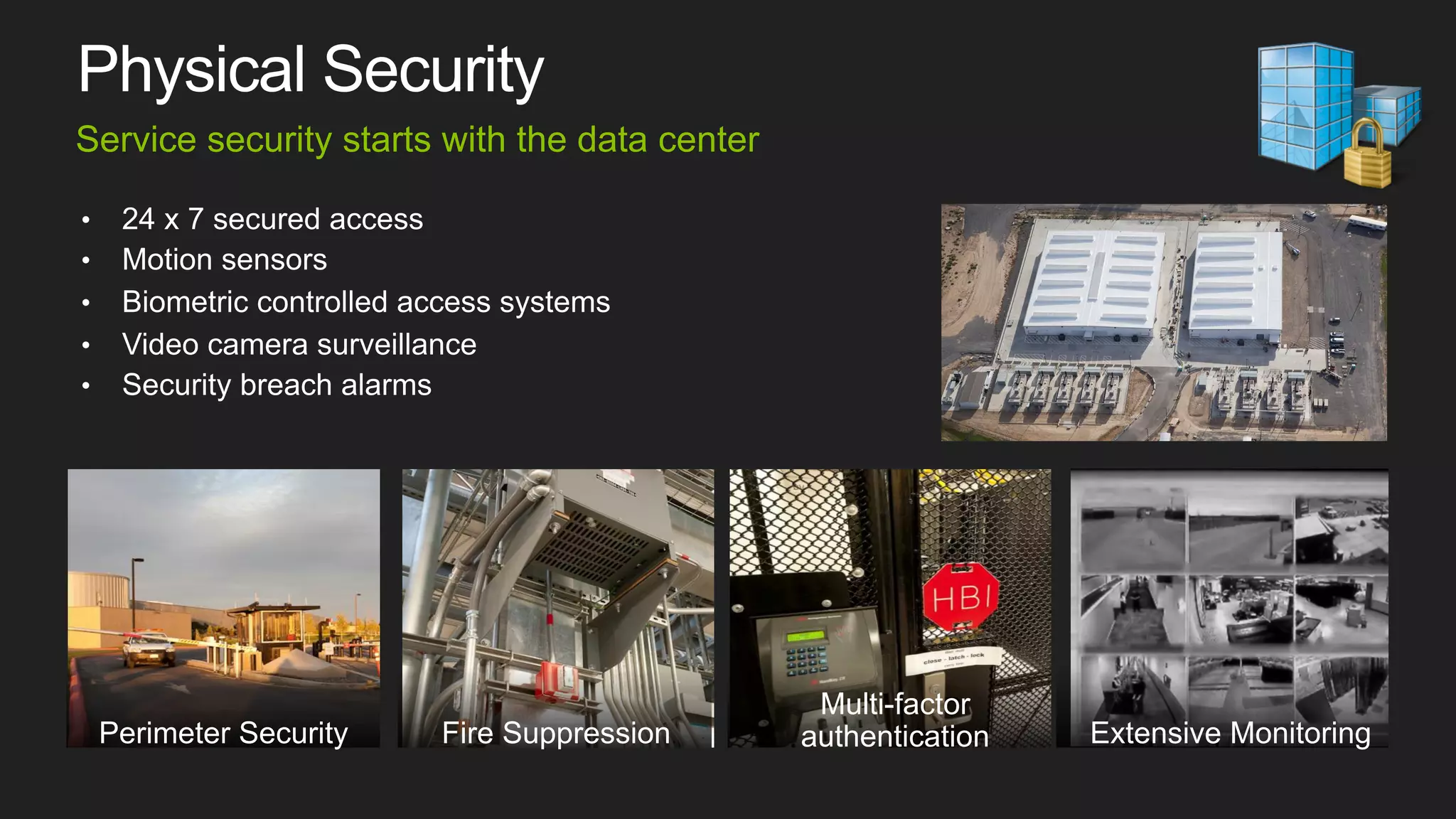
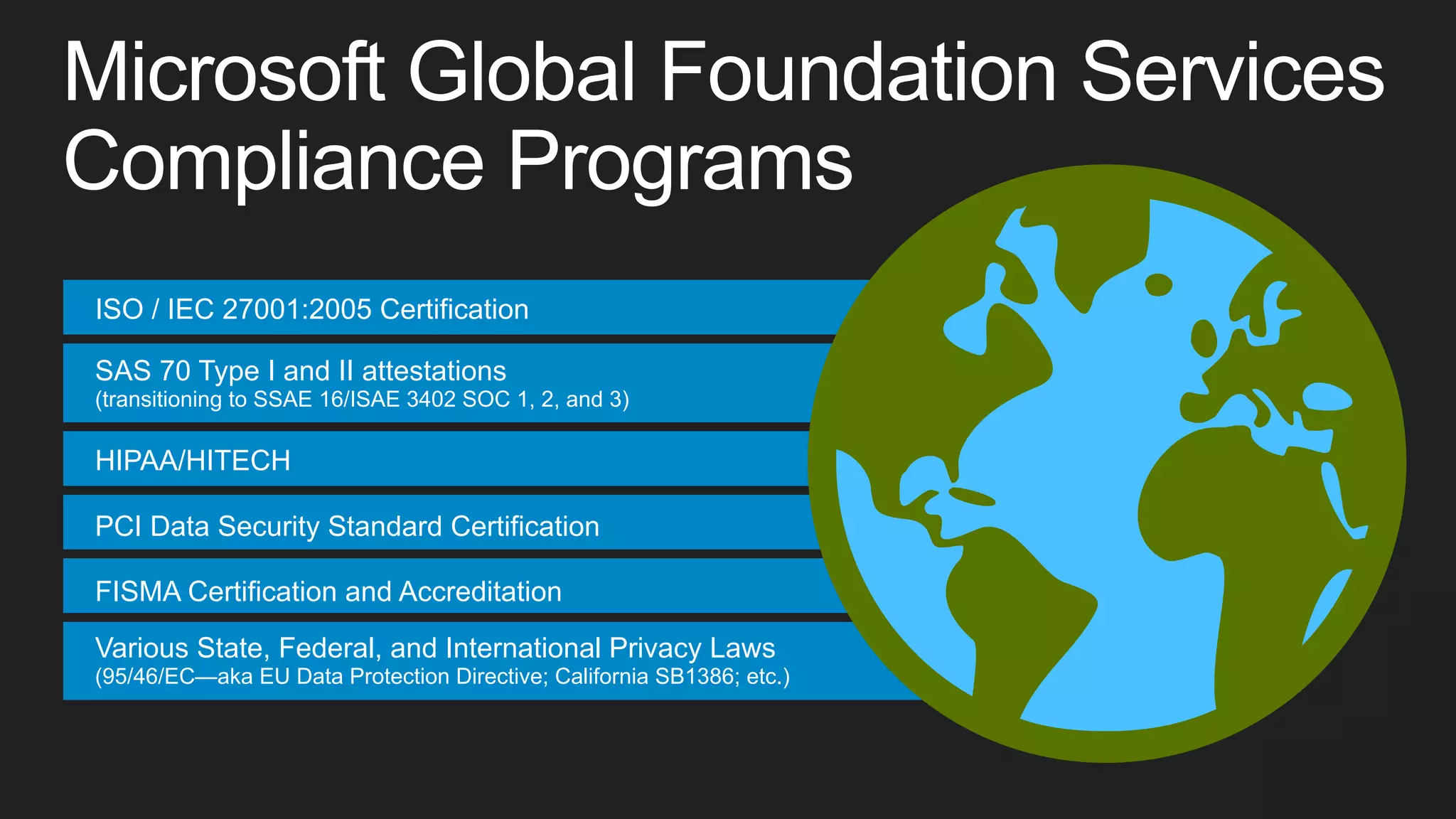
This document discusses cloud computing and security features of Microsoft Azure. It describes Azure's physical security measures, network security, platform integrity, data protection, and application security controls. Azure provides DDoS protection, storage redundancy, encryption, access controls, logging and more to help secure customer data and applications in the cloud. The trust center provides a single source of information about Azure's security, privacy and compliance.